Cybersecurity analysts constantly face a barrage of threats. Legacy security tools, often siloed and lacking integration, generate hundreds of false positive alerts daily. This overwhelming workload leads to security staff burnout and hinders effective threat response.
Security information and event management (SIEM) systems ingest and analyze data from diverse sources, allowing them to identify patterns and anomalies that individual tools might miss. They also prioritize alerts, reducing analyst fatigue and enabling them to focus on the most critical threats.
This article explains how SIEM improves your organization's security and equips you with the knowledge to choose and implement the right solution.

What Is Security Information and Event Management?
A SIEM system is a centralized platform that collects data from various sources, such as applications, network devices, and security tools. It analyzes this data to identify suspicious activity, prioritize threats, and facilitate efficient incident response.
SIEM systems offer organizations a unified view of their security posture by consolidating logs, threat intelligence feeds, vulnerability data, and network and endpoint response activities. This comprehensive overview enables them to streamline detection, analysis, and response to threats.
The effectiveness of SIEM is rooted in its capacity to intelligently process vast volumes of data. SIEM tools effectively filter through and correlate diverse data sets in real time by leveraging artificial intelligence, machine learning, and big data analytics.
What Does Security Information and Event Management Do?
Here are the core functions of a SIEM system:
- Data aggregation. SIEM systems collect and aggregate log data from various sources across an organization’s IT infrastructure. This enables them to function as a centralized platform for analyzing and storing security-related information.
- Alerting. Upon detecting a potential threat, SIEM systems generate real-time alerts, enabling security teams to swiftly address and mitigate cyber incidents.
- Event correlation. SIEM systems correlate events from these varied data sources. By leveraging predefined rules and patterns of known threats, SIEM platforms uncover complex patterns that signal potential security threats or data breaches, offering insights that might otherwise remain hidden.
- Dashboards. Visual dashboards are the cornerstone of SIEM solutions. They help security professionals identify trends, patterns, and anomalies that warrant further investigation.
- Forensic analysis. In the aftermath of a security incident, SIEM is an invaluable tool for forensic analysis. By offering access to detailed historical data on security incidents, SIEM enables investigators to trace the origins of a breach, assess its impact, and derive lessons to fortify security measures against future threats.
- Compliance reporting. SIEM platforms support compliance efforts by generating detailed reports that document adherence to regulations, simplifying the audit process, and ensuring the organization meets regulatory requirements.
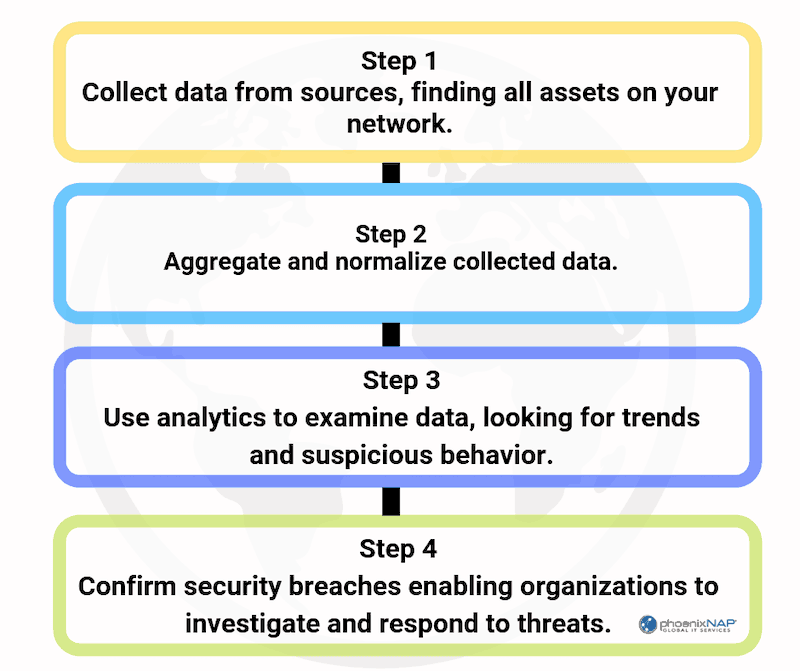
What Are the Types of SIEM?
There are three primary types of SIEM solutions: on-premises, cloud-based, and hybrid. Each type offers distinct advantages and disadvantages.
