Network breaches are inevitable, and every organization must be prepared to withstand a break-in. Among many cybersecurity mechanisms, network segmentation stands out for its effectiveness in limiting damage during a breach. If the system is compromised, this powerful technique restricts the damage intruders can inflict.
This article will explore the security benefits of network segmentation. We will explain how multi-layer protection can resist attacks and why segmentation is more reliable than flat network structures.

What Is Network Segmentation?
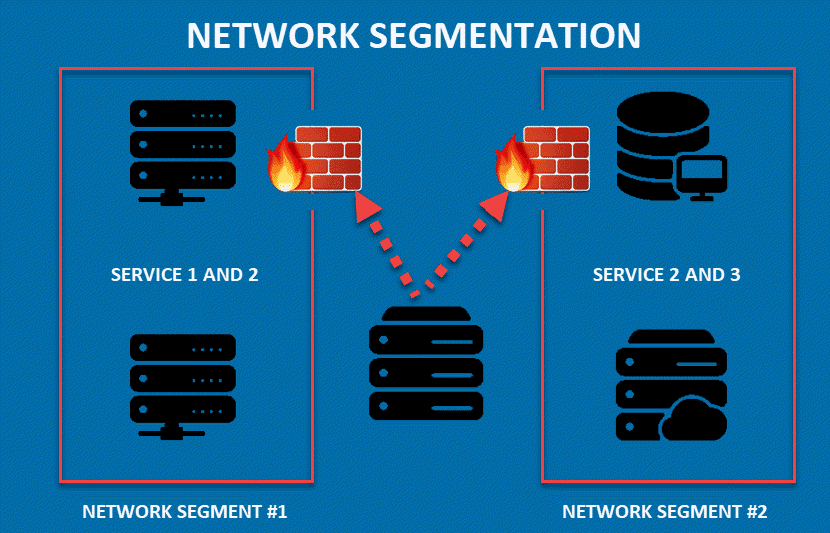
Network segmentation is a cybersecurity practice that divides a computer network into smaller, isolated segments or subnetworks. This process is achieved by placing barriers between parts of the system that do not need to interact directly. For example, a company can create a subnet for its printers or a segment reserved for storing sensitive data. Each segment is an independent unit with unique access controls and network security measures.
Once a network is segmented, every subnet operates independently, allowing precise control over data traffic between sections. Network engineers can stop all traffic in one segment from reaching another and filter data flow by traffic type, source, or purpose. This isolation limits a threat’s ability to move freely through the system. If a section of the network experiences a data breach, other segments remain secure.
Think of your network like a building. If the entire building is open and accessible, any breach can quickly escalate and affect everything inside. By creating separate rooms (or segments), you can control access more effectively, limit the spread of potential issues, and protect critical areas.
Network Segmentation vs. Segregation
Network segmentation enhances security within an interconnected network by creating manageable segments. Network segregation ensures maximum security by isolating critical systems entirely, preventing any interaction with less secure network areas.
For example, a company might segregate its internal corporate network from an external guest network or isolate critical infrastructure systems from the main IT network. Segregation minimizes the risk of cross-network contamination or attacks by blocking interaction between segregated networks. This approach is simpler to implement than segmentation but offers less operational flexibility.
Network Segmentation Methods
Below are the main network segmentation methods. They provide various levels of security and flexibility, allowing you to select the approach that best meets your needs. They are not mutually exclusive and are, in fact, often used in combination.
Physical Segmentation
Physical segmentation involves using dedicated hardware, such as switches and routers, to create completely separate networks. This method ensures that different segments have no physical connections, providing the highest level of isolation and security.
Virtual Segmentation
Virtual segmentation uses virtual local area networks (VLANs) to logically divide a single physical network into multiple distinct networks. Each VLAN operates as an independent network, although they share the same physical infrastructure.
VLANs are configured on network switches and routers to control traffic flow between segments, enhancing security and reducing the risk of lateral movement by attackers.
Intent-Based Segmentation
Intent-based segmentation defines and enforces network policies based on business intent and requirements. This method uses advanced software-defined networking (SDN) technologies to dynamically create and manage network segments according to predefined policies.
Intent-based segmentation allows for more granular control and automation, adapting to changing business needs and security requirements.
Microsegmentation
Microsegmentation is a granular approach to network segmentation that involves creating highly specific, isolated segments down to the individual workload or application level. This method uses software-defined networking and security policies to control traffic between microsegments, providing fine-tuned security and reducing the attack surface.
