Cybersecurity experts have engaged in a relentless cat-and-mouse game against hackers for decades, as every stride forward in security measures is met with cunning attempts to breach them. Whenever a supposed silver bullet is touted as a solution, hackers find a way to exploit its vulnerabilities.
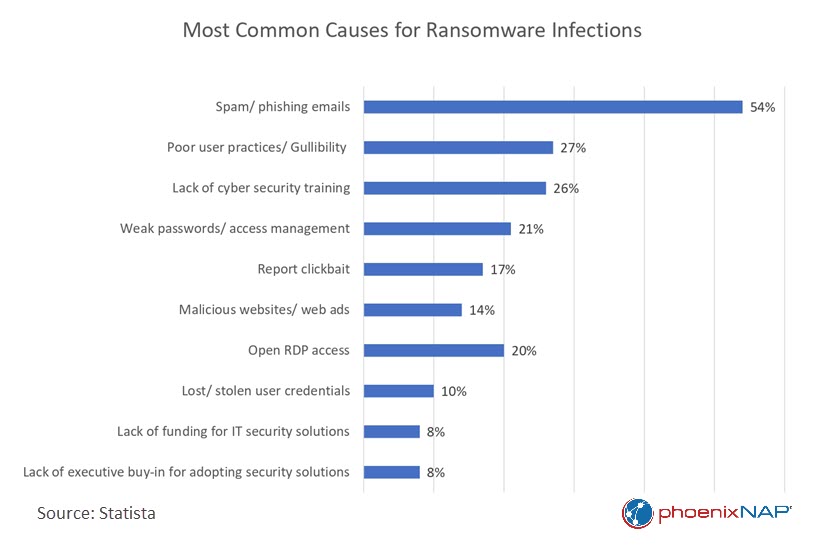
The single unchanging factor at the heart of this arms race is humans, whose susceptibility to manipulation remains as widespread as ever. Findings from Verizon's 2023 Data Breach Report underscore this truth, revealing that a staggering 74% of cybersecurity breaches can be traced back to human actions.
As organizations face increasing threats, the question arises: how can they effectively shield themselves from human error? The answer lies in cybersecurity awareness training and maintaining a well-trained and vigilant workforce.
This article explores the essential components of a robust security awareness program, which will equip your team with the skills to confidently identify and neutralize online threats.
What Is Security Awareness Training?
Security awareness training aims to teach people how to identify and avoid various types of cyber attacks. Security awareness training covers topics such as:
- What is cybersecurity, and why is it important?
- What is ransomware?
- How to recognize phishing emails and websites.
- How to report cyber attacks.
- The importance of strong passwords and regularly changing and securely storing them.
- Recognizing common social engineering tactics.
- Raising awareness of industry-specific data security regulations like HIPAA or HITRUST.
- The importance of software, operating system, and application updates for vulnerability mitigation.
- The best practices for secure remote work.
- The basics of data protection in the workplace.
- How to ensure mobile device security and endpoint protection.
Why Is Security Awareness Training Important?
Without formal security awareness training, you rely on your employees to be tech-savvy and self-educate on cybersecurity matters. However, that is a risky strategy and one that often backfires.
Current cybersecurity statistics paint a worrisome picture. According to a recent study by the University of Florida, 43% of participants couldn't recognize a simulated spear phishing email. Every day, 3 billion phishing emails flood inboxes, and 88% of organizations encounter spear phishing attempts within a year. While modern email filters are advanced, they still fail at a rate of around 7-10%.
Given these probabilities, it's merely a question of when, and not if, your organization will suffer a costly data breach. Therefore, you should prioritize creating a robust human firewall as the first line of defense against cybercriminals who would exploit untrained users, the most vulnerable aspect of your network security.
Additionally, a security awareness program aims to make cybersecurity best practices a natural and integral part of your organization's culture. Humans are inherently social creatures, and as new members join your organization, they tend to observe and adopt the cybersecurity practices already in place. When it becomes the norm among all employees to consistently lock computers and adhere to security measures, sustaining and improving your overall security posture becomes easier.
