By 2031, experts predict that ransomware will be infecting a new target (a business, consumer, or device) every two seconds. An organization's business continuity management plan determines its ability to recover from this type of malware.
This article provides a comprehensive guide to ransomware recovery, walking you through every step a company must take during and immediately after an attack. Read on to learn how to recover from a ransomware infection without costly downtime, permanent data loss, or having to pay a ransom.
Learn about different ransomware examples and see how diverse and dangerous this cyber threat has become in the last few years.
Is It Possible to Recover from a Ransomware Attack?
Ransomware recovery is possible if a business has an established backup strategy with up-to-date data backups and a disaster recovery (DR) strategy. These two precautions enable companies to fully recover from an attack without suffering:
- Permanent data loss.
- Prolonged downtime.
In some cases, it's possible to recover from a ransomware attack without up-to-date backups and DR plans. Some malware variants are less complex than others, so it's often enough to:
- Use an anti-virus or anti-malware tool to remove the ransomware and rely on decryption software to restore data to a pre-incident state.
- Reach out to authorities and get a decryption key for that specific ransomware variant.
- Seek assistance from cybersecurity or data recovery experts who can help recover from attacks.
- Use built-in OS features to restore settings to a previous recovery point.
Unfortunately, these reactive measures are rarely helpful for advanced ransomware types. More dangerous variants have no known decryption keys and typically disable or corrupt built-in recovery points. Recovering from these types of ransomware is only possible with up-to-date backups, DR, and a detailed incident response plan.
The best way to fight ransomware is to prevent it, or discover it early, before it gets the chance to do significant damage to your information ecosystem. Learn more about ransomware detection and find out how to prevent ransomware.
Should You Pay for a Ransomware Attack?
Never meet the demands of criminals if you suffer a ransomware attack. Here's why:
- There's no guarantee you'll receive the decryption key after you pay the ransom.
- Many victims who agree to a ransom receive a faulty decryption tool.
- You mark your company as a worthwhile target for future cyberattacks.
- Most ransomware groups ask for further payments after you give in to their initial demands.
- Many variants corrupt data during encryption, so not even a decryption key can restore files.
- Most criminals sell your data to the highest bidder regardless of whether you pay the ransom.
- You'll motivate the criminal to keep using ransomware against other companies.
Additionally, paying a ransom violates regulations in certain regions. Always consult with legal advisors and law enforcement agencies to learn about the legal ramifications before making ransom-related decisions.
Recent surveys reveal that only 26% of ransomware victims recover all data after paying the ransom, which is another reason not to meet the criminal's demand.
How to Recover from a Ransomware Attack
The security team must take immediate action if they detect the presence of ransomware in your network. Below is a step-by-step guide to recovering from a ransomware attack.
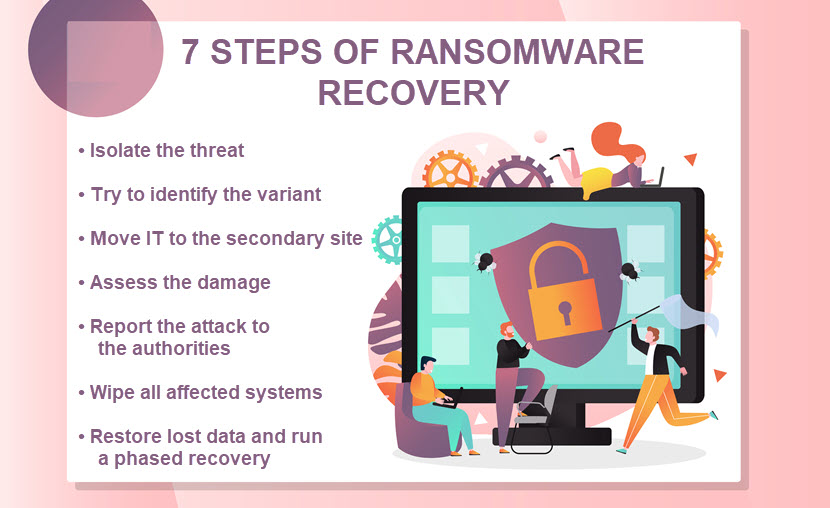
Isolate the Threat
As soon as your team identifies signs of ransomware, your priority is to isolate the threat and stop malware from spreading. You must do the following for every suspicious device:
- Disconnect the device from Wi-Fi.
