Cybersecurity's ever-expanding lexicon and classifications often lead to terms becoming mistakenly synonymous. Malware and ransomware are good examples of this issue, as the two terms are used interchangeably despite being distinct types of malicious software.
This article provides an in-depth malware vs. ransomware comparison. We outline the differences between the two overlapping terms, explain why some people confuse the two, and help you better prepare for all malware-based threats.
Malware vs. Ransomware: Key Differences
Let's start by defining both terms:
- Malware (short for malicious software) is an umbrella term for various programs designed to intrude, disrupt, or damage IT systems and networks.
- Ransomware is a specific type of malware that encrypts data and sometimes deletes original files to force the victim to pay a ransom for the decryption key.
The table below provides a head-to-head malware vs. ransomware comparison:
| Point of comparison | Malware | Ransomware |
|---|---|---|
| End-goal | It depends on the type of malware and may include spying on user activity, hijacking control, gaining unauthorized access to data, disrupting IT operations, setting up other types of cyber threats, etc. | Encrypt as many files as possible and force the victim to pay a ransom for the decryption key. |
| Danger level | The severity ranges from mild to severe, depending on the type of malware. | Devastating and long-lasting consequences (one in five SMBs shuts down permanently after a successful ransomware attack). |
| Go-to attack vectors | Infected email attachments, scareware, phishing, drive-by downloads, malicious ads, links on suspicious websites, and infected portable drives. | Rootkits and social engineering tactics that trick the victim into clicking a malicious link or downloading an infected file. |
| Variety | Many variants (viruses, worms, Trojan horses, spyware, adware, ransomware, spam bots, etc.). | Only two types (crypto and locker), but thousands of variants (WannaCry, Petya, Locky, Cryptolocker, REvil, etc.). |
| Ease of removal | You can remove most malware with an anti-virus tool. | Most variants are either extremely hard or impossible to remove once infected. |
| Main indicators of infection | Corrupt data, slow performance, apps freezing or crashing, browser redirects, annoying pop-ups, and unusual error messages. | Encrypted files and a message demanding a ransom. |
| Best prevention strategies | Keep software up to date, use anti-virus tools, and avoid suspicious downloads and attachments. | Regularly back up valuable data, and be cautious with emails from unknown or suspicious sources. |
What Is Malware?
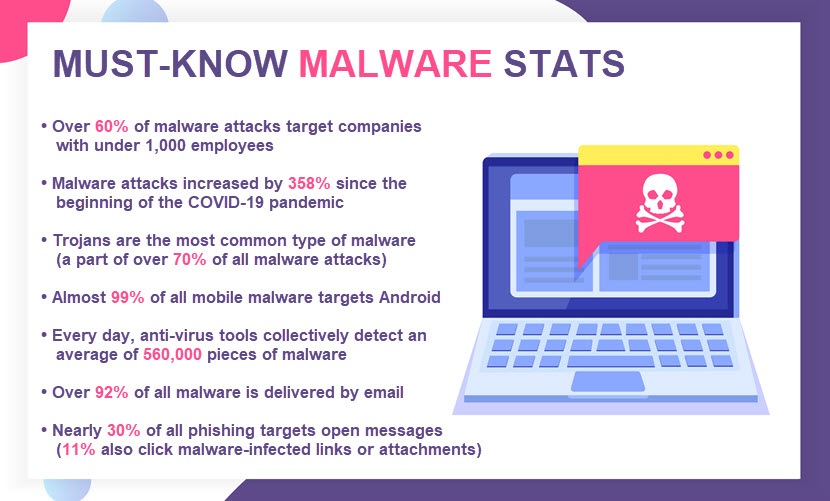
Malware is a broad term encompassing various types of malicious software that harm, exploit, or disrupt devices or networks. Cybercriminals use malware to perform a range of different objectives, such as:
- Spy on the victim's online activity.
- Destroy files or cause data corruption.
- Steal sensitive info required for identity theft.
- Divert the security team's attention away from other malicious activities.
- Slow down a system.
- Misuse the device's underlying hardware.
- Take over the control of a device.
- Redirect traffic.
- Set up other types of cyberattacks (such as APTs or DDoS).
Some forms of malware are more dangerous than others. For example, adware (malware that displays ad banners while you use other programs) hurts the user experience and slows down performance, but is relatively harmless as long as you don't click on the ads. Other types of malware (such as ransomware and rootkits) are hazardous and often result in permanent data loss.
How Does Malware Work?
Different malware types work in different ways, but all of them attempt to go through the same series of steps:
- Infect a system.
- Remain undetected.
- Carry out some form of harmful activity.
