Many cyber threats lurk in the shadows of today’s digital landscape, requiring organizations to stay alert and on top of their game when it comes to safeguarding sensitive data. Vulnerability scanning and penetration testing are efficient methods to identify weak spots in an organization’s system that cybercriminals aim to abuse to steal or damage a company’s assets.
This article explores the differences between vulnerability scanning and penetration testing, their unique traits, subtypes, and the benefits companies get by implementing these strategies to protect their data.
What Is Vulnerability Scanning?
Vulnerability scanning assesses company networks, systems, and devices for potential vulnerabilities that cybercriminals could exploit. These scans are either automated and set up to run on a regular basis or can be triggered manually when necessary.
Vulnerability scanning is a high-level test that identifies and reports on detected vulnerabilities, but does not remediate them. Patching the detected vulnerabilities to ensure complete protection across company systems is left for the organization’s IT staff to perform.
Learn about the network security threats that can affect your business so you can anticipate them and prevent the damage they may cause.

Types of Vulnerability Scanning
There are several types of vulnerability scanning that your business benefits from:
- Network vulnerability scanning. It utilizes vulnerability assessment tools to identify potential weak points in network devices such as firewalls, routers, and other network components that cybercriminals attempt to exploit.
- Wireless network vulnerability scanning. It checks for vulnerabilities in WiFi networks, such as weak encryption and default passwords.
- Social engineering vulnerability scanning. It tests human behavior and how people respond to and recognize social engineering attacks.
- Application vulnerability scanning. It tests web applications for vulnerabilities, such as SQL injection or authentication flaws.
- Database vulnerability scanning. It scans for vulnerabilities in databases, such as misconfigurations or access controls.
- Physical vulnerability scanning. It checks for physical weaknesses at company facilities and in confidential spaces, such as surveillance systems' blind spots, access control deficiencies, and physical security weak points.
- Container vulnerability scanning. It tests vulnerabilities in container images and their configurations.
- Cloud-based vulnerability scanning. It scans the cloud infrastructure for weak spots in cloud-based applications and services.
- Host-based vulnerability scanning. It tests host systems, such as servers, laptops, and workstations, to identify weaknesses, such as deficient security patches or outdated software.
- API-based vulnerability scanning. It checks for vulnerabilities in APIs, such as in their design, implementation, or deployment.
Choose your hosting service provider wisely based on our article that compares VPS and dedicated servers.
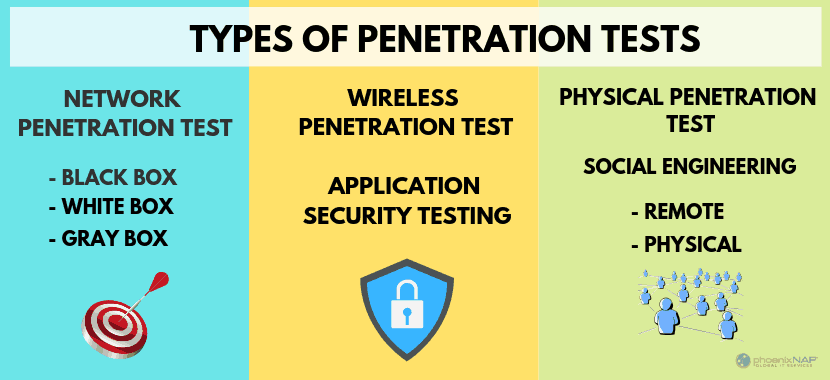
What Is Penetration Testing?
Penetration testing (sometimes referred to as ethical hacking) simulates a cyber attack on the company system to discover vulnerabilities that could be exploited and the potential impact of attacks on data and assets. Penetration testing requires a higher level of expertise since the attacks are triggered manually by skilled professionals dubbed “ethical hackers”. Based on their insights, companies can effectively improve their cybersecurity solutions to protect their assets.
Types of Penetration Testing
Here is a list of standard penetration testing methods:
- Network penetration testing. It simulates cyber attacks to identify weaknesses in an organization’s network.
- Application penetration testing. It identifies and prioritizes threats to web application security and functionality.
- Wireless penetration testing. It checks for wireless network weaknesses that could be exploited for unauthorized data extraction.
- Physical penetration testing. It simulates an attempt to gain access to facilities (data centers, server rooms, etc.) to determine the effectiveness of physical security measures.
