Secure communication between a client and server requires more than just encryption. Moreover, it depends on using the correct network ports. HTTPS, the secure version of HTTP, transmits encrypted traffic over specific ports.
However, misconfigured or blocked HTTPS ports lead to failed connections, security warnings, or degraded performance.
This tutorial will explain what HTTPS ports are, how they work, and how to enable them on different operating systems.
What Is HTTPS Port?
An HTTPS port is a network port that handles encrypted web traffic over the HTTPS protocol. When a browser connects to a secure website, it uses HTTPS to establish a connection through a designated port that supports Transport Layer Security (TLS) encryption.
During this process, the client and server perform a TLS handshake, where they authenticate each other, agree on encryption algorithms, and initiate a secure session. Therefore, these ports act as communication endpoints between the client and server, allowing secure data exchange.
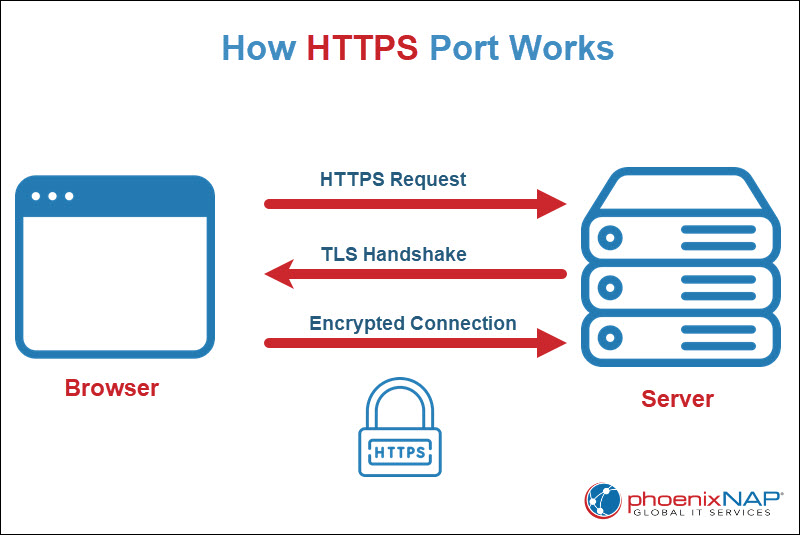
Each service on a network uses a specific port number to identify the type of traffic it handles. Specifically, HTTPS ports manage encrypted HTTP traffic and ensure the protection of data transmission against eavesdropping, tampering, and forgery. Consequently, without a properly configured HTTPS port, secure websites cannot load or sometimes display browser security errors.
HTTPS Port vs. SSL
HTTPS ports and SSL are similar, but they refer to different communication process layers. SSL/TLS handles encryption, while HTTPS uses ports to transmit that encrypted data. The two work together, but they are not interchangeable terms.
SSL (Secure Sockets Layer) was the original encryption protocol for HTTPS, but it has been deprecated due to security flaws. Therefore, TLS (Transport Layer Security) is the modern replacement. Still, the term SSL/TLS commonly refers to both, even though only TLS is in use today.
The table below outlines how HTTPS and SSL/TLS differ:
| Feature | HTTPS | SSL/TLS |
|---|---|---|
| Definition | Protocol for secure communication over the web. | Cryptographic protocol for encrypting connections. |
| Function | Transfers encrypted HTTP traffic through a network port. | Encrypts the data transferred over HTTPS. |
| Layer | Application layer (uses ports like 443 or 8443). | Security layer beneath HTTPS. |
| Port Involvement | Requires a specific port to operate. | Does not use a port directly. |
| Current Standard | HTTPS with TLS. | TLS (SSL is no longer considered secure). |
Why Use HTTPS Port?
Using an HTTPS port ensures all communication between a client and server is encrypted and secure. These ports handle HTTPS traffic, which uses TLS to prevent data interception, modification, or forgery during transit.
