Ransomware is malicious software made to extort money from individuals, businesses, and even governments. From simple lock screens to sophisticated code capable of encryption and data exfiltration, ransomware has evolved radically over the years.
As hackers adapt to exploit vulnerabilities and evade detection, knowing their tactics is crucial for staying safe. In this article, I will list the most famous ransomware examples and, hopefully, equip you with the knowledge you need to protect yourself in an ever-evolving threat landscape.
Ransomware Attack Examples
From the AIDS Trojan, distributed on floppy disks, to the audacious Petya, we will cover the technical and operational characteristics of these ransomware strains. But first, let us cover essential ransomware concepts needed to understand the examples:
- Encryption: Encryption is the process of converting data into a coded form that you can only decipher with a unique decryption key. Ransomware employs strong encryption algorithms to lock victims’ files, making them unreadable without the decryption key.
- Ransom Demand: Ransomware attackers demand payment from the victim to release the decryption key and restore access to the encrypted files. The ransom amount can vary widely, and hackers typically request that payments be made out in anonymous and difficult-to-trace cryptocurrencies like Bitcoin or Monero. Paying the ransom does not guarantee that the attackers will provide the decryption key or release the encrypted files. Therefore, the best course of action is to report the incident to law enforcement and seek assistance from cybersecurity professionals who may be able to help with recovery options.
- Exploitation: Ransomware often exploits vulnerabilities in software or operating systems to gain unauthorized access. Attack vectors include phishing, exploit kits, malicious email attachments, and other types of cyber attacks. Ransomware also often takes advantage of vulnerabilities in outdated software or uses social engineering to trick users into executing the payload.
- Propagation: Once ransomware infects a system, it can spread within a network or to other connected devices. Some ransomware types have worm-like capabilities that allow them to autonomously move through vulnerable systems without requiring user interaction.
- Ransomware as a Service: Given the widespread adoption of Software as a Service, it is no surprise that the concept has made its way into the realm of malware. Ransomware as a Service (RaaS) is a model where cybercriminals develop and distribute ransomware to other individuals or groups, also known as affiliates or partners, who then conduct the actual attacks. In this model, the creators of the ransomware function as service providers, offering the malware and its infrastructure to others for a fee or a share of the profits.

Now that we have covered the basic concepts of ransomware, let us delve into the list itself.
1. WannaCry
WannaCry, released in May 2017, was one of the most widespread and damaging ransomware attacks. Also known as WannaCrypt, and Wanna Decryptor, it was an encrypting worm primarily focused on computers that ran outdated versions of the Windows operating system. The attack had global reach, affecting an estimated 200,000 computers across 150 countries and causing billions of dollars in damage. Some of the hardest-hit victims included government agencies and large corporations.
WannaCry had the exceptional ability to spread without victim participation by leveraging the EternalBlue vulnerability. Notably, the United States National Security Agency (NSA) discovered the exploit but chose not to disclose it to Microsoft or the public. Many criticized this action because a patch could have been developed before WannaCry appeared if they had uncovered the vulnerability.
2. BitPaymer
BitPaymer emerged in August 2017 as a virus that encrypts a wide range of stored files and appends the “.locked” extension to their filenames, immediately rendering the compromised data unusable. It specifically targeted medical institutions, using email-related methods and exploiting vulnerabilities in the Remote Desktop protocol.
BitPaymer creates a separate text file for each encrypted file, exemplified by the generation of a sample.jpg.readme.txt files corresponding to the original sample.jpg file. These text files contain messages that inform victims about the encryption and urge them to contact BitPaymer’s developers to obtain decryption instructions.
Healthcare is one of the sectors most vulnerable to ransomware attacks. To learn why, read our article on ransomware in healthcare.
3. DoppelPaymer
Most experts believe that DoppelPaymer is based on BitPaymer due to similarities in code, ransom notes, and payment portals. However, DoppelPaymer surpasses BitPaymer’s encryption rate and employs more sophisticated network infiltration techniques.
Once downloaded, it installs additional malware onto the victim’s system. Notably, it utilizes a tool called Process Hacker to disable security, email server, backup, and database software, hindering defenses and preventing access during encryption. To further intensify their extortion scheme, the hackers behind DoppelPaymer launched a data leak site in February 2020, threatening victims with the public release of stolen files.
