In traditional computer systems, users prove their identities by typing in passwords. While easy to set up, this authentication method has a severe flaw. If hackers steal or crack the password, they can easily assume the user’s identity. Intruders log in as the real user, and the system is wide open to an attack.
Kerberos authentication protects user credentials from hackers. This protocol keeps passwords away from unsecured networks at all times, even during user verification.
Read on to learn what Kerberos authentication is and how it protects both end-users and systems.
What Is Kerberos?
Kerberos is an authentication protocol for client/server applications. This protocol relies on a combination of private key encryption and access tickets to safely verify user identities.
The main reasons for adopting Kerberos are:
- Plaintext passwords are never sent across an insecure network.
- Every login has three stages of authentication.
- Encryption protects all access keys and tickets.
- Authentication is mutual, so both users and providers are safe from scams.
MIT developed the first instances of Kerberos in the late ’80s. The protocol was named after Cerberus, a creature from Greek mythology. Cerberus was a ferocious three-headed dog who guarded Hades.
A refined version of Kerberos was introduced by Microsoft as part of Windows 2000. Since then, Kerberos became Windows’ default authorization protocol. Implementations of Kerberos also exist for Apple OS, FreeBSD, UNIX, and Linux. The Kerberos Consortium treats the protocol as an open-source project.
Three Main Components of Kerberos
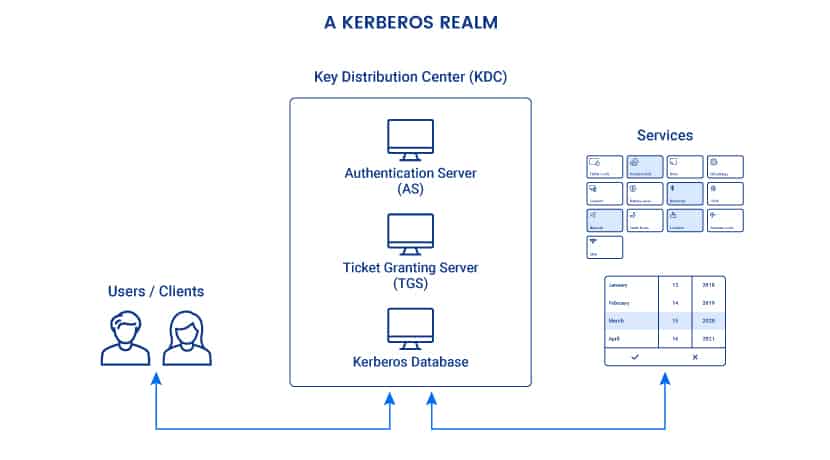
Every Kerberos verification involves a Key Distribution Center (KDC). The KDC acts as a trusted third-party authentication service, and it operates from the Kerberos server. KDC consists of three main components:
- An authentication server (AS): The AS performs initial authentication when a user wants to access a service.
- A ticket-granting server (TGS): This server connects a user with the service server (SS).
- A Kerberos database: This database stores IDs and passwords of verified users.
All Kerberos authentications take place in Kerberos realms. A realm is a group of systems over which a KDC has the authority to verify users and services.
How Kerberos Authentication Works
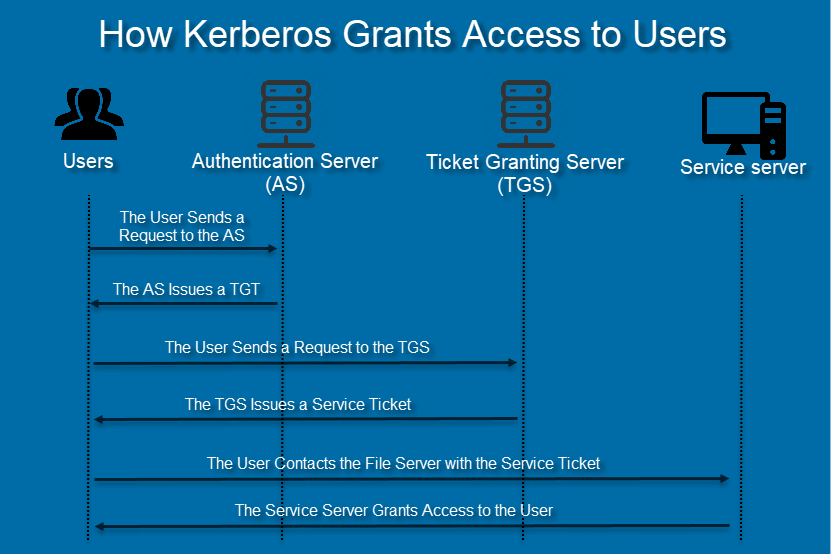
With Kerberos, users never authenticate themselves to the service directly. Instead, they go through a series of steps performed by different parts of the Key Distribution Center.
The AS Verifies Users with Decryption
The Kerberos protocol starts with the user requesting access to a service through the Authentication Server. This request is partially encrypted with a secret key, the user’s password. The password is a shared secret between the user and the AS.
The AS can only decrypt the request if the user encrypted the message with the correct password. If the password is wrong, the AS cannot interpret the request. In that case, AS does not verify the user, and the authentication process fails.
Once it decrypts the request, the AS creates a ticket-granting ticket (TGT) and encrypts it with the TGS’s secret key. This key is a shared secret between the AS and the Ticket Granting Server.
A TGT contains a client/TGS session key, an expiration date, and the client’s IP address. The IP address protects from man-in-the-middle attacks. Once it issues a TGT, the AS sends it to the user.
The TGS Connects Users to Service Servers
The user sends the TGT to the TGS. If the ticket is valid and the user has permission to access the service, the TGS issues a service ticket.
