As we speed through digital transformation, the number of vulnerabilities we need to address becomes unmanageable. To decrease the risks of exposure, we need a novel approach that helps us understand potential areas of attack, prioritize our actions effectively, and track progress over time.
Continuous Threat Exposure Management goes beyond just managing vulnerabilities. It is a forward-thinking framework that focuses on managing a broader range of risks likely to impact our business priorities.
This article outlines an effective method for creating a coherent and practical security improvement plan that business executives can easily understand and engineers can implement effectively.
What Is Continuous Threat Exposure Management (CTEM)?
In July 2022, Gartner introduced the concept of CTEM, a framework that enables organizations to continually and consistently evaluate the vulnerability of their physical and digital assets.
The objective of the CTEM program stages is to establish well-defined security and risk management strategies that align with business objectives. By continuously minimizing risk, improving resilience, and promoting collaboration, organizations can enhance their overall security posture.
CTEM overcomes the limitations of traditional information security risk management methods by actively and regularly identifying, assessing, monitoring, and reducing security weaknesses in an organization's infrastructure before they can cause harm.
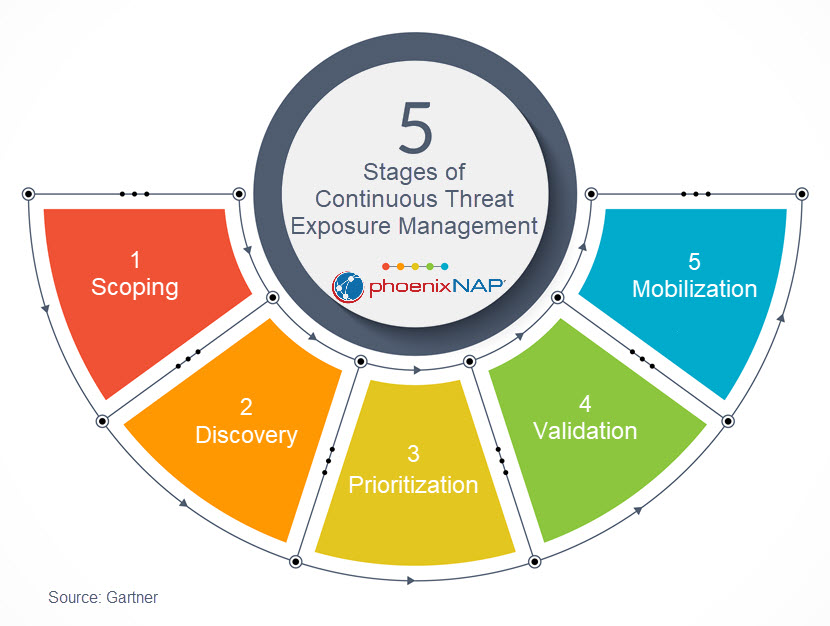
What Are the Five Stages of CTEM?
A CTEM program follows a cyclical structure consisting of five stages, with each stage repeating the iterative process.
1. Scoping
Every CTEM project begins with defining a specific scope that encompasses business-critical assets that need to be identified, tested, and strengthened.
Ideally, scoping should incorporate all stakeholders, including IT Operations, Governance, Risk, Compliance, and asset owners. They need to jointly consider the entire attack surface of the enterprise, both internal and external, including factors such as cloud infrastructure, software supply chain, and application risks, as well as buildings and hardware.
Read our article on the difference between attack vectors and attack surfaces, two interconnected security concepts crucial for effective preparation against malicious activity.
2. Discovery
During this stage, security teams take inventory of assets and assess risk profiles based on the earlier scoping process. They map out assets, vulnerabilities, misconfigurations, technology, and risk to gain a comprehensive understanding.
However, not every vulnerability or misconfiguration is equally relevant. Trying to fix all vulnerabilities immediately is also impractical. Therefore, prioritization is essential to determine which vulnerabilities should be addressed first.
Enhance your security by reading our list of the 17 best vulnerability assessment scanning tools.
3. Prioritization
The purpose of prioritization is to establish which threats are more likely to be exploited and pose an imminent risk to the enterprise. Prioritization goes beyond assigning severity scores to vulnerabilities. Security teams should consider the following factors to make informed decisions:
- Exploitability: Assess how easy it is for an attacker to exploit the threat.
- Effectiveness of Security Controls: Evaluate the mitigation capabilities of existing security measures.
- Network Topology: Understand how network security threats can spread through the organization's infrastructure.
- Risk Appetite: Consider your organization's risk tolerance, prioritizing threats that align with the risk threshold.
- Overall Impact: Evaluate the potential consequences of a threat, including financial losses, reputational damage, operational disruptions, and compliance violations resulting from successful exploitation.
4. Validation
During the validation phase, organizations evaluate how they would handle an actual attack and assess their ability to defend against it. This evaluation must go beyond identifying potential threats and involve validating security controls and determining the order of vulnerability remediation using simulated attacks.
