Companies wishing to deliver secure software to their users can no longer afford to treat security as an afterthought. In today’s digital landscape, security must be an inherent feature of every software solution.
Enter DevSecOps, an approach that integrates security measures and practices at every step of the software development lifecycle (SDLC), from planning and coding to testing, deployment, and monitoring.
In this article, we will examine the principles, practices, and benefits of DevSecOps, demonstrating how this approach helps businesses deliver robust and secure software solutions efficiently and quickly.
What Is DevSecOps?
DevSecOps (short for Development, Security, and Operations) is a software development practice that integrates security into every phase of the software development lifecycle. With DevSecOps, security is embedded into the software as it is developed rather than added later.
In the past, security practices and features were only considered at later stages in the software development lifecycle and were typically dealt with by a separate security team. However, rapidly evolving cybersecurity threats have necessitated the practice of integrating security from the very start and maintaining it throughout the CI/CD pipeline.
DevSecOps vs. DevOps
The DevSecOps and DevOps approach both aim to streamline and accelerate software development and delivery by enhancing collaboration between development and operations teams and automating repetitive tasks. The difference between the two is that DevSecOps places security concerns at the forefront during all phases of the software development lifecycle.
While DevOps remains fast and efficient, DevSecOps is more likely to identify and mitigate potential security vulnerabilities, thereby reducing the risk of data breaches and leaks.
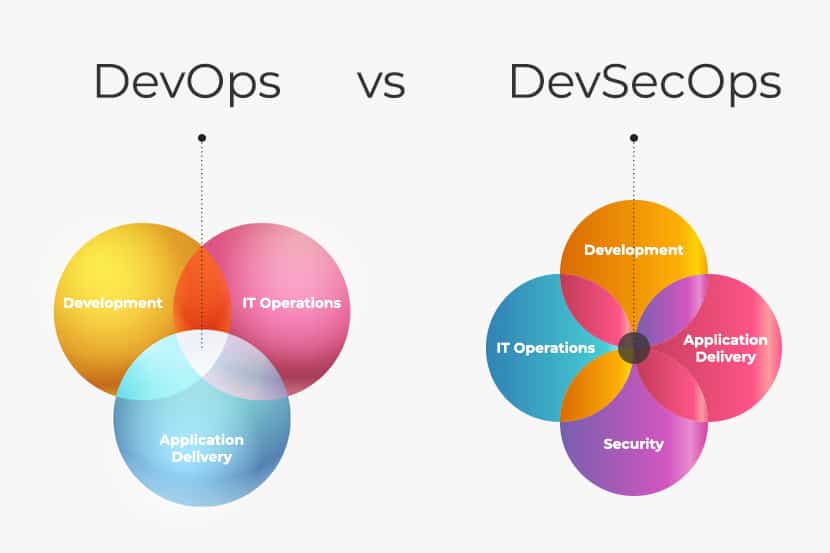
DevSecOps Components
To achieve its security goals, DevSecOps involves various components and practices:
- Collaboration and communication. DevSecOps fosters collaboration between the development, security, and operations teams. To achieve this aim, the teams must ensure there are no communication gaps between them and that all participants understand that they are working towards a common goal.
- Security awareness and ownership. As an extension of the principle of collaboration, everyone involved in the SDLC must be aware of the security imperative and have a sense of ownership over the results. DevSecOps is founded on the principle that “security is everyone’s responsibility”.
- Security of tools and architecture. The creation of secure applications requires a secure environment. Before any system is used, the security team must test the configurations to ensure they can resist malicious activity. This principle also incorporates the implementation of stringent security measures during the entire SDLC, including multi-factor authentication, least-privileged access, and the segregation of CI/CD pipelines to prevent lateral movement.
- Automation. Central to the DevSecOps approach is the automation of security testing and analysis throughout the CI/CD pipeline. This allows for the rapid delivery of new software that has passed vulnerability scanning, code analysis, and compliance checks. With integrated security controls, whenever the risk level rises over a certain level, the building process stops until the security team resolves the issue.
- Security testing. With DevSecOps, security testing is conducted on an ongoing basis, throughout the development process. The range of tests that ensure the delivery of secure software includes static application security testing (SAST), dynamic security testing (DAST), penetration testing, compliance checks, and others.
