An advanced persistent threat (APT) is among the most dangerous cyber threats a company can face. These attacks are hard to detect and allow an intruder to hide within a network for months. While hackers stay in the system, a company suffers regular data losses and outages without knowing the cause of problems.
This article is an introduction to APT attacks. We explain what APTs are, teach how to recognize signs of infection, and show ways to prepare for this type of an attack.
What Is an APT Attack?
An advanced persistent threat (APT) is a cyberattack in which an intruder gains and maintains a long-term presence within a network. The consequences of an APT attack are vast and include:
- Loss of data and intellectual property.
- Infrastructure sabotage.
- Service outage.
- Total site takeovers.
APTs are multi-stage attacks that take weeks to set up and last for months or even years. An APT is different from common cyberattacks in four critical ways:
- An APT is more complex than a usual online threat. Attacks require full-time teams to maintain a hidden presence in the target network.
- APTs are not hit-and-run attacks. Once hackers access a network, their goal is to remain inside for as long as possible.
- An APT is mostly a manual attack that does not rely on automation.
- APTs are not a threat to a large pool of targets. Attacks go after a specific company, so each breach has a custom plan that fits only the target’s defenses.
An APT attack requires a great deal of effort and resources. Hackers typically go after high-value targets, such as enterprises and corporations. However, APT attackers frequently target small firms in the supply chain of larger organizations.
Hackers often use less defended companies as entry points, so businesses of all sizes must know how to recognize an APT attack.
Create a robust security strategy by implementing cybersecurity best practices.
What Is the Main Goal of an APT Attack?
The goal of an APT attack is to infiltrate the network undetected and spend enough time inside to steal data. All valuable data is a potential target for an APT, including:
- Intellectual property.
- User PII.
- Classified data.
- Infrastructure data.
- Access credentials.
- Sensitive communications.
Besides stealing data, an APT’s objective can also include sabotaging infrastructure, destroying individual systems, or completing site takeovers. Each attack serves a unique purpose, with the ultimate goal often being a combination of data breaches, cyber espionage, and sabotage.
APT Attack Detection: What Are the Signs of an APT Attack?
APT hackers employ advanced methods to conceal their activity, but certain system anomalies can indicate that an attack is in progress.
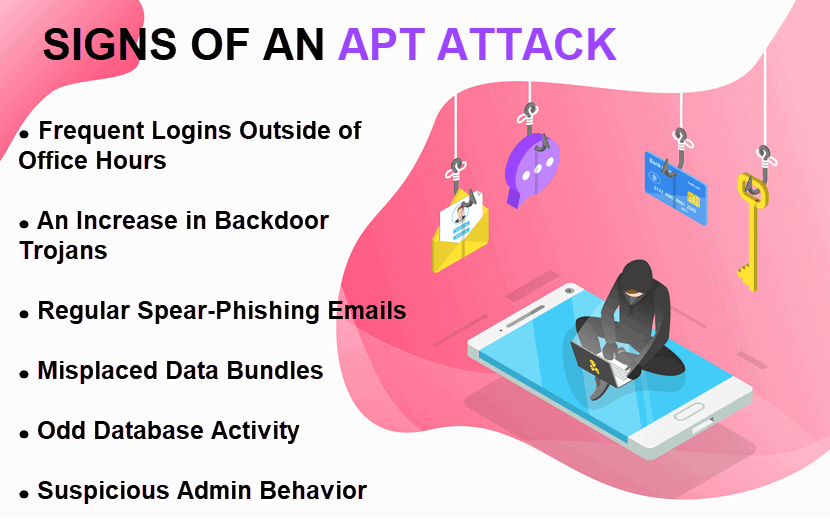
Unexpected Logins
Stolen login credentials are a primary method APT attackers use to gain network access. Frequent logins to servers at odd hours may indicate an ongoing APT attack. Hackers could be working in a different time zone or operating at night to decrease the chance of detection.
An Increase in Backdoor Trojans
If tools detect more backdoor trojans than usual, an APT attack could be the cause. APT attackers use backdoor Trojans to ensure continued access in case the login credentials change.
Spear-Phishing Emails
Spear-phishing emails are a clear sign of a potential APT. Hackers may be sending these emails to upper-management employees with the hope of accessing restricted data.
Data Bundles
APT attackers often copy and store the data they want to steal to another location in the network. Once isolated and bundled, the files become a more convenient transfer target.
Attackers place bundles in places where the team does not typically store data. Regularly scan for and inspect any misplaced or unusual data files.
Strange Database Activity
Odd database activity may be an indicator of an APT. Be cautious of sudden spikes in database operations involving large data volumes.