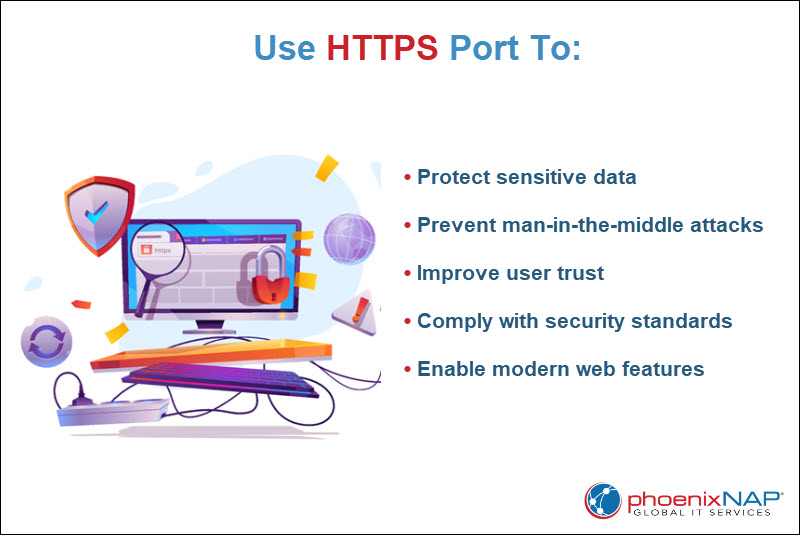
Properly configured HTTPS ports:
- Protect sensitive data. Information such as login credentials, payment details, and personal data is encrypted during transmission.
- Prevent man-in-the-middle attacks. Encrypted connections reduce the risk of third parties intercepting or altering traffic.
- Improve user trust. Browsers mark sites without HTTPS as Not Secure, which negatively impacts user confidence and site reputation.
- Comply with security standards. HTTPS is a requirement for many industry regulations and is a baseline for secure web applications.
- Enable modern web features. Features like HTTP/2, Progressive Web Apps (PWAs), and many APIs require a secure HTTPS connection.
However, without an HTTPS port, secure traffic is not possible, even if with a valid TLS certificate.
Default HTTPS Ports
Default HTTPS ports are predefined port numbers web servers and clients use to establish secure connections without manual configuration. Moreover, port numbers allow operating systems and networking hardware, such as routers, firewalls, and load balancers, to identify the correct service for incoming and outgoing traffic. For HTTPS, specific port numbers handle encrypted communication using TLS.
A default port is the port a protocol automatically uses if no other port is specified. The standardization allows clients and servers to communicate securely without needing to define ports explicitly in most scenarios.
While port 443 is the primary HTTPS port, 8443 is also common, especially for alternative services, development environments, or administrative interfaces.
The following sections explain the two most commonly used HTTPS ports and how they differ.
Port 443
Port 443 is the standard port for HTTPS traffic. Therefore, when a user visits a site using https://, the browser defaults to this port unless another is specified. However, this port is reserved for secure web communication using the TLS protocol.
Most web servers listen on port 443 for encrypted requests. Once there is a connection, TLS handles the encryption and decryption of data between the client and server, securing any sensitive information.
Since browsers and networking systems universally support port 443, users don't need to specify it in the URL. For example, https://example.com connects over port 443, which means connecting over https://example.com:443 is functionally identical.
Besides, this port is typically open by default in firewall settings.
Port 8443
Port 8443 is an alternative HTTPS port that handles secure web interfaces running separately from the main website. It supports TLS encryption and functions like port 443. However, it is often reserved for services that need to run alongside the primary HTTPS site.
Yet, this port is not standardized for general web access, so clients must explicitly include it in the URL (e.g., https://example.com:8443). Without it, browsers default to port 443 and fail to connect if no service is listening there.
Use cases for port 8443 include:
- Web-based admin consoles (e.g., routers, control panels).
- HTTPS versions of services already using port 443.
- Development servers running in parallel to production sites.
Unlike port 443, 8443 is not always open by default in firewalls or router settings. It requires manual configuration to allow secure traffic.
Port 443 vs. Port 8443
While both ports support HTTPS traffic secured by TLS, they work in different contexts and behave differently across systems and services.