By performing a combination of technical assessments, such as penetration testing, red teaming, data breach and attack simulation, and attack path analysis, Security Teams provide evidence that supports their prioritization decisions and effectively demonstrate the need for remediation to both IT Operations and business stakeholders.
Read our article highlighting the best penetration testing tools for assessing system resilience.
These findings are crucial in the process of establishing and improving a cybersecurity incident response plan.
Information security management is one of the core components of an ironclad business continuity plan. Improve yours by following our 10-step business continuity plan checklist.
5. Mobilization
During the mobilization step, organizations take action to improve their security posture. They integrate the findings from the validation process into the steps needed to fix vulnerabilities, allowing for swift implementation and improved efficiency.
To prevent the accumulation of a long list of unresolved vulnerabilities, it is crucial to address delays caused by approval processes and misunderstandings between different teams. By focusing on priorities that align with business goals, the most relevant threats get addressed promptly. This approach ensures vulnerabilities are addressed before malicious actors can exploit them, thereby safeguarding business continuity management efforts.
It's crucial to involve all stakeholders, even those less familiar with security matters, to ensure a comprehensive approach.
Develop a comprehensive testing culture by understanding the difference between vulnerability scanning and penetration testing.
How Is CTEM Different from Traditional Vulnerability Management Programs?
CTEM distinguishes itself from conventional vulnerability management programs because of the following six characteristics:
1. Proactive Approach
While traditional programs reactively identify and patch known vulnerabilities, CTEM adopts a proactive stance by continuously monitoring the threat landscape. It prioritizes the remediation of identified threats and vulnerabilities before hackers can exploit them.
2. Broad Scope
Unlike traditional programs that focus solely on technical vulnerabilities, CTEM adopts a holistic approach. It recognizes that threat exposure can come from various sources, such as configuration errors, misused credentials, and insider threats.
3. Business-Aligned Prioritization
Traditional vulnerability management often struggles to prioritize remediation efforts effectively, resulting in patching all vulnerabilities regardless of severity. Conversely, CTEM aligns its prioritization with business objectives, focusing on the most critical threats and vulnerabilities that could impact the organization's most valuable assets.
4. Continuous Improvement
Traditional programs typically adopt a point-in-time approach, conducting periodic scans and then moving on. In contrast, CTEM promotes a cycle of continuous improvement, constantly monitoring, evaluating, and enhancing the organization's security posture.
5. Integration with Security Controls
Traditional vulnerability management often operates separately from other security measures. However, CTEM integrates with existing security controls, fostering a more comprehensive and effective approach to managing threat exposure.
6. Emphasis on Validation
While traditional frameworks heavily rely on vulnerability assessments, CTEM places significant emphasis on validation to test the organization's defenses against simulated attacks.
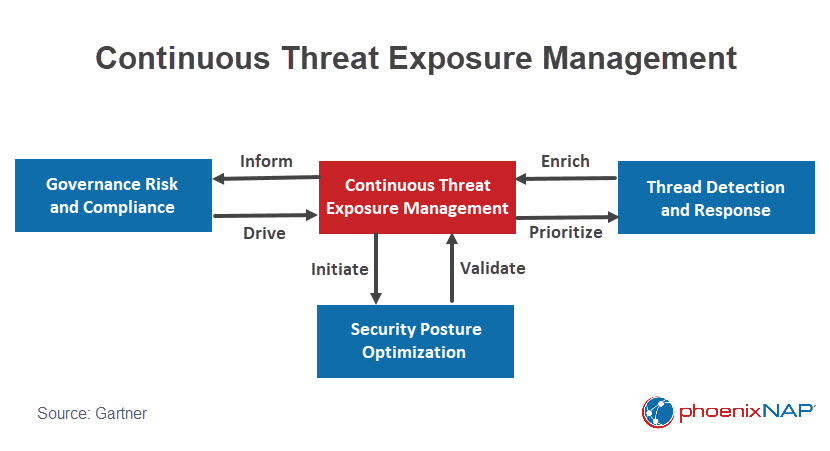
Benefits of CTEM
According to Gartner, organizations that implement a continuous threat exposure management program will experience a threefold decrease in the likelihood of suffering a breach by 2026.
By adopting the CTEM approach, organizations proactively and predictively address threats rather than rely on reactive and responsive measures. This strategy enables them to reduce vulnerability noise, minimize risks, and foster improved collaboration across distinct organizational functions.
However, to effectively implement CTEM, enterprises must ensure that their facilitating tools are not siloed and are fully integrated.
Challenges of CTEM Implementation
Implementing a CTEM program is a worthy initiative, but you must first address some challenges to ensure successful execution. Tackling these challenges early will save time and frustration later.
1. Aligning Non-security and Security Teams
IT infrastructure, DevOps, and security teams often have communication gaps. This disconnect becomes even more problematic when implementing new programs like CTEM. It can lead to confusion about ownership, a lack of alignment on expectations, and other issues.