All malware infections start with system infiltration. Here are a few common scenarios in which malware installs on a target system:
- A staff member clicks an infected link or attachment in a phishing email.
- Someone accidentally downloads an infected file from a compromised website.
- A disgruntled employee installs malicious software on purpose.
- Someone visits a shady website where they click on an infected ad or download a program with malware-infected files.
- A hacker exploits a zero-day system vulnerability.
- An employee uses an infected device to connect to a corporate network.
Once malware enters the system, the program begins executing its code. Typically, this process occurs stealthily as programs hide their presence by modifying system files or using encryption. Most malware programs also attempt to spread to other systems on the same network.
All malware has a specific payload (the action or attack the program is designed to carry out). Different types of malware have different goals. For example, a virus corrupts files, while spyware attempts to steal valuable data.
Here are the best methods of preventing malware:
- Use anti-virus and anti-malware software.
- Avoid suspicious websites and downloads.
- Keep software and operating systems up to date with the latest patches.
- Use ad blockers to avoid malware-infected pop-ups.
- Think twice before clicking email attachments and links.
- Use a firewall to block unauthorized access to your computer.
- Back up valuable data regularly.
- Don't disable security features on cybersecurity tools.
Remember that some types of malware create hidden files or registry entries to reinstall themselves once you remove the original infection.
Malware Types
Here are the most common types of malware:
- Virus. A virus is a type of malicious software that spreads between computers and causes damage to files and programs. The main characteristic of viruses is that they attach to data and apps to spread to new devices.
- Trojan horses. A Trojan horse is a malicious program that appears as a legitimate application or file. Once executed, Trojans have a wide range of payloads (redirect traffic, set up a back door, export data, etc.).
- Worm. A worm is a type of malicious program that can spread without needing a host file or application. Worms self-replicate and spread across networks by exploiting flaws in protocols and software. The primary objective of a worm is to induce network congestion or establish other types of malware.
- Spyware. Spyware secretly collects sensitive information, including the victim's browsing habits, banking data, and passwords. This type of malware is commonly used by criminals to gather information for identity theft.
- Adware. This type of malware displays unwanted ads and pop-ups on the user's screen. Adware slows down a system and interferes with normal usage.
- Cryptojacking. Crypto-mining malware allows hackers to exploit someone else's computer to mine cryptocurrency.
- Spam bots. A spam bot uses the power and memory of the host device to perform repetitive tasks, such as directing web traffic as a part of a DDoS attack or sending spam messages.
- Rootkits. Rootkits give hackers access to unauthorized areas of a computer by modifying system files or registry entries. Hackers use rootkits to gain remote access to a system and set up more advanced types of malware.
- Ransomware. This type of malware encrypts the data on a device, after which victims must pay a ransom for the decryption key.
Most malware enters a network via employee devices, so boosting endpoint security and enforcing strict shadow IT policies are vital steps in preventing malware-based threats.
What Is Ransomware?
Ransomware is malware that encrypts files on an infected device and instructs the victim to pay a ransom in exchange for the decryption key. Once ransomware executes on a device, the malicious program has several objectives:
- Encrypt as much data as possible.
- Exfiltrate files (transfer data to a remote server).
- Spread to other devices on the network in search of more data.
- Establish contingency plans for future attacks.
Ransomware attacks are highly disruptive and costly for businesses. Here are a few stats that demonstrate the seriousness of this cyber threat:
- Ransomware was the second leading cause of data breaches in 2022 (second only to phishing).
- The average cost of a ransomware attack on a business is $4.54 million (a figure that accounts for ransoms, reputation hits, fines, data recovery, and loss of business due to downtime).
- Businesses require an average of 49 days to return IT systems to a pre-incident state following a ransomware attack.
- The most likely targets for ransomware attacks are U.S.-based businesses (around 47% of all incidents).
- Only 13% of organizations that suffered a ransomware attack in 2022 report not paying the ransom.
Concerned about ransomware? Invest in a steady mix of in-house ransomware prevention and ransomware detection capabilities to stay a step ahead of criminals (or rely on pNAP's ransomware protection and outsource this responsibility to our team of seasoned security experts).
How Does Ransomware Work?
Hackers distribute ransomware in several ways. The most common strategies criminals rely on are:
- Infected attachments in phishing emails.
- Social engineering tactics that trick victims into clicking a link that leads to a website hosting ransomware.
- Malvertising (hacking legitimate online ads to spread malware).
- Drive-by downloads on unsafe websites.
- Exploit kits (programs that scan devices for software vulnerabilities and deploy malware if they detect a flaw).
Once ransomware enters a system, it scans the device for target files. The type of data the program searches for depends on the hacker's instructions (for example, a criminal might set ransomware to encrypt all Word documents and Excel sheets on the system). The ransomware then starts encrypting data and wiping any record of original files.