The table below highlights their differences:
| Feature | Port 443 | Port 8443 |
|---|---|---|
| Purpose | The default port for public HTTPS traffic. | Alternative port for secure services running alongside 443. |
| Default behavior | Automatically used by browsers and clients. | Requires explicit port reference in the URL. |
| Visibility in URL | Not shown. | Required. |
| Typical use cases | Shares the main TLS/SSL certificate. | Admin panels, dev/test instances, vendor tools. |
| Firewall status | Commonly open by default. | Often blocked; requires manual allow rules. |
| SSL certificate usage | Can use a separate certificate or the same as 443. | Can use a separate certificate or the same as 443. |
| Log visibility | Frequently monitored in the default server and WAF logs. | May be ignored unless explicitly configured. |
List of Other HTTPS Ports
Many services use alternative ports to support secure communication. They are assigned to particular software or specialized web interfaces. However, unlike port 443, they are not open by default, so users need to configure them manually.
The following table summarizes common HTTPS ports:
| Port | Function |
|---|---|
| 443 | Supports default HTTPS traffic for secure web communication. |
| 8443 | Supports default alternative HTTPS traffic for secure web applications. |
| 631 | Enables secure printer management using Internet Printing Protocol over HTTPS (IPPS). |
| 664 | Provides secure out-of-band management via HTTPS as defined by the DMTF. |
| 832 | Handles HTTPS-secured NETCONF communications over SOAP for automated network device management. |
| 1129 | Facilitates secure HTTPS communication for SAPHostControl to manage SAP processes. |
| 4849 | Provides secure HTTPS access to Oracle WebLogic Server administration console for enterprise app management. |
| 5989 | Manages WBEM CIM-XML over HTTPS for system monitoring in enterprise environments. |
| 5990 | Supports secure WBEM Export over HTTPS for exporting management data to remote clients. |
| 6443 | Serves as the default HTTPS port for the Kubernetes API server, managing containerized application clusters. |
| 7202 | Enables secure HTTPS communication for Inter-Channel Termination Protocol (ICTP) in multi-wavelength PON systems. |
| 7443 | Provides secure HTTPS access for Oracle Application Server interfaces. |
| 7677 | Handles secure HTTPS communication for Eclipse GlassFish Server administration. |
| 8243 | Processes non-blocking HTTPS traffic for Apache Synapse in enterprise service bus environments. |
| 9443 | Offers alternative HTTPS access for administrative interfaces and APIs in platforms like Kubernetes and Keycloak. |
| 9444 | Supports secure HTTPS communication for administration in WSO2 enterprise products. |
| 9445 | Enables secure HTTPS management of business processes on WSO2 Business Process Server. |
| 9446 | Provides secure HTTPS access for identity management via WSO2 Identity Server. |
| 9447 | Supports secure HTTPS administration for governance services on WSO2 Governance Registry. |
| 16993 | Enables remote management via secure HTTPS SOAP web services on Intel AMT. |
| 20003 | Supports secure HTTPS communication for industrial IoT remote monitoring via Commtact. |
| 10443 | Provides secure HTTPS administrative access for security appliances and network management consoles. |
| 10444 | Supports secure HTTPS communication for middleware and identity management products. |
| 12443 | Enables secure HTTPS access for proprietary network devices and software solutions. |
| 5443 | Supports secure HTTPS web services for Pearson in educational and enterprise systems. |
Port 631
Port 631 is used by the Internet Printing Protocol over HTTPS (IPPS). IPPS enables secure printing over a network by encrypting communication between the client (e.g., a computer or mobile device) and a printer using TLS.
Common UNIX Printing System (CUPS) uses this port on Unix-like systems, including Linux and macOS. It allows authenticated, encrypted remote printing and printer administration via a web interface and is usually restricted to internal networks.
Port 664
Port 664 handles secure out-of-band web services management defined by the Distributed Management Task Force (DMTF). Out-of-band (OOB) management allows system administrators to access and control hardware remotely, even when the operating system is unresponsive or powered off. However, this works through a dedicated management controller that operates independently of the main network interface.
The DMTF creates standards for platform-level management. This port supports HTTPS, enabling secure remote tasks such as diagnostics, firmware updates, and system configuration, especially in enterprise environments with server or storage hardware.
