Cyber attacks targeting healthcare providers are on the rise, and unfortunately, every year sees a record number of high-profile data breaches. To add insult to injury, any such incident can trigger a HIPAA audit, the failure of which could result in costly fines that can potentially cripple a healthcare organization.
If you are not confident that your organization has made a sufficient investment of time, effort, and money in compliance, take action now before it is too late. This article offers a comprehensive guide to understanding the HIPAA audit process, helping you pass with excellence.

What Is a HIPAA Audit?
A HIPAA audit is an assessment of a covered entity or business associate’s compliance with the Privacy, Security, and Breach Notification Rules of the Health Insurance Portability and Accountability Act (HIPAA).
HIPAA is a US federal law that establishes national standards for protecting the privacy and security of personal health information (PHI) and electronic health information (ePHI).
The Department of Health and Human Services Office for Civil Rights (OCR) conducts official HIPAA audits and enforces HIPAA regulations. The audit process typically involves a thorough review of an organization's policies, procedures, and practices related to HIPAA compliance, as well as an examination of the physical, technical, and administrative safeguards that protect PHI and ePHI.
Third-party auditors or internal audit departments may also conduct HIPAA audits, but these are not official and do not carry the same weight as an audit conducted by the OCR. Rather, these audits are typically used as part of a proactive information security risk management strategy to identify and address potential issues before they escalate into larger problems.
What Triggers a HIPAA Audit?
The OCR usually triggers audits in response to a complaint or breach report. Random audits are rare and are usually reserved for large and established organizations, due to the OCR’s limited resources.
Unfortunately, during audits, the OCR often discovers issues that were not the original trigger for the investigation, highlighting the importance of having an up-to-date and thorough HIPAA compliance strategy.
Here are the main HIPAA audit triggers.
1. Complaints
Two main types of complaints can trigger a HIPAA audit: patient and employee complaints.
Patients may file complaints about being denied access to their medical records or discovering that their PHI has been mishandled. For instance, a patient might see a social media post with their medical chart in the background, which is a clear violation of their privacy.
Another common trigger for an audit is disgruntled employees or whistleblowers. For example, if an employee suspects that their organization is violating HIPAA, they can summon an audit. A similar scenario can happen if they see their colleagues mishandling PHI or if their employer asks them to engage in activities that violate HIPAA. The media usually play a key role in raising awareness of such violations.
2. Breach Reports
Covered entities, as well as business associates, must report all breaches of PHI to the OCR. However, not all breaches will automatically trigger an audit. The OCR will typically consider several factors when deciding whether to start an audit after a breach. These factors include the nature and extent of the breach, the organization's prior compliance history, and the actions taken to mitigate the breach and prevent future incidents.
Here are the main causes of data breaches in healthcare:
- Employee mistakes: Many HIPAA audits are triggered by employee errors, such as falling for a phishing attack, not using strong passwords, or sending patients the wrong medical records.
- Employee misconduct: Employees sometimes intentionally violate HIPAA, whether for personal gain or out of curiosity. Examples include stealing patient records or accessing them without proper authorization.
- Third-party errors: If a business associate experiences a significant data breach, the covered entity will also be audited, as they are responsible for ensuring that their BAs follow HIPAA.
- Security incidents: Lost or stolen devices, particularly unencrypted ones, are a common security incident that triggers a HIPAA audit. Another trigger is unpatched software, leading to malware or ransomware attacks.
In 2022, healthcare organizations worldwide faced a staggering average of 1,463 cyberattacks per week, an increase of 74% compared to the previous year. Our comprehensive article on ransomware in healthcare examines the intricacies of this issue, equipping you with the knowledge needed to protect your organization.
3. Prior Non-Compliance
If an organization has previously violated HIPAA, it will likely be subject to a follow-up audit to ensure that it has implemented corrective measures and is now in compliance. The OCR will issue a Corrective Action Plan (CAP), which outlines the specific actions the organization must take to address the identified violations, mitigate risks, and achieve compliance.
During the follow-up audit, the OCR will thoroughly review the organization's execution of the CAP. They will assess whether the organization has made the necessary improvements and evaluate the effectiveness of the organization's ongoing compliance. Failure to adequately address the violations will likely result in fines and further penalties by the OCR.
Having a HIPAA compliance checklist will greatly assist you in identifying areas that need improvement.
What Will Be Audited?
Virtually every aspect of an organization's operations is potentially subject to scrutiny during a HIPAA audit. The specifics of what an OCR auditor may request will depend on the reason that triggered the audit.
In general, your organization should be ready to present visible, demonstrable evidence of compliance. Relevant evidence includes:
- Documentation of policies relating to compliance with the Privacy, Security, and Breach Notification Rules.