On-Prem SIEM
On-premises SIEM solutions are deployed and managed within an organization's physical facilities. They offer maximum control over the security environment, making them ideal for organizations with stringent data control and privacy requirements.
Advantages:
- Full control over data and security configurations.
- Easier to comply with regulatory requirements that mandate data to remain on-site.
- No dependency on external service providers.
Disadvantages:
- Higher upfront costs for hardware and software.
- Potential scalability issues as the organization grows.
- Requires in-house expertise for maintenance and management.
Cloud-Based SIEM
Cloud-based SIEM solutions leverage the provider's cloud computing infrastructure for scalability and ease of management. This deployment type suits organizations looking for cost-effective, flexible solutions that can easily scale with their growing data security needs.
Advantages:
- Lower initial costs and reduced need for in-house infrastructure.
- Managed by the service provider, reduces the need for in-house expertise.
- High scalability and flexibility.
Disadvantages:
- Potential concerns over data privacy and cloud security.
- Possible latency issues depending on network conditions.
- Dependency on the service provider for uptime and performance.
Hybrid SIEM
Hybrid SIEM solutions combine on-premises and cloud-based elements, allowing organizations to keep sensitive data on-premises while utilizing the cloud for scalability and efficiency. This option is ideal for businesses in transition or with varied operational environments.
Advantages:
- Balances control and flexibility by combining the benefits of both on-premises and cloud-based solutions.
- Allows for gradual migration to the cloud.
- Accommodates varied security and compliance requirements.
Disadvantages:
- Complexity in managing and integrating both on-premises and cloud components.
- Requires careful planning to ensure seamless data flow and security across environments.
- Potential for increased costs due to the need for dual infrastructure.
Choosing between on-site servers and cloud storage for your data and workloads is a challenge, as both approaches have advantages and disadvantages.
Read our comparison of on-premises vs. cloud computing to make an informed decision.
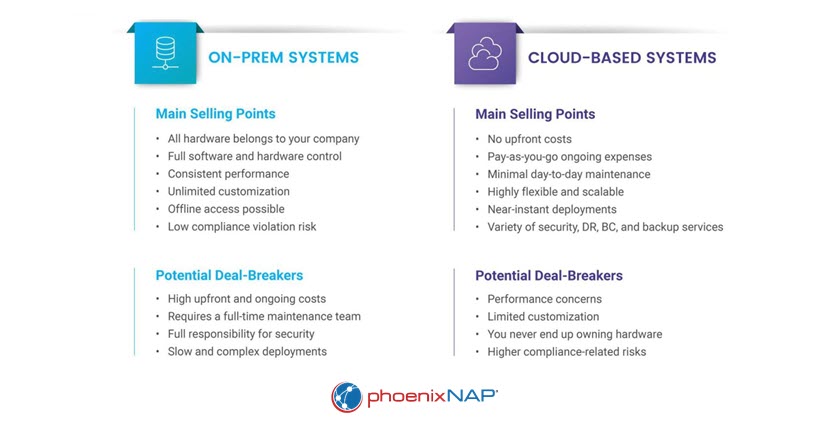
Security Information and Event Management Components
Here are the components of a SIEM system:
- Data ingestion layer. Collects logs and events from various sources within the organization, such as servers, network devices, and applications. It ensures all relevant data is captured in real time and forwarded to the SIEM system for further processing.
- Data storage layer. Stores the processed events and logs, making data available for querying and analysis. This layer includes a database or data warehouse optimized for real-time and historical data analysis.
- Data processing layer. Parses, normalizes, and enriches the collected data to prepare it for analysis. It includes a parsing and normalization engine that extracts relevant fields from raw data and formats them consistently.
- Analysis layer. Analyzes the collected data to identify patterns, trends, and anomalies that indicate security threats or policy violations. It includes a correlation engine that uses rules, statistical analysis, and machine learning to identify threats.
- Alerting and notification layer. Generates alerts based on the analysis results and notifies security staff. It includes alert generation based on analysis findings, alert prioritization based on severity and relevance, and a system that sends alerts via email, SMS, or ticketing systems.
- Integration layer. Integrates the SIEM system with other security tools, IT systems, and third-party services to ensure seamless operation with the organization's existing infrastructure.
- User interface layer. Provides a visual interface for users to interact with the SIEM system. It includes dashboards that visualize data, alerts, and trends with customizable widgets.
- System management layer. Manages the SIEM system's configuration, users, and overall health to ensure it operates correctly.