A service ticket contains the client ID, client network address, validity period, and client/server session key. The service ticket is encrypted with a secret key shared with the service server.
The user then sends the ticket to the service server along with the service request. The SS decrypts the key and grants access to the requested resources.
Verification Without Plain Text Passwords
During the entire verification process, a plain-text password never reaches the KDC or the service server. Encryption protects all three sets of temporary private keys.
Kerberos works both with symmetric and asymmetric (public-key) cryptography. The protocol can also handle multi-factor authentication (MFA).
Remote work may expose vulnerabilities to potential attacks. Learn how to secure remote access to computer systems.
Kerberos Authentication Steps
Kerberos Authentication is a multi-step process. Suppose a user wants to access a network file server to read a document. Below are the steps required to authenticate through Kerberos:
- The user sends a request to the AS. The user issues an encrypted request to the Authentication Server. When the AS gets the request, it searches for the password in the Kerberos database based on the user ID. If the user typed in the correct password, the AS decrypts the request.
- The AS issues a TGT. After verifying the user, the AS sends back a Ticket Granting Ticket.
- The user sends a request to the TGS. The user sends the TGT to the Ticket Granting Server. Along with the TGT, the user also explains the reason for accessing the file server. The TGS decrypts the ticket with the secret key shared with the AS.
- TGS issues a service ticket. If the TGT is valid, the TGS issues a service ticket to the user.
- The user contacts the file server with the service ticket. The client sends the service ticket to the file server. The file server decrypts the ticket with the secret key shared with TGS.
- The user opens the document. If the secret keys match, the file server allows the user to open the document. The service ticket determines how long the user has access to the record.
Once access expires, the user must repeat the entire Kerberos authentication protocol.
Benefits of Kerberos Authentication
These are the main benefits of adopting Kerberos:
- Improved security. Cryptography, multiple secret keys, and third-party authorization make Kerberos one of the industry’s most secure verification protocols. User passwords are never sent across the network. Secret keys pass through the system in encrypted form. If someone is logging conversations, it becomes difficult to collect sufficient data to impersonate a user or the service.
- Access control. Kerberos is a crucial component of today’s enterprises. The protocol allows excellent access control. With Kerberos, the company has a single point for enforcing security policies and tracking logins.
- Transparency and auditability. Kerberos makes it easy to see who requested what and at what time. Transparent and precise logs are vital for security audits and investigations.
- Mutual authentication. Kerberos enables users and service systems to authenticate each other. At each step of the authentication process, both the user and the server systems know that they are interacting with authentic counterparts.
- Limited ticket lifetime. All tickets in the Kerberos model have timestamps and lifetime data. Admins control the duration of the users’ authentication. Short ticket lifetimes are great for preventing brute-force and replay attacks.
- Scalability. Several technology giants have adopted Kerberos authentication, like Apple, Microsoft, and Sun. The adoption among enterprises speaks volumes about Kerberos’ ability to keep up with the demands of large companies.
- Reusable authentication. Kerberos authentication is reusable and durable. The user only verifies with the Kerberos system once. For the lifetime of the ticket, the user can authenticate to network services without re-entering personal data. Single sign-on is the most direct end-user benefit of Kerberos.
- Quick fixes and updates. Over the years, top programmers and security experts have tried to break Kerberos. This scrutiny ensures that any new weakness in the protocol is quickly analyzed and corrected.
Can Kerberos Be Hacked?
No security model is completely invulnerable, and Kerberos is no exception. Given Kerberos' widespread use, hackers have had ample opportunities to find ways around it.
The biggest threats to a Kerberos system are forged tickets, repeated attempts to guess a password, and malware that downgrades encryption. A combination of all three tactics is the usual recipe for successful breaches.
The most successful methods of hacking Kerberos include:
- Pass-the-ticket: A cyber attacker forges a session key and presents the fake credentials to reach the resources. Hackers typically use a golden ticket (granting domain admin access) or a silver ticket (granting access to a specific service).
- Credential stuffing and brute-force attacks: Automated, continued attempts to guess a user's password. Most brute-force attacks go after the initial ticketing and the ticket-granting service.
- Skeleton key malware: This malware bypasses Kerberos and downgrades key encryption. The attacker must have admin access to launch the cyberattack.
- DCShadow attack: This hack occurs when attackers gain enough access within the network to set up their own DC for further infiltration.
Despite these dangers, Kerberos remains the best security protocol available today. If users practice good password choice policies, the likelihood of hacks is minimal.
Weaknesses of Kerberos Authentication
While Kerberos effectively deals with security threats, the protocol does pose several challenges:
- The Kerberos server is a single point of failure (SPOF). If the Kerberos server goes down, users cannot log in. Fallback authentication mechanisms and secondary servers are typical solutions to this problem.
- Strict time requirements. Date/time configurations of the involved hosts must always be synchronized within predefined limits. Otherwise, authentications fail because tickets have a limited availability period.
- Every network service needs unique Kerberos key sets. Each network service that requires a different hostname needs its own set of Kerberos keys. Issues with virtual hosting and clusters are not uncommon.
- All nodes must be compatible with third-party authentication. Both user machines and service servers must be designed with Kerberos authentication in mind. Some legacy systems and local packages are not compatible with third-party authentication mechanisms.
An Old, But By No Means an Outdated Protocol
Cybercrime is an unfortunate element of today’s fiber interconnectivity. Experts predict that the average cost of a data breach for large enterprises will be more than $150 million in 2020. Forbes predicts that an increasing number of criminals will soon be using Artificial Intelligence (AI) to scale and better their attacks. The cybercrime problem is unlikely to disappear anytime soon, and Kerberos authentication is an excellent way for a company to protect its assets.