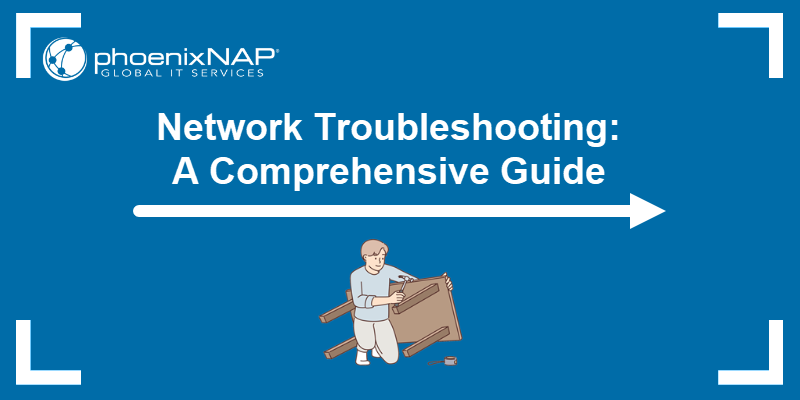
Before troubleshooting an issue, you need to know the cause, when it occurred, and whether it might happen again. Event logs store records of significant actions or incidents on the system, along with timestamps and event details. In Windows, these records are stored in the Windows Event Log.
In this guide, learn how to access and manage Windows Event Log entries to monitor system health and detect potential issues before they become problems.

What Is Windows Event Log?
The Windows Event Log is a built-in service that provides a chronological account of significant activities on a computer. It records events generated by the operating system, installed applications, and security processes.
Events are grouped into separate log types, and each event is assigned a severity level to indicate its urgency.
System and network administrators use the stored event details to pinpoint when an issue occurred, identify its cause, and take necessary action.
Windows Event Log Elements
Event logs can be viewed using the Event Viewer application. Each log entry contains the following data:
- Level. The severity of the event: Information, Warning, Error, Critical, Verbose.
- Date and Time. The date and time the event occurred.
- Source. The driver, software, or system component that caused the event.
- Event ID. A number that identifies the specific event type.
- Task Category. A classification defined by the event source to group related events.
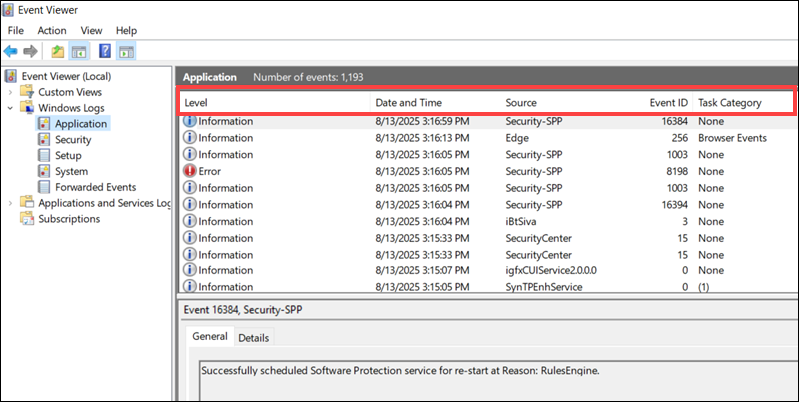
The lower pane of the Event Viewer displays a description of the event and additional information, including:
- Keywords. Tags that filter or classify events.
- User. The account under which the event occurred.
- Computer. The system where the event was logged.
- OpCode. Indicates the activity that triggered the event.
The Details tab allows you to view the event's raw data in:
- Friendly View. Structured, human-readable form.
- XML View. Raw XML data for programmatic access or automated analysis.
Windows Event Log Types
Events are recorded in several main log categories:
- Application. Logs events from software installed on the local computer. For example, if Microsoft Word fails to open a corrupted file, the Application log records the application name and error details.
- Security. Stores audit events based on the system's security policies. These include sign-in attempts and resource access. For example, event ID 4625 is logged when a user fails to sign in due to incorrect credentials.
- Setup. Contains events related to the Windows setup and installation process. In enterprise environments, this log can include domain controller setup or Windows feature installation records. For example, event ID 4902 is logged when the Windows Firewall settings are updated.
- System. Records events related to Windows system components, such as the status of device drivers or services. For example, event ID 7026 is logged when a device driver fails to load during startup.
- Forwarded Events. Collects events from other machines on the same network via event subscriptions. For example, multiple servers can forward security logs to an administrator's workstation for review.
Note: If you need to view and manage Windows Event Logs on remote machines, use the Remote Desktop Protocol (RDP) to perform the same actions through a graphical interface (GUI).
