Gone are the days of building software from scratch. Most development teams use open-source software (OSS) to speed up work and reduce time to market (TTM). Programmers use ready-made OSS components and write custom code to stitch everything together into a functioning piece of software.
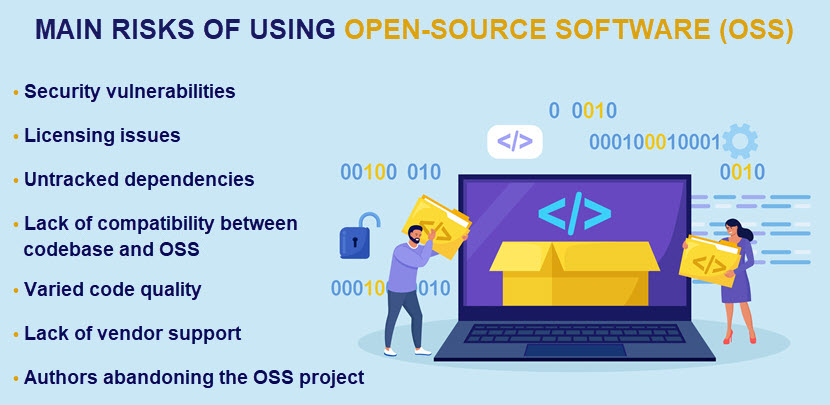
While beneficial in terms of time and costs, using OSS as building blocks can introduce critical vulnerabilities or flaws to an application. This inherent risk is why software composition analysis is a must for any app that relies on open-source code.
This article is an intro to software composition analysis (SCA), a software engineering practice that enables teams to manage open-source components within apps. Read on to see how SCA helps identify, evaluate, and remove OSS-related risks.
What Is Software Composition Analysis?
Software composition analysis is a security methodology that tracks and analyzes open-source packages within a codebase. SCA is vital when you consider the following figures:
- More than 90% of modern apps use OSS packages.
- An average app relies on 147 different open-source components.
- An average organization is aware of less than 10% of its OSS use.
Software composition analysis has two primary goals:
- Detect all open-source components within an app, including their supporting libraries and dependencies.
- Check OSS components for missing patches, security flaws, and licensing issues.
SCA procedures rely on an "inventory, analyze, control" framework to give teams a full view of OSS usage.
Here's an overview of how this framework works:
- Inventory. The first step is to inventory all OSS components and libraries within the software. Then, SCA generates a dependency tree that presents both direct dependencies (those explicitly included in the project) and transitive dependencies (those brought in indirectly through other dependencies).
- Analyze. The second step is to check all OSS components for flaws or license-related issues. If there's a problem, the process generates contextual info (e.g., issue description, affected components, CVSS scores, relationship paths, etc.).
- Control. Finally, SCA offers remediation guidance by providing information on mitigating the problem.
Reports generated from SCA go to the security personnel responsible for mitigating detected issues. In some CI/CD pipelines, an SCA-identified problem may block new commits to the codebase. Here's an overview of what issues SCA detects:
- Known security vulnerabilities in third-party components.
- License compliance issues.
- Outdated or end-of-life OSS components.
- Security misconfigurations.
- Cryptographic vulnerabilities (e.g., weak algorithms, outdated cryptographic libraries, insufficient key lengths, etc.).
- Components that may lead to the exposure of sensitive data (e.g., hardcoded credentials or configurations that inadvertently leak confidential data).
SCA is a standard part of DevSecOps, a development practice that integrates security into every phase of the software development lifecycle (SDLC). SCA enables OSS checks in the early stages of development before issues reach the build stage.
Why Is Software Composition Analysis Important?
Software composition analysis ensures the security, compliance, and reliability of open-source components within software. Here's an overview of all the benefits of adopting SCA:
- Improved security. SCA helps identify and fix software vulnerabilities, reducing the risk of security breaches, data leaks, and non-compliance.
- Dependency management. Modern software relies heavily on third-party libraries and open-source components. SCA helps manage dependencies by providing visibility into components and the way they interact with each other.
- SBOMs. SCA generates a software bill of materials (SBOM) that gives complete visibility into all proprietary and open-source components. This info helps stakeholders understand security risks and licensing requirements.
