PCI compliance is vital for any business that processes credit card payments. Ignoring these standards leads to hefty fines, erodes customer trust, and tarnishes your brand's reputation.
This checklist is a concise, practical guide to help you navigate and achieve PCI DSS compliance effectively.

What Is PCI Compliance?
PCI compliance refers to adherence to the Payment Card Industry Data Security Standard (PCI DSS). This standard was developed by major credit card brands (Visa, MasterCard, American Express, Discover, and JCB) to ensure that any organization handling, processing, or transmitting credit card information maintains a secure environment. Achieving and maintaining PCI compliance helps protect both businesses and consumers from fraud and data breaches by enforcing best practices for storing, handling, and transmitting sensitive payment data.

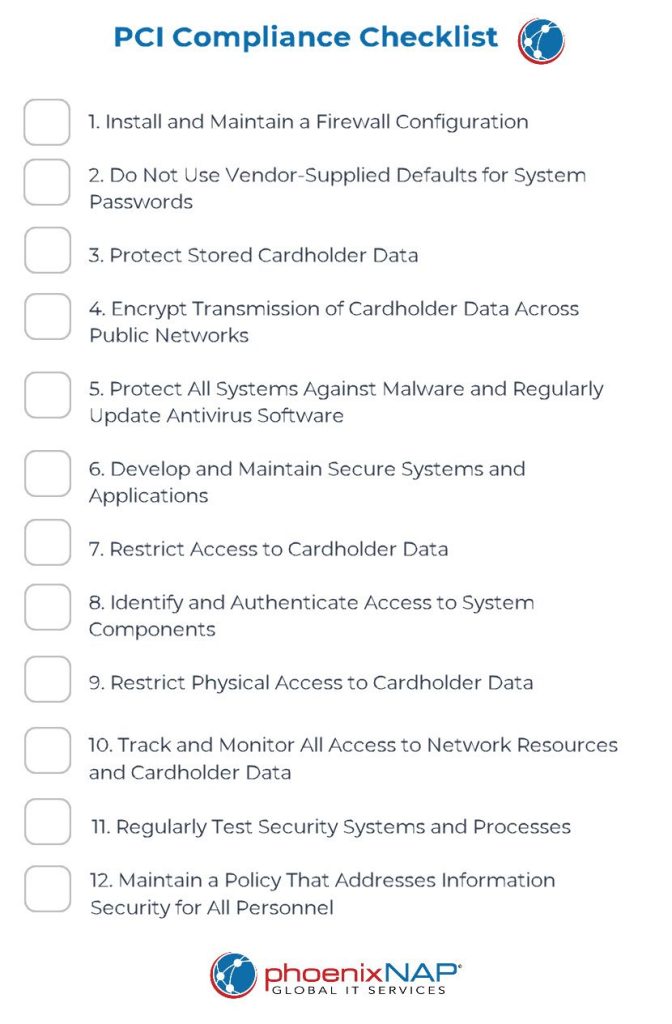
PCI Compliance Checklist
The checklist below breaks down the primary areas of the PCI DSS, detailing what you must do to comply and maintain a trustworthy system.
1. Install and Maintain a Firewall Configuration
Firewalls are a critical control point, regulating inbound and outbound traffic between the cardholder data environment (CDE) and external networks. They create a protective perimeter, blocking unauthorized attempts to access sensitive resources while permitting the approved traffic vital to daily business operations.
Document Your Network Topology
An accurate, up-to-date network diagram is indispensable for understanding how data flows through your environment. Each device, server, or application that processes or stores cardholder data should be clearly labeled on this diagram, along with connections to third-party service providers, if applicable. Keeping these diagrams current enables you to better identify areas of vulnerability, efficiently troubleshoot network issues, and streamline audits. Regularly revisiting your network documentation ensures you remain aware of new subnets, VLANs, or devices that could inadvertently introduce risk.
