Traditional security models, which rely on the concept of a trusted internal network protected by robust perimeter defenses, are increasingly ineffective against modern cyber threats. Attackers exploit vulnerabilities and compromised credentials to bypass perimeter defenses, leading to significant data breaches and system compromises. Zero trust security eliminates the notion of trust within the network, enforcing strict verification processes for every access request to resources, regardless of the user's location or network segment.
This article explores the principles, mechanisms, benefits, implementation strategies, and potential challenges of zero trust security.

What Is Meant by Zero Trust Security?
Zero trust security is a comprehensive cybersecurity model that operates on the foundational principle of "never trust, always verify." Coined by Stephen Paul Marsh in 1994, zero trust shifts the security focus from the perimeter to individual users, devices, applications, and data flows. Unlike traditional models that assume entities within the network are trustworthy, zero trust treats all interactions as potentially malicious, requiring continuous authentication, authorization, and validation before granting access to any resources.
This model addresses the evolving threat landscape where attackers exploit the implicit trust granted to internal network entities. By enforcing strict access controls and continuous monitoring, zero trust minimizes the risk of unauthorized access, lateral movement within the network, and data exfiltration. To create a robust, dynamic security posture, it integrates various security technologies and practices, including identity and access management (IAM), micro-segmentation, endpoint security, and advanced data analytics.
Zero Trust Security Example
Imagine a multinational corporation where employees access sensitive financial data stored on cloud servers. In a traditional security setup, an employee connected to the corporate network or via a virtual private network (VPN) might gain access based on network credentials alone. This approach assumes trust based on network location, which is easily exploitable.
Under zero trust security, the employee must first undergo multi-factor authentication (MFA), which combines something they know (password), something they have (hardware token or mobile device), and something they are (biometric verification, such as fingerprint or facial recognition). The authentication process might leverage protocols like time-based one-time password (TOTP) or FIDO2 standards for secure MFA.
The device used must comply with corporate security policies and undergo a posture assessment to verify the latest security patches, encryption status, installed security software, and configuration compliance. Tools like endpoint detection and response (EDR) or mobile device management (MDM) solutions enforce these policies.
Access to financial data is granted through a software-defined perimeter (SDP) that creates a secure, encrypted connection directly between the user and the resource. Network micro-segmentation ensures that the employee can access only the specific data required for their role, with access policies enforced by policy enforcement points (PEPs) using technologies like next-generation firewalls (NGFWs) or cloud access security brokers (CASBs).
Continuous monitoring detects any abnormal behavior during the session. For instance, if the user's behavior deviates from established patterns, such as accessing substantial amounts of data or attempting to access unauthorized resources, user and entity behavior analytics (UEBA) solutions flag these activities for immediate investigation or automated response actions.
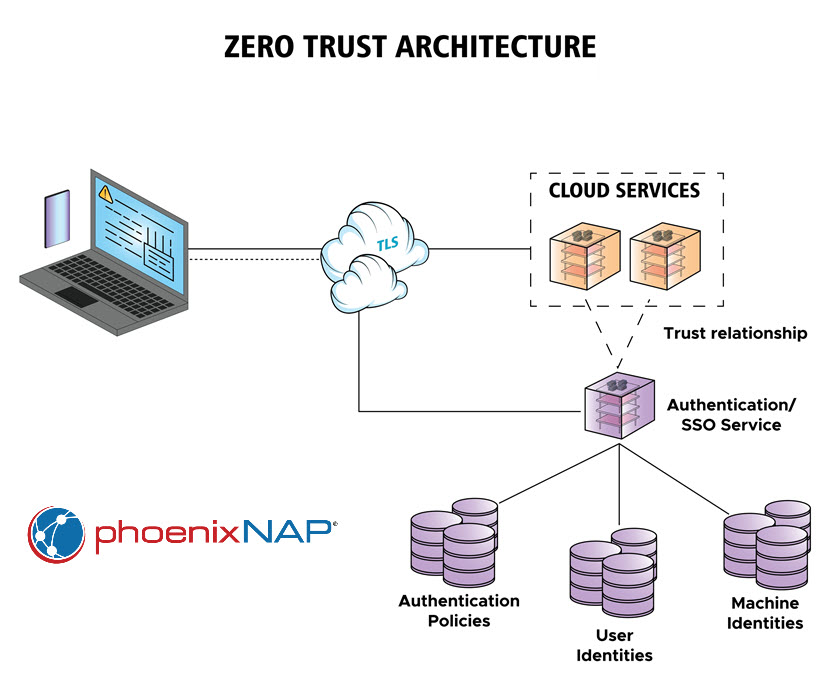
Traditional Security Architecture vs. Zero Trust Architecture
Traditional network security models rely on the "castle-and-moat" concept, focusing on securing the network perimeter while assuming that entities inside the network are trustworthy. This approach has significant limitations in modern IT environments due to factors like cloud computing, mobile workforces, and bring-your-own-device (BYOD) policies. Attackers who breach the perimeter face minimal resistance moving laterally within the network, leading to widespread data breaches.