- License compliance. Open-source software comes with various licenses, each with its own terms, permissions, and restrictions. SCA ensures compliance with all OSS licenses and prevents costly legal issues.
- Vulnerability detection. SCA identifies and alerts developers to flaws in OSS components. Teams then take proactive measures to update or replace vulnerable components.
- Risk prioritization. SCA prioritizes vulnerabilities based on various factors (the flaw's severity, the importance of the component, the availability of updates, etc.). These assessments help the team focus efforts on addressing the most critical risks.
- Enhanced team productivity. SCA automates a range of processes and frees up developers from manual tasks. Developers also get more freedom to innovate due to less worry about potential OSS incidents.
- Cost savings. Detecting and addressing security vulnerabilities early in development is far more cost-effective than dealing with post-release security incidents.
- Quicker, safer TTM. Companies that use SCA speed up time to market by enabling teams to use OS components to expedite work. The product reaches the market faster and with fewer delays. Additionally, the product becomes safer and has less risk for license non-compliance.
Concerned about high IT expenses? Check out our article on IT cost reduction to see 12 tried-and-tested strategies for lowering IT expenses.
Challenges of Software Composition Analysis
While software composition analysis is valuable when managing third-party software components, SCA has a few must-know drawbacks. Here are the usual challenges companies face once they adopt SCA:
- Limited scope. SCA only identifies risks in open-source components, not in custom (original) code. Teams must pair SCA with tools for proprietary code (like SAST, DAST, IAST, or RASP) to get a complete suite of app security tests.
- Incomplete component inventories. Dynamic development environments have frequent changes. Regular updates often lead to discrepancies in the component inventory. Keeping a comprehensive and up-to-date inventory of all components in a project is often challenging.
- False positives and negatives. SCA tools occasionally generate false positives (incorrectly flagging a component as vulnerable) or false negatives (failing to detect an actual vulnerability). False positives lead to unnecessary work, while false negatives lead to unaddressed security risks.
- Workflow integration. Integrating SCA seamlessly into existing development workflows is challenging. Most companies face a complex and labor-intensive deployment. Also, some teams resist using a tool that disrupts usual processes or introduces delays.
- No auto-remediation. Most SCA tools only identify vulnerabilities and provide remediation guidance without offering auto-mitigation of issues.
- Transitive (indirect) dependencies. Identifying and understanding the security implications of indirect dependencies is complex, and some SCA tools struggle to provide complete visibility into the entire dependency tree. The fact that 80% of vulnerabilities detected by SCA are in transitive dependencies further underlines this concern.
- Database vulnerability lag. Many vulnerability databases and SCA tools rely on fail to add freshly discovered flaws in a timely fashion.
- Resource constraints. Implementing and maintaining an SCA process requires dedicated resources for training, monitoring, and responding to security issues. Some organizations face resource constraints in terms of time, budget, or expertise.
Deploying SCA to a large codebase often reveals a sizable code debt. Learn more about this issue and the most effective ways to deal with it in our article on technical debt.
What Are Software Composition Analysis Tools?
Software composition analysis tools help organizations identify, analyze, and manage third-party components and open-source software used in their apps. These tools are crucial in addressing potential vulnerabilities, licensing issues, and other risks of using external code.
Here are a few of the most popular SCA tools currently on the market with an overview of their main selling points:
- Snyk provides automated scans, real-time incident alerts, and a vast custom database of software vulnerabilities.
- Qwiet AI uses AI to detect zero-day and pre-zero-day vulnerabilities in OSS code.
- Spectral provides automated scanning, customizable policies, and advanced rule creation.
- Mend is an enterprise-grade SCA platform that easily handles large numbers of apps and developers.
Here are the five different types of SCA tools based on their functionalities:
- Package managers that help install and manage open-source packages, plus provide info on dependencies to avoid version conflicts.
- Binary analysis tools that scan compiled code to identify open-source components and offer info on dependencies, security risks, and licensing issues.
- Vulnerability scanners that scan open-source packages and libraries for weaknesses.
- Continuous monitoring tools that track apps and alert developers to changes or updates to OSS components.
