A brute force attack is a simple hacking method where the attacker tries to guess a username and password to gain unauthorized access to a user account.
Once breached, the account can be used to launch larger attacks, steal sensitive data, or shut down systems.
Learn how to prevent brute force attacks using several basic techniques.

How to Identify Brute Force Attacks
Creating code for brute force attacks requires basic skills, and automated tools can submit thousands of password attempts per second. Attackers often use lists of real or common credentials to target websites.
A key indicator of a brute force attack is a sudden surge in failed login attempts. Watch for multiple failed login attempts and the use of various usernames originating from the same IP address. These unsuccessful attempts can be detected in your Apache access log or Linux log files, such as:
Sep 21 20:10:10 host proftpd[25197]: yourserver (usersip[usersip]) - USER theusername (Login failed): Incorrect password.Other signs include unrecognized IP addresses trying to log into a single account or unusual patterns in failed logins.
Note: Spam, malware, and phishing attacks often precede a brute force attack.
Brute Force Attack Prevention Techniques
A strong password policy is essential for countering brute force attacks, but there are additional practical methods to improve security without negatively impacting user experience (UX).
1. Implement Account Lockouts
Prevent brute-force attacks by locking out accounts after several unsuccessful login attempts. Legitimate users should be allowed to make mistakes, but you should limit the number of failed attempts to no more than 10.
Hackers may try to bypass lockouts by using a single password on many servers, leading to a potential denial-of-service (DoS) attack. If a server is under continuous attack, numerous user accounts could be locked out. To mitigate this, use progressive delays, where accounts are locked for a set time after multiple failed attempts. This approach reduces the effectiveness of brute-force tools and minimizes the need to unlock accounts manually.
Differentiate policies for administrator and regular user accounts. Administrator accounts must have stricter rules, while rules for customer accounts on, for example, ecommerce sites need to be more lenient to avoid frustrating users when they forget their passwords.
To ensure a smooth experience for website visitors, configure your system to disregard previous failed attempts once the user's credentials and IP address are verified.
2. Use CAPTCHA
CAPTCHA prevents software that imitates human behavior, typically deployed by bots or botnets, from accessing and using services intended for genuine human users. This tool requires users to enter a word or identify images to confirm they are human.
By adding this verification method, you can eliminate spam and block bots from overwhelming servers or using contact forms as a gateway to compromise core services. While effective, CAPTCHA is generally disliked by the online community.
However, recent developments, such as invisible CAPTCHA or behavioral analysis, can enhance security and reduce user inconvenience.

CAPTCHA remains very effective, and complements account lockouts well. If you implement CAPTCHA, consider lowering the number of failed login attempts before an account is locked.
3. Set up Two-Factor Authentication (2FA)
Two-factor authentication is a security system where users confirm their identity using two out of the following three methods:
- Something they know, such as a password.
- Something they have, like a code, one-time password, or token on their smartphone.
- Something they are, such as biometric data.
The most common combination is a password and a one-time password received on a personal device. 2FA is a strong defense against brute force attacks because, besides guessing a user's credentials, an attacker would need access to a second factor, such as a smartphone or email, to gain access. Persistent attackers might try to overcome that obstacle, but most will look for an easier target.