To address this challenge, involve stakeholders from non-security teams from the earliest stages. Simply providing them with a to-do list is not enough. Take the time to explain the goals of the CTEM program, and ensure they have a proper understanding of its objectives. Seek their input, understand their needs, and identify how you can make their work easier.
Additionally, consider initiating a security awareness training program to educate employees on common types of cyber attacks and their business impact, helping them understand their relevance to their work.
2. Creating a Comprehensive View
A comprehensive CTEM program encompasses various areas, including cloud and software vulnerabilities, as well as network security. Traditionally, each area operates in its silo with separate owners, tools, and issues to address. CTEM aims to unite these areas to aggregate information, enabling everyone to understand priorities and responsibilities and create a holistic perspective.
To overcome this challenge, designate a "point person" who can take a high-level view and understand how all the covered areas converge and impact each other. This person does not need to possess detailed expertise in every tool or security category. Still, they should grasp the big picture and ensure that all areas are accounted for and continuously addressed by professionals with specialized knowledge.
3. Managing Diagnostic Overload
With various areas covered in CTEM, each with its tools and alerts, there can be an overwhelming amount of extraneous noise. Streamlining information is a primary objective of CTEM. Nevertheless, this program can result in significant signal interference from multiple tools.
To address this challenge:
- Accept that fixing every issue is nearly impossible and focus on prioritization and efficiency.
- Identify scopes and exposures that attackers are most likely to exploit and that have the greatest business impact.
- Consider starting with a "crawl, walk, run" approach, where you begin with a small scope and gradually expand as the program matures.
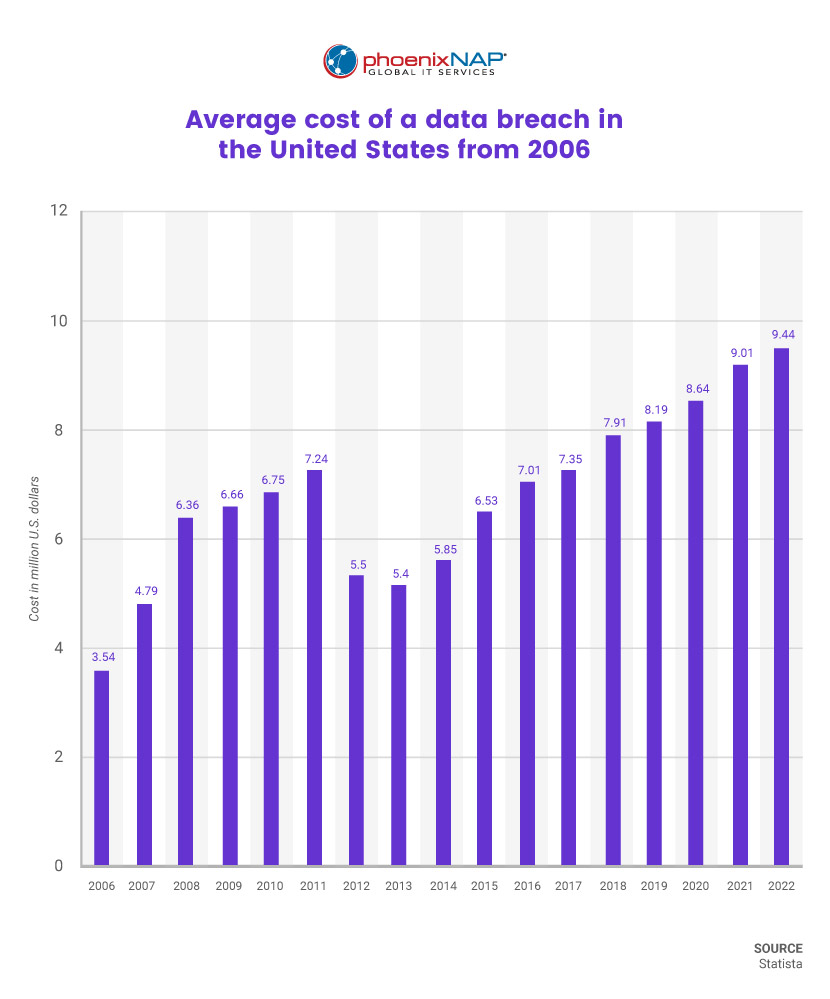
The average cost of a data breach hit a record high of $4.35 million in 2022, marking a 2.6% increase from the previous year and a 12.7% surge from 2020. Read my article to understand the factors that contribute to the costs and discover effective strategies for mitigating these losses.
Conclusion
Traditional security methods are becoming increasingly ineffective against fast-evolving threats and complex attack surfaces, resulting in lengthy, generic reports and slow vulnerability management responses. Continuous Threat Exposure Management (CTEM) addresses these issues by offering a clear, actionable, and cost-effective framework for identifying and mitigating vulnerabilities before attackers can exploit them, ultimately strengthening an organization’s overall security posture.