SIEM Use Cases
Here are the use cases for SIEM systems:
- Advanced threat detection. By leveraging machine learning to analyze vast datasets, SIEM systems uncover complex threats like zero-day exploits and polymorphic malware. They achieve this by uncovering hidden correlations and subtle anomalies that might evade traditional security solutions.
- Centralized log management. By automating the collection, parsing, and normalization of logs from diverse sources such as network devices, servers, and applications, SIEM systems bring uniformity to log management. This consistency simplifies the analysis process and ensures comprehensive visibility across the IT infrastructure.
- Covert communication discovery. SIEM systems help to block cybercriminals’ efforts to remain undetected within the network. By applying complex correlation rules and analytics to identify anomalies, these systems detect attackers' attempts to use encrypted channels or other covert methods for data exfiltration.
- Protocol anomaly detection. Analyzing protocol behavior enables SIEM systems to detect deviations from established network baselines, thereby identifying potential security issues or configuration errors that could expose vulnerabilities.
- Cyberwarfare defense. SIEM systems play a critical role in cyberwarfare by identifying the tactics, techniques, and procedures used in such attacks. This capability enables security teams to effectively recognize and counteract sophisticated threats, including advanced persistent threats (APTs).

How to Implement SIEM?
Below is a detailed strategy for implementing a security information and event management solution, structured to guide you through each phase of the process.
1. Define Objectives and Requirements
Before deploying the SIEM solution, it's essential to gain a clear understanding of your objectives and the specific requirements of your IT environment.
- Identify security goals. Clearly outline your primary security objectives to guide the SIEM selection and deployment strategy.
- Assess your environment. Conduct a thorough evaluation of your IT infrastructure to understand the data sources and volumes the SIEM will manage.
- Determine compliance needs. Identify all relevant regulatory compliance standards your organization is subject to. Start by pinpointing relevant regulations, such as HIPAA (healthcare data in the U.S.), PCI DSS (payment processing), or GDPR (personal data in the EU).
2. Choose the Right SIEM Solution
Selecting a SIEM solution that aligns with your organization's needs is crucial for effective deployment and operation:
- Consider deployment options. Decide on the most suitable deployment model - on-premises, cloud-based, or hybrid.
- Evaluate features. Review and compare the features of different SIEM solutions to find one that matches your requirements.
- Scalability and performance. Ensure the SIEM solution can scale with your organization's growth and efficiently manage the expected data volume.
3. Plan and Design the Deployment
Once you have chosen a SIEM solution, the next step is to plan its integration into your environment, taking into consideration all the necessary components:
- Design the architecture. Describe how the SIEM will integrate into your existing network and security infrastructure.
- Map data sources. List all the data sources within your organization that will feed into the SIEM.
- Define policies and procedures. Create specific policies for managing logs, responding to incidents, and defining user access within the SIEM system.
4. Implement the SIEM Solution
Implementing the SIEM involves setting up the system, integrating data sources, and configuring initial data processing and analysis settings:
- Deploy and configure. Install the SIEM software in your environment and configure it according to your security needs.
- Set up correlation rules. Establish initial correlation rules to enable the SIEM to identify potential security events effectively.
- Integrate data sources. Ensure all identified data sources are properly connected to the SIEM and that data is correctly ingested.
5. Tune and Optimize
After the SIEM is up and running, continuous tuning and optimization are necessary to maintain its effectiveness and efficiency:
- Optimize performance. Monitor the SIEM's performance and make necessary adjustments to efficiently handle data processing and analysis.
- Fine-tune correlation rules. Regularly adjust correlation rules to reduce false positives and ensure accurate threat detection.
- Continual learning. Use insights from security operations to refine the SIEM setup, improving its effectiveness over time.
6. Train Staff and Establish Processes
SIEM systems are powerful weapons, but they are not magic bullets. They are a force multiplier for your expertise. Ensuring your team is well-prepared to use the SIEM system effectively is as important as the technical setup:
- Develop incident response processes. Draft and implement clear processes for responding to alerts generated by the SIEM.
- Training. Provide training for security analysts and relevant staff on using the SIEM system.
7. Maintain and Review
SIEM deployment is an ongoing process that requires regular maintenance and reviews to stay effective:
- Continuous improvement. Periodically review the SIEM's operations to identify opportunities for improvement and adapt to evolving challenges.
