Cybercriminals often target companies through vulnerabilities that the security staff failed to discover and patch on time. While typically small and easy to overlook, these weaknesses offer a backdoor that enables a hacker to slip in unnoticed and cause a costly breach.
This article is an introduction to vulnerability assessments, one of the most effective and affordable techniques for discovering system flaws. Read on to learn how a vulnerability assessment helps detect system faults, evaluate risks, and improve overall cybersecurity.
What Is a Vulnerability Assessment?
A vulnerability assessment is a systematic review of an IT system that discovers, classifies, and prioritizes security flaws. This type of analysis has three goals:
- Evaluate the system for exploitable flaws.
- Assign a risk level to each vulnerability.
- Recommend actions to prevent hackers from exploiting the weaknesses.
Other common names for a vulnerability assessment are vulnerability analysis and vulnerability testing.
This test’s primary objective is to identify exploitable vulnerabilities and errors before hackers breach the system. As such, it is considered a core component for an ironclad information security risk management system. Most flaws are bugs in code, defects in software architecture, and mistakes in security procedures. Examples of common vulnerabilities are:
- System misconfigurations.
- A database weakness that allows SQL injections.
- Lack of careful staff behavior.
- Policy non-compliance mistakes.
- Unencrypted data moving through networks.
- A bug in software or programming interfaces.
- An exploitable authentication mechanism.
- A malicious backdoor program that allows hackers to manage an APT attack or set up ransomware.
- Automatic executions of scripts without virus and malware checks.
- A flaw in account privileges.
- Unpatched operating systems and applications.
- Weak passwords.
- Zero-day exploits.
Both enterprises and SMBs can benefit from a vulnerability test. Companies typically run assessments on an annual basis or whenever the team makes a significant change, such as:
- Adding new services.
- Opening new ports.
- Installing a new piece of equipment.
- Opening an office at a new location.
- Moving to the cloud.
A company wishing to organize a vulnerability test has two options: have the in-house staff run the test or hire a third-party to evaluate the system. While going with the in-house team is the cheaper choice, the best results come from testers unfamiliar with the subject system and its protocols.
Ensure your business follows cybersecurity best practices to minimize the attack surface and protect sensitive data.
Types of Vulnerability Assessments
Businesses rely on different types of vulnerability tests to discover system defects. Depending on the area of the infrastructure under review, there are three types of tests:
- External scans: Inspection of components that directly face the Internet and are available to external users (ports, networks, websites, apps, etc.).
- Internal scans: Examination of internal networks and systems accessible only to employees.
- Environmental scans: These tests focus on specific operational technologies, such as cloud deployments, IoT, or mobile devices.
Below are the four most common types of vulnerability assessments.
Network Assessments
Network assessment scans identify possible threats to network security. Testers inspect hubs, switches, routers, clusters, and servers to ensure network-accessible resources are safe from malicious actors.
A network test is the most common type of vulnerability scanning. This scan ensures the safety of networks, communication channels, and all networking equipment.
A network assessment also detects vulnerabilities in wireless networks. These scans typically focus on potential points of attack, configuration mistakes, and poor firewall setups.
Learn about the different types of firewalls, an essential aspect of any network security strategy.
Host Assessment
This analysis locates and classifies vulnerabilities in workstations, laptops, and other hosts. Host scans examine:
- Host configurations.
- User directories.
- File systems.
- Memory settings.
A host assessment ensures that a misconfiguration within an endpoint does not allow an attacker to pass the perimeter and breach the system.
Application Scans
Application scans detect software flaws and incorrect configurations of web apps and their source code. There are two common forms of application scans:
- Dynamic Application Security Testing (DAST): This testing technique executes an application and detects defects in real-time.
- Static Application Security Testing (SAST): This analysis identifies app flaws without running the program.
The two methods test applications differently and are more effective at different phases of the software development life cycle (SDLC). For example, SAST discovers flaws such as cross-site scripting (XSS) earlier in the SDLC, while DAST is more useful when an application enters production.