Windows Event Severity Levels
Each event is assigned a severity level to indicate its importance:
- Information. Logs with this entry indicate that the status is normal and the event occurred without incident. An example of a system-based information event is Event ID 6013, which reports system uptime.
- Verbose. A Verbose event might detail every step during a Windows update. It contains low-level information; however, it can be useful for troubleshooting and diagnostics in specific scenarios.
- Warning. There is a potential problem, and it may require your attention. For example, Event ID 51 is logged when Windows detects a potential delay in writing data to the disk.
- Error. This event indicates that an operation has failed, but the system can continue to function. For example, Event ID 7000 occurs when a Windows system fails to start. Some Error events require urgent attention, while others do not need to be addressed immediately.
- Critical. When a Critical event appears, it means that there is a serious problem that caused a major failure. For example, Event ID 1001 is logged when the system experiences a fatal error and creates a crash dump file.
Working With Event Logs in Windows
The Event Viewer application in Windows allows users to access, filter, and manage event logs from one central interface.
How to View Event Logs
To view event logs in Windows:
1. Press Windows+R to open the Run dialog.
2. Type eventvwr in the search box and press Enter.
3. In the Event Viewer, expand the Windows Logs menu from the left pane.
4. Select the log type you want to review, for example, Application.
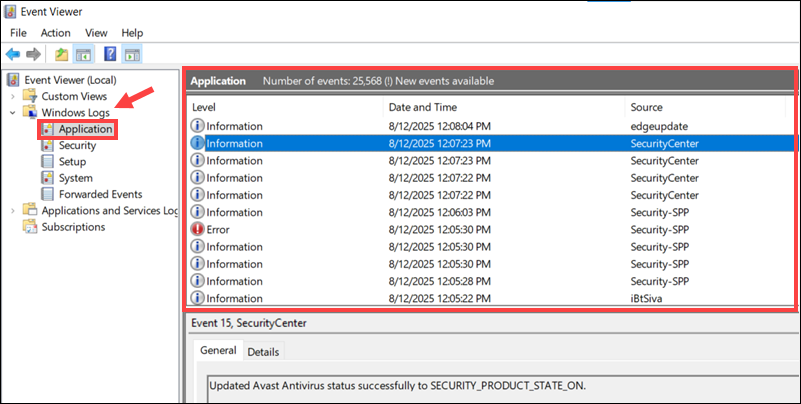
The events for the selected log appear in the middle pane.
How to Find and Filter Event Logs
Each log type can contain thousands of entries. To filter and find events in the Event Viewer:
1. Select the log you want to filter.
2. Click Filter Current Log on the right Actions pane.
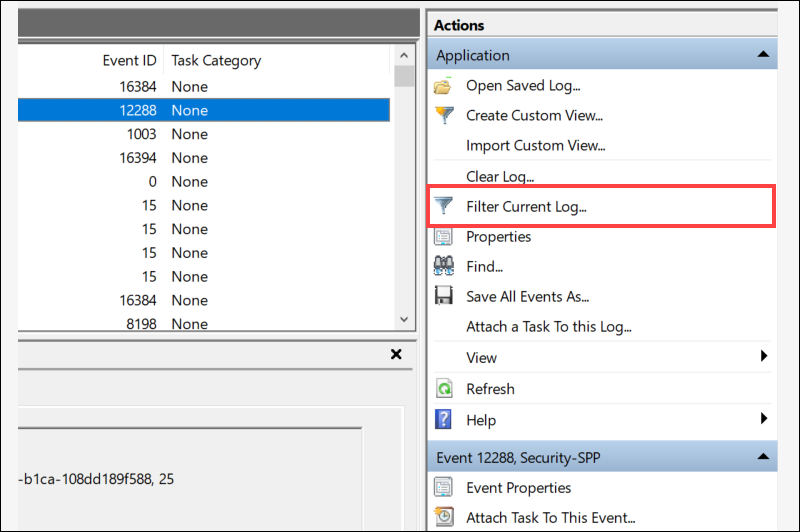
3. Narrow the results by defining one or more of the following filters:
- Logged. Select a time range from the dropdown menu.
- Event level. Check the box for the severity level to display. You can check multiple boxes if necessary.
- By log. Select the log type to filter.
- By source. Use this option to filter logs originating from specific drivers, apps, or providers.
- Event ID. Enter one or more Event IDs to filter.
- Keywords. Narrow the scope further by setting keywords.
- User. Limit events to a specific user.
- Computer(s). Show only events from specified machines.