- Social engineering penetration testing. It tests human response by simulating common social engineering attacks, including phishing, pretexting, and scareware.
- Client-side penetration testing. It tests for weak points in the software clients use, such as web browsers, media players, document readers, email clients, etc.
- IoT penetration testing. It identifies vulnerabilities in connected software, servers, and applications that organizations link to their systems.
- Red team penetration testing. It enables organizations to challenge their security policies, plans, and solutions through a series of simulated cyber attacks. The goal of this testing method is to learn how the organization’s components work when an incident occurs, thereby understanding their potential weak spots.
Vulnerability Scanning vs. Penetration Testing: What Are the Differences?
Here is an overview of the main differences between vulnerability testing and penetration scanning.
| Point of Comparison | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| Goal | To discover potential vulnerabilities in systems, networks, and applications | To identify the potential impact of mock cyber attacks |
| Methodology | Automated scanning | Manual attacks |
| Accuracy | Potential for false positives in automated attacks | Zero false positives in manual attacks |
| Depth of research | Surface-level | In-depth |
| Frequency | Daily or weekly | Annually or after implementing new security measures |
| Scope | Wider, across the entire system | Narrower; specific networks, systems, and applications |
| Results | A list of vulnerabilities ranked by severity | A detailed report on vulnerabilities and the impact of their exploitation |
| Remediation | Identifies vulnerabilities but does not remediate them | Identifies vulnerabilities and proposes solutions to remediate them |
| Cost | Less expensive than penetration testing due to automation | More expensive than vulnerability scanning due to the high level of expertise required from testers |
Vulnerability Scanning vs. Penetration Testing: Benefits
There are many benefits to vulnerability scanning:
- Cost-effective: The cost-effectiveness of vulnerability scanning is due to its being largely automated and proactive in nature, finding risks before they are exploited.
- Compliant: Vulnerability scanning is a valuable tool that helps companies achieve compliance with industry standards, such as PCI-DSS, HIPAA, and GDPR.
- Prioritization: Vulnerability scanning prioritizes detected vulnerabilities in order of severity, allowing organizations to address critical issues first.
- Frequency: Vulnerability scanning tools support automation, enabling organizations to conduct regular tests and ensure their security protocols are up to date.
- Integration: Vulnerability scanning is easily integrated into the existing IT infrastructure to complement and enhance its efficiency.
- Historical tracking: Vulnerability scanning creates records that can be used to track an organization’s progress over time and analyze changes and trends in cybersecurity.
- Validation and verification: Vulnerability scanning validates the effectiveness of existing security systems and protocols by providing tangible data.
- Broad coverage: Vulnerability scanning tests a wide range of systems, applications, and devices quickly and regularly, providing a comprehensive overview of an organization’s security posture.
On the other hand, here are the benefits of penetration testing:
- Accuracy: Penetration testing is triggered manually, addresses specific weak points, and does not produce false positives.
- In-depth results: Penetration testers simulate sophisticated, real-world attacks, uncovering vulnerabilities that automated scanning might miss.
- Addresses the human factor: Penetration testing focuses on human behavior and our susceptibility to social engineering attacks.
- Holistic approach: Penetration testing focuses on a broader range of security aspects and protocols, including both external and internal security threats.
- Customizable testing: Penetration testing can be tailored to suit specific environments, systems, and protocols being assessed.
- Detailed reporting: Penetration testing identifies vulnerabilities and proposes remediation solutions, helping organizations enhance their incident response.
- Supports regulatory compliance: Penetration testing helps organizations achieve compliance with industry-specific regulations.

Which One Is Better: Vulnerability Scanning or Penetration Testing?
Vulnerability scanning and penetration testing are both crucial tools for organizations to reinforce their security posture.
Because it is frequently automated, vulnerability scanning is a cost-effective method of regularly scanning for vulnerabilities, making it a viable option for businesses of all sizes. As a more in-depth method for identifying weaknesses, penetration testing requires additional time and resources. Based on their specific needs and resources, businesses can choose either method or, ideally, combine them for the most comprehensive results.
Bridging the Security Gap
In the digital era with constantly evolving security threats, companies must ensure their sensitive data and assets are protected. Vulnerability scanning and penetration testing are effective methods for identifying vulnerabilities and mitigating the potential damage cybercriminals can cause to business operations.