Restrict and Log Traffic
Carefully granting and denying inbound and outbound connections is the backbone of strong firewall security. Only those ports and services essential to business operations should be opened, and any other traffic must be blocked or otherwise restricted. Implementing robust logging practices offers invaluable insights into how data and requests flow through your network. Logs support forensic analysis if suspicious activity is detected and help you comply with the requirement to maintain an audit trail for crucial network events.
Review Firewall Rule Sets
Firewalls and routers operate on rule sets that determine what traffic is permitted. Outdated or overly broad rules can create unintentional entry points for attackers. A formal, documented change control process helps limit the possibility of human error when new rules are introduced or existing rules are modified. Reviewing configurations and rule sets at least twice yearly (or whenever a significant system change occurs) ensures continuous alignment with evolving operational requirements and emerging security threats.
Choosing the correct firewall type is vital because choosing the wrong type gives you a false sense of security despite the network being wide open to an attack.
2. Do Not Use Vendor-Supplied Defaults for System Passwords and Other Security Parameters
Many hardware and software components come with default settings that are widely shared in product documentation or openly available on the internet. Attackers often exploit organizations that fail to update these settings.
Replace Default Credentials
Replace every default username and password with strong, unique credentials upon installing new systems or devices. Inactive default accounts that serve no business purpose must be removed. This practice eliminates a known vulnerability that cybercriminals routinely attempt to leverage, especially in automated scanning attacks aimed at uncovering weak entry points.
Harden System Services
Unnecessary services, such as remote login tools or file-sharing protocols not used in daily operations, drastically widen your attack surface. Industry benchmarks (such as the CIS Benchmarks) provide detailed hardening recommendations tailored to specific operating systems, databases, or web servers. Regularly verifying that only the required services remain active helps maintain a lean, secure baseline across all assets in scope.
Maintain Secure Baseline Configurations
A secure baseline configuration is a documented set of approved settings for every system type within your PCI environment. This includes permitted services, properly configured logging, updated patches, and secure file permissions. Revisiting and updating these baselines when you learn of new vulnerabilities or after implementing major software upgrades enables you to adapt quickly to emerging threats. Sticking to a well-defined baseline also simplifies audits since you can systematically demonstrate that your environment meets recognized best practices.
3. Protect Stored Cardholder Data
Limiting both the scope and duration of data storage is a fundamental step in reducing exposure. If you don’t store it, you can’t lose it. Where storage is necessary, employing robust safeguards and minimal retention periods is key.
Limit Data Storage
Only retain the cardholder data strictly necessary for legitimate business processes or compliance obligations. Periodically assess whether certain fields—like the full 16-digit PAN—are essential, or if tokenization and truncation techniques can be employed to lessen risk. It’s also vital to ensure that sensitive authentication data (e.g., full magnetic stripe data, CVV/CVC codes, PIN blocks) is never retained post-authorization, closing a common gap that attackers seek to exploit.
Encrypt Data at Rest
Encryption ensures that the attackers cannot readily decipher the cardholder information, even if files are stolen or improperly accessed. Strengthening encryption involves using respected algorithms such as AES-256 and establishing comprehensive key management procedures. Keys should be rotated on a regular schedule or immediately if an employee with key access leaves the organization under questionable circumstances. By refining key management—covering generation, distribution, storage, and revocation—you reduce the likelihood of compromised encryption.
Mask PAN Display
Displaying only the first six and last four digits of the primary account number (PAN) wherever it appears is a clear PCI DSS requirement that prevents accidental or malicious use of full card numbers. Ensuring that only employees who explicitly require full PANs for essential business tasks can view them reduces the risk of internal threats or simple oversights, such as printing full PANs on paper or exposing them in shared logs.
Securely Dispose of Unneeded Data
Clearing out unneeded cardholder data requires rigorous procedures. File deletion alone may leave residual data on disk. Secure wiping or data sanitization methods—aligned with guidelines like NIST SP 800-88—should be used to ensure that no latent data is accessible. Incorporating routine data purges into your retention schedule, combined with safe disposal or destruction methods, significantly reduces the risk of post-authorization data exposure.
4. Encrypt Transmission of Cardholder Data Across Open, Public Networks
Transmitting unencrypted cardholder data over public or uncontrolled networks creates opportunities for interception and manipulation. Robust encryption prevents eavesdropping or tampering.