- Regular maintenance. Keep the SIEM system updated with the latest software patches and updates to ensure optimal performance and security.

Security Information and Event Management Tools
The SIEM market offers a range of options, from paid solutions to open-source platforms. Each option has unique strengths and is suited to different organizational contexts.
Free SIEM Tools
Open source SIEM tools are ideal for organizations with limited budgets or those looking for customizable solutions. They provide all the basic functions without the costs associated with commercial products, making them an attractive option for small to mid-sized organizations.
1. ELK Stack
The ELK Stack combines Elasticsearch, Logstash, and Kibana to offer a powerful and flexible log management and analysis solution. This stack enables organizations to collect, store, and visualize data from multiple sources in real time. The ELK Stack's scalability and customizable dashboards make it an attractive option for organizations looking to tailor their SIEM solution.
Features:
- Real-time data visualization.
- Scalable data storage.
- Full-text search capabilities.
- Customizable dashboards.
- Centralized logging.
Pros:
- Highly scalable and flexible.
- Strong community support and extensive documentation.
- Real-time data processing.
Cons:
- Requires significant setup and maintenance.
- Limited out-of-the-box SIEM features.
- Steep learning curve.
2. Ossec
Ossec is an open-source, host-based intrusion detection system that offers log analysis, file integrity checking, and real-time alerting. While not a complete SIEM solution, Ossec can be integrated with other tools to build a comprehensive security monitoring platform. This tool is ideal for organizations seeking a lightweight, expandable threat detection and compliance solution.
Features:
- Host-based intrusion detection.
- Log analysis.
- Rootkit detection.
- File integrity checking.
- Real-time alerting.
Pros:
- Lightweight and expandable.
- Free and open source.
- Real-time alerting.
Cons:
- Not a full SIEM solution on its own.
- Limited centralized management.
- Requires integration with other tools.
3. AlienVault OSSIM
AlienVault OSSIM (Open Source Security Information and Event Management) provides a unified platform that combines essential SIEM features with other security tools, including asset discovery, vulnerability assessment, and intrusion detection. OSSIM's community support and integrated threat intelligence from AlienVault Labs make it a compelling choice for SIEM beginners.
Features:
- Asset discovery.
- Intrusion detection.
- Vulnerability assessment.
Pros:
- Comprehensive feature set.
- Strong community support.
- Integrated threat intelligence.
Cons:
- Resource-intensive.
- Basic user interface.
- Limited scalability compared to paid solutions.
4. Apache Metron
Apache Metron is a big data cybersecurity platform that provides real-time threat detection and security monitoring. Built on the Hadoop ecosystem, it allows for the collection, processing, and analysis of security data at scale.
Features:
- Scalable data processing.
- Real-time threat detection.
- Data enrichment and correlation.
- Integration with the Hadoop ecosystem.
- Pluggable framework for parsers and enrichments.
Pros:
- Highly scalable with big data capabilities.
- Open source and highly customizable.
- Strong integration with existing Hadoop infrastructure.
Cons:
- Requires expertise in Hadoop and big data technologies.
- Limited support compared to commercial products.
- Complex setup and configuration.
5. Wazuh
Wazuh is an open-source security monitoring platform that offers SIEM capabilities, log data analysis, intrusion detection, and regulatory compliance monitoring. It is built on top of the ELK Stack, providing a robust and scalable solution for security operations.
Features:
- Log data analysis.
- File integrity monitoring.
- Intrusion detection.
- Vulnerability detection.
- Compliance monitoring.
Pros:
- Built on the scalable ELK Stack.
- Free and open source with strong community support.
- Comprehensive security monitoring features.
Cons:
- Requires integration and customization for full SIEM capabilities.
- Steep learning curve for beginners.
- Resource-intensive.
6. Graylog
Graylog is an open-source log management tool that provides real-time log analysis and SIEM capabilities. Its flexible and extensible architecture allows organizations to customize and scale their log management and analysis needs.
Features:
- Real-time log analysis.
- Customizable dashboards.
- Centralized log management.
- Alerting and reporting.
- Extensible architecture.
Pros:
- Flexible and extensible architecture.
- Free and open source with enterprise options available.
- Strong community support.
Cons:
- Requires significant setup and configuration.
- Limited out-of-the-box SIEM features.
- Resource-intensive.