- Shut down the machine.
- Unplug network cables.
Such a precaution not only contains the spread of malware but also prevents ransomware from receiving instructions from attackers. You should also proactively do one of the following:
- Disconnect all systems with sensitive data until you contain the threat.
- Boost cyber defenses around your most valuable assets.
The security team's primary goal is to determine how far malware has spread through the network. The team must also look for unusual triggers within the environment that could have caused the attack. Common triggers include:
- Clicking a malicious link in an email.
- Software vulnerabilities.
- Opening network ports with suspicious activity.
Speed is paramount at this point. An average ransomware script requires around 45 minutes to encrypt 100,000 files. The longer malware operates, the more damage it does.
Try to Identify the Ransomware Variant
Attempt to identify the exact type of ransomware that infected your system. Here are two websites that help identify thousands of known variants based on ransom notes and the type of encryption:
Many variants offer decryption keys that can be downloaded for free and used to descramble data after cleaning your system. Even if there's no known decryption method, you'll still learn how that type of malware propagates and what data formats are its go-to target.
Move IT Over to the Secondary Site
Next, ensure business continuity by moving over affected systems to a disaster recovery site. A mirrored version of the primary production center ensures that operations continue uninterrupted while the security team addresses the ransomware threat.
The most cost-effective way to build a secondary IT site is to host mirrored versions of systems in the cloud. This strategy is significantly cheaper than creating off-site data centers and has quicker failover and failback times.
If ransomware infects mission-critical data, prioritize pulling backups of those files to make them available for secondary site operations.
Check out our Disaster-Recovery-as-a-Service (DRaaS) and see how we use cloud-based secondary sites to help companies maintain business continuity in times of crisis.
Assess the Damage
Once the secondary site is operational, create a detailed report of all the systems, databases, and devices affected by malware. The goal of this step is to:
- Prioritize recovery efforts.
- Determine the scope of the incident.
- Double-check whether all compromised systems are offline and away from unaffected devices.
Instruct the team to also check for signs of data exfiltration (the process of remotely transferring files to an attacker's server). Exfiltration is a common tactic in ransomware attacks, enabling criminals to steal data before encrypting files. That way, attackers further pressure the victim into paying the ransom by threatening to leak sensitive data.
Report the Attack to the Authorities
Contact local law enforcement or cybercrime reporting agencies and inform them about the infection. If you operate in the US, report the attack to federal agencies via the CISA incident report form. If you're in the UK, reach out to Action Fraud.
If possible, state which variant infected your systems. With a bit of luck, authorities will know how to clean your systems and decrypt files with little to no risk.
Reporting a data breach to the authorities is required by law in 47 U.S. states, so always consult with your legal department when an intruder reaches sensitive data.
Wipe All Affected Systems and Devices
Wipe all systems and devices infected by ransomware while machines are still offline. The safest option is to delete everything on each device and start afresh (including reinstalling the operating system and formatting storage drives).
After wiping a device, check for signs of backdoors to ensure the system is truly clean of malicious software.
In some cases, it's possible to restore the system to a previous version with all programs and files intact. However, this method is not enough to delete more advanced forms of ransomware, so a complete wipe is always the safer strategy.
Restore Lost Data and Run a Phased Recovery
Once you have cleaned all systems and devices, start restoring data from backups. Ideally, a company maintains up-to-date backups to minimize or eliminate permanent data loss.
Always use immutable backups. Even if malicious software reaches an immutable backup, ransomware will be unable to scramble files. Also, if you use encryption at rest, there's no danger of data breaches or data leakage.
Always rely on phased recovery when introducing data back to clean systems. Restore the most essential and critical systems first, and conduct tests to ensure everything restores correctly and securely.
Our backup and restore services enable you to create immutable and encrypted backups that ensure there's no way you permanently lose files no matter what goes wrong.

What Next? Steps to Take After Recovering from a Ransomware Attack
Once you remove ransomware from your systems and you're back up and running, instruct your in-house team (or outsourced experts) to perform a post-attack investigation. This analysis outlines the incident in detail to help you understand the nature and scope of the attack.
