Ransomware is malicious software created to take control of your IT system, demanding payment in exchange for regaining access. However, not all ransomware behaves the same. Some strains encrypt files, others block access to systems, and some threaten to release or sell the data as a form of blackmail.
By understanding the different ransomware variants and their standard features, you can develop a more holistic approach to defending yourself and your organization.
This article explains the types of ransomware and how to identify them.

5 Different Types of Ransomware
All ransomware aims to extort payment from the victim, often in cryptocurrency, in exchange for restoring access or preventing further damage. However, paying the ransom doesn't guarantee data recovery. Additionally, it encourages cybercrime as perpetrators get motivated by financial gain.
Let's explore each attack method and analyze the potential dangers.
1. Crypto Ransomware
The most common strain of ransomware is known as crypto ransomware. The variant encrypts files within a system, rendering them inaccessible without a decryption key.
Also referred to as data kidnapping, crypto ransomware targets essential data without interfering with the operating system. The encrypted files are visible but inaccessible, a tactic employed to cause panic.
Cybercriminals often include a countdown clock alongside the ransom demand to create a sense of urgency. They threaten to delete the encrypted files unless the victim pays within the deadline.
2. Locker Ransomware
Locker ransomware completely locks victims out of their computer systems. This software partially disables the mouse and keyboard and renders the operating system unusable. The ransomware then employs a pop-up lock screen to display the ransom demand.
Screen lockers generally do not encrypt data, which makes recovery easier and destruction unlikely. For instance, removing the malware can be as simple as rebooting the machine in safe mode and running antivirus software.
The ransom demand lock screen may also falsely accuse the victim of downloading illegal content or warn about a virus infection.
3. Scareware
Scareware relies on social engineering to trick users into believing their computers are infected or facing urgent issues. The software shows deceptive pop-up alerts, often with logos of legitimate security software or law enforcement agencies, and instructs victims to address the fabricated problem by paying a ransom.
The characteristics of this type of ransomware vary. Some scareware strains lock the computer and encrypt files, while others flood the screen with pop-up alerts without causing damage.
The defining feature of scareware is that it tries to instill fear in its victims, manipulating them into paying a fee or purchasing software to fix a non-existent issue. While paying the ransom may work, there is a risk that the fix itself deploys additional ransomware.
4. Extortionware (Leakware)
Extortionware, also known as leakware, doxware, and exfiltrationware, involves hackers stealing data and threatening to publish it. Victims pay the ransom to prevent their data from entering the public domain or being sold on the dark web.
Extortionware is generally more damaging to companies than to individuals. A publicized data breach will likely damage a company's reputation and potentially lead to fines for violating data protection laws like HIPAA, PCI, and GDPR.
Hackers often combine data theft with encryption to amplify the pressure on their victims. This practice is called double extortion. In triple extortion, an additional layer is added to the attack. For instance, the criminals not only threaten the victim's data but also demand ransom by targeting the sensitive information of the victim's clients.
5. DDoS Ransomware
Distributed denial-of-service (DDoS) ransomware is a combination of DDoS attacks and traditional ransomware. Instead of directly encrypting or stealing information, DDoS ransomware attacks disrupt an organization's core services and request a ransom to stop the attack.
This disruption occurs through a barrage of illegitimate connection requests directed at the organization's web servers or services, overwhelming their capacity and effectively shutting them down. An accompanying ransom note promises to cease the attack upon receiving the ransom payment.
Unlike traditional ransomware, DDoS attacks require significant resources to maintain, potentially limiting their duration. Additionally, they pose no immediate threat to the integrity of stored data. However, extended network downtime considerably disrupts business continuity and damages a company’s reputation.
Looking for specific examples of ransomware incidents?
Our article on ransomware examples highlights the 25 most famous and devastating ransomware attacks.