Enforce Strong Encryption
Older encryption protocols, such as SSL and early TLS versions, contain known security flaws that malicious actors can exploit. Transitioning to TLS 1.2 or TLS 1.3 is vital for protecting cardholder data on public networks. Ensuring that server-side configurations disable weak ciphers and protocols further strengthens your defense, as does confirming that clients, such as web browsers or mobile apps, are also configured to handle modern TLS variants.
Manage Certificates Properly
Whether SSL/TLS or code-signing, certificates require continual oversight. Proper certificate management systems track expiration dates, automate renewals, and revoke compromised certificates. This process ensures that no cardholder data is transmitted over channels like email, which is generally not encrypted end-to-end. Formalizing these controls helps establish a uniform security posture across all systems.
Segment the Cardholder Data Environment
Utilizing a demilitarized zone (DMZ) architecture and internal firewalls separates the internet-facing parts of your network from critical servers that store and process cardholder data. Proper network segmentation ensures that a compromised public-facing application server does not grant attackers direct access to the entire internal network. Segmentation also reduces the scope of PCI DSS audits, focusing scrutiny on isolated segments rather than your entire infrastructure.
Data typically requires protection at three critical stages:
• At rest. This type of encryption relates to data stored on disks, tapes, or other media, where it is inactive and vulnerable to unauthorized access if left unencrypted.
• In transit. This type of encryption relates to data traveling across networks, such as between servers or from a client to a host. Encryption protocols like TLS/SSL guard against interception or tampering along the route.
• In use. This type of encryption relates to data actively processed in memory or by the CPU during computations or while generating analytics.
5. Protect All Systems Against Malware and Regularly Update Antivirus Software or Programs
Malicious software, or malware, remains a leading cause of data breaches. Prioritizing the deployment and maintenance of antivirus and anti-malware solutions is, therefore, central to maintaining a secure environment.
Deploy Antivirus and Anti-Malware Tools
A comprehensive anti-malware strategy typically includes solutions installed on endpoints (laptops, desktops), servers, and, where possible, network gateways. These tools should provide real-time scanning and scheduled deep scans, detecting threats before they spread or become deeply embedded in system files. Consistent coverage across all eligible systems ensures that no single workstation or server becomes an unprotected entry point.
Keep Definitions and Engines Updated
Vendors release updated malware definitions and scanning engines frequently to keep pace with evolving threats. Allowing these updates to be installed automatically (or as soon as feasible) maintains the highest level of protection. A policy limiting user permissions to disable or bypass these solutions is also critical; employees should not be able to undermine security protocols, intentionally or by accident.
Respond Promptly to Alerts
You must address alerts from antivirus and intrusion prevention systems without delay. Even what appears to be a routine malware detection could point to larger issues, such as an unknown vulnerability or a compromised employee account. Documenting each alert and the subsequent response allows you to track persistent threats, fine-tune detection rules, and improve overall incident response workflows.

6. Develop and Maintain Secure Systems and Applications
Security is not a one-time exercise but an ongoing process throughout the entire lifecycle of your infrastructure, applications, and software components. Emphasizing secure development practices and continuous upkeep strengthens your security posture.
Adopt a Secure SDLC
A secure software development life cycle (SDLC) integrates security activities at every project stage: requirement gathering, design, coding, testing, deployment, and maintenance. Performing both static (SAST) and dynamic (DAST) testing uncovers coding flaws like buffer overflows, SQL injection vulnerabilities, or insecure API endpoints before they ever go live. Early detection saves time and money and significantly reduces potential vulnerabilities in production environments.
Apply Critical Patches Quickly
Attackers often exploit well-publicized vulnerabilities. Establishing a clear patch management policy helps your organization quickly apply critical fixes within a defined timeframe, which is often 30 days for severe vulnerabilities. Doing so limits the window of opportunity for criminals. Tools like WSUS (Windows Server Update Services), patch management platforms, or DevOps workflows streamline monitoring for new patches across operating systems, third-party libraries, and application dependencies.