How to Develop a Successful Security Awareness Training Program
Your first decision centers on whether to outsource your training to external experts or manage it in-house.
Outsourcing provides quick and easy access to specialized knowledge and experience, offering a cost-effective solution when you lack in-house expertise. Outsourcing also provides scalability by eliminating the need for infrastructure and dedicated trainers. However, it may offer less control and potentially misalign with your goals.
Conversely, managing training in-house gives you greater control over aligning content with your organizational objectives. However, it can be resource-intensive and become outdated without regular updates, especially if your organization lacks cybersecurity expertise.
The following components are critical for effective security awareness training, regardless of your choice.
The 9 Stages of Security Awareness Training
Effective learning and development procedures require a systematic approach to establish and implement. What follows is an outline of the steps necessary to create a security awareness training program.
1. Assessment and Analysis
First, you must identify your organization's security needs and conduct an information security risk assessment. You will also need to determine the current level of employee knowledge and awareness, as well as any industry-relevant compliance requirements.
This introductory analysis is critical, as it will be the benchmark to which you compare any subsequent progress.
2. Set Clear Objectives
The second preparatory step is to define measurable training goals and specify what you want employees to learn. Training objectives should translate into actionable behaviors relevant to your industry.
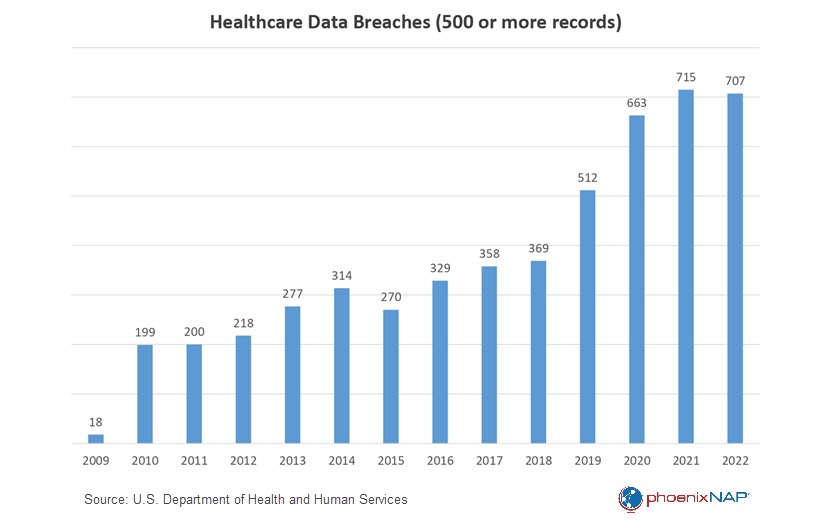
For instance, given the prevalence of phishing attacks in healthcare, training for healthcare employees should include detailed instructions on how to identify and report phishing attempts.
On the other hand, retailers often face point-of-sale (POS) system breaches and data theft due to the high volume of customer transactions. In their case, employees should receive training on securing POS systems, ensuring regular updates of POS terminals, and recognizing signs of tampering.
In 2022, healthcare organizations worldwide faced an average of 1,463 cyberattacks per week, a staggering 74% increase from the previous year. Our comprehensive article on ransomware in healthcare explores the complexities of this issue, empowering you with the knowledge to protect your organization.
3. Content Development
Create or obtain engaging materials, including videos, presentations, and quizzes, tailored to various job roles. Utilize interactive elements, real-world scenarios, and practical exercises to enhance engagement and facilitate active learning.
4. Delivery Methods
Choose suitable in-person or online formats to match workforce preferences and organizational capabilities. For example, online courses offer flexibility and scalability, making them ideal for larger or dispersed teams.
On the other hand, in-person training can be especially effective for smaller groups because it enables direct interaction and immediate feedback. Another possibility is email newsletters, which offer bite-sized information for easy consumption – ideal for boosting engagement while staying informative.