4. Click OK to apply the filter.
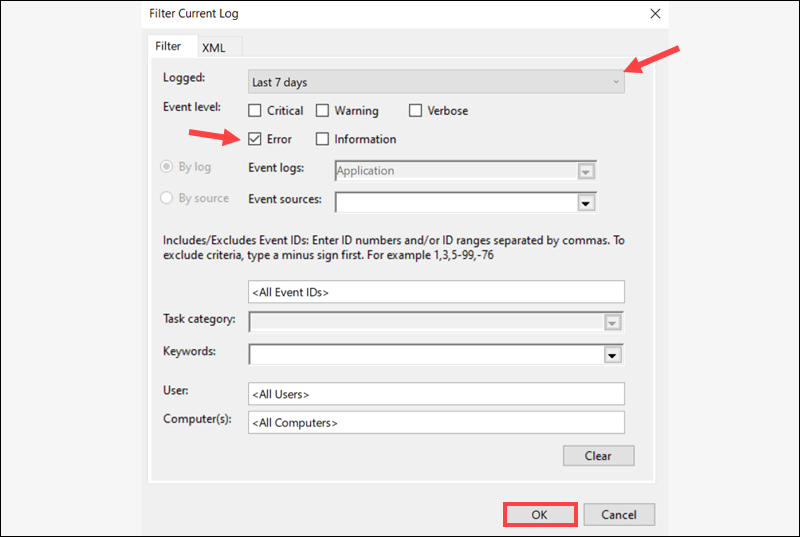
The main Event Viewer window will only display the events that match the selected criteria. Click Clear Filter to restore the full list.
How to Save Event Logs
You can save event logs to analyze them later or share them with other systems or users. All save options are in the Actions pane. Depending on the applied filters, you will have the option to:
- Save All Events As. Save every entry in the current log.
- Save Filtered Log File As. Only save entries matching the currently set filters.
- Save Selected Events. Save only highlighted entries.
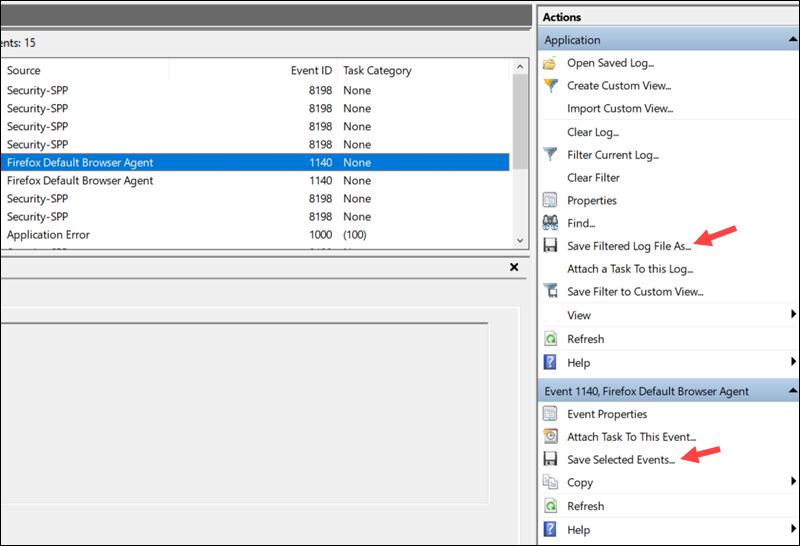
Logs are saved as .evtx files and can later be reopened in the Event Viewer. You can also export logs in formats such as .txt or .xml for use in scripts or analytics tools.
How to Clear Event Logs
To clear the events from the log:
1. Open the log you want to clear.
2. Click Clear Log in the Actions pane.
3. Choose Save and Clear to archive the entries first, or Clear to delete them immediately.
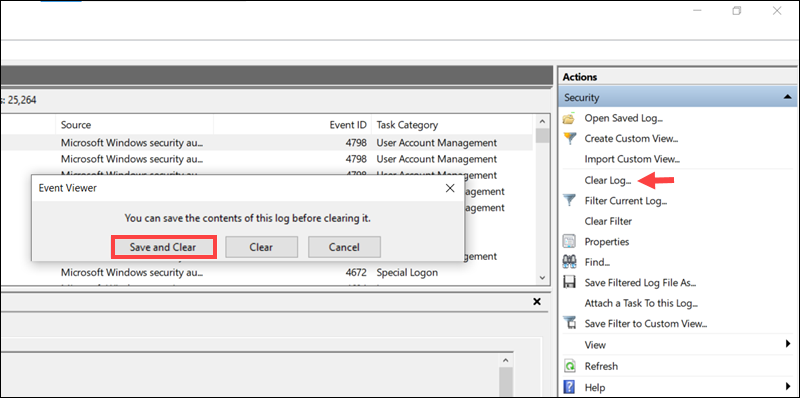
All entries in the log will be removed permanently and cannot be retrieved after clearing.
