Brute force attacks are alluring for hackers as they are often reliable and simple.
Hackers do not need to do much of the work. All they have to do is create an algorithm or use readily available brute force attack programs to automatically run different combinations of usernames and passwords until they find the right combination. Such cyberattacks account for roughly 5 percent of all data breaches. According to statistics on data breaches, it only takes one data breach to create severe adverse implications for your business.
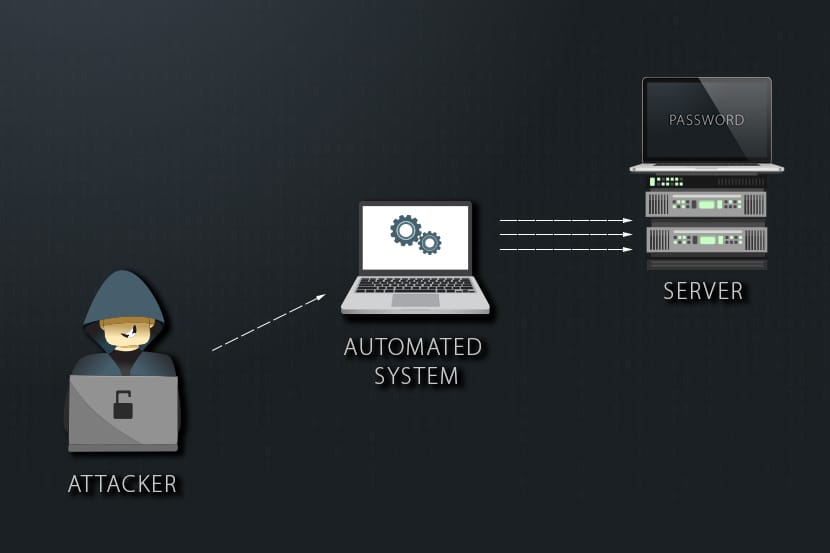
What is a Brute Force Attack?
The phrase “brute force” describes the simplistic manner in which the attack takes place. Since the attack involves guessing credentials to gain unauthorized access, it’s easy to see where it gets its name. Primitive as they are, brute force attacks can be very effective.
The majority of cyberattackers who specialize in brute force attacks use bots to do their bidding. Attackers will generally have a list of real or commonly used credentials and assign their bots to attack websites using these credentials.
Manual brute force cracking is time-consuming, and most attackers use brute force attack software and tools to aid them. With the tools at their disposal, attackers can attempt things like inputting numerous password combinations and accessing web applications by searching for the correct session ID, among others.
How Brute Force Attacks Work
In simple terms, brute force attacks try to guess login passwords. Brute force password cracking comes down to a numbers game.
For most online systems, a password is encouraged to be at least eight characters long. Most passwords are eight characters long, often combining numeric and alphabetic (case-sensitive) characters, which provides 62 possibilities for each character in a password chain. If we combine 62 options for every character in an eight-character password, the result would be 2.18 trillion possible combinations. That is a lot of combinations for a cyberattacker to try.
In the past, if a hacker tried to crack an eight-character password with one attempt per second, it would roughly take seven million years at most. Even if the hacker were able to attempt 1000 combinations per second, it would still take seven thousand years.

It’s a different story nowadays, with brute force hacking software having the power to attempt vastly more combinations per second than mentioned above. For example, let’s say a supercomputer can input 1 trillion combinations per second. With that amount of power, a hacker can reduce the time it takes to try 2.18 trillion password/username combinations to just 22 seconds!
Computers manufactured within the last decade have advanced to the point where only two hours are necessary to crack an eight-character alphanumeric password. Many cyber attackers can decrypt a weak encryption hash in months by using an exhaustive key search brute force attack.
The example above applies to password combinations of 8 characters in length. The time it takes to crack a password varies depending on its length and overall complexity.
Why Hackers Use Brute Force Attacks?
Hackers use brute force attacks during initial reconnaissance and infiltration. They can easily automate brute force attacks and even run them in parallel to maximize their chances of cracking credentials. However, that is not where their actions stop.
Once they gain access to a system, attackers will attempt to move laterally to other systems, gain advanced privileges, or run encryption downgrade attacks. Their end goal is to cause a denial of service and get data out of the system.
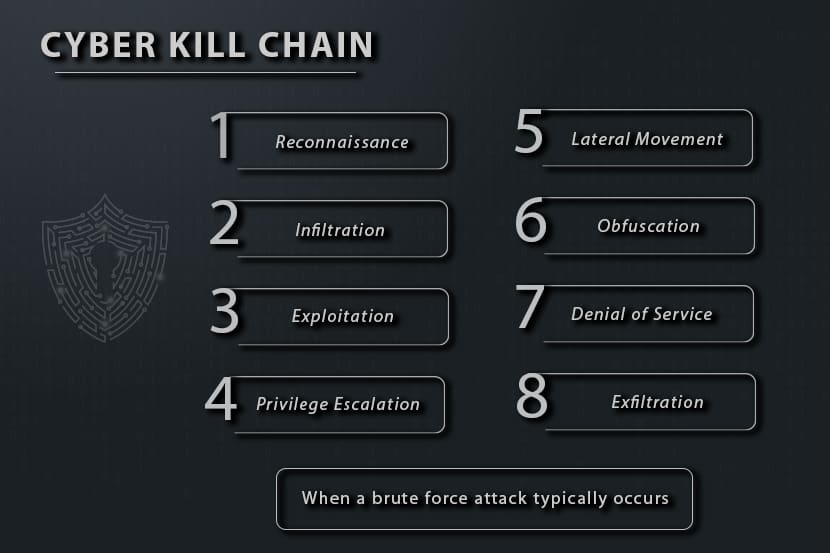
Brute force attacks are also used to find hidden web pages that attackers can exploit. This attack can be programmed to test web addresses, find valid web pages, and identify code vulnerabilities. Once identified, attackers use that information to infiltrate the system and compromise data.