5. Scheduling
When organizing training sessions, select times and dates that won't significantly disrupt the organization's daily workflow. This approach allows employees to participate in the training without hindering their work responsibilities.
For instance, consider scheduling training during less busy periods or staggering sessions for different departments to maintain operational efficiency.
6. Training Implementation
Effective training goes beyond presenting information: it actively engages the participants. During training, provide opportunities for participants to ask questions and seek clarification. Encourage active involvement and discussion to reinforce key concepts.
Additionally, consider incorporating feedback mechanisms like surveys to gauge how well participants comprehend and retain the material. Keep track of participants' progress throughout the training. This could involve tracking attendance, completion rates, and performance in assessments. Monitoring enables you to identify individuals or teams requiring additional support or follow-up training.
7. Assessment and Evaluation
Upon completing the training program, it is crucial to assess its success and gather insights for future improvements. Perfection is difficult to achieve and can’t be the goal, especially if it's your first time implementing a security awareness training program.
You can optimize training by identifying areas of strength and those that require improvement. As the program accumulates data, it naturally becomes more effective and efficient.
In addition to quantitative metrics, incorporating employee surveys into the evaluation process can also be beneficial. These surveys help gauge the program's reception within the organization and delve into subtler nuances. This qualitative data complements the quantitative metrics, providing a more comprehensive understanding of the program's effectiveness.
8. Documentation and Compliance
Maintaining meticulous training records creates a clear trail of accountability and serves as a tangible demonstration of your commitment to cybersecurity. Furthermore, for many industries, training records are a compliance requirement. For example, during a HIPAA compliance audit by the Department of Health and Human Services, an auditor might ask for training records from the past 3-4 years.
Beyond compliance, training records provide valuable insights into the evolution of your security awareness training program, enabling you to adapt to emerging threats and best practices, and ensuring your cybersecurity training program continually improves.
9. Ongoing Education
Criminals are constantly honing their craft and finding new attack vectors to target your organization. As a result, your program must adapt to maintain its relevance and effectiveness. Audit and update your company's security awareness training program at least once a year.
If significant changes occur in your organization's IT infrastructure or industry regulations, or if a new and substantial cybersecurity threat emerges, consider conducting an unscheduled audit and update to address these critical issues.
Learn about the differences between an attack vector and attack surface and the crucial role both play in data protection.
The 4 Stages of Competence
To create a meaningful and comprehensive training program, companies should understand the four stages of competence every individual goes through while learning. These four stages of competence provide a valuable framework for understanding an employee's journey as they become more adept at recognizing and responding to threats. By acknowledging and addressing these stages within the training program, organizations can design a curriculum that caters to different proficiency levels.
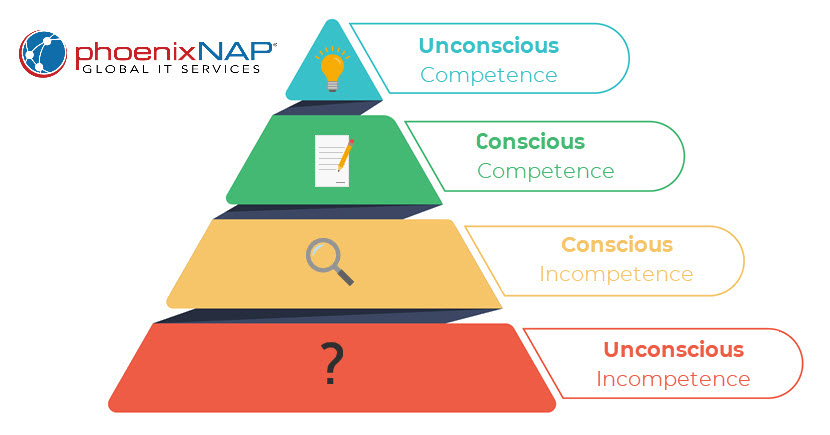
1. Lack of Awareness
This is the "Unconscious Incompetence" stage, or "I don't know that I don't know something." People in this stage are blissfully unaware of their lack of knowledge, and their actions reflect this ignorance.