Suspicious Behavior of Admin Accounts
Take note of any change in the behavior of administrator accounts. APT hackers rely on admin rights to move laterally through the network and infect larger surfaces. The creation of new accounts with strange patterns is also a sign of a potential APT.
APT Attack Lifecycle: The 4 Stages of an APT Attack
An APT attack involves multiple phases and a variety of attack techniques. A typical attack has four stages: planning, infiltration, expansion, and execution.
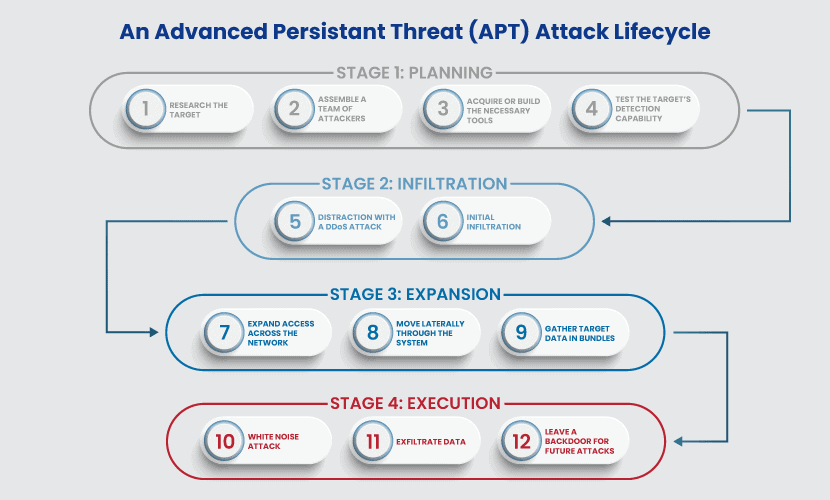
Stage 1: Planning
Every APT project requires a custom plan on how to beat the target’s protection systems. Hackers must perform the following steps during the planning stage:
- Define the target and the goal of the operation.
- Identify the necessary skills and hire team members.
- Find (or create) the right tools for the job.
- Learn about the target architecture, access controls, and all hardware and software solutions.
- Define the optimal approach for engineering the attack.
Once they gather all the information, attackers deploy a small version of the software. This reconnaissance program helps test alarms and identify system weak spots.
Test your system defenses with vulnerability assessment scanning tools.
Stage 2: Infiltration
The attacker gains access to the network. Infiltration typically occurs through one of three attack surfaces:
- Web assets.
- Network resources.
- Authorized human users.
To gain initial access, APT hackers use various attack methods, including:
- Advanced exploits of zero-day vulnerabilities.
- Social engineering techniques.
- High-target spear phishing.
- Remote file inclusion (RFI).
- RFI or SQL injections.
- Cross-site scripting (XSS).
- Physical malware infection.
- The exploitation of application weaknesses (especially zero-day bugs).
- Domain Name System (DNS) tunneling.
A common tactic during the infiltration is to launch a simultaneous DDoS attack. DDoS distracts the staff and weakens the perimeter, making it easier to breach the network.
Once they achieve initial access, attackers quickly install a backdoor malware that grants network access and allows remote operations.
Stage 3: Expansion
After they establish a foothold, attackers expand their presence within the network. The expansion involves moving up the user hierarchy and compromising staff members with access to valuable data. Brute force attacks are a usual tactic during this stage.
Malware is critical to APT as it allows hackers to maintain access without detection. The malware helps the attacker to:
- Hide from system controls.
- Navigate between network segments.
- Gather sensitive data.
- Monitor network activity.
- Detect new entry points in case existing ones become inaccessible.
At this stage, the attacker has reliable and long-term network access. Security controls are unaware of the danger, and the intruder can start completing the attack objective. If the goal is to steal data, attackers store information in bundles and hide them in a part of the network with little to no traffic.
Stage 4: Execution
Once they collect enough data, the thieves try to extract the information. A typical extraction tactic is to use white noise to distract the security team. Data transfer happens while the network personnel and the system’s defenses are busy.
APT teams typically try to complete the extraction without giving away their presence. Attackers often leave a backdoor after exiting the system, with the goal of accessing it again in the future.
If the APT attack’s goal is to sabotage a system, the execution phase acts out differently. Hackers subtly gain control of critical functions and manipulate them to cause damage. For example, attackers can destroy entire databases and then disrupt communications to prevent disaster recovery services.
Again, the goal is to cause damage without the security team discovering the intruders. This stealth approach allows repeat attacks.
How to Prevent an APT Attack
Standard security measures, such as antivirus programs, cannot effectively protect a company from an APT attack. APT detection and protection require various defense tactics and collaboration between network administrators, security teams, and all users.