7. Security Onion
Security Onion is an open source Linux distribution for intrusion detection, network security monitoring, and log management. It integrates various tools, including Suricata, Zeek (formerly Bro), and the ELK Stack, to provide comprehensive security monitoring capabilities.
Features:
- Network security monitoring.
- Intrusion detection with Suricata and Zeek.
- Log management with the ELK Stack.
- Integrated threat intelligence.
- Scalable and customizable deployment.
Pros:
- Comprehensive security monitoring in a single package.
- Free and open source with scalable architecture.
- Strong community support and documentation.
Cons:
- Complex configuration for optimal performance.
- Requires significant setup and maintenance.
- Resource-intensive, especially for large deployments.

Paid SIEM Tools
Premium SIEM tools offer comprehensive, integrated management for organizations seeking top-tier security and compliance.
1. Splunk Enterprise Security
Splunk Enterprise Security stands out for its advanced data analytics and visualization capabilities. It offers extensive features, including real-time monitoring, threat detection, and incident response workflows, making it a favorite among large organizations. Furthermore, its scalability and flexibility allow organizations to adapt the platform to their evolving security needs.
Features:
- Real-time data analytics.
- Threat detection and incident response.
- Customizable dashboards.
- Anomaly detection and machine learning capabilities.
- Extensive third-party integrations.
Pros:
- Highly advanced data analytics and visualization.
- Scalable and flexible.
- Real-time monitoring and alerting capabilities.
Cons:
- Requires extensive resources and expertise to manage.
- High cost for large-scale deployments.
- Complex configuration and setup.
2. IBM QRadar
IBM QRadar is renowned for its analytics engine, easy network device integration, and application integration. Thanks to its correlation capabilities and security intelligence database, QRadar excels at detecting anomalies and uncovering advanced threats. It is particularly well-suited for organizations that require a comprehensive, integrated approach to security and compliance.
Features:
- Anomaly detection.
- Integrated threat intelligence.
- Scalable architecture.
- Log and flow data analysis.
- Advanced correlation and incident response.
Pros:
- Powerful analytics engine and threat detection.
- Easy integration with network and application devices.
- Comprehensive threat intelligence and correlation capabilities.
Cons:
- High cost.
- Complex to deploy and manage.
- Requires skilled personnel for optimal use.
3. LogRhythm NextGen SIEM Platform
LogRhythm offers a unified solution that combines SIEM, log management, network and endpoint monitoring, and advanced security analytics. Its NextGen SIEM Platform is designed to streamline threat detection, minimize false positives, and enhance security operations efficiency. LogRhythm's focus on user and entity behavior analytics (UEBA) enables organizations to detect insider threats and compromised accounts with greater accuracy.
Features:
- SIEM and log management.
- Network and endpoint monitoring.
- Advanced security analytics.
- Automated response and remediation.
- User behavior analytics (UBA).
Pros:
- Advanced security analytics.
- Unified platform for comprehensive security management.
- Effective in reducing false positives and streamlining operations.
Cons:
- High cost of implementation and maintenance.
- Requires significant resources.
- Complex deployment.
4. ArcSight
ArcSight delivers strong SIEM functionality with an emphasis on real-time threat detection and response. Its modular design supports flexible deployment, accommodating organizations of different sizes and security requirements. Key strengths of ArcSight include event correlation, log management, and reporting, providing comprehensive visibility into security events and trends.
Features:
- Event correlation.
- Real-time threat detection.
- Scalable and modular architecture.
- Detailed reporting and insights.
- Advanced analytics and machine learning.
Pros:
- Flexible deployment options.
- Real-time threat detection with robust correlation.
- Strong event correlation and log management.
Cons:
- High cost.
- Requires skilled personnel for setup and maintenance.
- Resource-intensive setup and management.
5. SolarWinds Security Event Manager
SolarWinds Security Event Manager (SEM) offers powerful log management and threat detection capabilities to simplify compliance and security operations. SEM is known for its user-friendly interface and automation features.
Features:
- Automated threat detection.
- Real-time event correlation.
- Built-in compliance reporting.
- Comprehensive log management.
- User-friendly interface and dashboards.
Pros:
- Strong automation features for threat detection and response.
- Easy to deploy and use with an intuitive interface.
- Cost-effective compared to other paid solutions.
Cons:
- Basic compared to high-end SIEM tools.
- Limited scalability for very large organizations.
- Requires regular updates and maintenance.
