An immutable backup secures data by making it fixed and unchangeable. This backup type prevents data deletion and makes it recoverable at any time. As a result, immutable backups protect data from accidental or intentional deletion or ransomware attacks.
This article will show what immutable backups are and how they can help you protect your business from ransomware attacks.

Immutable Backups Explained
Data is a business-critical part of any organization. For that reason, it is a primary target for cyber attacks.
Ransomware is a malware type that encrypts data so that it is no longer usable. The encryption can go up to the Master Boot Record (MBR) level to prevent booting. This even extends to data backups.
A ransomware attack brings down vital business services. To gain access to your data, you need to pay a ransom.
A way to mitigate ransomware attacks is to regularly back up data, which is the last line of defense. However, simply making a data copy does not mean it is safe from cyber attacks.
Note: Learn the difference between snapshot and backup.
Advanced ransomware attacks now target backups as well. Attackers can modify or delete a backup and request large ransom payouts. Immutable backups prevent these situations.
Immutability prevents unauthorized data access or deletion. Having an immutable backup ensures there is always the most recent clean copy of your data, safe and recoverable at any time.
Immutable backups are built by copying data bits to the cloud as soon you create them.
After the data is in the cloud, users can set an immutability flag (immutable bits). The immutability flag locks the data, preventing accidental data deletion, malware infections, or data corruption.
A user can set the flag for a specific timeframe. For example, if you set the flag for seven days, you cannot delete or modify the backup during that period.
You can store short-term immutable backups locally or tier data backups into immutable object storage off-site. Therefore, you protect data from unforeseen malicious activity or accidental deletion.
Note: phoenixNAP and Veeam stand together against cyber threats. Check out the phoenixNAP backup and restore solution available across six global locations.
Disadvantages of Mutable Infrastructure
A mutable infrastructure is an IT server infrastructure that can be regularly modified and updated in-place.
Although this infrastructure has its benefits, they come at the cost of several disadvantages compared to immutable infrastructure.
The disadvantages of a mutable infrastructure are:
- Configuration drift. When server configuration changes are not systematically recorded, it is difficult to diagnose or reproduce technical issues.
- Indiscrete versioning. Version tracking is difficult because server changes are not always documented.
- Update failures. Updates are more likely to fail due to various network issues (DNS offline, poor connectivity, unresponsive repositories, etc.)
- Slow debugging. Version tracking issues slow down the debugging process. Hence, users can end up with several update versions and complex production workloads in case of buggy updates.
- Increased risk. A mutable infrastructure increases the risk of data loss and ransomware attacks compared to immutable ones.
- Manual configuration. A mutable infrastructure requires manual server configuration, resulting in a long process when provisioning servers.
How to Implement Immutable Backup Strategy?
Companies often fight ransomware by investing in a robust and resilient defense system. However, it is best to prepare for the worst - the scenario in which a company's defense systems fail.
Implementing an immutable backup strategy is the best way to protect your data and have a fast response to a cyber attack without having to pay a hefty ransom.
Note: Explore the differences between backup and replication.
Many best practices for data backup and recovery are not resistant to ransomware attacks.
For example, data replication to a remote data center does not provide ransomware protection because continuous backups can overwrite the healthy files with encrypted versions. Consequently, it is difficult to determine the starting point of the infection accurately.
