Choosing the correct type of firewall to protect your network is a vital security decision. Going with the wrong type is worse than having no firewall at all since you get a false sense of security despite the network being wide open to an attack.
So, what are the different types of firewalls you can deploy? And, more importantly, which one is the right option for your use case?
This article presents eight different types of firewalls that keep malicious traffic out of networks. We analyze the pros and cons of each solution, explain what OSI layer(s) they operate on, and offer tips for choosing a firewall that best meets your security requirements.

What Is a Firewall?
A firewall is a security device or program that monitors network traffic and detects potential threats. The main purpose of a firewall is to act as a barrier that allows non-threatening traffic in and keeps dangerous traffic out.
The scope of a firewall's protection varies between use cases. Security teams use firewalls to:
- Keep networks safe from external traffic sources (i.e., the Internet).
- Build "walls" around internal subnetworks (e.g., a firewall that prevents HR personnel from accessing a system reserved for the DevOps team).
- Set up traffic scanning on a single device (e.g., a firewall that protects a BYOD laptop from incoming traffic).
Firewalls are one of the bases of network security in the client-server model. These systems ensure both incoming and outgoing traffic is safe, but they are vulnerable to:
- Social engineering attacks (e.g., someone stealing a password and trying to commit CEO fraud).
- Insider threats (e.g., someone within the network intentionally changing firewall settings).
- Human mistakes (e.g., employee forgetting to turn the firewall on or ignoring update notifications).
While firewalls are a cybersecurity must-have, you require other mechanisms to remove threats reliably. Consider upgrading your firewall strategy with intrusion detection systems (IDSes), DDoS protection, and session monitoring.
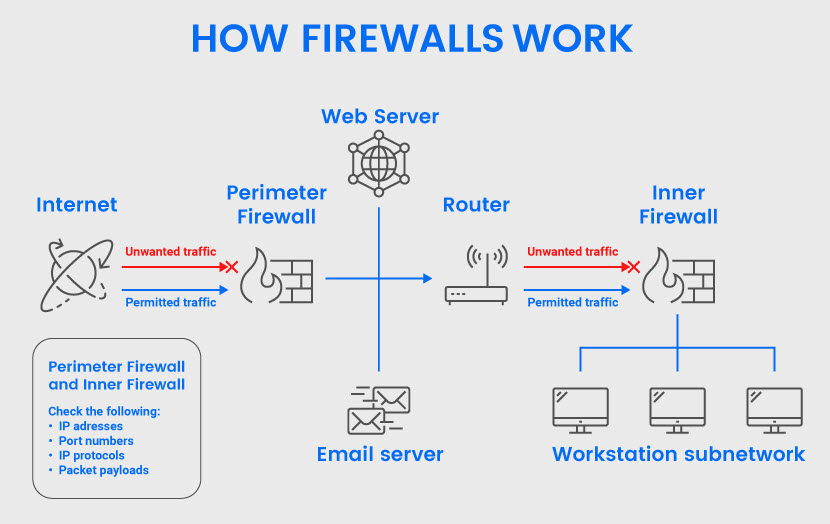
How Does a Firewall Work?
Teams set up a firewall inline across a network to act as a border between external sources and the guarded system. Admins create so-called choke points at which a firewall inspects all data packets entering and leaving the network. A packet is a piece of data formatted for Internet transfer that contains:
- The payload (the actual content).
- A header (info about the data, such as who sent it and to whom).
Firewalls analyze packets based on pre-set rules to distinguish between benign and malicious traffic. These rulesets dictate how the firewall inspects the following:
- Source and destination IP addresses.
- Content in the payload.
- Packet protocols (e.g., whether the connection uses a TCP/IP protocol).
- App protocols (HTTP, Telnet, FTP, DNS, SSH, etc.).
- Data patterns that indicate specific cyber attacks.
The firewall blocks all packets that do not abide by the rules and routes safe packets to the intended recipient. There are two options when a firewall prevents traffic from entering a network:
- Discard the request silently.
- Provide an error reply to the sender.
Both options keep dangerous traffic out of the network, so choose the one that makes more sense from a security standpoint. Typically, security teams prefer to drop requests silently to limit the info in case a would-be hacker is testing the firewall for potential vulnerabilities.