Internal Segmentation
Internal segmentation divides the internal network into isolated segments to protect sensitive data and critical systems from insider threats. This method uses internal firewalls, access control lists (ACLs), and network monitoring to control traffic between segments, enhancing security and reducing the risk of internal attacks.
Cloud Segmentation
Cloud segmentation involves dividing cloud environments into isolated segments to enhance security and compliance. This method uses cloud-native security controls and policies to create and manage segments within cloud platforms.
Hybrid Segmentation
Hybrid segmentation combines multiple segmentation methods to create a comprehensive security strategy that spans on-premises, cloud, and hybrid environments. This approach leverages the strengths of different segmentation techniques to provide robust security and flexibility.
phoenixNAP brings together microsegmentation, machine learning, and behavioral analytics in the world’s most secure cloud platform – Data Security Cloud.
How Does Network Segmentation Work?
Here are the primary techniques for network segmentation:
- Virtual local area networks. VLANs logically separate network traffic at the data link layer (Layer 2). Each VLAN creates a distinct broadcast domain, configured through network switches. Traffic between VLANs is managed and routed by Layer 3 devices, such as routers or Layer 3 switches. VLANs are particularly useful for segmenting traffic within a single physical network, enabling isolation and security without additional hardware.
- Subnetting. This technique divides a network into smaller, manageable parts at the IP layer (Layer 3). Each subnet receives a segment of the network's overall IP address range and operates independently. Subnetting enhances both security and performance by isolating network traffic and reducing broadcast domains. It also allows for more granular control over routing and access policies within an IP network.
- Firewalls. Firewalls are crucial for enforcing network segmentation. They function as barriers between segments, allowing only authorized traffic to pass through based on predefined security rules. Firewalls can be configured to inspect traffic at various layers (Layer 3 and above), providing deep packet inspection, application-aware filtering, and intrusion prevention. These measures ensure only legitimate traffic moves between segments, effectively isolating threats.
- Access control lists. Implemented on routers and switches, ACLs specify the traffic rules that govern movements between segments. ACLs filter traffic based on IP addresses, protocols, ports, and other criteria, ensuring only permitted interactions occur. They are essential for controlling access to network resources and enforcing security policies at the network perimeter and within internal segments.
- Software-defined networking. SDN provides dynamic and flexible network segmentation using software-based policies to manage and direct network traffic flows. SDN decouples the control plane from the data plane, allowing centralized management of network behavior. This level of control enables rapid reconfiguration of network segments in response to changing security needs, application requirements, or network conditions. SDN controllers also automate policy enforcement, optimize traffic flows, and enhance visibility across the network.
Network Segmentation Examples
Here are examples of how you can implement network segmentation.
Physical Segmentation
If you operate a manufacturing company, you can protect your industrial control systems by setting up a separate network infrastructure from your corporate IT network. Use dedicated switches and routers to ensure no physical connections between these networks. This isolation protects critical operational systems from cyber threats originating from the corporate network.
Virtual Segmentation
As a university administrator, you can use VLANs to separate network traffic for administrative offices, student dormitories, and guest Wi-Fi access. By configuring VLANs on your network switches, you can ensure that traffic from the guest network does not access the administrative network. This setup protects sensitive student records and administrative data while maintaining operational flexibility.
Intent-Based Segmentation
For financial institutions, intent-based segmentation can dynamically manage access to sensitive financial applications. With software-defined networking, you can establish policies that automatically segment network traffic by user roles and device types. For instance, you can allow only authorized financial analysts to access trading platforms while restricting other employees to general business applications. This approach ensures that sensitive financial data is accessible only to those with appropriate permissions.
Microsegmentation
If you run a technology company, implement microsegmentation within your data center to isolate individual applications. Each application can run in its own microsegment, with strict security policies controlling traffic between segments. For example, configure a web server to communicate only with the application server it supports, ensuring both can only access the specific database they need.
Internal Segmentation
As a healthcare provider, you can protect patient records by using internal segmentation to separate networks for different departments. Isolate the billing department's network from the network used by medical staff to access patient records. Use firewalls and access control lists to ensure only authorized personnel can access sensitive medical information.
Cloud Segmentation
A software development company can use cloud segmentation to separate development, testing, and production environments in the cloud. Isolating these environments prevents accidental exposure of sensitive data and ensures that experimental code changes do not impact live services. Cloud-native security controls and policies enforce this separation, enhancing security and compliance.
Hybrid Segmentation
If you manage a retail chain, you can implement hybrid segmentation by combining physical, virtual, and cloud segmentation methods. Physically segment your point-of-sale (POS) systems from the corporate network. Use VLANs to separate customer Wi-Fi from internal systems and employ cloud segmentation to protect your ecommerce platform.