- Incident documentation that provides a record of any incidents, breaches, or complaints related to PHI, as well as your organization’s response.
- Business Associate Agreements, which must outline the business associate’s responsibilities for safeguarding PHI and following HIPAA.
- Administrative safeguards, such as procedures for managing the security and privacy of PHI, including workforce security awareness training, access controls, and incident response.
- Physical safeguards, such as facility access controls and workstation security.
- Technical safeguards, such as access controls, encryption, and audit logging, protect PHI from unauthorized access or disclosure.
The auditor may also conduct on-site visits to assess an organization's physical safeguards and interview employees to ensure they are following established policies and procedures.

Before you decide to use Gmail for PHI communication, consider reading our article on whether Gmail is HIPAA compliant.
How to Prepare for a HIPAA Audit?
Preparing for a HIPAA audit means achieving full compliance with HIPAA regulations. To do so requires more than just having policies in place. It is crucial to have a comprehensive program that includes tangible processes that support your policies.
Moreover, tracking mechanisms are essential for supplying visible, demonstrable evidence of compliance. You need to capture and record all relevant information, such as employee training records, risk assessment reports, and incident response logs. You will use this data to prove to the OCR that your organization has a robust compliance program and is committed to protecting the privacy and security of PHI.
It is also crucial to remember that HIPAA compliance is not a one-time event, but an ongoing process that requires regular monitoring, training, and assessment. Organizations should be on the alert to find and address potential vulnerabilities and adapt policies as needed.
Below are the steps that an organization must take to prepare for a HIPAA audit:
Assign a Privacy and Security Officer
Appointing a Privacy Officer is essential to compliance. They will:
- Oversee all HIPAA-related efforts.
- Serve as the main point of contact for patients, employees, and regulatory agencies.
- Play a key role in workforce training and education.
- Monitor privacy practices.
- Develop security measures.
- Schedule regular policy reviews.
- Document any breach or incident.
The Privacy Officer is typically assisted by the Information Security Officer, whose role is to oversee the company's security program. In a small organization, one person can hold both titles.
Conduct a Risk Assessment
During a HIPAA audit or in the aftermath of a breach, a risk assessment is the first document you'll need to present to an auditor. It proves your commitment to maintaining a robust compliance program and security posture.
A risk assessment also uncovers any gaps and weaknesses within your business, enabling you to address them proactively before they become a problem. Taking the initiative minimizes the risk of unaddressed vulnerabilities being exposed during an audit.
Employee Training
A strong compliance program relies on a well-trained workforce that stays vigilant. All staff members who handle PHI, including contractors and part-time employees, must understand how to secure it during storage, transit, and at rest.
Educating staff on email security best practices is paramount in maintaining compliance. Ensuring secure communication through encryption protocols greatly mitigates the risk of unauthorized access or disclosure of ePHI.
It is also crucial to keep documentation of completed training for employees and provide HIPAA education to new hires shortly after their start date. Annual retraining is mandatory, and auditors often request access to training records from the past 3-4 years.
Note: Check out our guide on HIPAA violations in the workplace and the legal implications and process of documenting a suspected violation.
Review and Document HIPAA Policies and Procedures
It is fundamental to consistently review and update your HIPAA compliance policies and procedures, ensuring they align with changing requirements.
Regular reviews also help ensure that your organization stays abreast of any regulatory changes or emerging best practices. In addition, meticulously documenting all changes in policies and procedures will give you vital evidence in case you are audited.
Review Business Associate Agreements
As a covered entity, it is your responsibility to ensure compliance extends to your business associates. Regularly reviewing and updating all business associate agreements is, therefore, crucial in meeting this obligation.
To ensure compliance, BAAs must accurately reflect current HIPAA requirements and clearly outline the responsibilities and obligations of your business associates when it comes to protecting PHI.
Perform Regular Self-Audits and Monitoring
Consider conducting regular self-audits and reviewing various aspects of your operations to assess their compliance with HIPAA. The main difference between self-audits and risk assessments lies in their focus and scope.
A self-audit is an internal review that finds potential gaps within the organization's policies and procedures. On the other hand, a risk assessment is a broader evaluation that focuses on potential risks and vulnerabilities to the security of PHI.
Leverage Technological Advancements
To mitigate security risks, healthcare organizations can greatly benefit from investing in a robust zero-trust security strategy. Zero trust focuses on verifying and validating every user and device trying to access sensitive data, providing an extra layer of protection.
Additionally, healthcare organizations should prioritize endpoint security and network security. These measures fortify defenses against external threats, ensuring comprehensive protection of PHI from hackers.

