SELinux is a mandatory access control (MAC) enforcer built into the Linux kernel. It limits the privileges of individual services whose vulnerabilities might threaten the system.
Applications that do not comply with SELinux policies may encounter issues during installation or regular operations. As a last resort to troubleshoot or accommodate specific software requirements, you can consider temporarily disabling SELinux.
Find out how to disable SELinux on CentOS and Rocky Linux.

Prerequisites
- An RHEL-based system, like CentOS or Rocky Linux.
- Command-line access.
- Access to a user account with sudo privileges.
Steps for Disabling SELinux on CentOS and Rocky Linux
When SELinux (Security-Enhanced Linux) is disabled or unavailable, the security of a Linux system depends entirely on the correct configuration of all its privileged software applications. A single misconfiguration or vulnerability in a privileged application can potentially lead to a system-wide compromise.
Proceed with caution with the steps below to disable SELinux on CentOS and Rocky Linux.
Step 1: Check SELinux Status
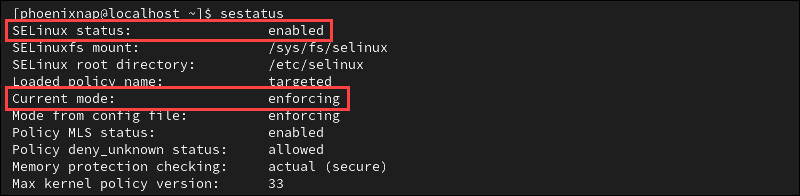
The SELinux service is enabled by default on most RHEL-based systems. To check the status of SELinux, enter the following command:
sestatusThe example output indicates that SELinux is enabled. The status shows the service is in the enforcing mode.
SELinux may prevent applications from functioning properly. The service denies access if:
- A file is mislabeled.
- An incompatible application attempts to access restricted files.
- A service is running under the incorrect security policy.
- The system detects an intrusion.
If services are not running correctly, check the SELinux log files. SELinux generates Access Vector Cache (AVC) messages if it needs to deny or audit an operation. AVC messages are logged in the /var/log/audit/audit.log file and labeled as type=AVC.
Note: If no audit logs are available, check the /var/log/messages file, which is used when the auditd daemon is not running.
Step 2: Disable SELinux
You can temporarily disable SELinux for troubleshooting (recommended), or permanently (discouraged unless absolutely necessary). The sections below cover both options.
Option 1: Disable SELinux Temporarily
Use the following command to disable SELinux temporarily:
sudo setenforce 0Alternatively, you can use the permissive keyword instead of 0:
sudo setenforce permissiveThe command does not provide an immediate output. Check the SELinux status to confirm the current mode:
sestatus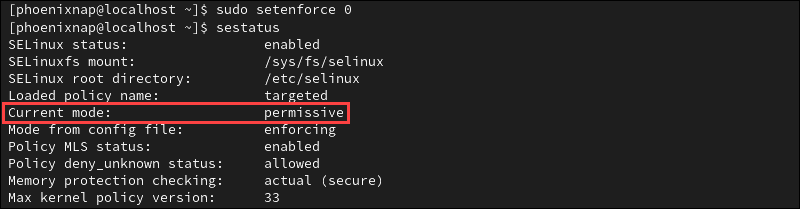
SELinux is now in permissive mode, meaning that the service is active, audits all actions, and logs AVC messages. However, it does not enforce security policies.
The change is active until the next reboot, when SELinux returns to its default mode.
Option 2: Disable SELinux Permanently
Warning: Switching to permissive mode is the preferred approach. Permanently disabling SELinux poses a risk to system security and is generally discouraged.
To disable SELinux permanently:
1. Open the /etc/sysconfig/selinux file using a text editor, for example, Nano:
sudo nano /etc/sysconfig/selinux2. Locate the SELINUX=enforcing directive in the file and change it to SELINUX=disabled.
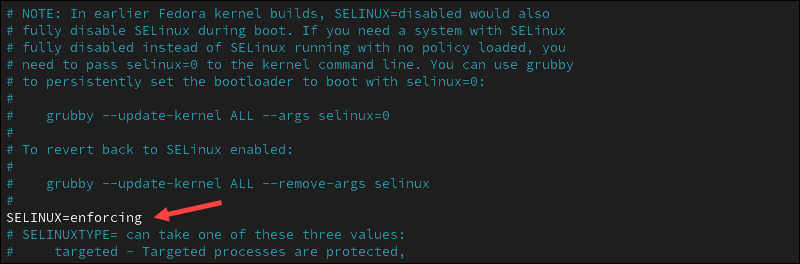
3. If using Nano, press Ctrl+X, Y, and then Enter to save the changes and exit the file.
4. For the change to take effect, reboot the system:
sudo shutdown -r now5. After the reboot, check the service status to confirm SELinux is disabled:
sestatus
The output confirms the SELinux service is disabled. From now on, the system will not load any SELinux policies or log AVC messages.
Conclusion
This guide showed how to check the SELinux status and disable the service on CentOS and Rocky Linux.
Security tools like SELinux or AppArmor are essential for enforcing strict security policies and conducting audits. They are a key component of best practices for managed server hosting.