How to Attach Task to Event
To automate certain tasks, you can create a script that runs when a specific event occurs. To attach a scripted task to an event:
1. Right-click the event you want to use as a trigger.
2. Select Attach Task To This Event.
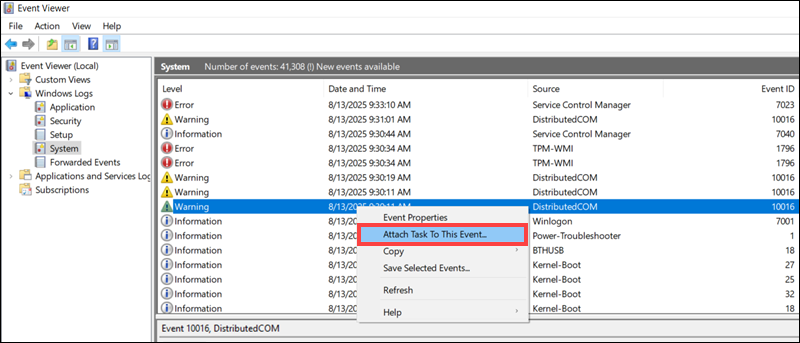
3. Follow the steps in the Create a Basic Task wizard.
4. Built-in actions for sending messages or emails have been deprecated in Windows 10 and 11. Use the Start a Program option to run a batch file, executable program, or PowerShell script.
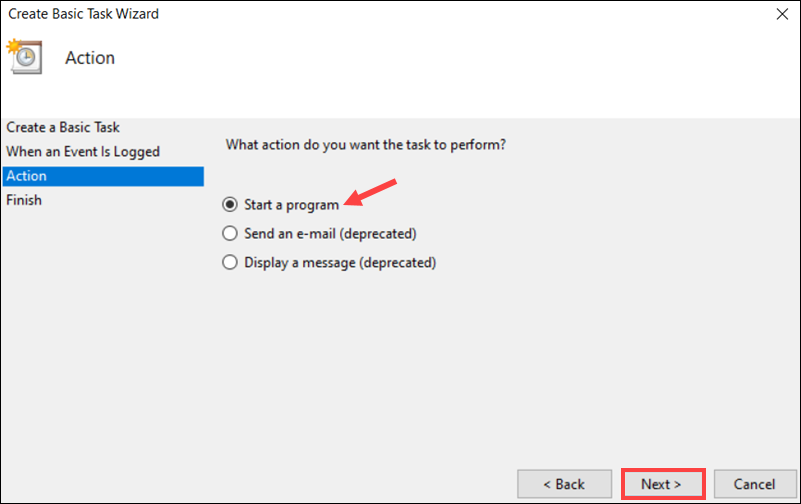
5. Enter the path to the script in the Program/script field and click Next.
6. Click Finish to save the event task schedule.
The script will now run automatically whenever the specific event ID with the configured parameters occurs.
How to Copy Event Details
To copy specific event details in a separate document:
1. Right-click the desired event.
2. Select Copy and then Copy Details as Text.
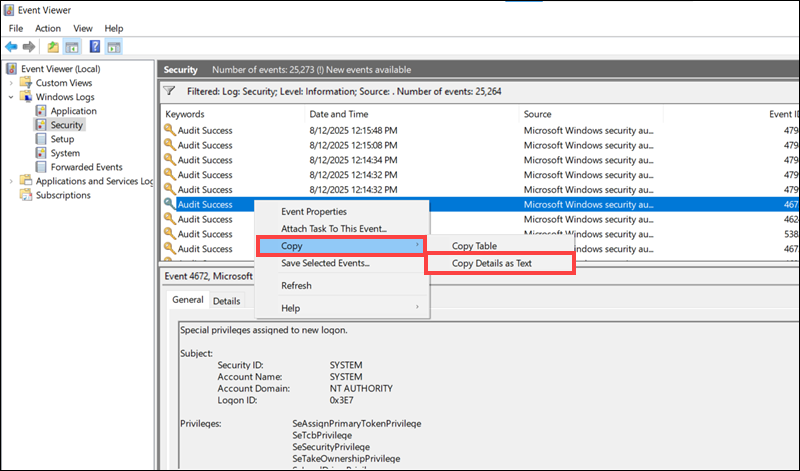
Paste the copied details into documentation, troubleshooting notes, or a support ticket.
