Encryption is the process of converting data into ciphertext to hide its meaning from unauthorized viewers (i.e., anyone who does not have a correct decryption key). This technique is among the most effective ways of protecting both static ("at rest") and moving data ("in transit"), which makes encryption a must-have for any data security strategy.
This article is an introduction to encryption in transit, one of the fundamentals of cybersecurity that protects data at its most vulnerable, while moving between two network points. Learn why keeping in-motion data safe is a priority and see the best practices your team must keep in mind when creating encryption in transit strategies.
Our article on encryption at rest explains how careful companies ensure their static data does not fall into the wrong hands.
What Is Data in Transit?
Data in transit (also known as data in motion or flight) is a piece of data actively moving between two network locations. Being in transit is one of the three primary states of data (the two others are at rest and in use). Here are a few examples of a file in transit:
- Sending an email over the Internet.
- Two employees exchanging files over a corporate network.
- Sending a message over an instant messenger (like WhatsApp or Viber) or a collaboration platform (like Slack or Microsoft Teams).
- Uploading a file from local storage to a cloud computing environment (or vice versa).
- Transferring data from a USB to a coworker's BYOD laptop.
- IoT data traveling between the cloud and an edge server.
- Data moving between a web app and a browser.
- Data traveling between different cloud deployment models within a multi-cloud strategy.
There are two broad categories of data in transit:
- Data flowing over public or untrusted networks (the Internet being the most common example).
- Files flowing within the confines of a private network (such as a corporate local area network (LAN)).
Data in transit is more vulnerable than static data you keep in an offline database due to the exposure in-motion files suffer during the route to the new location. Traveling data faces some unique risks that do not apply to stored data sets, such as:
- Man-in-the-middle and other eavesdropping attacks (also known as snooping or sniffing) intercept data as it travels across the network.
- The chance one of the employees sends data to the wrong recipient(s), which often leads to data leakage.
- Someone accidentally transmits data to a malware-infected device or website, which opens the door to advanced threats like ransomware or an APT attack.
Learn about data breaches, potentially business-ending threats that often start with an intercepted in-transit data packet.
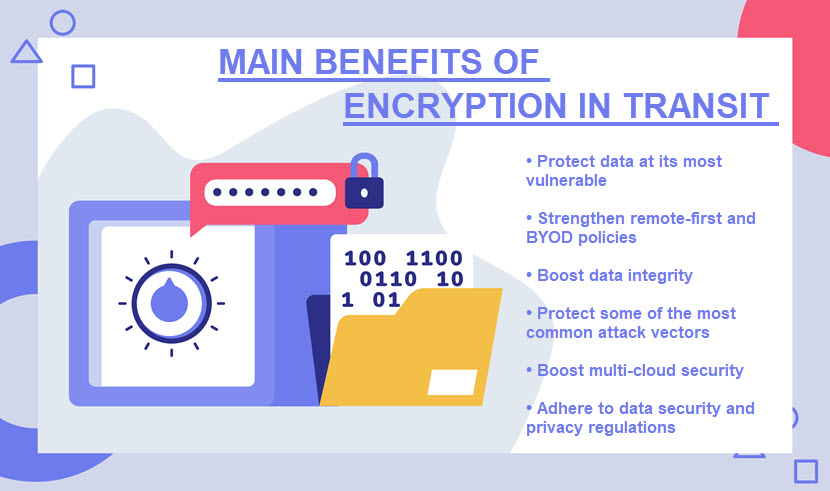
Importance of Encryption in Transit
Encryption in transit turns in-motion data into ciphertext before transmission. If a third-party intercepts traffic (accidentally or with malicious intent), the unauthorized user cannot open, edit, or decipher the data to its original state. Once data reaches the intended destination, endpoint authentication occurs, and the recipient's device decrypts files with a decryption key.
Here are the reasons why encrypting in-motion info is a priority:
- You ensure that all data employees send and receive is safe from prying eyes.
- You must protect data at every point of its lifecycle. No matter how strong the at-rest encryption is, a cryptography strategy is incomplete without in-transit protection.
- Data in flight is a prime target for a cyberattack. Intercepting data packets is much easier than breaching a database tucked behind a corporate firewall.
- It is much harder to detect in-transit interception than when a hacker passes an IDS and "breaks" into an on-site data storage. Not knowing about compromised data is a recipe for corporate espionage or CEO fraud attempts.
- Using encryption in transit is often a requirement for compliance. Strict regulations like PCI and GDPR make this form of cybersecurity non-optional for businesses in specific industries (namely, in finance and healthcare).
Encryption in transit is not vital only for big companies. Enterprises are an ideal target from a profit standpoint, but hackers often go after SMBs and family-owned businesses because they know these entities often lack adequate security policies and tools.
Our Data Security Cloud enables you to store data in a cloud-based platform and rely on security measures most companies cannot afford in-house (micro-segmentation, advanced threat scanning, MDR, end-to-end encryption, etc.).
Data in Transit Encryption Best Practices
Here are the best practices to keep in mind if you're looking to add encryption in transit to your cybersecurity strategy.