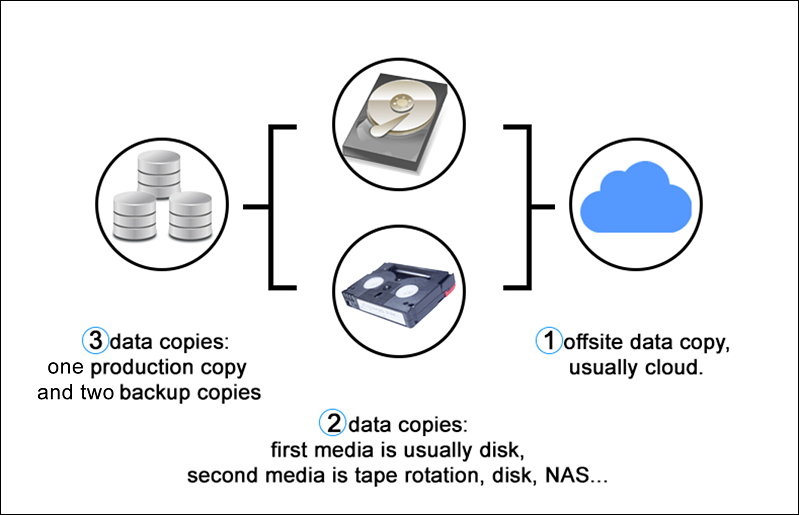
The 3-2-1 backup rule is a data protection strategy that involves having at least three data copies. Two copies are local but on different mediums, and one copy is off-site (e.g., an air-gapped immutable backup on the cloud).
Best practices for implementing an immutable backup are:
1. Data Integrity
The best way to protect a data backup is to store it on a platform that prevents modifications. Some vendors offer object-based storage that makes data modifications or encryption impossible in case of a ransomware attack.
Note: Check out our other article if you want to learn more about data integrity.
2. Zero Trust Model
The Zero Trust model includes strict identity verification for anyone accessing your data backups on a private network. This holistic approach consists of several principles and technologies that ensure an advanced security level and backup safety.
One of the methods is reinforcing security with multi-factor authentication (MFA).
3. Multi-level Resiliency
A good defense strategy combines immutable data backups with the latest cybersecurity technology and employee training.
Platforms that include excess deletion prevention or soft delete options ensure there is a data copy even if ransomware gets in the system.
Another level of protection is to use the WORM (write once read many) format offered many vendors offer.
4. Automate Response
Ransomware attacks usually occur months after a system infection. Attackers wait that long so the ransomware can spread quietly and locate all data backups. Then, it gets your data when everyone is out of the office.
Implement an automated response system in your backup solution to quarantine infected systems even if no one is in the office when an attack occurs.
5. Clean Restore Point
Make sure your data backup is free from malware to prevent reinfection. Scan the backups for malware or indicators of compromise (IOC) before restoring the data.
Store immutable data backups in the WORM format to protect the data from encryption and ensure a fast recovery.
Veeam Immutable Backup - Overview
Veeam offers immutable backups as a powerful and resilient solution against ransomware.
Note: Read our article to learn how to install Veeam Backup and Replication.
The features of Veeam Immutable Backup are:
- Multi-level Approvals
The backup is stored on the cloud and utilizes controls that hinder the possibility of data deletion or modification without strict multi-level approvals.
- Veeam Scale-Out Backup Repository (SOBR)
The SOBR solution, partnered with Capacity Tier, makes sure to write backups into object storage on any platform that supports object store. The platforms include Microsoft Azure, Amazon Web Services (AWS), and IBM Cloud.
AWS S3 or select S3-compatible storage also provides access to Object Lock, enabling backup data to be stored as an immutable backup.
- Veeam ONE Monitoring
Veeam ONE allows users to monitor their environment to stay on top of suspicious or abnormal activities.
The solution analyzes CPU usage, datastore write rate, and network data transmission rate to identify abnormal activities. Any issues trigger the alarm and notify the user to inspect the machine in question.
- Veeam SureBackup
The Veeam SureBackup is an automated solution that notifies the user of an unrecoverable system due to an undetected malware or ransomware infection. The solution automatically scans the existing backups for malware, providing protection at all stages of backup and recovery.
- Veeam Secure Restore
The Secure Restore solution conducts a complete antivirus scan of older backups when restoring them.
The virus definitions are always up to date and help recognize new and dormant viruses in data backups. This process prevents them from infecting the environment after restoration.
Veeam offers various solutions in alliance with different partners, including HPE, Cisco, Lenovo, NetApp, Microsoft, AWS, Google, VMware, IBM, Nutanix, and Pure Storage.
Conclusion
Now you know what immutable backups are and how they can help protect your data from cyber attacks. When it comes to ransomware, the best offense is a good defense.