The mod_evasive module is an Apache web server module that helps keep your server running in the event of an attack. A common type of cyber attack is a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack, or a brute-force attempt to overwhelm your security.
The nature of these attacks is to use several different computers to make repeated requests against your server. This causes the server to run out of processing power, memory, and network bandwidth and to become unresponsive.
This guide will walk you through configuring and installing mod_evasive to protect against DoS and DDoS.
Prerequisites
- The LAMP (Linux, Apache, MySQL, PHP) stack installed and configured.
- Access to a user account with sudo or root privileges.
- A functioning mail server (for email alerts).
How Does Apache mod_evasive Work
The mod_evasive Apache utility monitors incoming server requests. The tool also watches for suspicious activity from one IP, such as:
- Several requests for the same page in one second.
- More than 50 simultaneous requests per second.
- Requests made while the IP is temporarily blacklisted.
The module returns a 403 error if any of the above occurs. By default, this also includes a 10-second waiting period on the blacklist. If the IP address that made the request tries again within that 10-second window, the waiting time increases.
mod_evasive helps you defend against these kinds of attacks through network detection and management.
Note: Learn how to check for a DDoS attack on a Linux server.
Steps to Installing mod_evasive Apache Utility
Step 1: Install Apache Web Server Utility
Before installing the utility, update the package repository with the command for your Linux distribution:
Debian / Ubuntu:
sudo apt updateRedHat / CentOS:
sudo yum updateAllow the system to refresh and update your software listings.
Then, install a helper utility:
Debian / Ubuntu:
sudo apt install apache2-utils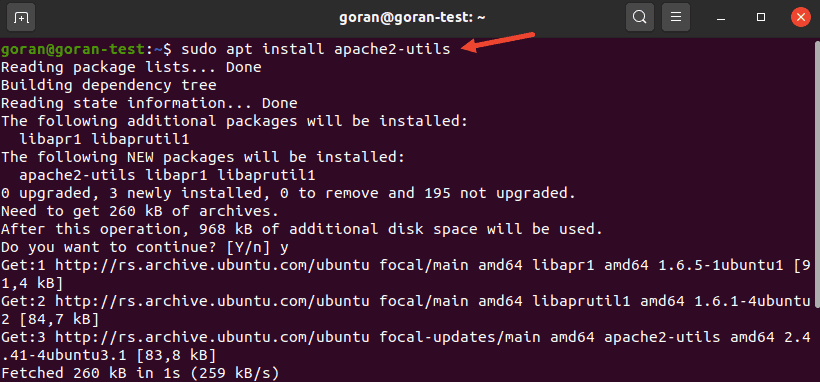
RedHat / CentOS:
sudo yum install httpd-develThe final section of the output looks like this:
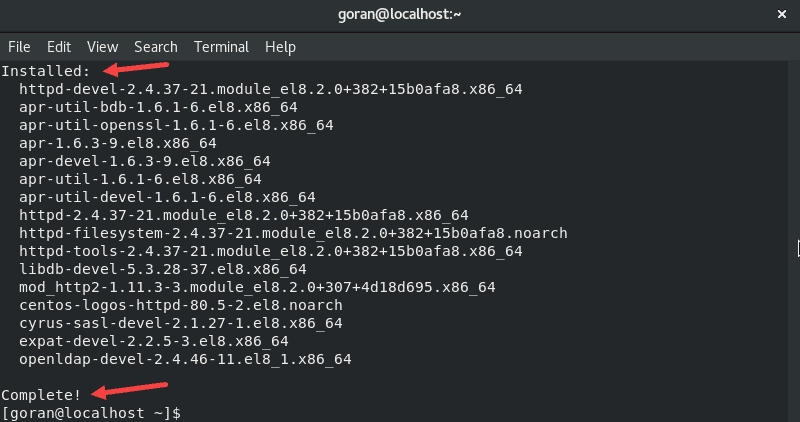
This utility is required for installing mod_evasive.