Benefits of Network Segmentation
Network segmentation provides several advantages:
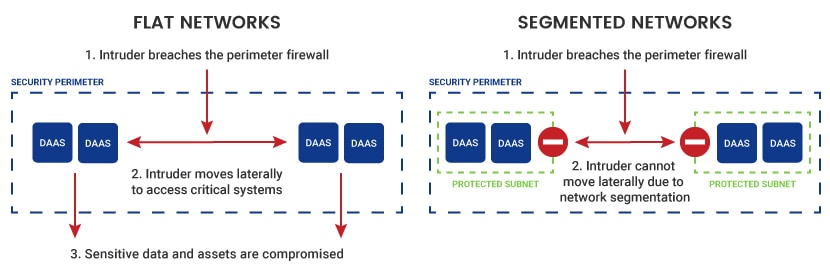
- Enhanced security. Segmenting a network limits the spread of malware and restricts unauthorized access. If one segment is compromised, the breach is contained, preventing lateral movement across the network.
- Improved performance. Dividing a network into smaller segments reduces traffic within each segment, minimizing congestion, improving bandwidth efficiency, and enhancing overall network performance.
- Regulatory compliance. Many regulations and standards, such as PCI DSS, HIPAA, and GDPR, mandate strict controls over sensitive data. Network segmentation helps organizations meet these requirements by isolating and protecting regulated data.
- Simplified management. Segmentation enables more manageable and focused security policies. Network administrators can tailor security measures and access controls to the needs of each segment.
- Reduced attack surface. Segmenting the network reduces the number of potential entry points for attackers, making it harder to penetrate the network and limiting the potential damage of successful attacks.
- Business continuity. In a network breach, segmentation ensures that unaffected segments continue to operate normally, reducing downtime and maintaining business continuity.
Network Segmentation Challenges
Implementing network segmentation presents the following challenges:
- Implementation complexity. Designing and executing an effective segmentation strategy requires a deep understanding of your network architecture, critical assets, and traffic patterns.
- An incorrectly implemented and configured segmentation creates security gaps and vulnerabilities.
- Cost considerations. Network segmentation requires investing in additional hardware, software, and network security tools. Additionally, maintaining multiple network segments increases administrative overhead, as each segment requires ongoing monitoring, updates, and management.
- Balancing security and usability. Over-segmentation leads to unnecessary complexity and hinders legitimate business processes, while under-segmentation leaves the network vulnerable to attacks.
- Integration with existing systems. Integrating segmentation strategies with existing network infrastructure and security systems requires thorough planning and execution to avoid compatibility issues and ensure seamless integration.
When to Segment a Network?
The primary reason to segment a network is proactive risk management. There is no one-size-fits-all answer to whether it is necessary for your organization.
When deciding, consider these key factors:
- Data sensitivity. This is the most critical factor. Segmentation is essential if your organization handles highly sensitive information like financial and medical records. Isolating and protecting this data reduces the risk and potential impact of a breach.
- Compliance requirements. Many industries face strict data security and privacy laws. Network segmentation helps you comply by demonstrating you have taken appropriate measures to protect sensitive data.
- Network size and complexity. Large and complex networks with many devices and users are inherently more vulnerable. Segmentation simplifies security management by dividing the network into smaller, more manageable sections, allowing you to implement different security controls for each segment based on its risk profile.
- Threat landscape. Consider the types of threats your organization faces. If you're a target for sophisticated cyberattacks and advanced persistent threats, segmentation is an additional security layer.
Network Segmentation: Best Practices
Here are the key best practices for implementing network segmentation:
Understand and Classify Network Assets
To effectively segment your network, you must know the assets within it.
- Asset inventory. Utilize automated asset discovery tools to maintain an up-to-date inventory of all network assets, including servers, applications, devices, and endpoints.
- Data classification. Implement a data classification scheme based on sensitivity, confidentiality, and regulatory requirements. Tools like data loss prevention (DLP) solutions help identify and classify sensitive data across the network.
Develop Clear Segmentation Policies
Clear and well-documented policies are crucial for effective network segmentation.
- Policy development. Develop comprehensive network segmentation policies that outline the criteria for segmenting the network. These should include guidelines for access controls, data flow rules, and security protocols for each segment.
- Role-based access control (RBAC). Implement RBAC by mapping out user roles and assigning permissions based on the principle of least privilege. Use identity and access management (IAM) solutions to enforce these controls across the network.
Select Appropriate Segmentation Methods
Choosing and combining the proper segmentation methods is key to building a robust architecture.