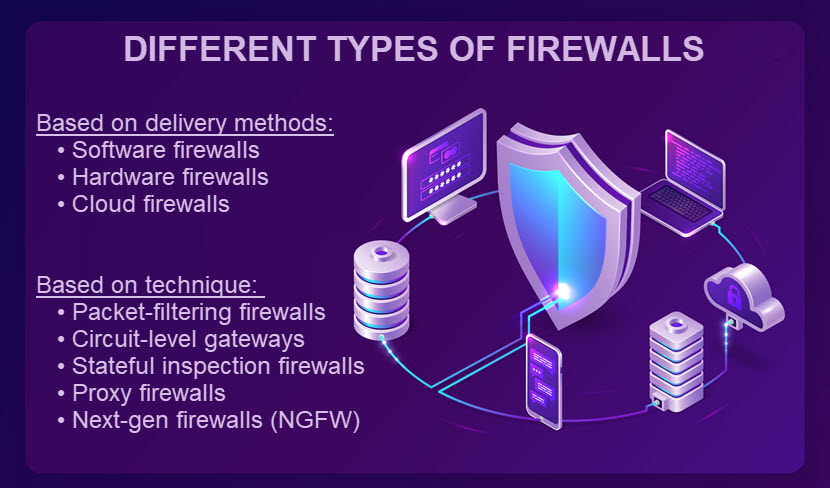
Types of Firewalls Based on Delivery Method
There are three types of firewalls based on how you decide to deploy them: hardware, software, and cloud-based firewalls. Let's see what each of these strategies offers.
Software Firewalls
A software firewall (or a host firewall) installs directly on the host device. This type of firewall protects only one machine (network endpoint, PC, laptop, server, etc.), so admins must install a version of the software on each device they want to protect.
Since admins attach a software firewall to a specific device, some resource usage is unavoidable. These firewalls inevitably eat up some system RAM and CPU, which is a deal-breaker for certain use cases.
Pros of software firewalls:
- Excellent protection for their assigned device.
- Isolate individual network endpoints from one another.
- Highly granular security in which an admin has complete control over allowed programs.
- Readily available.
Cons of software firewalls:
- Consume the device's CPU, RAM, and storage.
- Require configuration for each host device.
- Day-to-day maintenance is difficult and time-consuming.
- Not all devices are compatible with every firewall, so you may have to use different solutions within the same network.
Hardware Firewalls
A hardware firewall (or an appliance firewall) is a separate piece of hardware that filters traffic entering and coming out of a network. Unlike a software firewall, these self-contained devices have their own resources and do not consume any CPU or RAM from host devices.
For some SMBs, a hardware firewall is a bit of an overkill, and they might find more value in per-host software firewalls. Hardware firewalls are an excellent choice for larger organizations with several subnetworks containing multiple computers.
Pros of hardware firewalls:
- Protect multiple devices with one solution.
- Top-tier perimeter security as malicious traffic never reaches host devices.
- Do not consume resources of host devices.
- An admin manages only one firewall for the entire network.
Cons of hardware firewalls:
- More expensive than software firewalls.
- Insider threats are a considerable weakness.
- Configuration and management require more skill than software-based firewalls.
Cloud-Based Firewalls
Many providers offer cloud-based firewalls that they deliver on demand over the Internet. These services are also known as Firewall-as-a-Service and run either as IaaS or PaaS.
Since an MSP manages a cloud-based firewall, this option is excellent for:
- Highly distributed businesses.
- Teams with gaps in security resources.
- Companies without the necessary in-house expertise.
Like hardware-based solutions, cloud firewalls excel at perimeter security, but you can also set up these systems on a per-host basis.
Pros of cloud firewalls:
- The service provider handles all admin tasks (installation, deployment, patching, troubleshooting, etc.).
- Users are free to scale cloud resources to meet the traffic load.
- No need for any in-house hardware.
- High levels of availability.
Cons of cloud firewalls:
- A lack of transparency regarding exactly how the provider runs the firewall.
- Like other cloud-based services, these firewalls are difficult to migrate to a new provider.
- Traffic flows through a third party, which raises latency and privacy concerns.
- Expensive in the long run due to steep OpEx.
There's no reason to pick one type of deployment and rely solely on that setup. For example, you could set up a hardware or cloud firewall at the network perimeter while also having software firewalls on high-value hosts.
Types of Firewalls Based on Method of Operation
Below is an in-depth look at the five types of firewalls based on their function and the OSI layer. You can deploy any of them as hardware, software, or in the cloud.