Step 2: Install mod_evasive
Debian / Ubuntu
To install the mod_evasive module on Debian / Ubuntu, enter the following:
sudo apt install libapache2-mod-evasive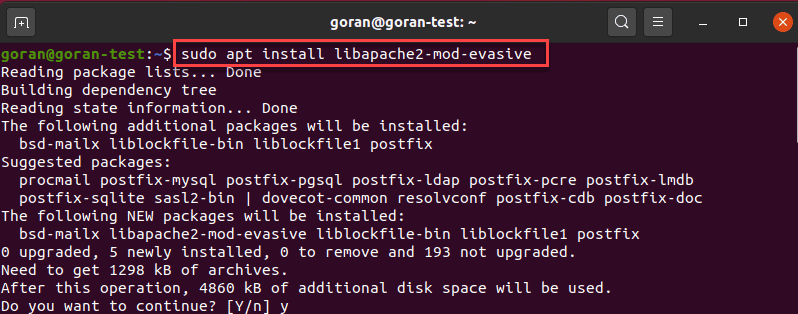
When you get a prompt, select Ok and choose your configuration.
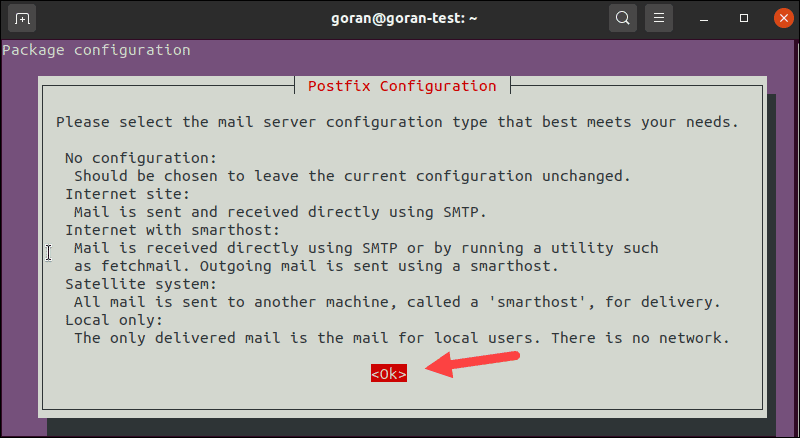
When unsure, select No configuration or Local only.
CentOS / RedHat
To install the mod_evasive module on RedHat / CentOS:
Add the EPEL repository:
sudo yum install epel-release
And then, enter:
sudo yum install mod_evasiveAllow the process to complete.
Step 3: Configure mod_evasive
Like most Linux software packages, mod_evasive is controlled by a configuration file. Make the following changes in the config file as the first step in preventing DDoS attacks:
1. Use a text editor of your choice with the following commands:
Debian / Ubuntu:
sudo nano /etc/apache2/mods-enabled/evasive.confRedHat / CentOS:
sudo nano /etc/httpd/conf.d/mod_evasive.conf2. Find the following entry:
#DOSEmailNotify [email protected]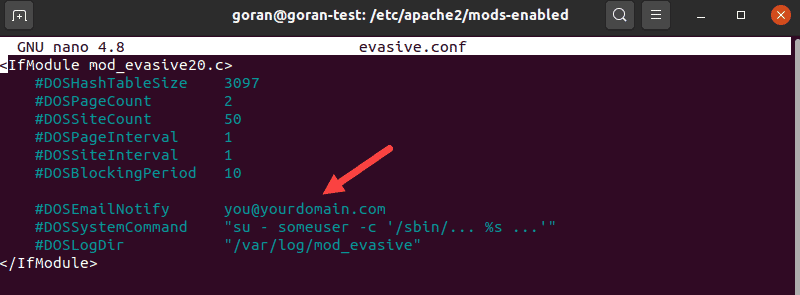
Remove the # sign, then replace [email protected] with your actual email address. Use an email that you check regularly – this is where the tool will send alerts.
3. Remove the comment tag from the following entries, so the log file looks as follows:
DOSHashTableSize 3097
DOSPageCount 2
DOSSiteCount 50
DOSPageInterval 1
DOSSiteInterval 1
DOSBlockingPeriod 10
DOSEmailNotify [email protected]
DOSLogDir "/var/log/apache2/"4. Save the file and exit. Reload the Apache service by entering the following:
Debian / Ubuntu:
sudo systemctl reload apache2RedHat / CentOS:
sudo systemctl restart httpd.serviceTest mod_evasive
Now, let’s verify the module is working correctly.