In contrast, zero trust architecture eliminates the notion of a trusted internal network. Every user, device, and application must be authenticated and authorized, regardless of their location or network segment. This paradigm shift addresses the shortcomings of traditional models by:
- Eliminating implicit trust. No user or device is trusted by default, reducing the risk of insider threats and unauthorized access.
- Adapting to modern workloads. Zero trust is designed to secure cloud services, remote workers, and distributed systems.
- Preventing lateral movement. Network segmentation and strict access controls limit attackers' ability to move within the network if a breach occurs.
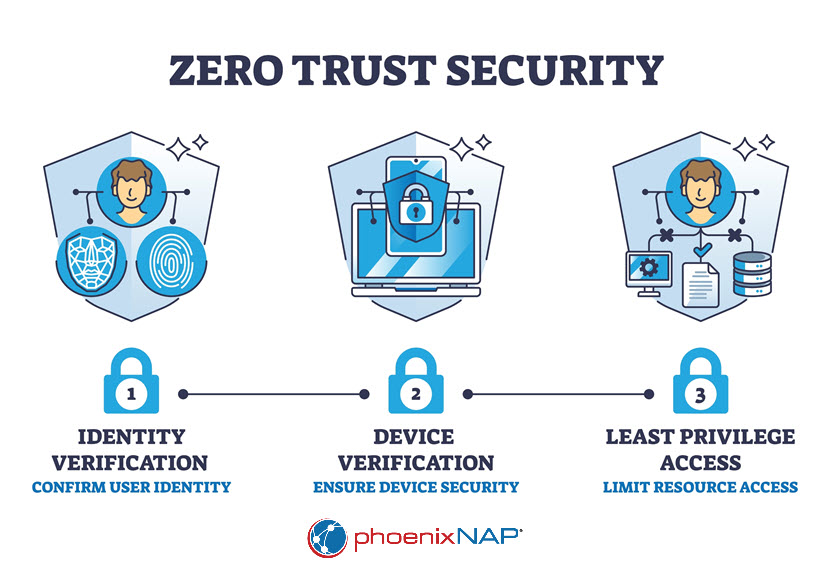
Zero Trust Security Principles
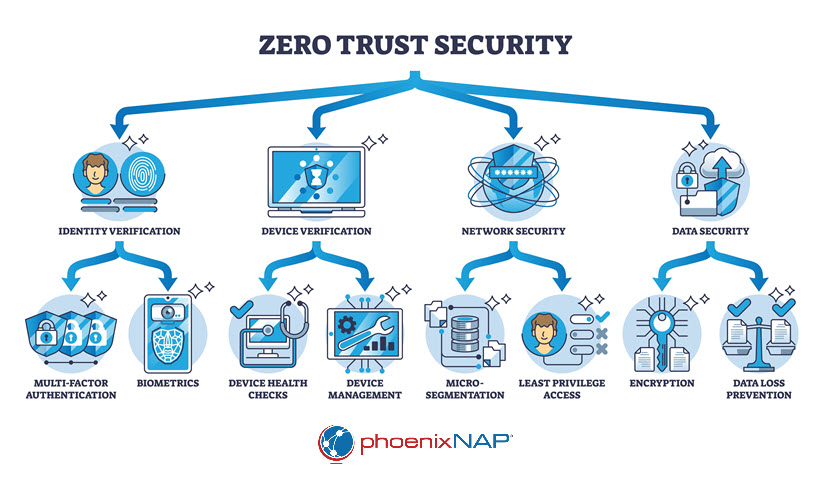
Understanding and implementing the core principles of zero trust security is crucial for building a resilient cybersecurity architecture. These principles guide the deployment of technologies and policies that collectively enforce the zero trust model.