Since its emergence in 2019, DoppelPaymer has targeted critical industries, with attacks persisting throughout 2020. However, on March 6, 2023, Europol announced that the German and Ukrainian Police had dismantled a ransomware group using DoppelPaymer, although it is uncertain whether the apprehended individuals were the group's founders.
4. Hive
First appearing in June 2021, Hive is an affiliate-based Ransomware-as-a-Service platform. In April 2022, they successfully attacked Microsoft Exchange Servers, exploiting a vulnerability called ProxyShell. They planted a backdoor web script and used a pass-the-hash technique to gain control of the servers and deploy ransomware, causing massive damage.
To further intimidate victims, Hive presented a plain-text ransom note, threatening to expose the victim’s data on a TOR website named ‘HiveLeaks’ unless they met the attacker’s demands. On January 26, 2023, the United States Department of Justice shut down Hive’s operations and seized the group’s back-end servers.
5. Petya
Petya is a ransomware strain that emerged in early 2016 and quickly gained notoriety. Unlike traditional ransomware, which focuses on encrypting individual files, Petya targets the Master Boot Record (MBR) or the hard drive’s partition table, rendering the entire system inoperable.
In its early iterations, Petya disguised its payload as a PDF file, propagating through email attachments using various infection vectors like spear phishing emails and compromised websites.
In April 2016, an anonymous programmer published a free decryptor on the code-sharing platform GitHub, ending Petya’s reign of terror. Amusingly, he claimed to have made the tool to assist his father-in-law in decrypting his Petya-locked computer.
6. NotPetya
NotPetya, also known as Petya 2.0, ExPetr, or Nyetya, was a highly destructive ransomware attack that first emerged in June 2017 and caused over $10 billion of damage. While it initially seemed like a variant of Petya, it was more sophisticated malware that exploited the EternalBlue vulnerability.
NotPetya employed multiple propagation techniques, including stolen credentials and the Windows Management Instrumentation Command-line (WMIC). Unlike traditional ransomware, the primary goal of NotPetya was not financial gain but rather the destruction of data and infrastructure. Upon infection, it encrypted the master boot record (MBR) and the file tables, making the system completely unusable. It then presented victims with a ransom note demanding payment in Bitcoin. But even if victims paid the ransom, decryption and data recovery were impossible.
Cybersecurity experts believe that NotPetya was a state-sponsored attack aimed at destabilizing Ukraine, as most of the initial infections occurred in that region.
7. REvil
REvil, also known as Sodinokibi, is a Ransomware-as-a-Service operation originating in Russia. First appearing in 2019, REvil has been uniquely professional and organized in its approach, utilizing various methods and vulnerabilities to attack its victims.
The ransomware code employed by REvil shares striking resemblances with the code used by DarkSide, hinting at a potential association between these hacking groups. Additionally, both groups employ ransom notes with a similar structure and utilize identical codes to verify the geographical location of their victims to avoid targeting countries within the former Soviet Union.
In one of the most high-profile ransomware incidents to date, REvil targeted Quanta, a supplier of Apple, and successfully obtained confidential schematics of their products. REvil demanded a ransom of $50 million, which they later doubled to $100 million. As a part of their strategy, REvil leaked several schematics and diagrams of MacBook components on their dark web leak site. However, none of the leaked documents pertained to new or unreleased Apple products.
In January 2022, the Russian Federal Security Service announced the dismantling of the REvil operation after receiving key information from the United States. They arrested fourteen of its members and seized twenty luxury cars, computer equipment, 426 million rubles, $600,000, and 500,000 euros. However, the group reappeared three months after the arrests and is, by all accounts, still active.
8. DarkSide
DarkSide is a Ransomware-as-a-Service group that emerged in July 2020, most likely in Russia. They gained notoriety for their alleged involvement in the Colonial Pipeline cyberattack. However, unlike other hacking groups responsible for prominent cyberattacks, DarkSide probably isn’t state-sponsored. Instead, the state merely tolerates them if they target foreign entities. Subsequently, DarkSide ransomware checks system language settings to avoid targets in former Soviet republics and Syria.