Database Scans
Database scans identify potential exploits in a database. These tests discover misconfigurations, rogue databases, and insecure dev and test environments. Database scans are vital to preventing SQL injections.
How to Conduct a Vulnerability Assessment?
A typical vulnerability test consists of five steps during which the team inspects the system, evaluates risks, and suggests improvements.
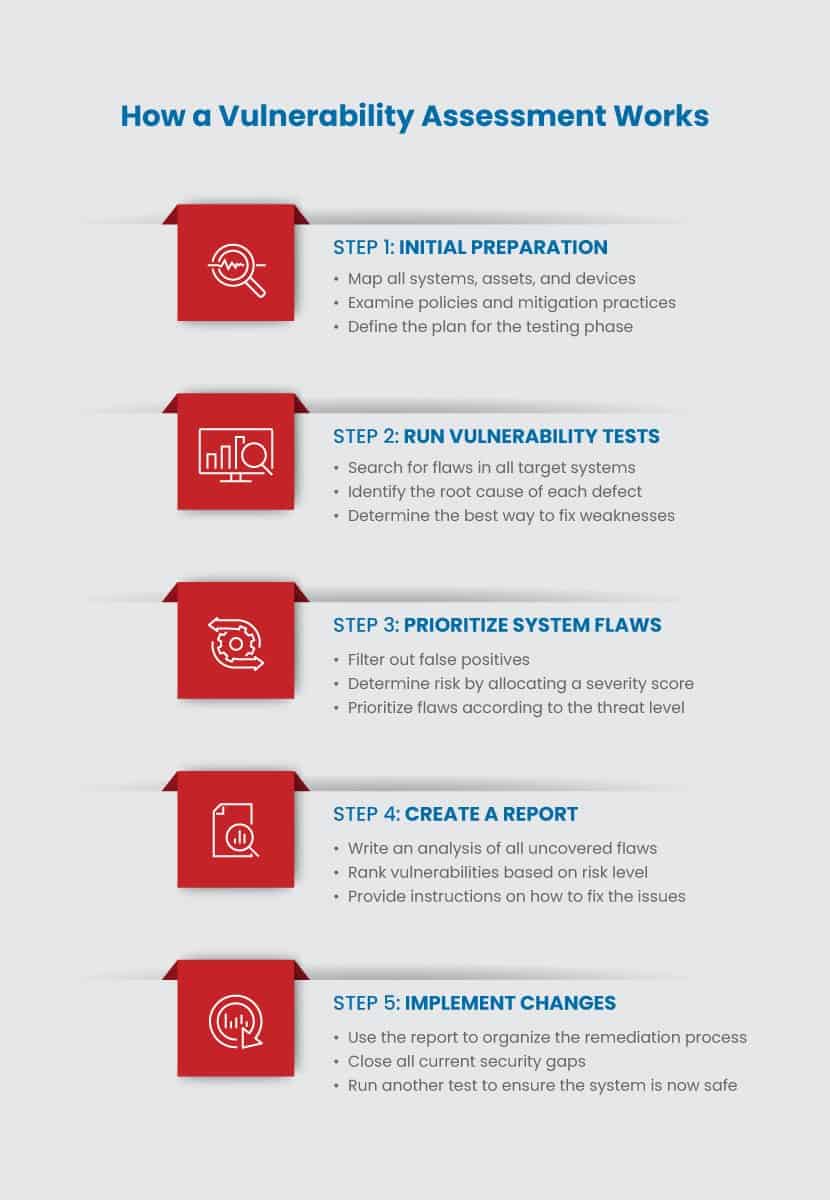
Step 1: Initial Preparation
This step is the planning stage. The team decides the scope and the goal of the upcoming test. Once the plan is ready, the testers examine the hardware and software in the test environment. The team performs the following tasks:
- Identify all subject assets and critical devices.