Ransomware Delivery Methods
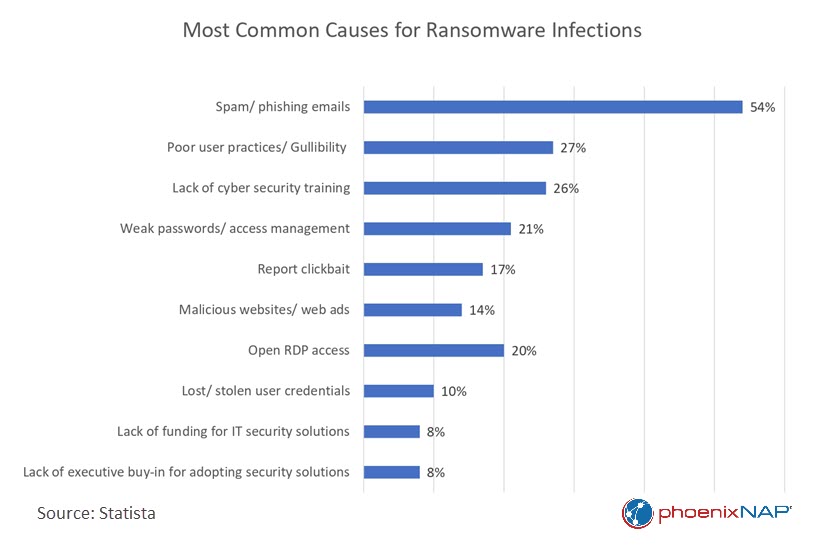
Hackers exploit vulnerabilities to infiltrate systems and deliver ransomware. They might leverage the human element or exploit software flaws and network weaknesses.
Here are the methods hackers use to deploy ransomware:
- Phishing. In this tactic, cyber criminals use emails, texts, and calls to impersonate legitimate entities and trick victims into clicking infected links or downloading malware-laced attachments.
- Drive-by downloads. A user can become a victim without realizing it, as they may automatically download ransomware when visiting compromised websites.
- Vulnerabilities. Software vulnerabilities are flaws in computer programs, applications, or operating systems that attackers exploit to gain unauthorized access or manipulate data.
- Remote desktop protocol (RDP) exploits. Hackers can use poorly secured RDP connections to access computer networks and deploy ransomware.
- Insider threats. An organization insider may, willingly or unknowingly, help external threat actors to facilitate a ransomware attack.
Ransomware-as-a-Service (RaaS) is a business model where cyber criminals lease access to pre-developed ransomware tools. Once their affiliates successfully deploy the ransomware and collect payments, a percentage of the profits is shared with the RaaS creator.
The RaaS model significantly lowers the barrier to entry for cyber crime and enables less skilled individuals to launch sophisticated attacks.
How to Prevent Ransomware Attacks?
Many ransomware variants can spread beyond the initial entry point after infiltrating a system. Sometimes, the malware stays hidden for months, installs backdoors, and gathers data, even if you quarantine the initial intrusion. The possibility of lateral movement makes ransomware prevention better than mitigation.
Here are some tips for successfully preventing a ransomware attack:
- Patch software vulnerabilities. Patching known vulnerabilities reduces the attack surface by closing potential entry points for attackers.
- Improve your email security. Mandating email security best practices reduces the likelihood of successful phishing attacks, the most common method for ransomware infiltration.
- Set up a firewall. A firewall controls incoming and outgoing network traffic to block unauthorized access.
- Build staff awareness. Security awareness training empowers employees to recognize and avoid potential ransomware threats.
- Improve endpoint protection. Robust endpoint security reduces the risk of ransomware infecting vulnerable entry points within the network.
- Enforce strong password policy. Strong passwords prevent unauthorized access through compromised credentials.
Read our guide on how to prevent ransomware for a detailed breakdown of the most effective methods of protecting your organization.

Hope for the Best, but Prepare for the Worst
A backup strategy is the last line of defense against ransomware, as it offers a way to restore data after a successful attack. However, according to the Veeam 2023 Ransomware Trends report, 93% of ransomware attacks target backup systems.
That's where a disaster recovery plan comes in. It is a proactive framework that anticipates potential threats and outlines specific actions to counter them. With a well-defined disaster recovery plan, you can isolate infected systems and activate secondary systems stored in secure, offsite locations, minimizing downtime and data loss.