Port 832
Port 832 is the main port for Network Configuration Protocol (NETCONF) when transmitted over Simple Object Access Protocol (SOAP) with HTTPS, which works in environments that require automated, encrypted management of network devices.
NETCONF manages and configures network devices such as routers, switches, and firewalls. Moreover, it enables administrators to retrieve, modify, and install configuration data remotely. NETCONF is common in network automation and orchestration systems.
SOAP is a messaging protocol that allows programs running on different systems to communicate using XML-based messages over HTTP or HTTPS. These messages use Extensible Markup Language (XML) to format structured data that is human-readable and easy for machines to process.
Port 1129
SAPHostControl, a component in SAP systems that provides management functions over HTTPS using SOAP, employs port 1129.
Specifically, SAPHostControl allows administrators to monitor and control SAP system processes, read configuration files, check system status, and perform basic operations remotely. Additionally, communication over HTTPS ensures the data exchanged between the SAP tools and the host agent remains secure.
Port 4849
Port 4849 is the default HTTPS port for the Oracle WebLogic Server administration console. WebLogic Server is a Java Enterprise Edition (Java EE) application server for deploying and managing enterprise applications.
Furthermore, the administration console provides administrators a secure web interface to configure settings, monitor server health, and enforce security policies. HTTPS encrypts all communication over port 4849, protecting sensitive data and credentials during remote management.
Oracle WebLogic Server is common in large enterprises, financial institutions, and government organizations that require scalable, reliable application hosting.
Port 5989
Port 5989 is used for WBEM CIM-XML over HTTPS, a protocol standard for system management and monitoring.
Web-Based Enterprise Management (WBEM) is a set of standards that unify the management of distributed computing environments. Common Information Model (CIM) defines how managed elements in an IT environment are represented. The CIM-XML protocol transmits this management data using XML over HTTP or HTTPS.
Port 5989 specifically handles the secure HTTPS version, ensuring encrypted communication between management applications and managed devices. Hence, it is common in enterprise IT for remote system monitoring, configuration, and management tasks.
Port 5990
WBEM Export over HTTPS, a part of the Web-Based Enterprise Management (WBEM) framework, uses port 5990. This service allows systems to securely export management data to remote clients or monitoring tools using HTTPS.
It works in enterprise environments where administrators need to collect system metrics, logs, and status data from remote hosts for analysis or centralized monitoring. Like port 5989, it relies on CIM standards to structure the exported data.
While newer solutions are becoming more common, WBEM Export over HTTPS remains in use in legacy systems and secure, compliance-driven infrastructures.
Port 6443
Port 6443 is the default HTTPS port for the Kubernetes API server. Kubernetes is an open-source system for automating the deployment, scaling, and management of containerized applications.
This port handles communication between users, command-line tools such as kubectl, and internal components and controllers. Also, it is responsible for all operations related to the Kubernetes control plane.
HTTPS encrypts all traffic through port 6443. However, mechanisms such as tokens or certificates provide authentication.
Port 7202
The Inter-Channel Termination Protocol (ICTP) over HTTPS uses port 7202. ICTP is a specialized protocol for managing multi-wavelength Passive Optical Network (PON) systems.
PON is a fiber-optic telecommunications technology that delivers high-speed internet access to end users via a shared optical fiber. ICTP allows secure coordination and control between different wavelength channels within these networks, helping manage data distribution across the optical infrastructure.
Port 7202 ensures encrypted management communication for advanced PON deployments, often used by Internet Service Providers (ISPs). While niche, it is still relevant in modern fiber-based access networks.
Port 7443
The Oracle application server uses port 7443 for secure HTTPS-based communication. This port handles administrative interfaces and web services provided by the server.
However, Oracle Application Server is a legacy middleware platform that deploys and manages enterprise applications, especially those using Java EE technologies. It worked in corporate environments for hosting internal web apps, running Oracle Forms, and managing service-oriented architecture (SOA) components.
Although Oracle has shifted focus toward newer platforms like Oracle WebLogic Server, some organizations still maintain older systems that rely on the 7443 port for secure admin access and service communication.