6. Sumo Logic
Sumo Logic provides a cloud-native SIEM platform with real-time analytics and security monitoring capabilities designed for modern IT environments. It is known for its ease of use, scalability, and strong integration with cloud services.
Features:
- Real-time analytics and security monitoring.
- Cloud-native architecture.
- Integration with cloud services (AWS, Azure, GCP).
- Advanced threat detection and machine learning.
- Scalable and flexible deployment options.
Pros:
- Scalable cloud-based solution with strong data analytics.
- User-friendly interface and quick deployment.
- Easy integration with major cloud services.
Cons:
- Becomes costly at scale.
- Requires familiarity with cloud environments and security practices.
- Dependence on internet connectivity for cloud services.
7. RSA NetWitness
RSA NetWitness Platform is a full-featured SIEM solution that integrates network, endpoint, and log data to deliver sophisticated threat detection and response. It uses machine learning and behavioral analytics to quickly identify and address potential security threats.
Features:
- Advanced threat detection and response.
- Incident response and investigation tools.
- Network, endpoint, and log data integration.
- Machine learning and behavioral analytics.
- Scalable and modular architecture.
Pros:
- Comprehensive threat detection across multiple data sources.
- Effective incident response and investigation tools.
- Advanced analytics and machine learning capabilities.
Cons:
- High cost of ownership.
- Requires significant resources and skilled personnel.
- Complex deployment and configuration.
phoenixNAP's Bare Metal Cloud delivers the raw power and flexibility for handling the immense data volumes and complex analytics required by modern SIEM solutions.
With dedicated hardware resources and unrestricted root access, you have complete control over your environment, ensuring optimal performance and customization.

What Are the Benefits of SIEM?
One of the key advantages of security information and event management systems is their ability to generate high-fidelity alerts, which provide actionable intelligence. The term "high fidelity" highlights the strong likelihood that the identified activities pose real security risks. This precision is crucial for several reasons:
- Reduced false positives. High-fidelity alerts minimize the number of false positives, ensuring that security teams are not drowned in irrelevant alerts. The reduction in noise allows analysts to focus on genuine threats.
- Optimized resource allocation. By generating high-fidelity alerts, SIEM systems optimize security resource allocation. Security teams can prioritize their efforts based on the severity and likelihood of threats.
- Actionable intelligence. SIEM systems provide detailed and contextual information about potential threats, enabling security teams to immediately and effectively identify and mitigate security risks.
- Preventing employee burnout. The precision of SIEM systems prevents employee burnout by reducing the workload associated with investigating false positives. Security analysts can focus on meaningful tasks, leading to higher job satisfaction and better overall performance.
What Are the Challenges of Implementing SIEM?
Implementing and maintaining security information and event management solutions presents several challenges. Understanding these is crucial for maximizing the effectiveness of SIEM systems:
- Complexity. Setting up and managing SIEM involves several key steps: configuring log sources, creating correlation rules, and minimizing false positives. This complexity demands skilled personnel.
- Scalability. As organizations grow, the volume of log data increases, potentially straining SIEM performance. Ensuring scalability to handle large data volumes is essential.
- Cost. SIEM ownership costs can be a barrier to entry for smaller businesses. Expenses include purchase and subscription fees, implementation, maintenance, and staff training.
- Keeping up with threats. SIEM systems require regular updates with new correlation rules and threat intelligence to identify evolving threats. This process requires access to the latest threat data and the ability to adapt to new attack vectors.
- Integration challenges. Integrating SIEM systems with existing security tools and IT infrastructure can be problematic. Ensuring compatibility and facilitating data exchange is essential, but it requires additional effort.
- Reliance on log data. SIEM systems primarily rely on log data. If devices or applications fail to generate logs or if logs are not configured properly, these activities won't be visible, resulting in security blind spots.
Organizations with limited resources benefit greatly from managed security service providers (MSSPs) for expert SIEM deployment, management, and threat monitoring.

SIEM: The Cornerstone of Modern Threat Detection and Response
Security information and event management systems are critical for modern cybersecurity. They provide real-time threat detection, efficient incident response, and compliance assistance. These platforms centralize security data from multiple sources, helping teams detect and respond to threats faster.
They also enhance security maturity by offering insights into an organization's threat landscape and security posture. Implementing a SIEM system is a strategic investment for organizations seeking to solidify their digital defenses. Regular tuning and optimization further improve detection accuracy and reduce false positives.