Here's a brief to-do list of what you should do during a post-recovery investigation:
- Identify and document all the systems infected by ransomware (servers, workstations, network devices, endpoint devices, etc.).
- Assess the extent of data that ransomware managed to encrypt.
- Determine how malicious software entered the network (e.g., a phishing email, faulty port, vulnerable software, an insider threat, etc.).
- Analyze network and firewall logs to determine how malware spread across the network.
- Examine system, event, and security logs to identify any suspicious activities before and during the attack.
- Evaluate the effectiveness of the team's response procedures during the attack.
- Assess the effectiveness of data backups and DR sites.
Next, develop a security improvement plan to prevent similar attacks from happening in the future. Learn from the incident and identify areas that need improvement to enhance your security posture.
Finally, notify the public if the attack compromised customer or user data. Outline the following info:
- When the attack happened.
- Who was affected by the incident.
- What data the attackers compromised.
- What actions you took to minimize the damage.
If possible, share Indicators of Compromise (IOCs) with as many online communities as possible. IOCs help prevent future attacks and aid other victims in early detection.
How to Prevent Future Ransomware Attacks
Companies must rely on a mix of technical measures, employee training, and proactive security practices to prevent future ransomware attacks. Here are several measures that enhance your defense against ransomware:
- Organize regular cybersecurity awareness training to improve your team's ability to identify suspicious emails, links, and attachments.
- Deploy more or better monitoring tools and firewalls to improve network security.
- Keep OSes and applications up to date with the latest patches.
- Use network segmentation and zero trust security to "build a wall" around your most valuable assets (i.e., sensitive user data, backups, and mission-critical systems).
- Deploy real-time, immutable, and automated data backups.
- Invest more funds into disaster recovery capabilities and incident response plans.
- Introduce additional security measures (e.g., 2FA or SCA, email scanning, more traffic filtering, better threat detection, intrusion detection systems (IDSes), etc.).
- Deploy an enterprise password management tool to eliminate credential reuse and help employees create and store strong passwords.
- Minimize the use of shadow IT devices with software restriction strategies.
- Create and enforce strict IT security policies (e.g., your cloud security or BYOD policies).
- Invest more funds and effort into endpoint security to improve your ability to detect and contain ransomware on employee devices.
- Run occasional attack simulations to test your team's readiness for real-life incidents.
- Encourage employees to report any suspicious activities, even if they were the ones who made the mistake.
- Conduct regular security and vulnerability assessments.
- Keep up with the latest trends in ransomware and stay up to date with new attack techniques and best prevention practices.
Are these measures looking too expensive to implement? If so, learn about pNAP's ransomware protection and our highly effective (yet affordable) mix of immutable backups and cloud-based disaster recovery.
Ransomware Attack Recovery: FAQ
Looking for quick takeaways? Below are answers to some of the most frequently asked questions about ransomware recovery strategies.
Should I Use Decryption Software to Recover My Files?
Many ransomware variants offer decryption tools that can help you recover scrambled files. However, there are a few considerations to keep in mind:
- These programs do not remove ransomware from a system but only decrypt whatever files the malware has encrypted.
- Newer and more sophisticated variants have no known decryption keys.
- The Internet is full of fake and malicious tools that further harm systems instead of decrypting files.
While decryption software plays a role in ransomware recovery, relying on immutable data backups is always a far safer strategy.
Is There Any Other Way to Restore Files?
There is no way to restore encrypted data without a backup, a restore point, or a decryption tool. Restoring data from either of these methods does not remove ransomware presence. Therefore, always wipe systems before recovering files.
How Long Does Ransomware Recovery Take?
On average, ransomware recovery takes between a few days to a week for companies that were prepared for an attack. Ideally, this process occurs with minimal downtime as a DR site takes over operations until the primary server room is free of malware.
However, if a victim is unprepared for an attack, ransomware can take out operations for several weeks or even months.
Failing to Plan is Planning to Fail: Take No Chances with Ransomware Recovery
There were approximately 236 million ransomware attacks globally in the first half of 2022 alone, so it's almost guaranteed you'll face this type of malware at some point. When that happens, your ability to contain the threat and restore compromised files will be the difference between a minor incident and a full-blown disaster.