Interestingly, DarkSide presents itself as apolitical and avoids targeting certain sectors like hospitals, schools, non-profits, and governments, instead focusing on large corporations capable of paying hefty ransoms. They receive around 25% of the bounty, while the rest goes to the affiliate orchestrating the attack.
To combat this hacker group, the U.S. Department of State has offered a reward of up to $10 million for leads on the name or location of key leaders. Following the gas pipeline attack, President Joe Biden indicated that the U.S. would intensify efforts to disrupt DarkSide’s operations.
On May 14, 2021, DarkSide announced the shutdown of its operations and the closure of its affiliate program, claiming pressure from the U.S. Cybersecurity experts caution that this might be a ploy to deflect scrutiny and resume activities under a different name, as it is common for cybercriminal networks to shut down, revive, and rebrand.
Learn about different methods of ransomware delivery.
9. SimpleLocker
With basic design and functionalities, Simple Locker, which appeared in 2015, marked the beginning of Android-based ransomware.
It used a Trojan downloader to infect and encrypt files stored on a mobile device’s SD card or internal storage, infecting an estimated 150,000 devices as of late 2016. Once infected, Simple Locker displayed a ransom message on the device’s screen, demanding payment in exchange for the decryption key.
The spread of Simple Locker occurred through malicious websites and third-party app stores, emphasizing the importance of downloading apps exclusively from the official Google Play store.
10. TeslaCrypt
TeslaCrypt was a prominent ransomware family that first emerged in early 2015. Their campaign ended unexpectedly in May 2016 when its creators abruptly decided to shut down operations and release the master decryption key, providing victims with the means to recover their encrypted files.
What made TeslaCrypt notable was its focus on saved files from games like World of Warcraft, Minecraft, Call of Duty, and World of Tanks. This approach appealed to gamers’ emotional attachment to their progress, increasing the likelihood of them complying with the ransom demands.
11. Cryptolocker
Cryptolocker is a strain that gained infamy in 2013, successfully extracting around $3 million from its victims. It utilized a trojan that specifically targeted computers running Microsoft Windows and spread through the Gameover ZeuS botnet. Once activated, Cryptolocker employed RSA public-key cryptography to encrypt certain file types stored on local and network drives, with the decryption key stored exclusively on the malware’s control servers. Although removing CryptoLocker itself was straightforward, the encrypted files remained inaccessible because researchers deemed breaking the encryption impossible.
In late May 2014, an international law enforcement collaboration successfully dismantled the Gameover ZeuS botnet responsible for distributing Cryptolocker. As part of the operation, a security firm involved in the process obtained the database of private keys used by CryptoLocker. These keys were subsequently used to develop an online tool that allowed affected individuals to recover their files without paying the ransom.
12. Dharma
Dharma is most likely an evolution of the Crysis ransomware family and is closely related to Phobos, with which it shares most of its code. This similarity makes it difficult for anti-malware systems to differentiate between them, particularly given the numerous variants.
Introduced in December 2018, Dharma serves as a Ransomware-as-a-Service platform, catering to individuals or groups who lack advanced programming skills.
Targeting Windows-operated computers, Dharma primarily exploits the Remote Desktop Protocol (RDP) as its primary method of attack. The attackers search the Internet for computers utilizing RDP, commonly on TCP port 3389, and subsequently launch password brute-force attempts to gain unauthorized access to the targeted systems.