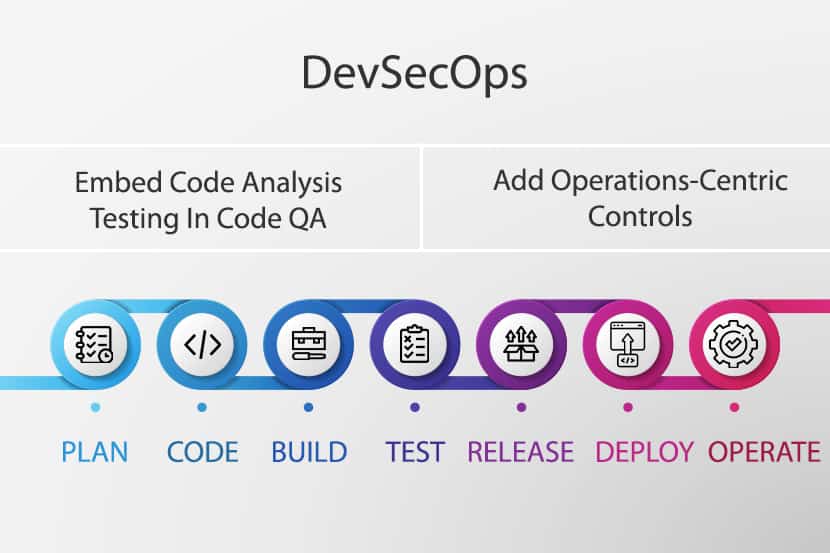
What Does a DevSecOps Workflow Look Like?
A DevSecOps workflow emphasizes collaboration, automation, and the proactive implementation of security measures at every stage of the SDLC. While specific workflows vary depending on the organization’s tools and needs, a general DevSecOps workflow might include the following:
- Planning. Involves defining the security requirements and objectives, identifying potential threats and vulnerabilities, and conducting threat modeling. From these activities, developers and architects can design security controls directly into the application’s architecture.
- Coding and development. Developers write code following secure coding practices, the code is peer reviewed, and automated static application security tools (SAST) analyze the source code for vulnerabilities.
- Continuous integration (CI). Changes introduced to the code trigger automated building and testing and developers receive immediate feedback if security issues are detected.
- Continuous deployment (CD). Container images are scanned for vulnerabilities in the staging environment before deployment to container orchestration platforms via automated dynamic application security testing (DAST) tools.
- Operations and monitoring. Applications and infrastructure are monitored in production for security anomalies and threats; automated cyber incident detection and response are implemented to mitigate potential security issues and breaches.
- Remediation and feedback. Vulnerabilities and weaknesses are remediated according to priority, and their root causes are analyzed and addressed. All parties involved receive feedback that helps them to improve security practices.
- Education and sharing knowledge. Security awareness programs and training are ongoing practices, and teams are encouraged to share knowledge and collaborate around a common goal.
- Compliance. Automated compliance checks ensure that all processes adhere to security standards as well as industry regulations (PCI DSS, GDPR, HIPAA, etc.).
- Reporting. Compliance checks, alerts, and test results are collated into reports that are shared with stakeholders and used for auditing purposes.
DevSecOps Benefits
By using the DevSecOps approach and integrating security practices into their software development and delivery process, organizations reap numerous benefits, including:
- Enhanced security. Proactive and constant monitoring for security vulnerabilities reduces the risk of security breaches and data leaks.
- Faster and more reliable software delivery. The automation of CI/CD pipelines enables the speedier delivery of consistently secure software that has been scanned and tested.
- Better collaboration. DevSecOps rests on the collaboration between developers, security experts, and operations teams, who all share the responsibility for delivering a safe product.
- Cost reduction. Early detection of security issues is more cost-effective than having to fix them in production.
- Full compliance. The automation of compliance checks at every step ensures that software development adheres to regulation and security standards.
- Risk management. DevSecOps incorporates threat modeling and regular vulnerability scanning of code, dependencies, and infrastructure to minimize the likelihood of weaknesses being exploited.
- Enhanced incident response. The automation of incident detection and response mechanisms helps organizations to quickly respond to security incidents.
- Flexibility and scalability. DevSecOps practices integrated well with cloud-native architectures, enabling organizations to easily scale their operations and adapt to changing business needs.
- Higher quality software. When security is embedded into the software development process, technical debt is reduced and the result are applications that are of greater quality and require less maintenance.
- Competitive advantage and trust. Organizations committed to security build trust with their customers and stakeholders, potentially gaining a competitive advantage in the market.
DevSecOps Challenges
While it offers numerous benefits, DevSecOps also comes with a set of challenges:
- Cultural shift. A DevSecOps approach requires that teams embrace collaboration and share responsibility for security. This may create resistance, especially in organizations with long-standing silos.
- Security tool integration. Choosing the right security tools and integrating them into the CI/CD pipeline to ensure they are compatible with development and deployment tools can be time- and resource-consuming.