Types of Brute Force Attacks
Brute force cracking boils down to inputting every possible combination access is gained. However, there are variants of this kind of attack.
Dictionary Attack
A dictionary attack uses a dictionary of possible passwords and tests them all.
Instead of using an exhaustive key search, where they try every possible combination, the hacker begins from an assumption of common passwords. They build a dictionary of passwords and iterate the inputs.
With this approach, hackers eliminate the need to attack websites randomly. Instead, they can acquire a password list to improve their chances of success.
Dictionary attacks often need a large number of attempts against multiple targets.
Simple Brute Force Attack
A simple brute force attack is used to gain access to local files, as there is no limit to the number of access attempts. The higher the scale of the attack, the more successful the chances of entry.
Simple brute force attacks circulate by inputting all possible passwords one at a time.
Hybrid Brute Force Attack
The hybrid brute force attack combines aspects of both the dictionary and the simple brute force attack. It begins with an external logic, such as the dictionary attack, and modifies passwords in a manner akin to a simple brute force attack.
The hybrid attack utilizes a list of passwords, creating and testing small variations of the words in the list, such as case changes and number additions, instead of testing every password individually.
Reverse Brute Force Attack
The reverse brute force attack flips the method of guessing passwords on its head. Rather than guessing the password, it will use a generic one and try to brute force a username.
Credential Recycling
As the name suggests, credential recycling reuses passwords. Since many institutions don’t use password managers or have strict password policies, password reuse is an easy way to gain access to accounts.
Because these cyberattacks depend entirely on lists of second-hand credentials gained from data breaches, they have a low rate of success. It’s essential to update usernames and passwords after a breach regularly to limit the effectiveness of stolen credentials.
Rainbow Table Attacks
Rainbow table attacks are unique as they don’t target passwords; instead, they are used to target the hash function, which encrypts the credentials.
The table is a precomputed dictionary of plain text passwords and corresponding hash values. Hackers can then see which plain-text passwords produce a specific hash and expose them.
When a user enters a password, it is converted into a hash value. If the inputted password hash value matches the stored hash value, the user authenticates. Rainbow table attacks exploit this process.
Examples of Brute Force Attacks
How common are brute force attacks?
Brute force attacks are so frequent that everyone, from individuals to enterprises operating in the online realm, has experienced such an attack. The organizations that have been hit the hardest in the last couple of years include:
- In 2018, Firefox’s master password feature was proven to be easily cracked with a brute force attack. It is unknown how many users’ credentials were exposed. In 2019. Firefox deployed a fix to resolve this issue.
- In March 2018, Magento was hit by a brute force attack. Up to 1000 admin panels had been compromised.
- In March 2018, several accounts of members of the Northern Irish Parliament had been compromised in a brute force attack.
- In 2016, a brute force attack resulted in a massive data leak in the e-commerce giant, Alibaba.
- According to Kaspersky, RDP-related brute force attacks rose dramatically in 2020 due to the COVID-19 pandemic.
Every brute force attack’s end-goal attack is to steal data and/or cause a disruption of service.
How to Detect Brute Force Attacks
The key indication that a bad actor is trying to brute force their way into your system is to monitor unsuccessful login attempts. If you see there have been many repeated failed login attempts, be suspicious. Watch for signs of multiple failed login attempts from the same IP address and the use of multiple usernames from the same IP address.
Other signs can include a variety of unrecognized IP addresses unsuccessfully attempting to log in to a single account, an unusual numerical or alphabetical pattern of failed logins, and multiple login attempts in a short time period.
It’s also possible for these cyberattacks to add you to a botnet that can perform denial-of-service attacks on your website. Aside from the above, spam, malware, and phishing attacks can all be the prerequisite of a brute force attack.
If you receive an email from your network service provider notifying you of a user from an unrecognized location logged into your system, immediately change all passwords and credentials.
In Conclusion, Stay Safe and Secure
The primitive nature of brute force attacks means there is an easy way to defend against them. The best defense against a brute force attack is to buy yourself as much time as you can, as these types of cyber attacks usually take weeks or months to provide anything of substance to the hacker. The simplest precaution you can take to boost your accounts’ security is to use strong passwords.
It is also highly recommended to monitor servers and systems at all times. Utilizing a threat management system can significantly help as it detects and reports issues in real-time.
For more information, read our detailed knowledge base article on how to prevent brute force attacks or the cyber kill chain, which can help you understand and predict different stages of a cyberattack. Knowing how hackers work enables a company to select the right tools and strategies to limit breaches, respond to in-progress attacks, and minimize risks.