2. Awareness
At this stage of "Conscious Incompetence," individuals recognize that they lack the necessary knowledge and tools. They become aware of their gaps in understanding, which is a critical first step towards improvement.
3. Step-by-Step Proficiency
Once they reach the level of "Conscious Competence," individuals possess knowledge but must consciously think through the process as they execute it. They may need to access stored information or weigh various options deliberately to arrive at the right solution.
4. Skilled Mastery
This final stage, "Unconscious Competence," represents a level of expertise where individuals perform tasks so well that they don't need to consciously think about them. A good example is piloting a vehicle, which seems intimidatingly challenging to beginners but is second nature to experienced drivers.
Many security awareness training programs fail to achieve mastery, leaving individuals stuck in stages 1 and 2. The key is to design your program to guide them through all four stages. Achieving stage 4 through continuous training and simulations and fostering behavior that effectively safeguards against security breaches is the ideal outcome.

Security Awareness Training Tips
Boost your security awareness program with these simple but effective recommendations.
Make Training Modular
Not all employees need the same level or type of security awareness training. Take IT staff, for instance. They possess a deeper grasp of the technical intricacies of cybersecurity, making them pivotal in upholding business continuity during cyber attacks. Consequently, their training should encompass specialized areas such as intrusion detection, data backups, network security, and incident response planning.
On the other hand, customer support agents may need training emphasizing awareness of social engineering tactics, as they frequently interact with customers and are potential targets for phishing attacks. They should be well-versed in recognizing suspicious requests for information and handling customer inquiries related to security concerns.
Furthermore, the level of security clearance and access to sensitive information determines the extent of training required. Employees with access to highly confidential data or critical systems should undergo more rigorous training to safeguard these valuable assets.
Review your identity and access management policies and grant users access to role-relevant resources only.
Incorporate Real-Life Scenarios
Effective cybersecurity training goes beyond technical details and policies. It involves creating an immersive and relatable learning environment that empowers individuals to protect themselves, their organizations, and society against cyber threats.
Utilizing narratives and real-world examples helps to convince employees how easy it is to fall prey to a phishing attack. It also makes the training more engaging. By witnessing relatable situations, your staff becomes more cautious and thoughtful in their interactions with emails and messages.
Ideally, the training should focus not only on the company's security but also on how individuals can protect themselves personally by employing good "internet hygiene." Include tips on avoiding scams, protecting credit card information, and encouraging participants to share this knowledge with their friends and family.
In 2020, Barbara Corcoran, the host of the reality TV show Shark Tank, almost lost $400,000 to a spear phishing attack. The scammer used a well-crafted email to trick her bookkeeper into sending money to a fake contractor working on one of Corcoran's renovation projects. The hacker's story made perfect sense, as Barbara was heavily involved in real estate investments and renovation projects.
Find more stories like this to use in your security awareness training in our article on social engineering examples.
Get Buy-in From Senior Leadership
Leadership plays a crucial role in endorsing and supporting a successful security awareness training program. Senior management set the tone for a culture of awareness by demonstrating commitment.
Leadership involvement includes:
- Providing necessary resources.
- Emphasizing the program's importance.
- Participating in training.
- Recognizing and rewarding employees for their efforts.
Test Senior Leadership as Well
All employees should participate in security awareness training, regardless of their role or level of experience. You should not exclude upper management from either training or testing.
Executives are four times more likely to be victims of phishing attacks than other employees. In addition, over one-third of executives have clicked on a phishing link, and nearly one-quarter use easy-to-remember passwords, with many keeping the passwords for years.
Furthermore, upper management accounts are particularly valuable to hijackers due to their security clearances and exceptions, which can grant attackers access to sensitive data, systems, and resources.
Learn more about whaling, a type of phishing attack targeting C-level management.