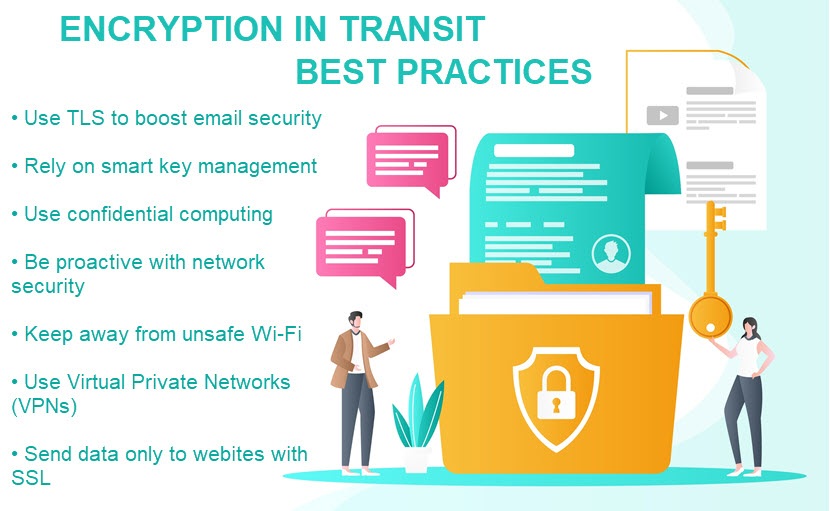
Use TLS Encryption for Emails
Email communications are a go-to attack vector for hackers looking to intercept outbound and inbound communications. Encryption in transit is a standard email precaution and is provided by all major providers (Google, Yahoo, Outlook, etc.).
Still, there's a catch—both the email sender and recipient must enable Transport Layer Security (TLS) for the encryption to take place. Enable TLS encryption on the email platform of your choice, plus only allow employees to exchange emails with recipients who have turned TLS encryption on their end.
Using in-transit encryption is only a small part of protecting corporate emails. Learn what else your team must cover in our article on email security.
Rely on Smart Key Management
If you want to deploy an in-house encryption strategy (whether at rest or in transit), you must get your key management procedures spot-on. Establish a business-wide policy that dictates the entire lifecycle of an encryption key, including strict rules for its:
- Creation.
- Storage.
- Use and rollover.
- Backup.
- Rotations.
- Destruction.
The goal of key management is to centralize your cryptography efforts and enforce encryption key management best practices.
Our Encryption Management Platform (EMP) offers an all-in-one solution that lets you control all company keys and usage rules from a single pane of glass.
Combine Encryption in Transit and Confidential Computing
An excellent way to boost encryption in transit is to use confidential computing. This cloud computing security feature isolates data during processing (editing, viewing, analyzing, etc.) by placing it in a protected, separate CPU enclave.
Everything within the dedicated CPU enclave, including the data and the programs that process files, remain secret. Access to the CPU enclave is only available to the user with an authorized programming code.
Combining encryption in transit and confidential computing guarantees end-to-end data security during transmission.
Interested in improving the safety of data and workloads during processing? PhoenixNAP's confidential computing enables you to adopt this cutting-edge tech and ensure airtight protection of valuable files.
Be Proactive (Not Reactive) with Security
Implement proactive security measures and robust network security to protect data in motion. Firewalls, anti-malware tools, strict access, and authentication controls help proactively secure data transmission networks, so you'll boost the efficiency of encryption in transit.
Your team must also ensure proper visibility of all data in motion. Security tools that ingest and analyze network data help:
- Detect anomalies in data access behavior.
- Identify potential threats and breach attempts.
- Determine the extent of the damage and limit further data loss in case of an interception.
You should also use a cloud access security broker to monitor data going to and from the cloud.
Our article on network infrastructure security offers an in-depth look at how top-tier companies keep networking devices and software safe.
Keep Employees Off Unsafe Wi-Fi and Use VPN
The growth of remote work increased the likelihood of employees using unsafe Wi-Fi connections to access and send data.
Ensure employees understand that public Wi-Fi networks with secure WPA (Wi-Fi Protected Access) and WPA2 networks are not inherently secure. While some of these networks encrypt user data from outside observers, they do not protect the data from other users within the same network. A malicious party could connect to the same public Wi-Fi and view sensitive corporate data.
Instruct your employees to rely on secure Wi-Fi connections from mobile phone hotspots and avoid insecure networks altogether. Even if all data transmissions have encryption, there's no reason to use unsafe Wi-Fi. Team members should use a VPN whenever accessing data from an off-site network. When you connect to the Internet via a VPN, it is almost impossible for someone to track your location or IP address by simply following it through the Internet.
Share Data Only with Websites That Have SSL Encryption
Ensure your employees visit and give data only to SSL-protected sites. SSL certification (identifiable via padlock symbol at the top of the address bar on an internet website) means that the website encrypts any info it exchanges with the visitor.
An SSL-protected website also has a URL that begins with HTTPS instead of just HTTP. HTTPS is a standard encryption approach for browser-to-web host and host-to-host communications. The lack of HTTPS is a massive red flag, and avoiding contact with such websites is a cybersecurity best practice.
Employees must never give sensitive data (passwords, login credentials, payment info, PII, etc.) to a website without SSL. If a site does not have SSL protection, a hacker can intercept data sent to a server and view, edit, or even destroy files.
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are vital processes for encryption in transit. Learn the difference between the two technologies in our TLS vs SSL article.

Encryption in Transit: A Non-Optional, Cybersecurity 101 Practice
Encryption in transit is the only way to ensure the integrity and security of file transmissions. Failing to protect in-motion data leads to permanent file loss, hefty legal fines, data breaches, and loss of user trust. Since all these scenarios have the potential to end a business, investing resources and time into setting up encryption in transit is a no-brainer for any security-aware company.