Continuous Verification
Zero trust requires rigorous and continuous verification of every access request, employing a dynamic and context-aware approach to authentication and authorization. Verification encompasses multiple factors:
- User authentication. Implementing strong authentication mechanisms, such as MFA, adaptive authentication, and identity proofing. Protocols such as OAuth 2.0, OpenID Connect, and Security Assertion Markup Language (SAML) enable secure authentication and authorization across different systems and platforms.
- Device authentication and posture assessment. Validating device identities using digital certificates or device fingerprints. Posture assessment tools evaluate compliance with security policies, checking for encryption, antivirus status, operating system versions, and the presence of vulnerabilities.
- Contextual factors. Consideration is given to additional context, including geolocation, time of access, network type (wired, wireless, VPN), and the sensitivity of the requested resource. Risk-based authentication adjusts the verification requirements based on the assessed risk level.
- Session management. Monitoring active sessions for anomalies, enforcing session timeouts, and requiring re-authentication under certain conditions. Technologies like JSON web tokens (JWT) and security token services (STS) manage secure session tokens.
Multi-Factor Authentication
MFA is a critical component of zero trust security. It requires users to provide multiple forms of verification before granting access. By combining:
- Something the user knows. Passwords or PINs.
- Something the user has. Security tokens, smart cards, or mobile devices.
- Something the user is. Biometric verification, such as fingerprints or facial recognition.
Read our comparison article on biometrics vs. passwords to learn the advantages and drawbacks of each method.
Least Privilege Access
Implementing least privilege access minimizes the attack surface by ensuring users and applications have only the permissions necessary to perform their tasks. Achieving this requires:
- Role-based access control (RBAC). Defining roles with specific permissions and assigning users accordingly. This step simplifies management but can be inflexible in dynamic environments.
- Policy decision points (PDP) and policy enforcement points (PEP). Separating policy decision logic from enforcement mechanisms. PDPs evaluate access requests against policies, while PEPs enforce the decisions at the resource level.
- Attribute-based access control (ABAC). Using attributes (user attributes, resource attributes, environmental attributes) to define access policies enables more granular and dynamic control.
- Privileged access management (PAM). Controlling and monitoring access to critical systems by privileged users, using tools that manage credential storage, session recording, and command filtering.
- Just-in-time (JIT) access. Providing temporary, time-bound access privileges when necessary, reducing standing privileges that attackers might exploit.
Micro-Segmentation
Micro-segmentation enhances security by dividing the network into isolated segments or zones, each with its own security controls. This limits the potential impact of a breach by containing it within a segment. Implementation involves:
- Software-defined networking (SDN). Abstracting network control from hardware to software allows dynamic network configuration and segmentation.
- Virtual local area networks (VLANs) and virtual extensible LANs (VXLANs). Creating logical network segments that isolate traffic at Layer 2 or Layer 3.
- Host-based firewalls and agents. Deploying security controls at the host level, using agents that enforce policies and monitor traffic.
- Network access control lists (ACLs). Defining rules that permit or deny traffic between segments based on IP addresses, ports, and protocols.
- Zero trust network access (ZTNA). Implementing per-application access controls, where users are granted access only to specific applications rather than broad network segments.
Assume Breach Mentality
Adopting an "assume breach" mindset involves proactive strategies to detect, respond to, and recover from security incidents. Key practices include:
- Advanced threat detection. Deploying tools like endpoint detection and response, network detection and response, and user and entity behavior analytics to detect sophisticated threats, including zero-day exploits and insider attacks.
- Deception technologies. Using honeypots, honey tokens, and decoy systems to lure attackers and gather intelligence on their tactics.
- Security orchestration, automation, and response (SOAR). Automating incident response workflows to accelerate containment and remediation efforts.
- Comprehensive logging and monitoring. Implementing centralized logging of all security events, using security information and event management (SIEM) solutions to correlate and analyze data.
- Implement data backup strategies. Regularly back up critical data to minimize loss during an incident.
- Regular red team exercises and penetration testing. Simulating attacks to evaluate the effectiveness of security controls and incident response plans.