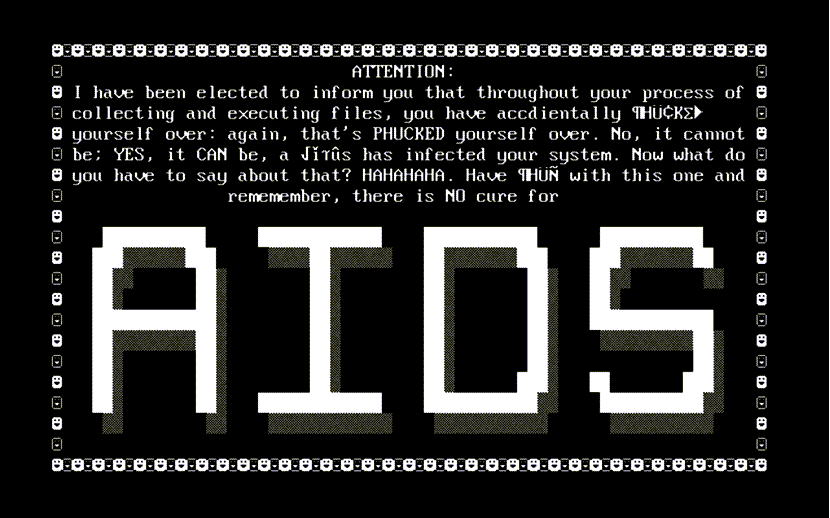
13. AIDS Trojan
In 1989, the AIDS Trojan, also known as the PC Cyborg virus, became the first documented ransomware. It was distributed via infected floppy disks during the World Health Organization’s AIDS conference, catching many unawares.
The mastermind behind the AIDS Trojan was biologist Joseph Popp, who handed out approximately 20,000 infected disks labeled “AIDS Information - Introductory Diskettes” to conference attendees. Upon reaching ninety computer boot-ups, the virus would activate, hiding directories and encrypting or locking file names on the C drive.
To regain access, victims were instructed to send $189 to PC Cyborg Corporation at a Panama-based PO box. Despite its initial impact, the AIDS Trojan’s encryption was relatively simple to overcome as decryption tools quickly became available.
14. GandCrab
GandCrab, first appearing in January 2018, was a widespread and sophisticated Ransomware-as-a-Service operation. GandCrab’s rapid evolution and ability to bypass security made it particularly dangerous.
Its creators regularly released new versions with improved encryption techniques and anti-detection capabilities, making it challenging for security researchers to keep up. The GandCrab ransomware campaign ended in June 2019, when the operators announced the end of their activities and released decryption keys for many of the affected victims.
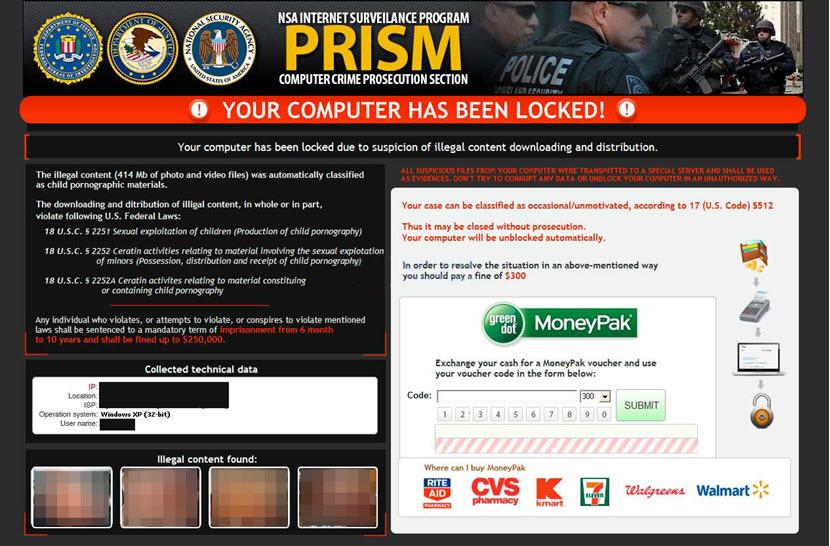
15. Reveton
The Reveton strain emerged in 2012 and gained significant attention for its aggressive and intimidating tactics. Namely, Reveton locks the victim’s screen and displays a fake message from law enforcement agencies claiming they have evidence of illegal activities.
Often known as a “Police Trojan,” the deceptive message accuses the victim of various crimes, such as distributing copyrighted material or engaging in child pornography, and demands the payment of a fine to unlock the computer. The ransom note also included official logos and used language that created a sense of urgency and fear, coercing the victim into paying the ransom.
Reveton is a prime example of hackers using social engineering to establish credibility. The ransomware also presented the user with their computer’s IP address and webcam imagery, creating the false impression that their activities were being monitored and recorded.