- Skills and training. Not all development and operations teams have sufficient security knowledge and may require additional training. Organizations need to make an effort to enhance security awareness among all team members.
- Automation challenges. Implementing automated security scanning tools is a complex task. Furthermore, automated scanning can create false positives that must be addressed manually.
- Developer overload. Repeated security alerts can lead to alert fatigue among developers, potentially resulting in important issues being overlooked.
- Speed vs. security. Finding the right balance between development speed and robust security testing can be difficult, as too many security checks slow down the development process.
- Resource limitations. Organizations with budget and staff constraints may find it difficult to adequately implement DevSecOps practices.
- Legacy systems. DevSecOps practices can be difficult to integrate with legacy systems and monolithic applications.
- Complex environments. It can be difficult to manage security across multi-cloud and hybrid environments using diverse technologies.

DevSecOps Best Practices
Organizations wishing to effectively implement DevSecOps throughout the SDLC should follow these best practices:
- Shift left. This means that security practices are implemented earlier in the development process, right from the design stage.
- Adopt automation. The entire CI/CD pipeline should be automated to enable the rapid and consistent delivery of software, with a security check at every stage.
- Implement security as code. Security controls should be embedded into the infrastructure code.
- Maintain secure coding standards. Ensure that developers follow coding best practices and guidelines so that applications are secure from the start.
- Foster a culture of collaboration. The development, security and operations teams should be aware of their shared responsibility and be encouraged to collaborate and share skills and knowledge.
- Test early and regularly. Scan your code, dependencies, and infrastructure early in the development process and continue to conduct tests regularly.
- Create feedback loops. Establish feedback loops so that teams can learn from security incidents and improve security practices.
- Enforce access controls. Access controls such as least-privilege principles and role-based access controls should be implemented throughout the development process to protect sensitive data and systems.
- Prioritize risk management. DevSecOps teams that make risk management their priority ensure that security controls are implemented, and risks reduced.
- Manage third-party risks. Assess the risks associated with third-party software and regularly perform code dependency checks.
- Maintain scalability. Ensure your DevSecOps practices can scale to accommodate evolving environments and meet your organization’s growing needs.
20 DevSecOps Tools to Consider
The following list contains some of the more widely recognized and comprehensive DevSecOps tools:
- Checkmarx. An AI-powered software security solution that identifies and fixes vulnerabilities in source code.
- Fortify. Offers static, dynamic, and interactive testing tools that find security issues in source code.
- Veracode. A cloud-based application security platform that integrates security analysis into the CI/CD pipeline.
- Snyk. A tool that finds and fixes vulnerabilities in code, dependencies, containers, and IaC.
- OWASP ZAP. An open-source tool for finding vulnerabilities in web applications.
- Burp Suite. A suite of security tools used for penetration testing of web applications.
- WhiteHat Sentinel. Offers a scalable application security tool that integrates across the whole SDLC pipeline.
- Nexus Lifecycle. A security tool that scans and checks for vulnerabilities in open-source libraries and products.
- Codacy. An automated tool that reviews code via static code analysis.
- SonarQube. An open-source platform offering plugins that identify code bugs during development.
- Aqua Security. A security platform for cloud-native apps with full CI/CD integration.
- Spectral. A security solution that scans for exposed secrets and security misconfigurations during build.
- Clair. A container vulnerability scanner that analyzes container images and reports on known vulnerabilities.
- ThreatModeler. A security tool that allows developers to create threat models for their applications, helping to identify weaknesses and vulnerabilities.
- Anchore Engine. An open-source tool that analyzes container images and reports on CVE.
- Cloud Foundry. An open-source, multi-cloud PaaS solution that protects containerized environments and cloud-native applications, ensuring security and compliance with regulations.
- Palo Alto Networks Cortex XSOAR. A security orchestration automation and response (SOAR) platform that helps organizations investigate and respond to threats quickly.
- OpenSCAP: A security content automation protocol (SCAP) framework that checks for compliance violations and security vulnerabilities.
- DoControl. A tool that manages access privileges and data exposure by automating data access controls.
- TheHive: An open-source incident response and case management platform with vulnerability tracking and management features.
DevSecOps: Where Innovation Meets Security
DevSecOps represents a cultural shift in the world of software development. This holistic approach gives security paramount importance while fostering collaboration and communication, whereby development, security, and operations teams work together to achieve common security goals.
By incorporating security practices at every stage of the SDLC, organizations proactively identify and remedy vulnerabilities in their applications, reducing the risk of breaches while delivering innovative software faster and more reliably. DevSecOps is the natural response to a continually evolving digital landscape, where safety and efficiency must go hand in hand.