- Develop incident response plans. Outline procedures for responding to security incidents effectively.
Download our cyber security incident response plan (CSIRP) checklist for a step-by-step guide to incident response.
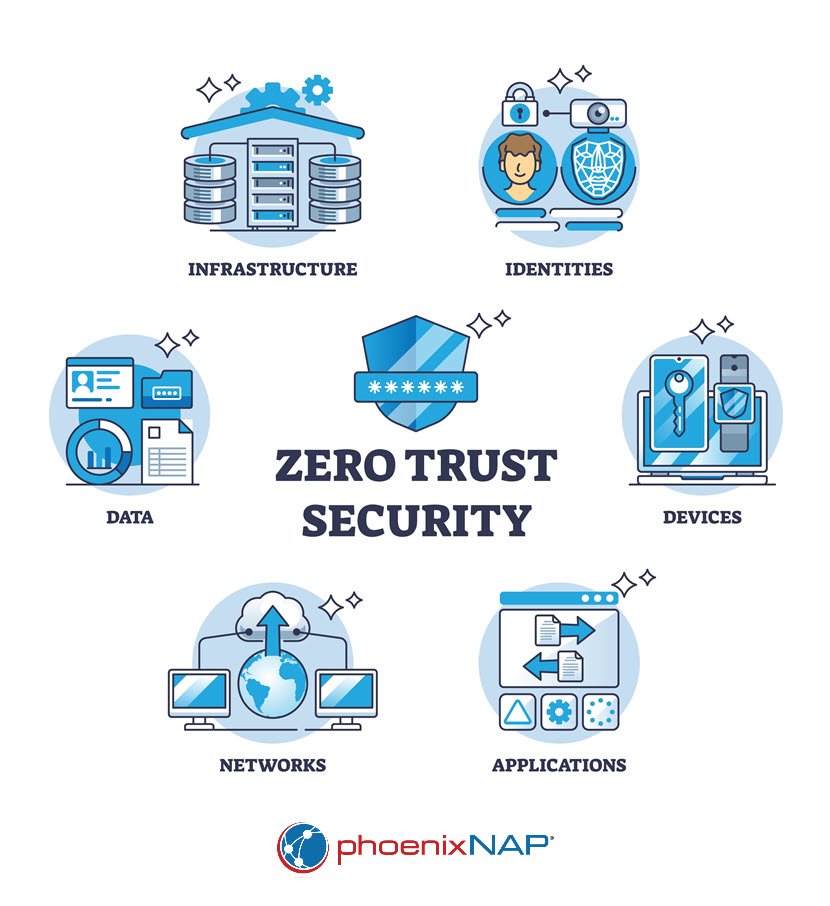
Zero Trust Security Use Cases
Zero trust security is applicable across various domains where traditional security models are insufficient. Below are practical applications illustrating how zero trust enhances security in different environments.
Securing Remote Workforces
Securing access from diverse locations and devices has become a crucial security concern with the rise of remote work. Zero trust secures remote access by providing granular, application-specific connections without exposing the entire network.
This method improves upon traditional VPNs by granting access only to necessary applications, enhancing security, and reducing the attack surface for remote employees.
Protecting Cloud Environments
As organizations migrate to hybrid and multi-cloud infrastructures, zero trust ensures consistent security policies across all environments.
Implementing zero trust in the cloud allows for agility and maintains uniform security controls, effectively securing cloud-native applications and services regardless of their deployment location.
Protecting Sensitive Data
Industries managing sensitive data, such as healthcare and finance, benefit from zero trust through enhanced data protection. Zero trust emphasizes compliance with regulations and reduces the risk of data breaches by focusing on data encryption and data loss prevention strategies.
Additionally, strict access controls and continuous monitoring ensure that only authorized users can access sensitive information.
Mitigating Insider Threats
Zero trust helps detect and respond to insider threats by monitoring user behavior for anomalies. Behavior monitoring identifies unusual activities that may indicate compromised accounts or malicious intent.
This early detection and response capability minimizes the potential impact of insider threats, ensuring that users access only the resources necessary for their roles.
Enhancing Supply Chain Security
Supply chain attacks, which exploit vulnerabilities in third-party vendors and partners, have skyrocketed since the pandemic, increasing by over 300%. Zero trust architecture offers a solution by extending security policies to external entities.