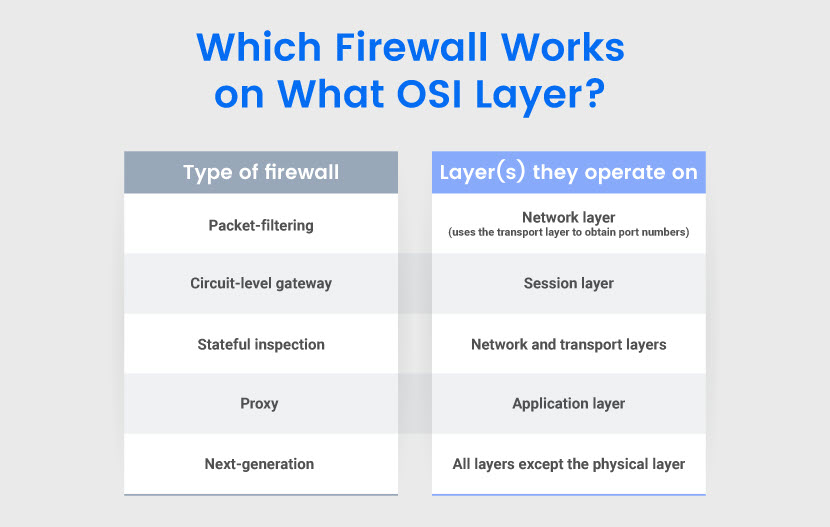
Packet-Filtering Firewalls
Packet-filtering firewalls act as a checkpoint at the network layer and compare each packet's header info to a set of pre-established criteria. These firewalls check the following header-based info:
- Destination and origination IP addresses.
- Packet type.
- Port number.
- Network protocols.
These types of firewalls only analyze surface-level details and do not open the packet to examine its payload. A packet-filtering firewall examines each packet in a vacuum without considering existing traffic streams.
Packet-filtering firewalls are ideal for small organizations that require a basic level of security against well-established threats.
Pros of packet-filtering firewalls:
- A low-cost solution.
- Fast packet filtering and processing.
- Excellent at screening traffic between internal departments.
- Low resource consumption.
- Minimal impact on network speed and end-user experience.
- Enables complex security policies through filtering on packet headers.
- An excellent first line of defense in a multi-layered firewall strategy.
Cons of packet-filtering firewalls:
- No checks of packet payloads (the actual data).
- Easy to bypass for an experienced hacker.
- Incapable of filtering at the app layer.
- Vulnerable to IP spoofing attacks since it processes each packet in isolation.
- No user authentication or logging features.
- Access control lists are challenging to set up and manage.
Circuit-Level Gateways
Circuit-level gateways operate at the session OSI layer and monitor TCP (Transmission Control Protocol) handshakes between local and remote hosts.
This simplistic firewall type quickly approves or denies traffic without consuming a lot of resources. However, these systems do not inspect packets, so even malware-infected requests get access if there's a proper TCP handshake.
Pros of circuit-level gateways:
- Only process requested transactions and reject all other traffic.
- Simple to set up and manage.
- Resource and cost-efficient.
- Strong protection against address exposure.
- Minimum impact on end-user experience.
Cons of circuit-level gateways:
- Not a stand-alone solution as there's no content filtering.
- Often requires software and network protocol tweaks.
Stateful Inspection Firewalls
A stateful inspection firewall (or dynamic packet-filtering firewall) monitors incoming and outgoing packets at the network and transport layers. This firewall type combines packet inspection and TCP handshake verification.
Stateful inspection firewalls maintain a table database that tracks all open connections and enables the system to check existing traffic streams. This database stores all key packet-related info, including:
- The source IP.
- Source port.
- Destination IP.
- Destination port for each connection.
When a new packet arrives, the firewall checks the table of valid connections. Familiar packets go through without further analysis, while the firewall evaluates non-matching traffic according to the pre-set ruleset.
Pros of stateful inspection firewalls:
- Consider previously inspected packets while filtering traffic.
- Excellent at stopping attacks that aim to exploit protocol flaws.
- Do not open numerous ports to allow traffic in or out, as this shrinks the attack surface.
- Detailed logging capabilities that help in digital forensics.
- Reduced exposure to port scanners.
Cons of stateful inspection firewalls:
- More expensive than packet-filtering firewalls.
- Require a high degree of skill to set up correctly.
- Often take a toll on performance and lead to network latency.
- No authentication support for validating spoofed traffic sources.
- Vulnerable to TCP flood attacks that take advantage of pre-established connections.
Proxy Firewalls
A proxy firewall (or application-level gateway) serves as an intermediate between internal and external systems. These firewalls protect a network by masking client requests before sending them to the host.