- Composition analysis tools that provide a comprehensive view of OSS components, plus analyze dependencies, license issues, and overall software health.
Many software composition analysis tools provide features from two or more of these categories. Others are more specialized, so adopters often combine several tools to ensure well-rounded SCA capabilities.

How SCA Tools Work?
SCA tools integrate seamlessly into development workflows and CI/CD pipelines. Once integrated, the tool automatically scans the code for issues and provides real-time feedback.
Here's an overview of how SCA tools work:
- Component identification. The first step is to scan the source code and the associated artifacts used to compile the app. The tool identifies all OSS components.
- Dependency discovery. The SCA tool analyzes OSS components to identify all relevant dependencies (direct and transitive).
- Vulnerability detection. The tool compares all identified components against a database of known vulnerabilities and flaws. This process often involves referencing the Common Vulnerabilities and Exposures (CVE) database, but many tools use additional proprietary resources.
- Policy enforcement. Many SCA tools enable you to apply security and license policies at scale. If an admin defines policies related to OSS security (e.g., rules for acceptable risk levels or license types), the SCA tool flags all components that do not meet the set criteria.
- License analysis. The tool analyzes the licensing info associated with each OSS element. The SCA platform also checks whether licenses comply with the organization's policies and relevant legal requirements.
- Risk scoring. The tool assigns a risk score to each detected vulnerability. The usual scoring factors are severity, exploitability, and the number of dependencies.
- Reporting. SCA tools generate reports that offer insights into software composition, vulnerabilities, and the overall OSS security posture.
- OSS monitoring. SCA is not a one-time process. Tools continually monitor for updates to vulnerability databases and changes in the status of third-party components. The tool alerts admins of any newly detected flaws or license conflicts.
- Remediation guidance. The SCA tool offers guidance on how to remediate detected issues. Most tools provide info on available updates, patches, or alternative components that address current security or licensing concerns.
Learn about vulnerability assessments and see why a proactive search for flaws should be at the top of any security team's to-do list.
What to Consider When Choosing a Software Composition Analysis Tool?
Here are a few considerations to keep in mind when choosing an SCA tool:
- Ease of use. Your SCA tool must be as simple to use and unintrusive to workflows as possible. Look for intuitive interfaces, clear documentation, and features that simplify the configuration and management of the tool.
- Tech compatibility. Ensure the SCA tool supports your software development stack's programming languages and technologies.
- Team fit. An SCA tool must not require developers to learn new software from scratch. Find a tool that fits your team's current skill set and preference.
- Vulnerability databases. Check the accuracy and comprehensiveness of the tool's vulnerability database(s). A reliable SCA tool relies on up-to-date and widely recognized databases.
- Community support. Consider the community around the SCA tool and check for user feedback and reviews. A vibrant community and positive feedback indicate a tool's effectiveness and reliability.
- License analysis. Assess the accuracy and thoroughness of the license analysis provided by the SCA tool. Ensure that the tool effectively identifies and manages OSS licenses.
- Scalability. Evaluate whether the SCA tool is scalable enough to meet the demands of your project (both currently and in the future).
- Integration. A SCA tool must seamlessly integrate with existing development workflows, including CI/CD pipelines, issue tracking systems, and version control systems. The tool must work within existing workflows so developers don't have to exit development environments to implement security functions.
- Reporting and analytics. Clear, correct, informative, and actionable reports are essential for effective SCA. Consider the reporting and analytics capabilities of every potential SCA tool.
- Policy enforcement. Not all SCA tools allow you to define and enforce policies. Check whether the tool has policy enforcement capabilities if you plan to set predefined guidelines and standards.
Remember that SCA must not interrupt the development process or force teams into steep learning curves. Seamless integration with both systems and personnel is vital for maximizing the benefits of an SCA tool.
An Absolute Must for Any OSS-Based App
The growing adoption of OSS has made SCA vital to application security. Software composition analysis enables teams to use open-source packages without exposing companies to unnecessary vulnerabilities or legal issues. Use SCA to pre-empt risks and grant your developers the freedom to safely use OSS as building blocks when creating software.