These policies require them to adhere to the same verification standards as internal users. Organizations significantly reduce the risks associated with external partnerships by limiting third-party access to essential resources and closely monitoring their activities.
What Does Zero Trust Security Protect?
Zero trust security protects all aspects of an organization's digital environment:
- Data. By implementing strict access controls and encryption, zero trust protects sensitive information, including personally identifiable information (PII), protected health information (PHI), payment card information (PCI), and intellectual property (IP).
- People. Zero trust enforces authentication and authorization policies for all users, reducing risks associated with phishing, compromised credentials, and malicious insiders.
- Networks. Through network segmentation and micro-segmentation, zero trust protects network infrastructure from unauthorized access and lateral movement by attackers.
- Devices. By verifying device compliance and health, zero trust secures endpoints, including laptops, mobile devices, IoT devices, and servers, preventing them from becoming entry points for attackers.
- Workloads. The security model protects applications and services, ensuring that only legitimate processes communicate within the environment, securing workloads across on-premises and cloud platforms.
Discover the most common types of cyber attacks you are most likely to encounter.
What Are the Benefits of Zero Trust Security?
Zero trust security offers significant advantages that enhance an organization's cybersecurity posture and operational resilience.
- Reduced risk of data breaches. By enforcing continuous verification and the principle of least privilege, zero trust significantly lowers the likelihood of unauthorized access and data breaches.
- Improved compliance posture. Zero trust aligns with regulatory requirements by enforcing robust security measures. Organizations demonstrate compliance with standards like GDPR, HIPAA, PCI DSS, and ISO/IEC 27001 by implementing strong authentication, access controls, encryption, and continuous monitoring.
- Flexibility and scalability. Zero trust models are adaptable to various network architectures, including on-premises, cloud, and hybrid environments. Organizations can scale their security measures along with business growth, integrating new technologies and accommodating changing operational needs without compromising security.
- Enhanced visibility and control. Continuous monitoring and advanced analytics provide detailed insights into network activities and user behaviors. This visibility enables proactive threat detection, swift incident response, and informed decision-making regarding security policies and resource allocation.
- Increased business agility. Zero trust decouples security policies from the underlying network infrastructure, allowing organizations to move applications and data across environments without manually reconfiguring security settings. This flexibility accelerates deployment times and supports business growth.
- Protection against advanced threats. Zero trust effectively counters sophisticated cyber threats, including zero-day exploits, advanced persistent threats (APTs), and insider threats. The model's emphasis on verification, micro-segmentation, and continuous monitoring disrupts common attack vectors and limits the impact of successful breaches.
Discover the best network security tools and enhance your organization's safety.

How to Implement Zero Trust Security?
Implementing zero trust security requires a strategic, phased approach that addresses technological, organizational, and cultural aspects.
The following best practices guide organizations through the implementation process.
1. Conduct a Comprehensive Security Assessment
Begin by evaluating your current security situation:
- Asset inventory. Catalog all assets, including devices, applications, data repositories, and network components.
- Threat modeling. Analyze potential threats and vulnerabilities within the current infrastructure.
- User and role mapping. Identify all users, their roles, and existing access privileges.
- Gap analysis. Compare existing security measures against zero trust principles to identify areas needing improvement.
2. Define the Protect Surface
Focus on the most critical assets:
- Data classification. Identify sensitive data, intellectual property, and mission-critical information.
- Transactional flows. Understand how data moves within the organization, mapping interactions between users, applications, and data.
- Application mapping. Determine which applications and services support critical business functions.
- Prioritize protection efforts. Allocate resources to protect the most valuable assets first.
3. Enforce Strict Access Controls
Develop and enforce granular access policies:
- Adopt RBAC or ABAC models. Define roles or attributes that dictate access permissions.
- Regularly review access rights. Conduct periodic audits to ensure that access privileges remain appropriate.
- Use policy engines. Implement solutions that evaluate access requests in real time based on policies.
- Implement just-in-time access. Provide temporary access when necessary, reducing standing privileges.
4. Establish Strong Identity Verification Processes
Implement robust IAM solutions:
- Deploy MFA across the organization. Ensure all users, including administrators and third parties, use MFA.
- Centralize identity management. Use directory services like Active Directory, LDAP, or cloud-based identity providers for unified management.