For a comprehensive guide on enhancing cybersecurity, we recommend reading our article on cybersecurity best practices.
What Else You Should Know About HIPAA Audits
Not all HIPAA audits are the same. They vary in scope, intensity, and duration depending on the nature and severity of the issue being investigated. Some audits are limited to a specific area, while others may be more comprehensive and cover all aspects of HIPAA compliance.
How Long Does a HIPAA Audit Take?
A HIPAA audit can take anywhere from several weeks to several months, depending on factors such as:
- The scope of the audit.
- The size and complexity of the organization being audited.
- The presence of external entities complicates and lengthens the investigation.
The OCR typically gives advance notice before conducting an audit. Audited organizations are also informed of the audit's purpose, scope, and expected duration. Depending on the severity of any identified issues, the OCR may also conduct follow-up audits to ensure that the organization has implemented the necessary corrective actions.
How Much Does a HIPAA Audit Cost?
If an organization is selected for an official HIPAA audit by OCR, there are no direct costs to the organization being audited. However, there are indirect costs of preparing for the audit, such as hiring consultants, and the opportunity costs of allocating staff time.
Additionally, an organization can perform a voluntary self-audit with an external or internal auditor. External auditors typically charge fees from a few thousand to tens of thousands of dollars, based on the scope of the audit and the amount of time needed.
What Happens if You Violate HIPAA?
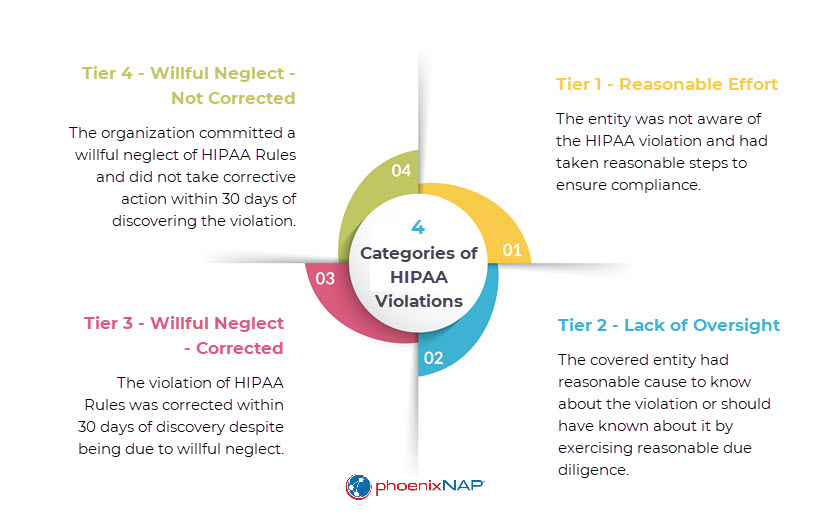
Violating HIPAA incurs significant fines and penalties, both civil and criminal. HIPAA fines and penalties range from $127 to almost $2 million, while intentional or reckless violations can result in imprisonment of up to 10 years. Particularly egregious violations can invite both civil fines and criminal charges, as well as class action lawsuits against the covered entity or business associate.
In addition to fines and legal action, the OCR may also require the offender to take corrective action to address the violation and prevent future incidents. The OCR often issues corrective action plans (CAPs) that require the offender to adopt new policies as directed by the OCR. These CAPs also entail follow-up audits, with stricter penalties if the CAP is not adhered to.
A HIPAA violation will also damage the offender’s reputation if the incident results in media attention. Negative publicity leads to a loss of trust among patients and other stakeholders and can have long-lasting consequences. Finally, HIPAA violators may also lose their medical licensure or accreditation.
Conclusion
It is understandable to feel apprehensive about HIPAA audits. However, they are not meant to be punitive, but rather a means to assess an organization's compliance. If you are genuinely committed to maintaining information safety and security, it is unlikely you will face significant issues during an audit.
Moreover, if the OCR finds compliance issues, they will typically collaborate with the audited organization to implement a corrective action plan rather than impose a fine. In the overwhelming majority of cases, the OCR will first provide technical assistance and guidance to help address the issues and improve overall compliance.
Nevertheless, the OCR is not lenient towards willful neglect of HIPAA and expects organizations to take a proactive approach. The recent high-profile data breaches in the healthcare sector have raised the compliance bar to new heights. At the very least, healthcare providers need to keep the trust of their patients and take the protection of PHI seriously. To meet these expectations, it is crucial to make a good faith effort to follow HIPAA regulations – or risk costly fines and legal action. Also, learn more about the key differences between HIPAA vs HITRUST, two critical frameworks that govern compliance in the healthcare industry.