Randomize Phishing Tests
Randomizing phishing tests keeps employees on their toes and makes the tests more realistic. If employees start to see a pattern in the phishing tests they receive, they are more likely to identify them as tests.
Here are some tips for randomizing phishing tests:
- Segment your employees. Segmenting your employees into groups and sending them different phishing tests is an exceptionally effective tactic. The first advantage of sending different phishing tests is that it allows you to tailor the simulations to each group's specific weaknesses and skills, making your simulation more targeted. Additionally, if everyone receives the same phishing test, they are more likely to talk about it with each other and figure out that it is a test, which can reduce the effectiveness of the training.
- Send tests on different days of the week and times of day. For instance, if employees are aware that they only receive phishing tests on Mondays at 9:00 AM, they are more likely to be suspicious of emails arriving on that day. Instead, you could send phishing tests on Mondays, Wednesdays, and Fridays at different times. You can even use a random number generator to determine when to send phishing tests to avoid any pattern.
Make Feedback Constructive
If employees fail a phishing test or training module, it’s vital to provide constructive feedback and additional training instead of punishment. This creates a supportive environment where they feel comfortable seeking help and improving their security awareness, rather than fostering fear and distrust.
On the other hand, when employees identify and report phishing attacks or improve their performance on security awareness training modules, it is essential to celebrate their success. This shows employees that their efforts to improve their security awareness are appreciated, motivating them to continue to learn and improve.
Gamify Training
Implementing gamification elements, such as leaderboards and rewards, helps to motivate participation in security awareness training by making it fun and engaging.
Leaderboards enable employees to compete against each other to achieve the highest score on the training modules. You can reward employees who achieve high scores or rank on the leaderboards.
People are more likely to participate in activities that they enjoy. Gamification elements can make the training more enjoyable by adding elements of competition and challenge, as well as creating a sense of community and camaraderie among employees.

Security Awareness Training Program FAQs
Let's move on to the FAQ section, where we'll address common questions about security awareness training.
How Often to Test Employees
Conducting comprehensive training sessions once a year is a common practice. However, learning doesn't end with a single training session. Employees need reinforcement through periodic updates and assessments to solidify and retain the information provided during training.
Simulations also hold immense value as they provide employees with a controlled environment to apply their knowledge and practice responding to security incidents. The practical experiences gained through simulations empower employees to hone their ability to recognize and mitigate security risks.
How Much Does Security Awareness Training Cost
Security awareness training can cost anywhere from a few dollars to over $60 per user per year, while specialized and advanced programs can cost more than $100 per employee.
Here are the factors that influence training costs:
- The size of your organization. Larger organizations can provide training to their employees at a much lower cost per person than smaller organizations due to cost-sharing, higher bargaining power with vendors, and efficiency gains.
- Delivery method. Online courses are often more affordable than in-person or blended training.
- Content complexity. The depth and complexity of the training materials influence the cost. Basic courses are less expensive, whereas comprehensive and specialized courses are more costly.
- Customization. Tailoring training materials to your organization's specific needs increases costs.
- Additional features. Some providers offer extra features like simulated phishing attacks or reporting tools, which increase costs.
How Long Does It Take to Build a Security Awareness Training Program
Generally, you can expect to spend between 3 and 6 months developing and implementing a security awareness training program. However, this is just a general guideline. The actual amount of time it takes varies depending on the size and complexity of your organization, available resources, and the scope of your program.
Larger and more complex organizations typically need more time to develop and implement a comprehensive training program. Setting up a program is more efficient with a dedicated security awareness team and a sufficient budget.
Finally, developing a comprehensive training program that covers a wide range of topics will take more time than developing a more basic program.

Conclusion
Security awareness training equips employees to recognize and avoid online threats, reducing the risk of costly cyber attacks. However, awareness must lead to behavioral changes. By fostering a cybersecurity culture, employees actively protect the organization’s assets, enhancing security and making the company more appealing to customers and investors.



