In 2021, there were an average of 270 cyber attacks per company, which is a 31% increase from 2020. That figure is not going down in 2022 (if anything, it's more likely to go up), so preparing for cyber threats must be at the top of your to-do list. So, what are the different types of cyber attacks you should be ready to face?
This article examines the most common types of cyber attacks you are most likely to encounter in the current cybercrime landscape. We provide an overview of each threat type, explain how victims fall prey to these tactics, and offer tips to help you avoid becoming an easy target for would-be hackers.

What Is a Cyber Attack?
A cyber attack is a malicious attempt by an unauthorized third party to breach an IT system. Attacks vary in sophistication and tactics, but every effort to "break into" a system has one of the following goals:
- Steal valuable files (personal identifiable information, passwords, financial records, etc.) and ask for a ransom under the threat of data leakage.
- Collect valuable data and sell it to the highest bidder (typically on the Dark Web).
- Expose business secrets (such as a patent or code).
- Disable computers or disrupt the victim's network (often to form a launch point for other attacks or get a short competitive edge).
- Steal personal data and commit identity theft (typically with the idea of pulling off an unauthorized money transfer).
- Destroy systems and delete data as a form of "hacktivism."
A successful cyber attack has a long line of adverse effects, including:
- Financial losses (a single successful attack costs companies an average of $200,000).
- Data breaches.
- Loss of user trust.
- Permanent data loss or corruption.
- Potential legal fines and lawsuits are common if you lose customer data during an attack.
- Bad press.
Companies are increasingly investing more in security as criminals get more creative and aggressive with their tactics. Recent reports reveal that 69% of US-based firms are expanding their cybersecurity budgets in 2022 (over 85% expect allocated budgets to increase by up to 50%). The current top areas of investment are:
- Cyber insurance.
- Digital forensics.
- Incident response.
- Security awareness training.
Learn the difference between an attack vector and surface, two overlapping security concepts you must firmly understand to make reliable preparations for malicious activity.
Types of Cyber Security Attacks
A criminal rarely decides to reinvent the wheel when trying to hack a way into a network. Instead, attackers draw upon tried-and-tested techniques they know are highly effective. Let's take a close look at the most common types of cyber attacks a third party might use to breach your company.
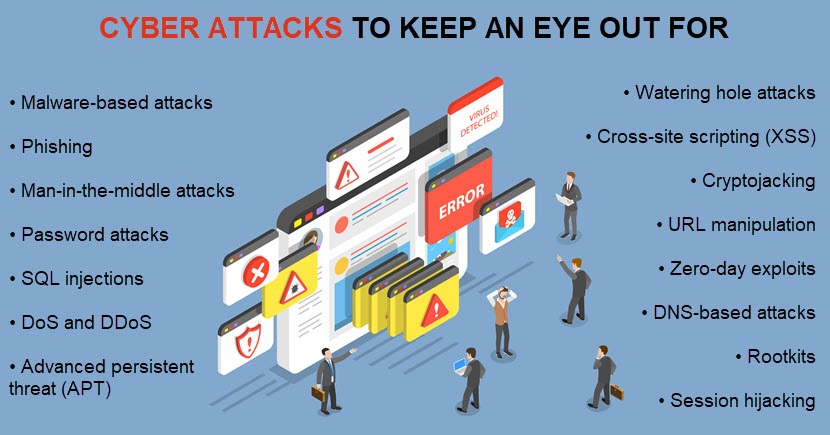
1. Malware-Based Attacks (Ransomware, Trojans, Viruses, etc.)
Malware is malicious software that disrupts or steals data from a computer, network, or server. The malware must install on a target device to become active, after which a malicious script moves past the security measures and performs one or more of the following actions:
- Deny access to a critical system or data.
- Damage data integrity.
- Steal files.
- Spy on user activity.
- Hijack control of the target device (or multiple systems on the same network).
- Disrupt or even render the system inoperable.
While some malware exploits system vulnerabilities (for example, an issue with UPnP), these programs typically breach a system through human error, such as when the victim:
- Clicks on a dangerous link.
- Plugs in a corrupted USB drive or portable hard drive.
- Opens an infected email attachment.
- Visits an infected website that runs a drive-by download (unintentional download of malicious code onto the visitor's device).
Malware is one of the most common types of cyber attacks and has multiple variations. Let's look at all the most prominent ones.
Spyware
Spyware is a type of malware that spies on the infected device and sends information to the hacker. Most attackers use this tactic to spy on user data and browsing habits silently.