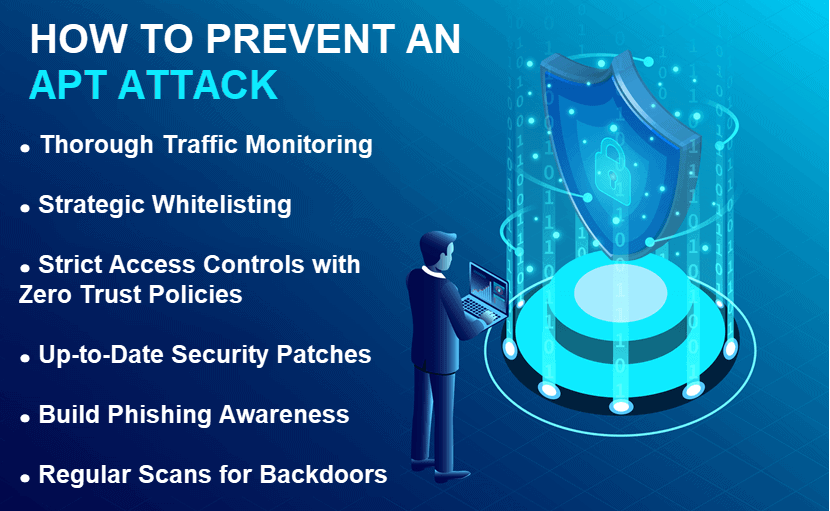
Monitor Traffic
Monitoring traffic is critical for:
- Preventing backdoor setups.
- Blocking stolen data extraction.
- Identifying suspicious users.
Examining traffic inside and outside the network perimeter helps detect any unusual behavior. A web application firewall (WAF) on the network’s edge should filter all traffic to servers. A WAF prevents application-layer attacks like RFI and SQL injections, two common attacks in the APT infiltration phase.
Internal traffic monitoring is also vital. Network firewalls offer an overview of user interactions and help identify irregular logins or odd data transfers. Internal monitoring also allows a business to watch over file shares and system honeypots while detecting and removing backdoor shells.
Use server monitoring tools to ensure the health and safety of your servers.
Whitelist Domains and Applications
Whitelisting is a method of controlling what domains and applications are accessible from a network. Whitelisting reduces the APT success rate by minimizing the number of attack surfaces.
For whitelisting to work, a team must carefully select acceptable domains and applications. Strict update policies are also necessary, as you must ensure users are always running the latest version of all applications.
Establish Strict Access Controls
Employees are typically the most vulnerable point in a security perimeter. APT intruders often try to turn employees into an easy gateway to bypass the defenses.
The best method to protect a business from malicious insiders is to rely on the Zero Trust policy. Zero Trust security limits access levels of each account, granting access only to resources a user requires to perform the job.
In a Zero Trust environment, a compromised account limits the intruder’s ability to move through the network.
Another useful security measure is to use two-factor authentication (2FA). 2FA requires users to provide a second form of verification when accessing sensitive areas of the network. An additional layer of security on each resource slows down intruders moving through the system.
Keep Security Patches Up to Date
Keeping patches up to date is vital to preventing an APT attack. Ensuring network software has the latest security updates reduces the risk of vulnerabilities and compatibility issues.
Prevent Phishing Attempts
Phishing fraud is a usual entry point for an APT attack. Train employees to recognize phishing attempts and instruct them on how to respond when they encounter one.
Email filtering helps prevent the success rate of phishing attacks. Filtering and blocking malicious links or attachments within emails stops penetration attempts.
Use email security best practices and protect your inboxes from malicious activity.
Perform Regular Scans for Backdoors
APT hackers leave backdoors across the network after they gain illegal access. Scanning for and removing backdoors is an effective method of stopping current and preventing future APT attempts.
Experts suggest looking for:
- Command shells (WMI, CMD, and PowerShell) that establish network connections.
- Remote server or network administration tools on non-administrator systems.
- Microsoft Office documents, Flash, or Java incidents that invoke new processes or spawn command shells.
Remember to scan endpoint devices for backdoors and other malware. APT attacks often involve a takeover of an endpoint device, so detecting and responding to a compromise is a priority.
Learn about Managed Detection and Response (MDR), the most effective method of removing system threats.
Know the Gravity of APTs and Be Ready for an Attack
The consequences of an APT attack can be extreme. Loss of data and reputation is almost a guarantee, so take every possible step to prevent an attack. Luckily, now you know what an APT is and how to recognize one, so you are ready to reinforce and protect your workloads. Learn about the cyber kill chain, which can help you understand and predict different stages of a cyberattack. Knowing how hackers work enables a company to select the right tools and strategies to limit breaches, respond to in-progress attacks, and minimize risks.