Cryptographic keys play a vital role in protecting sensitive information, preventing data breaches, and complying with regulations. Unfortunately, a lost or stolen key can lead to costly losses of systems and data, which is why every security-aware company should enforce robust key management protocols.
This article is an introduction to encryption key management. Read on to learn about the basic concepts surrounding encryption, the value of proper key management, and how to keep data safe throughout a key’s lifecycle.
What Is Encryption Key Management?
Encryption key management is a set of practices and rules that ensure the safe use of cryptographic keys. Proper management ensures a key stays safe throughout its lifecycle, from generation and use to storing and deletion.
A cryptographic key is a file that contains a string of letters and numbers that can encrypt and decrypt data when processed by a crypto algorithm. The primary objective of key management is to prevent unauthorized access to these files.
Check out our post about 16 encryption key management best practices to properly manage your security.
Losing a key to a malicious party can have grave consequences, so a robust encryption key management strategy must include:
- Instructions on how employees should manage keys at different stages of existence.
- Security measures that prevent unauthorized physical and virtual access to the server storing the keys.
- Policies and systems for key functions.
- Role-based controls that limit access and define who and when can access the keys.
- Instructions on how different departments should interact and coordinate with keys.
A business can approach key management in three different ways:
- Decentralized: End-users or employees are responsible for key management, and the company does not handle governance.
- Distributed: Each team or department has a separate key management protocol, while the business provides basic guidance.
- Centralized: A business-wide policy dictates how all staff members and departments use keys.
The safest approach is to set up a centralized strategy and achieve complete control over how teams store, share, and use private keys.
Consider adopting zero-trust security, a strategy that ensures no user or system has access to private keys by default.
Why Is Key Management Important?
Careful management of keys is vital to the effective use of cryptography in your cybersecurity strategy.
A key is similar to a safe combination: no safe can stop the thief if a perpetrator knows how to unlock the vault. Similarly, poor key management can make even the best encryption algorithm worthless. A compromised key allows an attacker to:
- Convert encrypted data back to its original, plaintext form.
- Create a phishing website that impersonates your official website.
- Take the entire security infrastructure down.
- Act as a privileged user and access different systems and databases.
- Sign apps and documents in your name.
Proper key management guarantees high levels of security around encrypted data and ensures:
- Only authorized users can read or access data.
- Safe transfers of data across the Internet and private networks.
- Different cyberattack types cannot easily spy, infect, or spread through your systems.
The use of encryption also helps comply with some regulations, such as HIPAA or PCI.
Consider setting up our Encryption Management Platform, an all-in-one EMP that allows you to centralize encryption management and control all keys from a single pane of glass.
How Does Key Encryption Work?
Encryption enables us to exchange data securely, keeping its contents unreadable to everyone except the sender and the recipient. Exchanging encrypted data is a two-step process:
- First, algorithms scramble data into a string of seemingly random characters (ciphertext). The sender then forwards the ciphertext to the recipient.
- Once the receiving party gets the ciphertext, a decryption key descrambles the message back to the original plaintext form.
Throughout this process, the information is unreadable to anyone who does not possess the descrambling key. Encryption is fully automatic, and the two parties exchanging data do not have to code and decode messages. Key actors and operations in the encryption process are:
- The data encryption key (DEK): An encryption key that encrypts and decrypts the data.
- The key encryption key (KEK): A key that encrypts and decrypts the DEK.
- Key management system (KMS): A system that stores and runs the key management software.
- Key management API (KM API): An API that retrieves encryption keys from a server to a client.
- A certificate authority (CA): A third-party entity that authenticates users and systems via digital certificates.
- Transport layer security (TLS): A cryptographic protocol that protects data moving over a computer network.
You can use encryption to protect data both at rest and in motion:
- Encryption at rest: This encryption type protects stored data. If hackers break into a database, they cannot decipher information without a key.
- Encryption in transit: This encryption type secures data on the move and prevents interception or tampering. Typical examples are emails, text messages, and web data.
Read about Kerberos authentication, a verification protocol that relies on a mix of encryption and access tickets to validate user identities.
Encryption Key Types
There are two main types of encryption:
- Symmetric: The same key both encrypts and decrypts the message.
- Asymmetric: One key encrypts the content, and a different, paired key decrypts the data.
Symmetrical encryption is easier to use and set up. However, relying on the same key for coding and decoding content makes this strategy less secure than asymmetric encryption.