If the target accesses valuable data on a spyware-infected device (e.g., logging into a bank account), the criminal gathers sensitive info without the victim knowing something's wrong.
Keyloggers
Keyloggers are similar to spyware, but they differ in that they spy on what you type into your keyboard. That info enables a criminal to gather valuable data and later use it for blackmail or identity theft.
Viruses
A computer virus is a malicious program capable of replicating itself across programs on the target device. If you activate a virus-infected file, the malicious software self-replicates across the device, slowing down performance or destroying data.
Worms
A worm is a standalone malware that replicates itself across different computers. Worms move around via a network, relying on security failures to spread and steal data, set up backdoors, or corrupt files.
Unlike a virus that requires a host computer or operating system, a worm operates alone and does not attach to a host file.
Trojans
Trojans "hide" inside a seemingly legit piece of software (hence the Greek mythology-inspired name). If you install a trojan-infected program, the malware installs on your device and runs malicious code in the background.
Unlike a virus or a worm, a Trojan does not replicate itself. The most common goal of a Trojan is to establish a silent backdoor within the system that enables remote access.
Adware
Adware is a type of malware that displays marketing content, such as banners or pop-ups, on a target device when you visit a website. Some adware also monitors user behavior online, which enables the malicious program to "serve" better-targeted ads.
While adware may seem relatively innocent compared to other malware, many criminals use this tactic to display ads, hiding files with malicious code.
Fileless Malware
Fileless malware does not rely on executable files to infect devices or directly impact user data. Instead, this type of malware goes after files native to the operating system (like Microsoft Office macros, PowerShell, WMI, and similar system tools).
Fileless malware is difficult to detect because it lacks executables, the primary scanning target for network security tools. Recent studies indicate that the fileless approach is up to 10 times more successful than traditional malware.
Ransomware
Ransomware is a type of malware that encrypts files on a target system. Once the program encrypts data, the hacker demands a ransom (usually requested in cryptocurrency) in exchange for the decryption key.
If the victim declines to pay the ransom, the criminal destroys the decryption key, which means there's (usually) no way to restore data. However, many who opt to meet the demands never receive the promised key. Ransomware code often corrupts data beyond repair during the infection process, making the key you receive from the criminal sometimes useless.
Ransomware is a threat to both individual users and organizations. More tech-savvy criminals prepare malicious packages that attack multiple computers or go after a central server essential to business operations.
Want to learn more about ransomware? Check out these articles:
- Ransomware Examples: 25 Most Famous Ransomware Attacks
- How to Prevent Ransomware: 18 Best Practices
- Linux Ransomware: Famous Attacks and How to Protect Your System
- Terrifying Ransomware Statistics and Facts
- How to Use Immutable Backups to Fight Ransomware
Our ransomware protection enables you to use various cloud-based solutions to ensure you never end up in a situation where paying a ransom is the only way to get your data back.
2. Phishing Attacks
A phishing attack occurs when someone attempts to deceive a target with a fraudulent email, text (referred to as SMS phishing or "smishing"), or phone call (known as voice phishing or "vishing"). These social engineering messages appear to be coming from someone official (like a colleague, bank, a third-party supplier, etc.). Still, the imposter is actually trying to extract sensitive info from the recipient.
Some criminals do not ask for info directly. A hacker might try to get the victim to click on a link or open an email-attached file that:
- Downloads and installs malware on the device.
- Leads to a phishing website (typically a fake login page) that steals data if you type in credentials.
Phishing is among the most popular types of cyber attacks. Simple to pull off and highly reliable, recent reports reveal that phishing tactics were a part of 36% of data breaches in 2021.
Many phishing attacks target as many individuals as possible, but some focus on a specific team or person. Let's take a closer look at these more targeted tactics.
Spear Phishing Attacks
Spear phishing goes after a specific individual. The attacker uses personal info about the target (gathered on social media, bought on the Dark Web, or collected via other phishing attacks) to make a more credible message tailored to that person.
Email is by far the most common attack vector for spear phishing. If criminals decide to use an email, they have two choices:
- Hack someone's email and reach out to the target from a real account.
- Use email spoofing to create a new address that closely resembles the email being impersonated.
Hackers usually time-spear-phish emails to make a more compelling message. For example, a criminal may wait for the target to go away on a business trip or make a new hire and create a strategy centered around those unique circumstances.