16. Maze
Maze emerged in 2019 and gained significant attention due to its technique of double extortion. The criminals not only encrypted the files but also exfiltrated sensitive data, threatening to release it if the victims did not pay.
The ransomware stealthily exfiltrated sensitive data from the target’s network, including personal information, financial records, and intellectual property. This information enabled Maze operators to contact the victims more effectively, usually through a ransom note or email, demanding a significant ransom in exchange for the decryption key and a promise not to disclose the stolen data.
17. MedusaLocker
Named after the mythical creature with snakes for hair, MedusaLocker originated in 2019 and mostly relied on vulnerabilities in the Remote Desktop Protocol to access victims’ networks. In January 2020, a variant called Ako emerged, featuring enhancements such as integrating a Tor hidden service.
This update also enabled them to adopt a Ransomware-as-a-Service model, streamlining their malicious activities. Recent observations suggest that MedusaLocker consistently divides the ransom payments between the affiliate, who receives 55 to 60 percent of the ransom, and the developer, who claims the remaining portion.
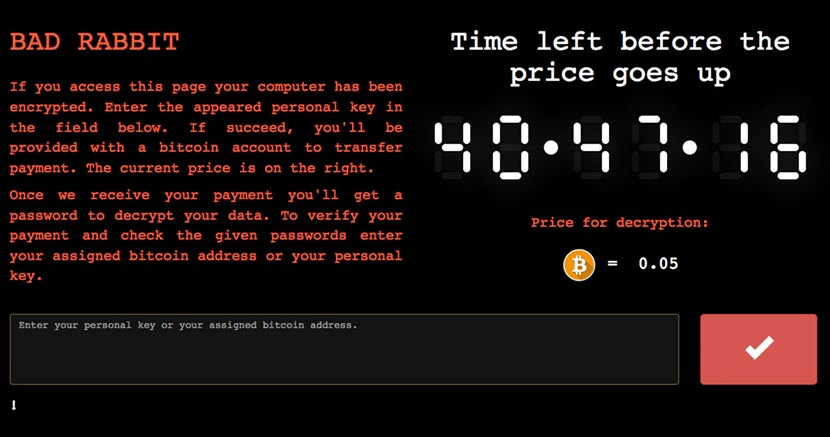
18. Bad Rabbit
Bad Rabbit was a ransomware strain that surfaced in October 2017 and targeted various organizations, primarily in Russia and Ukraine. A notable aspect of Bad Rabbit was its resemblance to the earlier Petya and NotPetya strains, both in terms of code similarities and lateral movement techniques. This connection led to speculation that Bad Rabbit may have been a variant or inspired by the same threat actors.
Unlike traditional ransomware that spreads through phishing emails, Bad Rabbit disguises itself as an Adobe Flash installer and incorporates ransomware into websites by embedding JavaScript within the HTML code. This method allows the ransomware to activate when users visit compromised websites. The owners of the compromised websites hosting the Bad Rabbit ransomware are, in most cases, unaware of its presence on their service.
Bad Rabbit gained notoriety for significantly disrupting critical networks in Bulgaria, Japan, Russia, Turkey, and Ukraine. Their attacks affected various systems, including the payment network of the Kyiv metro system and flight schedules at Odesa’s airport. In October 2018, the United Kingdom claimed the incidents were Russian military cyberattacks.
19. NetWalker
NetWalker is a highly sophisticated variant that gained prominence in 2019 and continues to pose a significant threat worldwide. What sets it apart is its double-extortion tactic, also used by the infamous Maze gang. NetWalker published a sample of the compromised files on the dark web as proof of the breach. They then give the victims an ultimatum – pay the ransom or suffer a more extensive data breach.
In March 2020, NetWalker underwent a significant transformation, adopting a Ransomware-as-a-Service model that facilitated rapid expansion. The criminal affiliates involved in the operation receive a substantial percentage of each ransom payment, providing them with a strong incentive to quickly propagate the ransomware far and wide, leading to its proliferation.
A leaked recruitment post has revealed that NetWalker is expanding its focus beyond the ubiquitous spear phishing attack vector. The ransomware strain will target internet-exposed Remote Desktop Protocols (RDPs), broadening its scope and potentially increasing its reach.
Learn the difference between attack vector and attack surface.