- Implement adaptive authentication. Adjust authentication requirements based on risk assessments.
- Integrate IAM with applications. Ensure that applications support modern authentication protocols for seamless integration.
5. Implement Micro-Segmentation
Isolate network segments to contain potential breaches:
- Use SDN and virtualization technologies. Leverage tools like VMware NSX or OpenStack Neutron for network segmentation.
- Deploy host-based controls. Install agents or host firewalls that enforce policies at the workload level.
- Define segmentation policies. Determine how segments interact, specifying allowed traffic flows.
- Monitor east-west traffic. Inspect internal traffic between segments for malicious activity.
6. Integrate Security Automation and Orchestration
Enhance efficiency and consistency through automation:
- Automate routine tasks. Utilize scripts and automation tools to handle updates, patches, and compliance checks.
- Implement infrastructure as code (IaC). Manage configurations and deployments programmatically, ensuring consistency.
- Orchestrate security controls. Coordinate actions across different security tools and platforms.
- Use DevSecOps practices. Integrate security into development and operational processes.
Master automated security testing best practices before removing manual tasks from your security processes.
7. Deploy Continuous Monitoring Tools
Invest in comprehensive monitoring and analytics solutions:
- Implement SIEM systems. Centralize log collection and analysis from all relevant sources.
- Use NTA and DPI tools. Monitor network traffic at a granular level.
- Adopt UEBA solutions. Analyze user behaviors to detect anomalies.
- Automate responses. Utilize security orchestration and automation response (SOAR) platforms to streamline and manage incident response workflows.
- Integrate threat intelligence. Leverage external data to enhance detection capabilities.
8. Develop a Zero Trust Policy Framework
Establish clear policies and guidelines:
- Define security policies. Document principles, access controls, incident response procedures, and compliance requirements.
- Enforce policies consistently. Apply policies across all environments, including on-premises, cloud, and mobile.
- Communicate policies clearly. Ensure that all stakeholders understand their responsibilities.
- Regularly update policies. Adapt to changing threats, technologies, and business needs.
9. Educate and Train Staff
Promote a security-aware culture:
- Provide training programs. Offer regular training on cybersecurity best practices, security awareness, and policy compliance.
- Engage leadership. Secure buy-in from executive management to prioritize security initiatives.
- Encourage reporting of incidents. Create an environment where employees feel comfortable reporting security concerns.
- Assess and reinforce learning. Use assessments to gauge understanding and reinforce training as needed.

What Are the Downsides of Zero Trust Security?
Implementing zero trust security presents specific challenges that organizations must consider and address:
- Implementation complexity. Transitioning to a zero trust model requires significant changes to existing network architectures and security protocols. This complexity demands careful planning, expertise, and coordination across multiple departments.
- User experience challenges. Strict verification processes lead to user frustration if not implemented thoughtfully.
- High initial costs. Investing in new technologies, training personnel, and restructuring security processes involves substantial financial outlay. Small and medium-sized companies may find the costs prohibitive without careful budgeting and prioritization.
- Continuous maintenance requirements. Zero trust demands ongoing efforts to monitor, update, and manage security measures. Dedicated personnel and resources are necessary to maintain effectiveness, increasing operational expenses.
- Integration with legacy systems. Legacy applications and systems often lack support for modern security standards and integration with zero trust technologies. This limitation necessitates additional efforts to secure or replace outdated systems.
- Vendor and technology selection. Navigating a multitude of vendors and technologies in a zero trust space is challenging. Organizations must carefully evaluate solutions to meet specific needs without creating vendor lock-in.
- Cultural resistance. Shifting to a zero trust model may face resistance from staff accustomed to traditional security approaches. Change management strategies are essential to facilitate adoption.
- Potential for overhead and latency. Implementing additional security layers may introduce processing overhead and network latency. Optimizing configurations and leveraging efficient technologies is crucial to minimizing performance impacts.

Advancing Security with Zero Trust
Zero trust security addresses the weaknesses of traditional models by eliminating implicit trust and enforcing continuous verification. This approach enhances defenses against unauthorized access, data breaches, and advanced cyber attacks in complex IT environments. By leveraging the insights and best practices outlined in this guide, you can navigate the complexities of zero trust, tailor solutions to your organization's needs, and contribute to a more secure digital landscape.