Angler Phishing Attacks
An Angler attack happens when a phishing imposter targets someone on social media and attempts to steal their credentials outside a corporate network. There are no strict firewall rules or custom IDSes to stop spam messages, which is why this relatively new phishing tactic has had much success in recent years. People tend to be more guarded on social media than when viewing messages on official email addresses.
Whaling Attacks
Whale phishing occurs when an attacker targets a high-profile employee, such as the CEO, COO, or CFO. The idea is to target someone who has the authorization to make significant money transfers.
While harder to pull off than trying to trick a lower-ranking employee, whale phishing is the most profitable form of phishing. Profits often reach millions of dollars, so C-level executives must always be on guard for such tactics.
Phishing is a typical first step to CEO fraud. These scams are now a $26-billion-a-year industry, so check out our article on CEO fraud for an in-depth look at how to counter this threat.
3. Password Attacks
Passwords are the most common method of authenticating users when accessing a computer system, which makes them a go-to target for cyber attacks. Stealing someone's credentials allows a hacker to access data and systems without overcoming cybersecurity measures.
Recent studies reveal that 20% of data breaches start with a compromised credential. Criminals rely on a variety of methods to get their hands on an individual's passphrase, including using:
- Social engineering.
- Hacking a password database or a company's password management platform.
- Spying on an unencrypted network transmission.
- Guessing the password (usually with a bot).
- Paying one of the employees to share their password.
Let's explore the most common password-based types of cyber attacks.
Brute-Force Attack
A brute-force attack involves a program that systematically tests all possible character combinations to guess a password. The easier the password is, the quicker the program does its job.
This simple method is time-consuming, which is why hackers always use a bot to crack the credentials. Here are the most popular programs attackers rely on to brute-force a passphrase:
- Aircrack.
- Cain.
- Abel.
- John the Ripper.
- Hashcat.
Hackers often use basic info about the target to narrow the guessing process, "feeding" the bot with personal data (such as job titles, school names, birthdays, family and pet names, etc.). The program then tests combinations of that data to speed up the deciphering process.
Preventing a brute-force attack does not boil down to using unique passwords. A top-tier program can crack a seven-character password in under 30 seconds. Using lengthy, alphanumeric passwords is the most reliable way of preventing brute-force attacks.
Dictionary Attack
A dictionary attack is a strategy in which a hacker uses a list of common passphrases to gain access to the target's computer or network. Most hackers purchase previously cracked passwords in a bundle on the Dark Web, but some dictionary attacks rely solely on common words and phrases.
Password Spraying
Password spraying is a strategy in which a hacker attempts to use the same password across as many accounts as possible. For instance, a bot might crawl the Internet, attempting to log into every profile using a "password1" credential.
While not too reliable a tactic at first glance, spraying takes on a new light when you consider that over 3.5 million U.S. citizens use "123456" as a password.
Our guide to strong passwords explains a multitude of simple ways to create passwords that are easy to remember and impossible to crack.
4. Man-in-the-Middle Attacks
A man-in-the-middle attack (MitM) occurs when a hacker intercepts in-transit data moving between two network points. An attacker hijacks the session between a client and host, which creates an opportunity to view or edit data. A more common name for the MitM is an eavesdropping attack.
The main problem with MitM attacks is that they are very challenging to detect. The victim believes the information is being sent to a legitimate destination (which it is), but there are often no signs that the data has made a "pitstop" along the way.
There are two common points of entry for a MitM attack:
- Unsecured public Wi-Fi that does not have sufficient network security.
- Pre-installed malware that works in the background of the sender's or the recipient's system (or the network as a whole).
For instance, suppose you're using the Wi-Fi at a local coffee shop and decide to check your bank account balance. You log in and send info to a bank's server, but a hacker intercepts data and captures your username and password. There's no VPN to protect info, so the hacker gathers everything needed to log into your account and drain all funds.
Want to learn more about the MitM threat? Our article on man-in-the-middle attacks goes through everything your security team needs to know about this strategy.
5. SQL Injection Attacks
An SQL injection enables a hacker to "trick" a website into revealing info stored within its SQL database (login data, passwords, account info, etc.).
Injections are a bit more technical than an average brute-force attack or a phishing strategy, but even a novice hacker knows how to pull these attacks off. The attacker types in predefined SQL commands into a data-entry box (such as a login field). Once injected, commands exploit a weakness in database design and can:
- Read sensitive data.
- Modify or permanently delete stored files.