20. Troldesh
Troldesh, also known as Shade or Encoder.858, is a ransomware strain created in Russia in 2014. It is an encryptor that utilizes the “.xtbl” extension to encrypt a victim’s files. The initial spread of Troldesh occurs through email spam.
What sets Troldesh apart is its direct communication approach with the victims. Unlike many ransomware attackers who prefer to remain anonymous, Troldesh’s creators provide an email address to establish direct contact with their targets. Through this email correspondence, the attackers demand a ransom and specify their expected payment method.
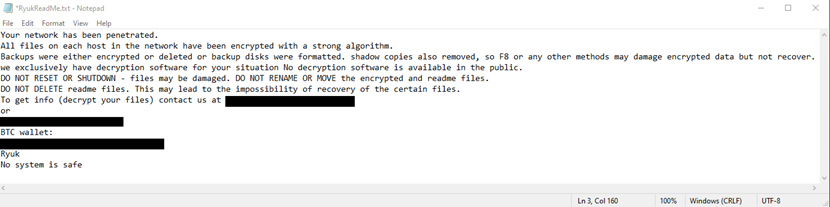
21. Ryuk
Ryuk (pronounced ree-yook) is a ransomware family that first appeared in mid- to late-2018, most likely as a variant of the older Hermes ransomware. Although initially suspected to be of North Korean origin, experts now believe a Russian cybercriminal group known as Wizard Spider operates Ryuk.
With a focus on large organizations capable of paying substantial sums, Ryuk targets those with valuable data. The U.S. Department of Health and Human Services reports that Ryuk's attacks resulted in over $61 million in ransom payments during 2018-2019, making it one of the most dangerous and successful strains in history.
Early in 2021, a newly identified variant of Ryuk emerged, exhibiting worm-like characteristics that enable it to self-propagate and infect other devices within the local network it infiltrates.
22. SamSam
Also known as Samas or SamsamCrypt, the first known version of this strain appeared in late 2015 or early 2016. SamSam derived its name from the file extension it adds to the encrypted files (.sam). Reports from victims revealed that it utilized the JexBoss Exploit Kit to exploit vulnerable JBoss applications.
A unique aspect of SamSam is that it remains covert and undetected for extended periods following the initial infection, acting as a spy within the compromised system. Attackers use Remote Desktop Protocol (RDP) to maintain persistent access to victims’ networks and employ brute force attacks or stolen login credentials. Detecting RDP intrusions is challenging because the malware typically enters through an authorized access point.
Despite the arrest of two Iranian hackers linked to the operation of SamSam and the last reported attack being in 2018, we should not consider it inactive. Firstly, there is still no publicly available decryption tool and no definitive evidence of SamSam’s complete termination. As such, it is prudent to regard this strain as still active.
23. Locky
Appearing in early 2016, Locky is one of the most prolific and successful ransomware families to date. It proliferated primarily through email phishing campaigns, tricking unsuspecting users into opening malicious attachments, typically Microsoft Office documents. Once opened, these attachments deployed macros and scripts that downloaded and executed the payload on the victim’s computer.
The way Locky tricked people into opening the spam email attachments was very cunning. To entice users to enable macros, the emails often included misleading instructions, such as claiming that the document contains valuable information that requires macros to be enabled for proper display. Locky exploited users' trust and familiarity with Microsoft Office documents and relied on them unknowingly executing the malicious code by enabling macros, ultimately leading to the infection and encryption of their files.
Locky ransomware remains a threat, although its impact has decreased since its peak in 2016 and 2017. Over time, cybersecurity researchers and law enforcement agencies have also disrupted Locky’s operations and associated infrastructure, leading to a decline in distribution.

Following email security best practices, such as strong spam filters and disabling macros in attachments, can minimize the risk of falling victim to Locky ransomware.