Symmetric Keys
Symmetric cryptography relies on the same key both for data encryption and decryption. As a single key protects the entire operation, the privacy of the key is paramount. Below is a diagram that shows what a symmetric encryption process looks like:
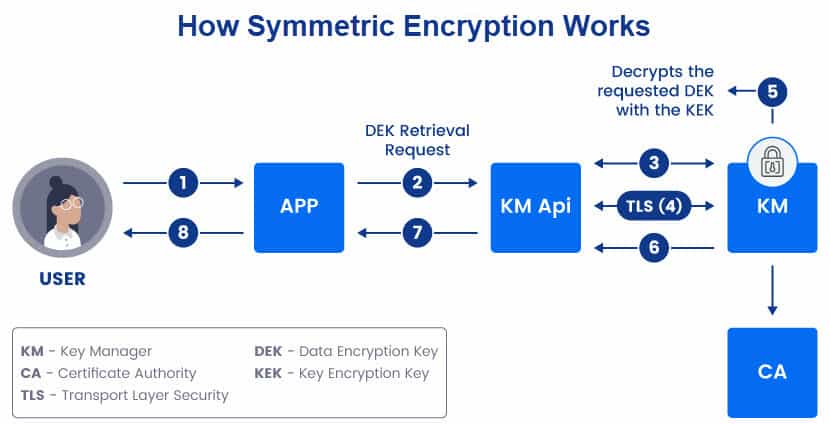
Here is a step-by-step explanation of how the process in the diagram above works:
- A user sends a request to an app and asks to access encrypted data.
- The app sends a DEK retrieval request to the client’s KM API.
- The client (via a KM API) and KM verify each other’s certificates.
- If the credentials are valid, the KM API and the KM form a secure TLS connection.
- The KM decrypts the requested DEK with the KEK.
- The key manager sends the DEK to the KM API.
- The KM API sends the DEK to the app.
- The app sends plaintext data to the user.
Companies typically use symmetric encryption to protect data at rest.
Learn the differences between TLS and SSL (Transport Layer Security and Secure Sockets Layer), two standard protocols for encrypting web data.
Asymmetric Keys
Asymmetric encryption relies on a pair of keys for the encryption and decryption of data:
- The public key encrypts the data and can be available to the public, as it only scrambles content.
- The private key decrypts the data and is a unique counterpart to the public key. Keeping this key safe is vital as there is no way to decode the data without it.
Both keys are unique, exclusive to each other, and created at the same time. The primary use of asymmetric keys is to protect data while it moves across a network connection, whether public or private.
Here is a diagram that shows how asymmetric encryption allows two parties to exchange files safely:
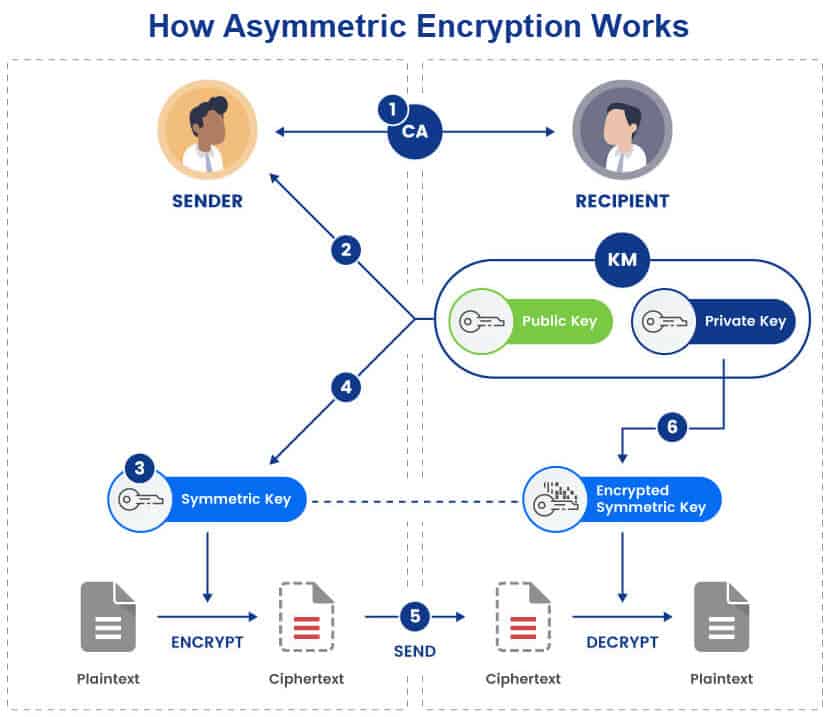
Below is a step-by-step explanation of how the process in the diagram above works:
- The two parties verify each other’s certificates. Similar to symmetric encryption, the recipient performs authentication first, using a CA.