Proxy firewalls operate at the app layer, the highest level of the OSI model. These systems have deep packet inspection (DPI) capabilities that check both payloads and headers of incoming traffic.
When a client sends a request to access a network, the message first goes to the proxy server. The firewall checks the following:
- Previous communications between the client and devices behind the firewall (if any).
- Header info.
- The content itself.
The proxy then masks the request and forwards the message to the web server. This process hides the client's ID. The server responds and sends the requested data to the proxy, after which the firewall passes the info to the original client.
Proxy firewalls are the go-to option for businesses trying to secure a web application from malicious users. These systems are also popular when a use case requires network anonymity.
Pros of proxy firewalls:
- DPI that checks both packet headers and payloads.
- Add an extra layer of separation between clients and your network.
- Conceal internal IP addresses from potential threat actors.
- Detect and block attacks invisible at the OSI model network layer.
- Fine-grained security controls over network traffic.
- Unlock geolocational restrictions.
Cons of proxy firewalls:
- Increased latency due to thorough packet checks and extra communication steps.
- Not as cost-effective as other types of firewalls due to high processing overhead.
- Challenging to set up and manage.
- Not compatible with every network protocol.
Next-Generation Firewalls
A next-generation firewall (NGFW) is a security device or program that combines several functions of other firewalls. Such a system offers:
- Deep packet inspection that analyzes the traffic's content.
- TCP handshake checks.
- Surface-level packet inspection.
Next-gen firewalls also include additional network security measures, such as:
- IDSes and IPSes.
- Malware scanning and filtering.
- Advanced threat intelligence (pattern matching, protocol-based detections, reputation-based malware detection, anomaly-based detections, etc.)
- Antivirus programs.
- Network Address Translation (NAT).
- Quality of service (QoS) features.
- Secure Shell (SSH) inspection.
NGFWs are a common choice in heavily regulated industries, such as healthcare or finance. Companies that must adhere to HIPAA and PCI are the usual adopters.
Pros of next-generation firewalls:
- Combine traditional firewall features with advanced cybersecurity capabilities.
- Inspect network traffic from the data link layer to the app layer (layers 2-7 in the OSI model).
- Substantive logging capabilities.
Cons of next-generation firewalls:
- More expensive than other firewalls.
- A massive single point of failure.
- Slow deployment time.
- Require a high degree of expertise to set up and run.
- Hindered network performance.
Like with delivery models, nothing is stopping you from using multiple types of firewalls at the same time. Companies often set up several firewalls in the same network and deploy them at different levels.

Which Firewall Type is Right for Your Business?
No two businesses have the same assets, networks, and risk tolerance, so every company has unique firewall needs. The main questions to answer when choosing a firewall type are:
- What kind of network are you trying to keep safe?
- How valuable are the assets you're trying to protect? Is there anything mission-critical?
- What's the allocated budget for the project?
- What are the technical objectives of the firewall?
- How big is the network? How many hosts are there?
- What kind of traffic will the firewall face? Will the load be consistent?
- Do you require a firewall on each host device?
- Does your team have hands-on experience with setting up and using a particular firewall type?
- What kind of traffic inspection do you need?
- How do different types of firewalls fit into your current app architecture?
- Are you ready to make infrastructure changes if necessary?
- How much (if any) latency can you afford to introduce with the new firewall?
- Do you have any compliance-related rules to consider? How about data privacy or protection laws?
- How much time can your team set aside for firewall management?
Answers to these questions help identify the right firewall option. Here are a few extra tips to help you out:
- Perform in-depth threat modeling before deciding on the right firewall type.
- Try to align your choices with the team's experience.
- Consider more cost-effective options first (i.e., do not go for a full-blown NGFW if a simple packet-filtering firewall would do the job).
- Ensure the new firewall does not slow down the network to a point where it impacts the end-user experience.
- Do not rely solely on packet-filtering and stateful inspection firewalls if you require protection at the app layer.
- Use firewalls to boost your network segmentation strategy.
A smart strategy when choosing a firewall is to start by analyzing your weaknesses. Learn how to perform a network security audit that thoroughly examines the current state of your network.
Understand What Different Types of Firewalls Offer
A firewall serves as the first line of defense against potential breaches to your company. These systems have the potential to make or break a security strategy, so treat their selection and setup accordingly.
Know what different types of firewalls offer and how they keep assets safe before you go all-in on a solution. Understanding their capabilities ensures you choose a firewall that aligns with your organization’s specific security needs and risk profile.