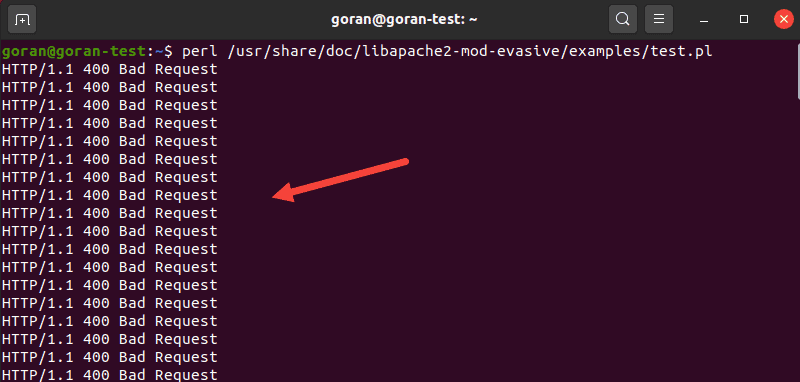
In this example, use the test.pl script to test mod_evasive.
The script is located at: /usr/share/doc/libapache2-mod-evasive/examples/test.pl.
Run the script with the following command:
perl /usr/share/doc/libapache2-mod-evasive/examples/test.plThe output should return an error message.
Parameters and Settings
There are many mod_evasive parameters you can configure:
DOSSystemCommand. Specify a system command to run when an IP address is added to the blacklist. You can use this to launch a command to add an IP address to a firewall or IP filter.DOSHashTableSize. Allocate space for running the lookup operations. Increasing the size improves the speed at the cost of memory.DOSPageCount. The number of requests for an individual page that triggers blacklisting. This is set to 2, which is low (and aggressive) – increase this value to reduce false-positives.DOSSiteCount. The total number of requests for the same site by the same IP address. By default, this is set to 50. You can increase it to 100 to reduce false positives.DOSPageInterval. Number of seconds forDOSPageCount. By default, this is set to 1 second. That means that if you don’t change it, requesting 2 pages in 1 second will temporarily blacklist an IP address.DOSSiteInterval. Similar toDOSPageInterval, this option specifies the number of seconds thatDOSSiteCountmonitors. By default, this is set to 1 second. That means that if a single IP address requests 50 resources on the same website in a single second, it will be temporarily blacklisted.DOSBlockingPeriod. The amount of time an IP address stays on the blacklist. Set to 10 seconds by default, you can change this to any value you like. Increase this value to keep blocked IP addresses in time-out for a more extended period.DOSLogDir. By default, this is set to write logs to /var/log/mod_evasive. These logs can be reviewed later to evaluate client behavior.
You can create a new directory to save these Apache access logs – make sure you change the owner to Apache, then update the location in this entry:
sudo mkdir /var/log/apache/mod_evasivesudo chown -R apache:apache /var/log/apache/mod_evasivesudo nano /etc/apache2/mods-enabled/evasive.confDOSLogDir "/var/log/apache/mod_evasive"Whitelisting IP addresses: This option isn’t included in the evasive.conf file by default.
Open the file again for editing, then add the following line:
DOSWhitelist 192.168.0.13
DOSWhitelist 192.168.0.*Substitute the IP address with the one you want to whitelist. Also, you should list only one entry per line. This is typically used with a trusted client that exchanges a lot of data with your website.
This tool is good at detecting bots and scripts. If there are bots or scripts that you want to allow, you can whitelist them to prevent these bots and scripts from triggering a blacklist action.
Make sure to save the file and exit. Then, reload your Apache service before testing any of these options.
Conclusion
Now you know how to install and configure mod_evasive on Apache.
Between its ease of configuration and its effectiveness, it has become a favorite tool for protecting Apache and Linux systems. For more information and the manual, please refer to the developer’s GitHub documentation page.