- Define the value, access controls, and capabilities of all subject systems.
- Establish where sensitive data resides and how data moves between systems.
- Record all the services, processes, and open ports of subject devices.
- Map all endpoints.
- Inspect operating systems (OS).
- Get to know risk mitigation practices and policies for each environment.
The information from this step helps the team both come up with attack scenarios and create a sound remediation strategy. The testing team often makes a central document to structure the process during this step.
Step 2: Vulnerability Assessment Testing
The team initiates scanning on subject devices and environments. Analysts use both automated and manual tools to test the security health of systems. Teams also rely on the following assets for accurate flaw identification:
- Vulnerability databases.
- Vendor vulnerability announcements.
- Asset management systems.
- Threat intelligence.
- Network security audits.
Testers need to identify the root cause of each vulnerability they discover. Determining the flaw’s root cause allows testers to understand the vulnerability’s scope and the best method to fix the issue.
Depending on the target system’s size and the type of scan, a single test can take anywhere between a minute to a few hours.
Step 3: Prioritize System Flaws
The team prioritizes defects according to the threat level. Most testers determine risk by allocating a severity score. Some factors that impact the score are:
- The consequences of a potential attack.
- How easy it is to exploit the weakness.
- The age of the issue.
- Whether the flaw is a common problem or a rarity.
- The room for lateral movement.
- The business functions and sensitive data at risk.
- Patch availability.
- Whether the fault is a matter of public knowledge.
The team must also ensure to filter out false positives during this step. A false positive occurs when a scanning tool incorrectly flags a security defect, which leads to unnecessary remediation work.
Step 4: Create a Vulnerability Assessment Report
Testers compile an analysis report that outlines the uncovered flaws and instructs on how to fix the issues. While minor problems do not require an in-depth explanation, a tester should provide the following information for each medium-to-high risk weakness:
- The name of the vulnerability.
- The date of discovery.
- The method by which the team discovered the threat.
- A detailed description of the flaw.
- Details regarding the affected systems.
- The potential damage an attacker can cause by exploiting the defect.
- Instructions on how to correct the vulnerability.
Quantifying the threat gives a clear sense of the level of urgency behind each flaw. If possible, the team should also provide a proof of concept (PoC) for each significant vulnerability.
Step 5: Implement Changes Per the Report
The company uses the information from the report to close the security gaps within IT systems. The implementation of changes is typically a joint effort between security staff, development, and operations teams.
The risk ranking enables the company to prioritize the remediation process and handle urgent threats first. Ignoring low-risk flaws is also common as some threats have so little impact that fixing them is not worth the cost or the necessary downtime.
The most common remediation actions are:
- Introduction of new procedures and measures.
- Installation of new security tools.
- Software updates.
- Custom patches.
- Addition of zero-trust security.
- Operational and configuration changes.
- Network segmentation.
- Firewall updates.
- Improvements to the cyber kill chain.
Depending on the arrangement, the hired team that ran the vulnerability test can participate in this step.
If the team makes significant changes to the system, a subsequent test is highly advisable. If the team adds only minor updates, the next regular round of testing can evaluate the improved system’s health.
Continuous vulnerability assessments drive cybersecurity improvements. An example of a threat that could have remained undiscovered are Meltdown and Spectre, threats designed to exploit flaws in the design of CPUs and leave no trace of intrusion.
Learn more about how Meltdown and Spectre work and what organizations and individuals can do to protect their data assets.
Vulnerability Assessment Tools
A vulnerability assessment involves the use of both automated and manual testing techniques. Common types of tools include:
- Web application scanners that simulate different attack patterns to test the cyber defenses.
- Protocol scanners that search for unsafe processes, ports, and services.
- Network scanners that discover flaws such as stray IP addresses, suspicious packet generation, and spoofed packets.
Read our article about vulnerability assessment tools for an in-depth explanation of what the pros use to inspect a system.