Port 7677
The Eclipse GlassFish Server uses port 7667 for secure HTTPS communication. This Java EE application server was originally developed by Sun Microsystems and is now maintained as an open-source project under the Eclipse Foundation.
The port provides access to the administration console and other management interfaces, allowing administrators to deploy applications, configure server settings, and monitor system health securely over HTTPS.
While GlassFish remains popular in development and some production environments, many enterprises have shifted to other platforms, but the port is still relevant for those using or maintaining GlassFish-based applications.
Port 8243
Apache Synapse uses port 8243 for handling non-blocking HTTPS traffic. Synapse is an open-source enterprise service bus (ESB) that routes, transforms, and manages messages between services in service-oriented architecture (SOA) systems.
The term non-blocking refers to the way Synapse handles incoming HTTPS requests asynchronously. This means the server is able to process multiple requests concurrently without waiting for each to complete, which improves scalability. The port works as the default HTTPS endpoint in such ESB environments.
Port 9443
Port 9443 is an alternative HTTPS port for accessing administrative interfaces and secure APIs of various enterprise applications. For example, platforms like Kubernetes and Keycloak adopted it for web-based admin consoles and REST APIs.
This port is functionally similar to port 443 but often separates administrative traffic from public-facing HTTPS services. Moreover, it encrypts communication using SSL/TLS and works in environments that require secure access to backend services, especially in microservices or API-driven architectures.
Port 9444
Port 9444 is used for secure administrative or management interfaces in middleware and enterprise platforms. For example, in WSO2 products (like WSO2 API Manager), it hosts internal services and secure transport layers for administration.
Moreover, WSO2 is an open-source platform for building and managing APIs and services. It is popular in enterprise environments for service integration, API management, and identity handling.
Using a separate port like 9444 for internal tasks helps isolate backend functions from public endpoints and improves security. Like port 9443, this port serves encrypted HTTPS traffic. However, it often handles internal or backend communications without exposing it to public networks. It's common in clustered deployments and service-oriented architectures.
Port 9445
WSO2 Business Process Server (BPS) uses port 9445 for secure HTTPS communication. WSO2 BPS is an open-source platform that enables organizations to design, execute, and monitor business processes based on the Business Process Execution Language (BPEL).
Through port 9445, WSO2 BPS exposes administrative consoles and APIs securely, allowing administrators to manage workflows, monitor process execution, and handle human tasks. The use of HTTPS on this port ensures sensitive business process data remains encrypted and protected during transmission.
While niche, WSO2 Business Process Server is still relevant in enterprises that rely on complex workflow automation and process orchestration within service-oriented architectures.
Port 9446
WSO2 Identity Server uses port 9446 for secure HTTPS communication. WSO2 Identity Server is an open-source identity and access management (IAM) solution. In addition, it enables organizations to manage user identities, authentication, and authorization across applications and services.
Using port 9446, the Identity Server provides secure administrative and API access for identity-related operations, such as single sign-on (SSO), identity federation, and user provisioning. This port ensures the encryption and protection of sensitive identity management traffic.
Port 9447
Port 9447 is the default port for WSO2 Governance Registry, which provides secure HTTPS access for managing governance-related services. The WSO2 Governance Registry is a middleware platform that helps organizations govern, manage, and monitor enterprise policies, metadata, and service descriptions.
Moreover, with port 9447, administrators have secure access to the registry's management console and APIs, enabling control over service lifecycles, versioning, and compliance tracking. Encryption through HTTPS on this port ensures sensitive governance data remains protected during transmission.
WSO2 Governance Registry is used in enterprise environments that require strong governance and policy enforcement within their service-oriented architectures.
Port 16993
Intel Active Management Technology (AMT) uses port 16993 for secure HTTPS communication over its SOAP-based web services. Intel AMT is a hardware and firmware technology built into many Intel-based computers that allows remote management and monitoring, even when the device is powered off or the operating system is unresponsive.
With port 16993, administrators perform remote diagnostics, system recovery, and firmware updates through encrypted channels. This port ensures secure communication between management consoles and Intel AMT-enabled devices.
Intel AMT works in enterprise environments for out-of-band device management and is an important component in many IT asset management strategies.