- Layered approach. Utilize multiple segmentation techniques, including VLANs, microsegmentation, and physical segmentation, to establish a layered defense. For example, combine VLANs for logical separation within a physical network and microsegmentation for isolating workloads within data centers.
- Dynamic segmentation with SDN. Implement SDN to manage and automate network segmentation dynamically. SDN controllers are capable of creating, modifying, and removing segments in real time according to predefined security policies, enabling rapid adaptation to evolving needs and conditions.
Implement Strong Access Controls
Strong access controls are necessary to protect segmented networks.
- Firewall configuration. Deploy next-generation firewalls (NGFWs) at the boundaries of each segment. Configure them to enforce deep packet inspection, application-aware filtering, and intrusion prevention. Use firewall rules to control traffic flow between segments tightly.
- Network access control (NAC): Use NAC solutions to enforce endpoint security policies and control device access to network segments. NAC can validate device compliance with security standards before granting access to the network.
Continuous Monitoring and Management
Monitoring and management ensure the continuing effectiveness of network segmentation.
- Security Information and Event Management (SIEM). Deploy SIEM systems to collect and analyze logs from firewalls, switches, routers, and endpoints across all segments. SIEM systems also provide real-time alerts for suspicious activities, aiding in the detection of potential security incidents.
- Network traffic analysis (NTA). Use NTA tools to monitor traffic patterns within and between segments. These tools can detect anomalies, such as unusual data transfers or access attempts, which may indicate a security breach.
- Regular audits. Conduct regular network security audits and vulnerability assessments on each network segment. Utilize automated tools to identify misconfigurations, unpatched systems, and compliance issues.
Prepare for Incident Response
Effective incident response planning is critical for managing cyber incidents within segmented networks.
- Segmentation for response. Design network segments to enable quick isolation during an incident. For example, use SDN to create quarantine segments where compromised devices can be moved for investigation.
- Incident response plan. Develop and regularly update an incident response plan that outlines detailed procedures for detecting, isolating, and mitigating breaches within segmented networks. Ensure the plan includes coordination with third-party security services if needed.
Optimize Network Performance
Optimizing network performance is essential for maintaining efficiency.
- Traffic analysis tools. Use network performance monitoring tools to analyze traffic patterns and identify bottlenecks continuously. Implement quality of service (QoS) policies to prioritize critical traffic and ensure efficient data flow.
- Load balancing. Deploy load-balancing solutions to distribute traffic evenly across network segments. This helps prevent congestion and ensures that resources are utilized effectively.

Network Segmentation vs. Zero-Trust Network Access (ZTNA)
Network segmentation and zero-trust network access (ZTNA) are complementary strategies. While network segmentation aims to divide and isolate network segments to limit threats, ZTNA focuses on continuous verification and enforces strict access controls for each access request. Integrating both methods provides a robust, multi-layered security framework for network and data protection.
The table below compares network segmentation and ZTNA.
| Network segmentation | Zero-trust network access | |
| Primary objective | Divide a network into smaller, isolated segments to enhance security and manageability. | Ensure that no user or device is trusted by default, regardless of their location. |
| Security philosophy | Organizes the network into segments based on criteria such as device type, department, and other relevant factors. | Assumes all users and devices are potentially compromised and verifies each request. |
| Implementation focus | No inherent trust is given; verification is required for every access attempt. | Focuses on securing access to resources based on strict identity verification. |
| Traffic control | Controls traffic at network boundaries using firewalls, VLANs, and ACLs. | Controls access to applications and services on a need-to-know basis using policies. |
| User/Device trust | Trust is based on the segment’s security posture. | Environments where the separation of different network areas is vital. |
| Operational complexity | Can become complex depending on the size and number of segments. | High due to the continuous verification processes and dynamic policy management. |
| Technology used | Firewalls, VLANs, subnetting, ACLs, and SDN. | Identity and access management (IAM), multi-factor authentication (MFA). |
| Use case | Environments where the separation of different network areas is vital. | Environments that require strict access control. |
Zero-trust security is an effective strategy for protecting large networks from advanced cyber threats. Read our article to learn how it works and what benefits it offers
The Power of Network Segmentation in Modern Cybersecurity
Network segmentation has long been a cornerstone of effective cybersecurity because it reduces the attack surface and isolates key assets. It remains an essential solution, even against increasingly sophisticated threats.
However, to fully leverage the benefits of network segmentation, consider complementing it with continuous monitoring, regular audits, and an updated IT security policy. Implementing these additional measures helps ensure that segmentation remains effective and adaptive to evolving threats.