Control Changes with Formal Processes
Every configuration change, be it to a firewall rule, database setting, or code deployment, poses a risk of introducing errors or security flaws. A formal change management process involving peer reviews, testing environments, and documented approval paths ensures that modifications do not compromise existing security controls. Thorough documentation, including a rollback plan, allows swift remediation if unintended consequences arise.
Protect Web Applications
Web applications are frequent targets of attacks, including injections, cross-site scripting (XSS), and cross-site request forgery (CSRF). Deploying a web application firewall (WAF) can block common malicious patterns before they reach your backend. Furthermore, secure coding practices, including proper input validation and output encoding, are crucial for mitigating application-layer threats. Regularly updated frameworks, sanitized user input, and careful session management significantly reduce exposure.
7. Restrict Access to Cardholder Data
By granting employees minimal access to payment card information, you reduce both the impact of insider threats and the risk of unauthorized disclosure if credentials are stolen.
Implement Role-Based Access Control (RBAC)
Role-based access control ensures users only have privileges aligned with their job responsibilities. Access rights to view or modify cardholder data must be approved at the managerial level and reviewed periodically. Employing group-based privileges in Active Directory (for Windows) or other LDAP-based solutions simplifies permission management across departments.
Update Access Policies Regularly
A dynamic workforce means roles and responsibilities shift over time. Frequent reviews—such as quarterly or upon any departmental changes—are essential to adjust permissions accordingly. Departing employees or contractors should have their access revoked promptly to prevent unauthorized lingering accounts, which are a common attack vector for security breaches.
Read our article on the most common types of cyber attacks you are most likely to encounter.
8. Identify and Authenticate Access to System Components
Accurate identification and authentication systems tie every action within your environment to a unique user or service account, promoting accountability and traceability.
Use Unique User IDs
Shared accounts create an "anonymity blanket" that attackers love, as tracing specific actions back to an individual becomes impossible. Assigning each team member a unique ID and service accounts for automated processes ensures accurate auditing and leadership.
Strengthen Authentication
Passwords remain a leading cause of breaches when they are weak or reused. Implementing multi-factor authentication (MFA) significantly boosts security by requiring additional verification steps. Strong password policies covering minimum length, complexity rules (mix of characters), expiration, and lockout thresholds help stave off brute-force or credential-stuffing attacks.
Manage Session and Lockout Policies
Session management involves automatically logging out users after a defined period of inactivity. This step reduces the chance of unauthorized access on unattended terminals. Implementing lockout policies after a certain number of failed login attempts deters brute force tactics, prompting security teams to investigate potential misuse of credentials.
9. Restrict Physical Access to Cardholder Data
Physical controls are often overshadowed by digital security, yet they are just as important. Unauthorized individuals who can physically reach servers or storage media might bypass even the strongest network defenses.
Control Entry to Sensitive Areas
Data centers, server rooms, and network closets containing cardholder data systems must have restricted access. Solutions include keycard locks, biometric scanners, or round-the-clock security personnel. A log of who enters and exits these critical areas helps detect suspicious or unauthorized visits.
Secure Media and Backups
Backup tapes, external hard drives, and other removable media may contain full dumps of cardholder data, making them exceptionally high-value targets for theft. Encrypting these media ensures data remains unreadable if lost or stolen. Tracking their movement via chain-of-custody documentation records who is responsible for them at any time.
Destroy Media Properly
When media or physical documents that store cardholder data become outdated or unnecessary, you must securely destroy them. Shredding paper records or using certified methods (e.g., degaussing or physically shredding disk drives) ensures criminals cannot recover the information. A documented destruction policy supports compliance with PCI DSS and other data protection regulations.
10. Track and Monitor All Access to Network Resources and Cardholder Data
A robust logging and monitoring framework is crucial for uncovering anomalies, investigating potential breaches, and meeting regulatory requirements for data security.
Enable System Logs
All critical endpoints, such as firewalls, intrusion detection/prevention systems, databases, and servers, should produce logs capturing relevant events such as authentication attempts, configuration changes, and data access. Granular logging may include recording what specific PAN was accessed and by whom, ensuring a comprehensive audit trail.