- Once the two parties have mutual acceptance, the sender requests the recipient’s public key.
- The sender creates a temporary symmetric key (a key valid only for a single session) and encrypts the requested file.
- The sender encrypts the symmetric key with the recipient’s public key and sends it alongside the requested file.
- The recipient receives the package.
- The user decrypts the symmetric key with the private key from its KM and then descrambles the data with the symmetric key. Decryption returns the data to its plaintext state.
Learn about ransomware, a dangerous cyberattack that uses asymmetric keys to encrypt and steal valuable business data.
How to Manage Encryption Keys?
Sound encryption key management requires you to organize the entire lifecycle of each key, roughly divided into the following stages:
- Key creation.
- Use and rollover.
- Revocation.
- Backup.
- Destruction.
Ensuring the safe use of encryption keys without accounting for each stage of the lifecycle is a mistake. Other common errors companies make are:
- Relying on weak, overly short keys.
- Using the same key for different purposes and tasks.
- Reusing old key versions.
- Storing private keys on the same server or database as the encrypted data.
- Keeping keys in an unencrypted form.
- Moving keys between systems and users without proper protection.
Below is a closer look at each stage of a key’s lifecycle and what your team should look out for to ensure the safe use of encryption keys.
Key Generation
Companies create and store encryption keys on a key management server. Ensure the generator only creates long and complex keys to prevent attackers from using simple techniques to crack the code.
The server typically uses a secure random bit generator and stores the key, along with all its attributes, in a storage database. The essential info is:
- The key’s name.
- Activation date.
- Size.
- Instance (or version).
- Rollover.
- Mirroring.
- Access rights.
A key manager should allow admins to edit the key’s characteristics at any time. Key activation happens either upon creation or at a later date (either automatically or manually).
You also need to define a crypto period for each key. This period is the time during which a key is functional. Two factors impact the duration of a crypto period:
- The originator usage period (OUP).
- The recipient usage period (RUP).
For example, you encrypt a database and plan to add items to it for the next six months. In that case, the OUP sits at six months. If you plan to allow users to access and use the database for two years, that period is the RUP. As the OUP and RUP overlap, the crypto period is two years.
Once you generate a key, ensure the server stores it in an encrypted state. Keys should be available in unencrypted form only within a secure, tamper-protected environment. Also, never store the key in the same database as the encrypted data it protects.
Key Use and Rollover
The key manager allows authorized systems and users to retrieve keys for encryption or decryption processes. The manager should also oversee the management of all current and past instances of encryption keys.
For example, if the software generates a new key and deactivates (or rolls) the old one every year, the manager should retain previous versions of the key but dispense only the current instance.
Many companies choose to turn key rotations into an automatic process. This approach limits the room for human error and frees up the team to focus on more impactful tasks. For additional security, consider also logging key usage and providing audit trails.
Ensure the team does not use the same key for different purposes. Each task should rely on a unique key to prevent potential lateral movement between systems in the event of a key compromise.
Key Revocation
An admin must be able to use the key manager to revoke a key and prevent its use. This ability is crucial when:
- Individuals leave the company.
- You archive certain processes.
- Monitoring tools detect malicious behavior.
- The security team identifies an insider threat.
If necessary, reactivating a revoked key can help admins decrypt data previously encrypted with it, like old backups.
Backup (or Escrow)
All keys require a backup before deactivation, so the manager should keep a mirror archive of all deactivated keys. Recoveries after the crypto period enable admins to reconstruct keys if reactivation is needed.
The inability to recover a key means any data that remains decrypted with the key in question is effectively lost.
Key Deletion
An admin should be able to delete the key from the storage database. The deletion option is vital if:
- The key is no longer in use.
- Someone compromises the key.
Removing a key can either delete all or some of its instances. Admins typically ensure the recovery of the key is impossible without a backup image.
If someone compromises encrypted data, the ability to delete the key quickly can keep data safe and unrecoverable. When the security team eliminates the threat, an admin can use the image to recreate the key and descramble data.
Read about the cybersecurity best practices that can add additional layers of safety to your systems and encrypted data.
There Is No Safe Cryptography Without Robust Key Management
Effective key management is a crucial part of your data protection strategy. Set up a system that keeps keys safe at all stages of the lifecycle and ensures the protocols offer the flexibility necessary for your teams’ dynamic work environments.