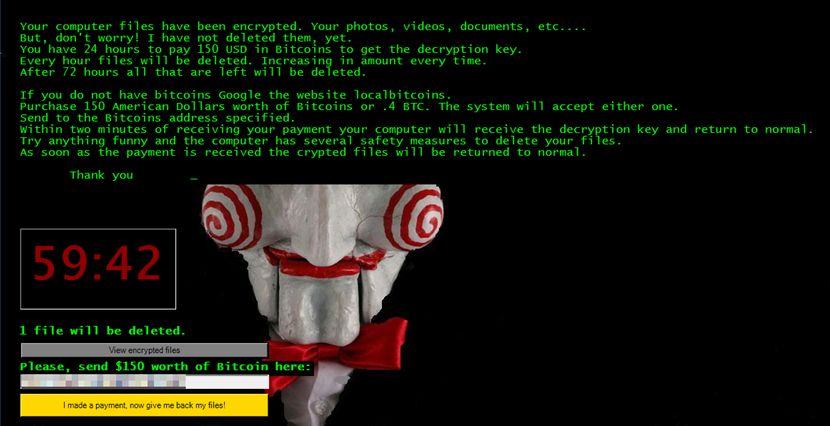
24. Jigsaw
Named after the character from the “Saw” horror movie, the Jigsaw variant emerged in 2016 and gained attention for its unique behavior. Namely, it deletes a few files every hour until the victim pays the ransom, creating psychological pressure to comply. Moreover, if the target attempts to terminate the ransomware or remove it from the system, Jigsaw threatens to delete a large number of files as punishment.
Jigsaw also displays a menacing interface on the victim’s screen, featuring pictures and audio clips from the “Saw” movie and a countdown timer. The ransom note informs the victim about the encryption and demands a ransom in Bitcoin within a specific time limit. Failure to meet the deadline permanently deletes an increasing number of files.
Although it struck fear into people worldwide, it turned out that Jigsaw, written in .NET, had a fatal weakness. Experts were able to analyze its code and quickly devise decryption methods, rendering the need to pay the ransom unnecessary. While Jigsaw is not actively spreading, it has a history of resurfacing, potentially causing anguish to network managers.
25. ZCryptor
Emerging in 2016, ZCryptor became known for its ability to self-propagate rapidly across networks, demonstrating worm-like behavior. This capability posed a significant threat and was a relatively unique feature.
ZCryptor employs a clever technique to infect computers by dropping an autorun.inf file on removable drives. When users plug these drives into other computers, the autorun.inf file triggers the execution of the malware, facilitating its spread. In addition to leveraging removable drives, ZCryptor takes advantage of network drives to further propagate its malicious payload.
Like many other older ransomware strains, ZCryptor is not the threat it used to be. It does not restrict .exe files, allowing modern malware removal tools to eliminate it efficiently – a faster solution than manual removal.
Discover effective strategies and practical tips to safeguard your digital assets in our comprehensive article on how to prevent ransomware.
How phoenixNAP Can Help You Against Ransomware
We can equip you with the tools and expertise to mitigate ransomware risks and ensure the continuity and security of your valuable data.
Here is a range of comprehensive solutions to bolster your defense against ransomware:
Veeam Backups
Our Veeam Backups add an extra layer of protection against ransomware, guaranteeing the integrity of your data and eliminating the need for ransom payments. This secure platform enables quick restoration and seamless operations in the face of data loss or system failure and minimizes downtime in your IT environment.
Disaster Recovery
We offer reliable and affordable disaster recovery solutions to swiftly restore your IT environment in the face of unexpected events. Our servers are strategically located across the globe, and you can count on our expert team to guide you in choosing and implementing the right disaster recovery and business continuity plans.
Data Security Cloud
Protect your data with the Data Security Cloud, a highly stable cloud infrastructure platform we designed from the ground up with malware protection in mind. Developed in partnership with Intel and VMware, this robust solution implements multiple layers of security, making it ideal for healthcare providers seeking HIPAA-compliant servers.
Discover the latest ransomware statistics in our comprehensive article that sheds light on the impact these growing threats have on individuals and organizations worldwide.
Conclusion
The fight against ransomware is ongoing as cybercriminals continue to evolve their tactics and exploit new vulnerabilities. Staying ahead requires constant vigilance, innovative technologies like AI and behavioral analytics, and effective ransomware solutions that strengthen detection and prevention. Alongside these tools, cybersecurity training and awareness remain vital to help individuals recognize and respond to threats, ensuring a more resilient and secure digital future for all.