Use Centralized Log Management
Collecting logs in a centralized security information and event management (SIEM) solution simplifies correlation and analysis. Real-time analytics can flag patterns such as repeated failed logins across multiple systems or unexpected spikes in data access, helping you quickly detect potential breaches or misconfigurations. Additionally, storing logs for at least one year is mandated by PCI, and having three months instantly available helps with incident response.
Review and Alert
Log data is only useful if you actively review it. Regularly examining daily or weekly logs allows you to spot suspicious trends. Automated alerts via email, SMS, or integrations with ticketing systems can trigger immediate investigation. Quick responses to flagged events help contain possible intrusions before they escalate.
11. Regularly Test Security Systems and Processes
Periodic security testing validates your current controls, revealing gaps before malicious actors discover them. These tests should be both consistent and repeatable.
Perform Vulnerability Scans
Vulnerability scans, performed both internally and externally, identify missing patches, outdated libraries, and configuration weaknesses. Approved scanning vendors (ASVs) ensure external scans meet PCI DSS standards. Internal scans provide insight into potential problems within the perimeter, where a compromised machine might spread an attack laterally.
Conduct Penetration Tests
Penetration testing goes a step further by attempting to exploit detected vulnerabilities in a controlled scenario. Conducting these tests annually (or after significant infrastructure changes) ensures you can remedy any discovered weaknesses before attackers capitalize on them. If your organization relies on network segmentation to lower PCI scope, penetration tests should verify the effectiveness of isolation measures.
Deploy IDS/IPS and Wireless Scans
IDS and IPS systems guard your network in real time. By analyzing traffic patterns, they detect abnormal or malicious activities. Wireless network scans seek unauthorized devices or rogue access points, which can operate as hidden channels for data exfiltration or eavesdropping. Ensure that corporate Wi-Fi uses WPA2 or WPA3 encryption, rather than outdated standards like WEP.
12. Maintain a Policy That Addresses Information Security for All Personnel
The human factor plays a role in 68% of data breaches. Consequently, clear and well-enforced security policies form the bedrock of your security, guiding employees on correct practices and legal obligations.
Develop a Formal Security Policy
A dedicated IT security policy outlines the management’s vision, the scope of security measures, and the roles and responsibilities of every stakeholder. It should also define reporting channels, compliance requirements, and acceptable use policies. This authoritative document can be supplemented by supporting policies covering specific technical details or departmental requirements.
Train and Educate Employees
Even sophisticated technical controls fail if employees are not informed about common threats. Security awareness training covering phishing, social engineering, password hygiene, and incident reporting procedures ensures that staff remain vigilant. Role-specific training can be particularly helpful, for instance, developers learning secure coding principles or IT staff mastering correct system hardening techniques.
Oversee Vendors and Third Parties
When third-party vendors or service providers handle cardholder data on your behalf, their security practices directly affect your compliance status. Contracts should explicitly require PCI DSS adherence, and periodic security reviews or audits should validate alignment. Vendor management programs help you track who has access to your data and under what conditions, lessening the risk of unauthorized disclosures.
Create and Test an Incident Response Plan
An incident response plan defines what to do if a security incident occurs, delineating responsibilities, communication protocols, and escalation paths. Testing this plan (through tabletop exercises, red-teaming, or drills) reveals weaknesses in coordination, technology, or processes. Incorporating lessons learned from each test cycle helps the organization respond swiftly and effectively to incidents.
Strengthening Your PCI DSS Posture
Every organization faces unique risks and challenges, and adhering to core PCI DSS requirements is just the beginning. You can enhance your security further by implementing additional measures, such as network segmentation, continuous monitoring, meticulous documentation, and regular scope reviews.
Above all, remember that maintaining PCI compliance is not a one-time task but an ongoing commitment. Regularly reviewing and updating your policies, procedures, and technical configurations helps you stay aligned with best practices, keep pace with emerging threats, and protect your customers and your organization from potentially devastating data breaches.