Note: Two-factor authentication is very effective against different types of cyber attacks, including keylogger attacks. Many security guidelines, such as PCI DSS and HIPAA, mandate the use of 2FA.
Companies should implement 2FA for their employees, especially for users with administrative access. Implementing 2FA for regular users depends on the business model and industry. Users of companies that deal with sensitive information or financial details might appreciate the additional security layer, while casual browsers can become frustrated with the additional step.
4. Edit sshd_config File
The sshd_config file defines which users can connect to a server remotely via SSH. Modifying rules in this file can prevent brute force attacks, especially those that target administrative and employee user accounts.
To access the sshd_config file, log in to the server's command line and open the file using a text editor. The following examples show how to edit the file using the Nano text editor on an Ubuntu 22.04 system.
Enter the following command to open the sshd_config file using Nano:
sudo nano /etc/ssh/sshd_configIn the sshd_config file, website owners can:
- Make the root user inaccessible via SSH.
- Change the default port number.
- Limit logins to specific IPs.
Make root User Inaccessible via SSH
Brute force attempts often target the root user as it gives attackers almost unlimited access to a remote system. Website owners must ensure that the root users on their servers cannot be accessed remotely.
To make the root user inaccessible via SSH:
1. Remove the # symbol at the beginning of the following line to uncomment it and set the PermitRootLogin value to no:
PermitRootLogin no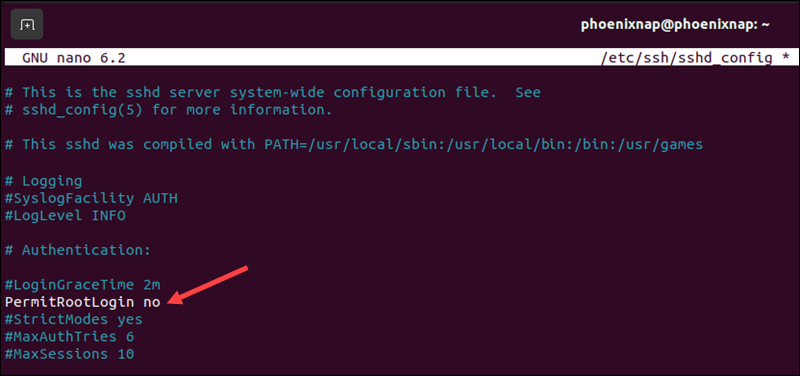
Note: Alternatively, you can enter PermitRootLogin prohibit-password to only allow root login with SSH keys.
2. Press Ctrl+X, then Y, and Enter to save the changes and exit the editor.
3. Restart the SSH service to apply the changes:
sudo systemctl restart sshdChange Default SSH Port
Most automated SSH attacks target the default port 22. Changing the SSH port can help mitigate brute-force attacks. To switch to a non-standard port:
1. Uncomment the sshd_config file line that specifies the port by removing the # symbol and change the port number to a non-standard port:
Port 6789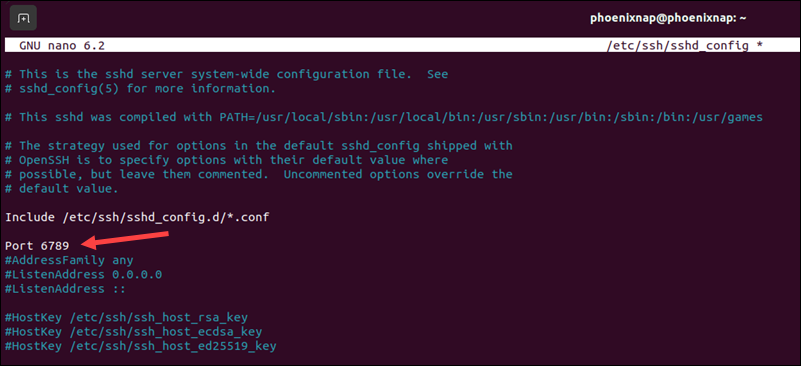
2. To save the changes and exit the editor, press Ctrl+X, followed by Y, and then Enter.
3. If a firewall is installed, allow traffic on the new SSH port. For example, if using the ufw firewall tool, enter the following commands:
sudo ufw allow 6789/tcpsudo ufw reload4. Apply the changes by restarting the SSH service:
sudo systemctl restart sshd5. To connect to the servers via SSH, specify the new port number:
ssh -p 6789 username@server_ipLimit Logins to a Specified IP Address or Range
Restricting access to a designated IP address or range makes it more difficult for brute-force attackers to gain access. Users who do not originate from the correct IP address are not allowed access.
1. To restrict access to a designated IP range, add the following line to the end of the sshd_config file:
AllowUsers [email protected].*2. Add the following line to allow access to a specific IP address:
AllowUsers [email protected]3. Press Ctrl + X, then Y, and Enter to save the changes and exit the editor.
4. Apply the changes by restarting the SSH service:
sudo systemctl restart sshd5. Use Unique Login URLs
Create a unique login URL for admins, such as /admin-login, and limit access to specific IPs to ensure that only authorized users can access this page. You can also create a /user-login subdomain with appropriate access controls for regular users.
This will not stop a brute force attack, but introducing this additional variable makes things a bit more challenging and time-consuming for an attacker. This method should always be used with other strong verification methods, such as 2FA.
Remember to update your web application routing to handle these unique URLs and inform users about the correct login URL.
6. Monitor Server Logs
The first step in prevention is identifying a brute force attack before it starts disrupting operations. Review logs regularly to isolate and respond to suspicious activity. Log management applications, such as Logwatch or Fail2ban, can help you perform daily check-ups, set up alerts, and generate daily reports.
If you are using a Ubuntu-based Linux system, enter the following command to install Logwatch from the command line:
sudo apt install logwatchYou can also set up the Logwatch service to send a daily report for the current day to the specified email:
sudo logwatch --detail high --mailto [email protected] --service all --range today7. Using Machine Learning Algorithms
Larger companies have already begun to use machine learning algorithms to detect different types of risks, including cyber attacks. These algorithms can learn from previous attack patterns and improve over time.
While implementing ML tools is currently out of reach for many smaller businesses due to cost, it is slowly becoming more affordable. Soon, even smaller websites will be able to leverage these advanced technologies to detect and block brute force attacks effectively.
8. Subscribe to IP Reputation Services
IP Reputation Services maintain databases of addresses associated with malicious activities and can block them preemptively. Website owners can configure their firewalls and security tools to block these identified IPs before an attack occurs.
Although attackers have adapted by mass-creating and using anonymized IP addresses, reducing the effectiveness of these services, IP reputation remains a crucial security layer when integrated into a broader security infrastructure.
Conclusion
Implementing the methods outlined in this article reduces the risk of becoming a victim of a brute-force attack.
Brute force attackers prefer easy targets and will likely move on to another target if you introduce effective cybersecurity practices.