- Trigger executive functions (like causing a system shutdown or changing user permissions).
6. DoS and DDoS Attacks
Denial of Service (DOS) and Distributed Denial of Service (DDoS) are cyber attacks that aim to overwhelm a system, server, or network with fake requests. The attackers spam the target until they exhaust all resources or bandwidth, rendering the system unable to fulfill legitimate requests.
Here's the difference between DOS and DDoS:
- A DOS occurs when a hacker uses false requests or traffic to overwhelm a system until it fails or goes down.
- A DDoS is essentially the same type of attack, but with the hacker relying on multiple malware-infected devices to crash the system more quickly. IoT devices are a common choice for hackers building these "bot armies."
The most common types of DoS and DDoS attacks are:
- Teardrop attack.
- Botnets.
- Smurf attack.
- Ping-of-death attack.
- The TCP SYN flood attack.
The goal of DOS and DDoS is not to steal data but to slow down operations. Sometimes, a hacker uses a DDoS attack to distract the security team and create a window of opportunity to perform other malicious activities.
Learn about the most effective methods of preventing DDoS attacks and see how the pros ensure hackers cannot overwhelm a system with illegitimate requests.
7. Advanced Persistent Threat (APT)
An APT is a type of cyber attack where an intruder maintains a long-term presence within a system without the victim's knowledge. The goal of these attacks varies, but the most common objectives are to:
- Steal large amounts of business data.
- Establish a source of corporate espionage.
- Sabotage infrastructure.
- Cause a long-term service outage.
- Perform a total website or app takeover.
An APT is more complex than other types of cyber attacks. Criminals often form a full-time team to maintain a months-long presence within the target system. These attacks rarely rely on automation as criminals develop custom programs and tactics for breaching a specific tech stack.
Our article on APT attacks offers an in-depth look at this potentially business-ending threat.
8. Zero-Day Exploits
A zero-day exploit is a security flaw within a piece of software that exists without the admin's knowledge. For instance, a company might release a new app version with an unidentified weakness that a hacker can exploit.
Once the team discovers the flaw, they have "zero days" to fix the issue, as hackers are likely already working on exploits.
A zero-day exploit is an umbrella term that covers any malicious activity that exploits a system weakness that has not yet been patched. Companies must be wary of zero-day vulnerabilities whenever they update apps or services, so they must invest in proactive flaw detection and agile threat management.
9. Watering Hole Attacks
A watering hole attack is a strategy in which a hacker infects a website or sets up a malicious copy of a page that a specific user group is likely to visit. This strategy targets a specific group of end users, prompting attackers to profile their targets and identify their preferred websites.
Once the target interacts with the malware-infested website, the intruder gets an opportunity to perform malicious activities (steal login details, inject malware, gain access to the network infrastructure, set up remote controls, etc.).
10. Cryptojacking
Cryptojacking is a cyber attack that enables a hacker to secretly use a computer's processing power to mine for cryptocurrencies (most commonly Bitcoin or Ethereum). Most infections occur when the target:
- Visits an infected website.
- Opens a malicious link.
- Clicks on a malware-infected ad.
Cryptojacking severely slows down the system, but it also causes other vulnerabilities. The malicious program often tempers with firewall settings, which creates more space for other threats.
Cases of cryptojacking nearly quadrupled from 2020 to 2021. Recent reports suggest that one in 500 Alexa sites hosts crypto mining malware.
11. URL Manipulation
URL manipulation (or URL rewriting) happens when an attacker changes the parameters in a URL address to redirect the victim to a different website. This tactic typically happens via a malicious script and leads the victim to a phishing or malware-infected page.
URL manipulation is not URL poisoning (also known as location poisoning). Poisoning a URL involves tracking Web visiting behavior by adding an ID number to the URL when a user visits a particular site. Hackers then use the ID to track the visitor's browsing history.

12. DNS-Based Attacks
The Domain Name System (DNS) protocol is frequently exploited, allowing hackers to launch cyber attacks. Let us look at the two most common ones: DNS tunneling and spoofing.
DNS Tunneling
DNS tunneling uses the protocol to tunnel malware and data through a client-server model while bypassing the firewall and other security measures. Once a malicious program enters the system, it latches onto the server and gives the hacker remote access.
Inbound DNS traffic carries commands to the malware, while outbound traffic enables a hacker to steal data or respond to malware requests (such as changing code or installing new access points).