Why Is Vulnerability Assessment Important?
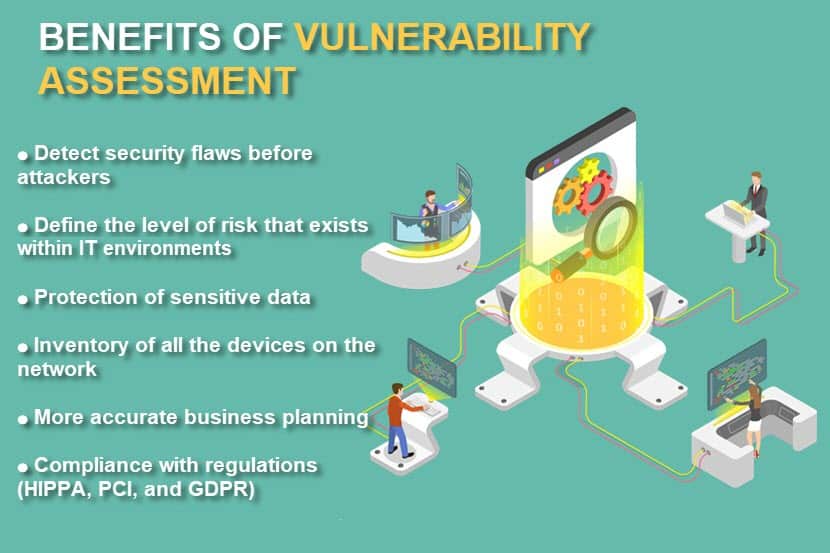
Vulnerability scans enable companies to implement a consistent and comprehensive strategy for identifying and resolving cyber threats. Thorough and regular security checks offer significant benefits to a business, including:
- Early discovery of IT weaknesses.
- Protection of sensitive data and assets.
- Ensured compliance with regulations such as HIPAA, PCI, and GDPR.
- Prevention of unauthorized access.
- Accurate business planning that allows careful security investments.
Assessments reduce the likelihood of successful data breaches and are vital to protecting against all major types of cyber attacks.
Vulnerability Assessments vs. Penetration Testing
Both vulnerability analysis and penetration testing detect weaknesses within an IT system and improve the overall security level. A penetration test also typically includes a vulnerability scan by default.
However, there is a difference between the two testing processes. Whereas a vulnerability scan tries to detect and mitigate system flaws, a pen test involves actual attempts to exploit weaknesses. Pen testers (or ethical hackers) actively try to break into a system by simulating a real cyberattack in a controlled setting. The goal is to prove that:
- A system has an exploitable weak point.
- An attacker can use the vulnerability to damage the system.
Vulnerability scans can also include small-scale pen tests. Analysts use penetration testing tools to detect specific flaws invisible to standard network or system scans.
Both vulnerability assessment and penetration testing play a key role in the fourth phase of an information security risk management approach called Continuous Threat Exposure Management. Find out what Continuous Threat Exposure Management (CTEM) is and how it works.
Vulnerability Assessment vs Risk Assessment?
A vulnerability assessment discovers, quantifies, and prioritizes weaknesses in an IT environment. In contrast, a risk assessment evaluates the probability that certain flaws and threat actors will lead to an exposure or data loss.
A vulnerability scan is larger in scope than a risk assessment. A complete analysis not only evaluates the likelihood of a breach but also deals with potential consequences and strategies for avoiding future incidents.
Create a sound cybersecurity incident response plan to ensure your company is ready for breach attempts.
Ensure High System Resilience
Vulnerability tests are an essential part of any rock-solid IT security strategy. Schedule regular scans of all critical systems to minimize the risk of costly breaches and ensure uninterrupted business growth.
Consider also migrating sensitive workloads to the most secure Cloud platform for a piece of mind. Data Security Cloud is a multi-tenant, secure-hosted cloud infrastructure platform built in collaboration with Intel® and VMware®.