Most ransomware variants encrypt files at an incredible rate. On average, it takes around 45 minutes to encrypt 100,000 files. Some programs also steal data before encrypting it. That way, hackers can threaten to cause a data leakage if the victim declines to pay the ransom.
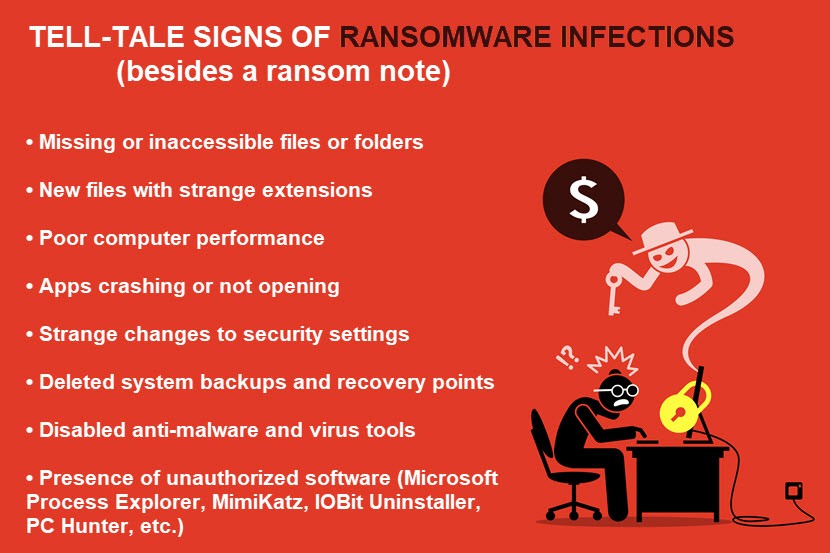
Once ransomware finishes encrypting data, there's no way to restore files without the decryption key. Criminals are willing to provide the key in exchange for a ransom, typically demanded in Bitcoin or other cryptocurrencies to prevent traceability.
Remember that paying the ransom does not guarantee you'll recover lost data. Even if you meet the criminal's demands, there's a strong possibility that:
- You'll never hear from criminals again.
- Hackers will ask for further payments before sending the key.
- Scripts damaged data beyond repair, preventing you from decrypting some, if not most, files.
- Criminals still leak your files or sell them to the highest bidder.
Be one step ahead of the attacker. Learn how to recover from a ransomware attack with minimal downtime and damage.
A vast majority of ransomware attacks target Windows and Mac-based machines, but there's been a 146% increase in Linux-based attacks in 2022. Learn more about this often-overlooked trend in our Linux ransomware post.
Ransomware Types
There are two main types of ransomware:
- Crypto ransomware. This type of ransomware (also known as data lockers) encrypts files on a computer, typically targeting data with a specific extension.
- Locker ransomware. This ransomware type locks the user out of the entire computer instead of encrypting specific data. The hacker unlocks the device only after the target pays the ransom.
While there are only two primary types of ransomware, experts suspect that there are roughly 250 ransomware families out there (most of which are crypto ransomware programs). Some of the most dangerous recent variants are:
- Conti. This ransomware variant first emerged in late 2019. Conti encrypts and exfiltrates data, has advanced encryption techniques, and is notoriously hard to detect. Hackers used Conti in several high-profile attacks, including the attack on Ireland's national health service in May 2021.
- REevil (a.k.a. Sodinokibi). REvil has been active since 2019 and has caused several attacks on high-profile targets (including the attack on Universal Health Services in September 2020).
- DarkSide. This ransomware variant emerged in 2021, when hackers utilized it to launch an attack on Colonial Pipeline, a major US fuel pipeline. Like Conti, DarkSide both encrypts and exfiltrates data.
- LockBit. This variant first appeared in 2019 but gained popularity among criminals following an update in 2021. LockBit is notorious for its fast and efficient encryption process, which, although prone to data corruption, scrambles files faster than most other variants.
- Ryuk. Ryuk has been active since August 2018 and is the weapon of choice for hackers targeting high-value organizations. Unlike most other variants, the criminals behind Ryuk conduct heavy reconnaissance to prepare attacks and include manual intervention during the infection to ensure the encryption process is successful.
Check out our article on ransomware examples for an in-depth analysis of all major ransomware variants that appeared in recent years.
All Ransomware Is Malware, but Not All Malware Is Ransomware
Educating your team on the difference between malware and ransomware clears up confusion and helps prepare the staff for malware-based threats. Since employees are always the most vulnerable attack vectors for malware, ensuring everyone is up to date with the cybersecurity terminology is a priority for every cautious organization.