Port 20003
Commtact services use port 20003 for secure HTTPS communication. Commtact provides industrial Internet of Things (IoT) solutions, including remote monitoring and control of devices in sectors like manufacturing, energy, and utilities.
Through port 20003, Commtact systems enable encrypted data exchange between IoT devices, gateways, and management platforms. This ensures the confidentiality and integrity of operational data critical for industrial automation and monitoring.
This port is relevant in specialized industrial environments where secure remote management of IoT infrastructure is required.
Port 10443
Network management consoles use port 10443 for secure HTTPS access. They enable encrypted communication for web-based administrative interfaces in firewall systems, VPN gateways, and intrusion detection or prevention platforms.
While less common than standard HTTPS ports, it is still important in enterprise security setups that require isolated management channels.
Port 10444
Port 10444 serves middleware, identity management, and clustered enterprise software products for secure HTTPS communication. However, it often functions as a secondary or dedicated port for administrative consoles, API endpoints, or inter-node communication in modular architectures.
Its use is mostly confined to specialized enterprise environments with enhanced security and traffic segmentation requirements.
Port 12443
Proprietary network devices and specialized software solutions that require secure HTTPS connections use port 12443. Its use is in industrial automation, telecommunications, or enterprise management systems for remote encrypted access and configuration.
Though not widespread, it is relevant in scenarios demanding vendor-specific secure management interfaces.
Port 5443
Pearson services, often related to educational platforms and online learning management systems, use port 5443 for secure HTTPS communication. This port supports encrypted data exchange between clients and Pearson's web applications or administrative interfaces.
This vendor-specific port supports secure access to administration consoles and service endpoints. Although it is popular outside Pearson environments, it is active and important in those domains.
How to Enable Default HTTPS Ports on Different Operating Systems
Enabling HTTPS ports such as 443 and 8443 is essential to ensure secure communication between clients and servers. Without properly opening and configuring ports, HTTPS traffic firewalls, or system settings, block HTTPS traffic, which leads to connection failures, security warnings, or inaccessible services.
Therefore, the following sections explain how to enable default HTTPS ports 443 and 8443 on Windows, Linux, and macOS systems.
Enable HTTPS Port on Windows
To allow HTTPS traffic through ports 443 and 8443 on Windows, configure inbound rules using the Windows Defender Firewall with Advanced Security tool. This ensures applications using secure connections receive traffic without the system firewall blocking them.
To accomplish this, take the following steps:
1. Open Windows Defender Firewall.
2. Go to Advanced Settings.
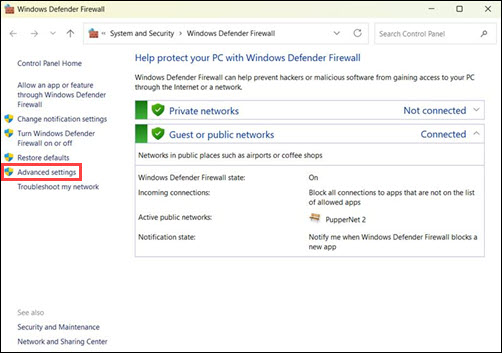
3. In the left pane, click Inbound Rules.
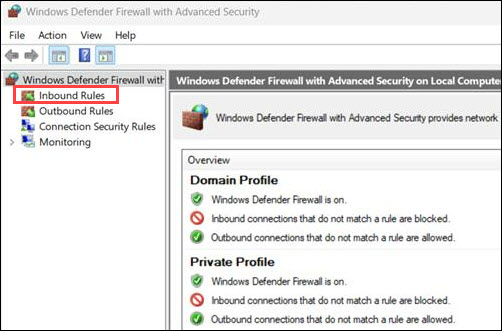
4. Select New Rule from the right-hand pane.
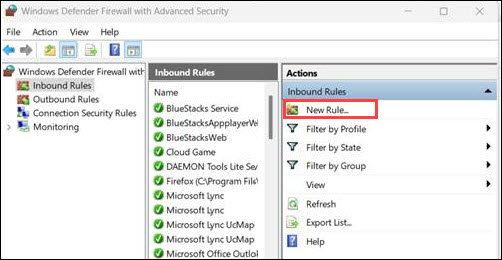
5. Select Port and click Next.
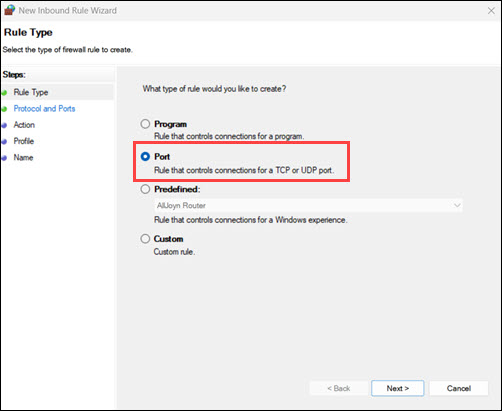
6. Choose TCP, then select Specific local ports. Next, enter 443,8443 and click Next.
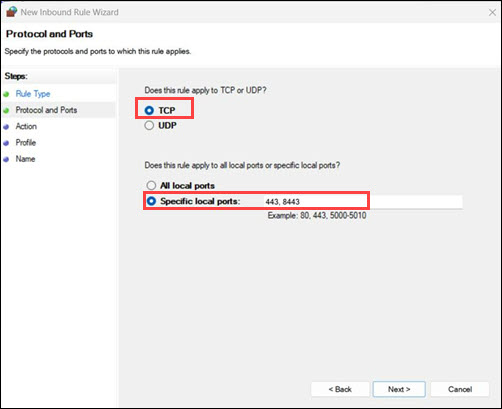
7. Choose Allow the connection and click Next.
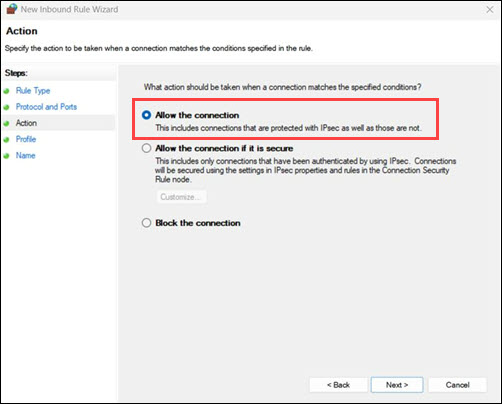
8. Check Domain, Private, and Public (as needed), then click Next.
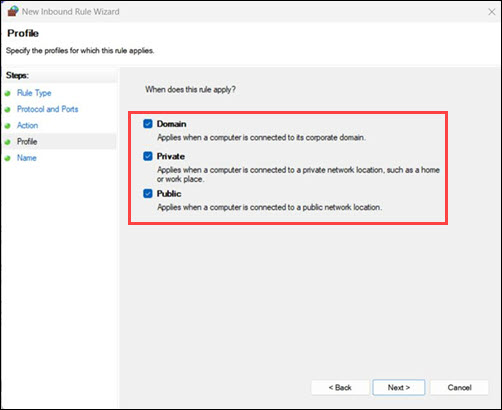
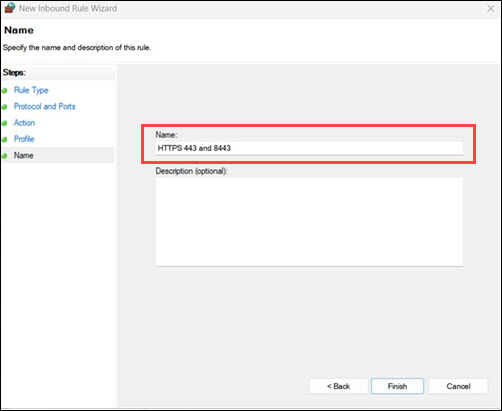
9. Enter a name such as HTTPS 443 and 8443. Finally, click Finish.
Enable HTTPS Port on Linux
On Debian-based Linux systems, open HTTPS ports with the UFW utility. Take the following steps:
1. Run ufw with sudo or as root to allow ports 443 and 8443:
sudo ufw allow 443/tcp
sudo ufw allow 8443/tcp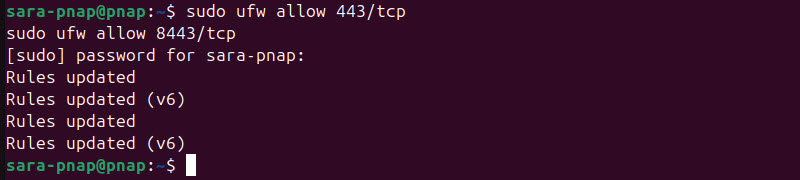
2. Confirm the rules:
sudo ufw status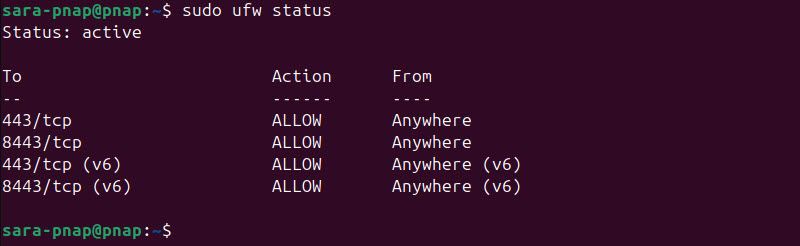
The output shows entries for both ports listed as ALLOW.
3. If the firewall is not active, the sudo ufw status command outputs the following:

In that case, enable it with this command:
sudo ufw enable
Note: On RHEL-based systems, use firewalld instead of ufw to manage firewall rules.
Enable HTTPS Port on Mac