DNS Spoofing (or "Poisoning")
DNS spoofing enables an attacker to send traffic to a fake (or "spoofed") website and gather data from unwitting visitors. These websites are an identical replica of the legitimate site (typically a copy of a login page for a bank or a social media account) that sends info directly to hackers once you type in the credentials.
Hackers also use DNS spoofing to sabotage a business by redirecting visitors to a poor-quality page, often with mature or obscene content. Some companies employ this tactic as an underhanded means of attacking a competitor's reputation.
Learn about the DNS security best practices and see the best proactive ways to keep your DNS-powered systems healthy.
13. Cross-Site Scripting (XSS)
A cross-site scripting (XSS) attack exploits vulnerable websites, enabling criminals to embed malicious code on web pages and apps. A hacker injects a payload with malicious JavaScript into a website database, which executes as a part of the HTML body when someone requests to open a page in their browser.
When the malicious script executes, the hacker bypasses access controls and hijacks the account. Tech-savvy hackers also use XSS to exploit and create additional security flaws, such as laying the groundwork for malware, taking screenshots, or collecting network data.
15. Rootkits
Rootkits are malicious programs that give an intruder unauthorized admin-level access to a computer or other software. A criminal often uses a rootkit to:
- Remotely access the target computer.
- Edit system files and data.
- Exfiltrate data without the victim's knowledge of the breach.
- Install keyloggers and other malware.
Rootkits are notoriously hard to detect as they "hide" deep within the operating system. Top-tier programs also impact anti-virus settings, making the detection process even more challenging. Most rootkit infections spread through email attachments and drive-by downloads on unsafe websites.
16. Session Hijacking
Session hijacking is an advanced form of a MITM attack in which an imposter takes over a session between a client and the server instead of only spying on the communication. The hacker steals the client's IP address, and the server continues the session because it has already formed a trusted connection with the device.
Once intruders hijack a session, they can do anything within the victim's account permissions. For instance, if a criminal hijacks a session during an admin's access to a company's database, the attacker can view, edit, or destroy files.
Most security teams focus on external threats when preparing for cyber attacks. In actuality, an insider could do just as much if not more damage than a third-party hacker—learn how to prepare for insider threats and see how smart companies deal with dangers from within the organization.
How to Prevent Cyber Attacks?
Let's look at the most effective ways to prevent the different types of cyber attacks discussed above:
- Use strong passwords that are unique for every account.
- Do not include everyday phrases, personal info, or simple number sequences in credentials.
- Keep all apps, browsers, OSes, and devices up to date with the latest patches.
- Change passwords every few weeks.
- Disable password hints on your apps and websites.
- Boost network security with strict access controls, firewalls, segmentation rules, traffic analysis, and intrusion prevention systems (IPS).
- Perform regular network security audits.
- Scrutinize emails for loopholes and grammatical errors, especially when confronted with an unsolicited message.
- Rely on an anti-virus protection tool for threat detection.
- Never click on links or attachments in an email from an unknown sender.
- Stay clear of public Wi-Fi networks.
- Organize regular employee awareness training.
- Use VPN when accessing the corporate network outside of the office.
- Perform daily data backups.
- Use account lockout and two-factor authentication to prevent password attacks.
- Ensure employees know how to keep their BYOD devices safe.
- Never download or install anything unless you're interacting with a verified source.
- Enforce zero-trust security policies.
- Know how to recognize warning signs (network slowdown, website crashes, etc.).
- Limit the info your company shares on its official website and social media.
- Keep data safe with at-rest encryption, in-transit encryption, and confidential computing (protecting data during processing). Also, ensure your key management has no exploitable flaws.
- Form a Cyber Incident Response Team (CIRT) that develops response strategies, disaster recovery plans, and cyber kill chains.
- Create a cloud security policy to ensure your use of cloud computing does not lead to weaknesses.
- Use an ad blocker when browsing the Internet.
- Organize penetration tests to assess how systems and staff respond to realistic simulations of various cyber attack types.
Do you rely on in-house hosting? Then your security plan must also include hardware protection—refer to our article on server room design to learn how companies keep on-site infrastructure safe.
The Best Way to Counter Different Types of Cyber Attacks Is to Understand How They Work
Is the goal of this article to make you paranoid? No, but we want to make you aware of the various types of cyber attacks you may encounter. Once you know how an average hacker thinks, creating an effective protection strategy becomes easier. Use this article to stay a crucial step ahead of would-be criminals looking to make a quick buck off your company.