macOS does not block ports like 443 or 8443 by default unless the application firewall actively restricts connections. However, if you need to explicitly allow incoming HTTPS traffic on these ports, use the built-in pf (Packet Filter) firewall via the command line.
Therefore, take the following steps to configure pf to allow ports 443 and 8443:
1. Create a custom PF rule file in a text editor. For example, to do it in Nano, run:
sudo nano /etc/pf.https.conf2. Add the following rules to allow incoming HTTPS traffic:
pass in proto tcp from any to any port 443
pass in proto tcp from any to any port 8443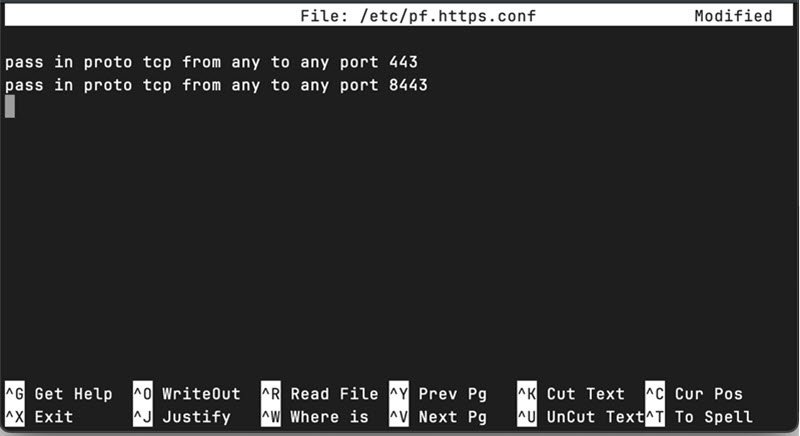
3. Save and exit the file.
4. Backup the default PF configuration with:
sudo cp /etc/pf.conf /etc/pf.conf.bakThe command has no output.
5. Include the custom rule in the main config:
echo "anchor \"https\"" | sudo tee -a /etc/pf.conf
echo "load anchor \"https\" from \"/etc/pf.https.conf\"" | sudo tee -a /etc/pf.confHowever, the echo command doesn't produce an output.
6. Enable and load the PF firewall with the new rules:
sudo pfctl -f /etc/pf.conf
sudo pfctl -e
Conclusion
This article explained what the HTTPS port is and how it differs from SSL. Moreover, it elaborated on its function and usage. Additionally, the text presented default and other common HTTPS ports, showing how to open them on different operating systems.
Next, learn how to ping a specific port in Linux, Windows, and macOS.