How to Create Custom View
Use Custom Views to combine events from different logs into a single view or for advanced filtering. To create a custom view:
1. Right-click Custom Views and select Create Custom View…
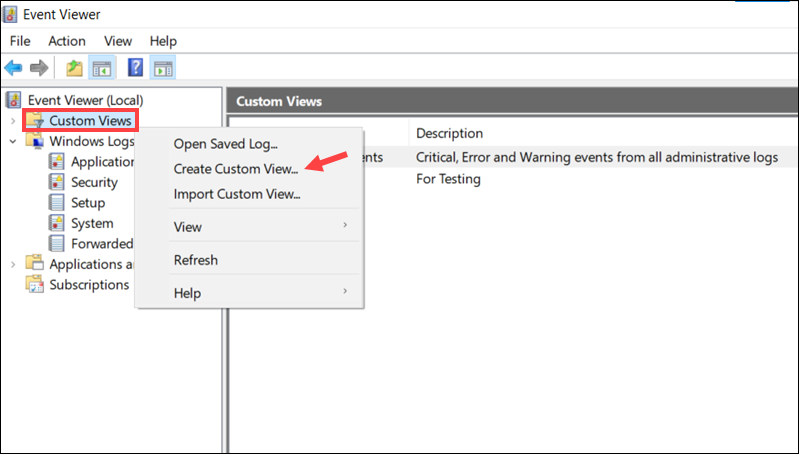
2. Apply filters:
- Logged. Select a time range from the dropdown menu.
- Event level. Check the box for the severity level to display. You can check multiple boxes if necessary.
- By log. Select the log type to filter.
- By source. Use this option to filter logs originating from specific drivers, apps, or providers.
- Event ID. Enter one or more Event IDs to filter.
- Keywords. Narrow the scope further by setting keywords.
- User. Limit events to a specific user.
- Computer(s). Show only events from specified machines.
3. Click OK.
4. Enter a name for the view, add a description, and choose where to save it under Custom Views.
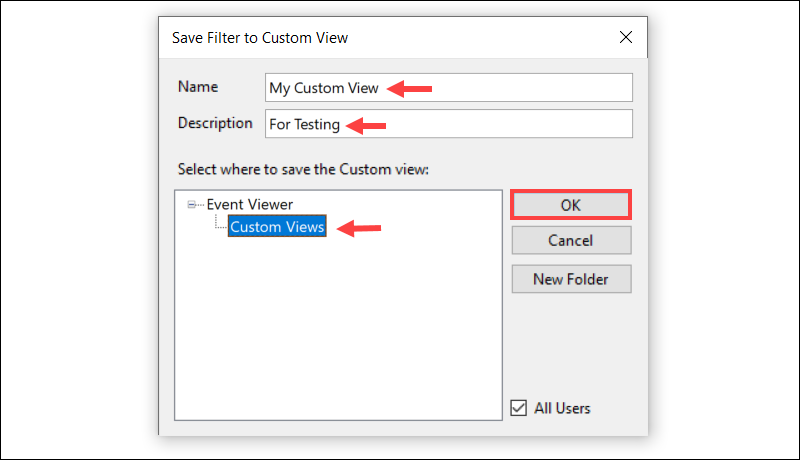
5. Click OK to save the custom view.
6. Select the new Custom View in the left pane to see matching events in the middle pane.
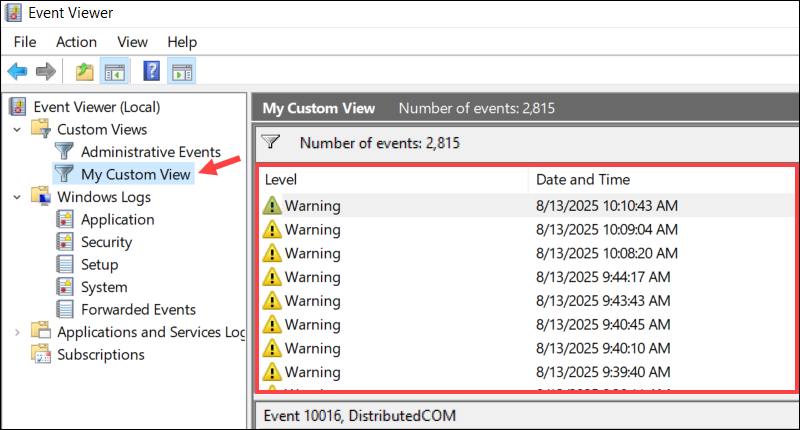
Custom Views are persistent, which means you can access them without reapplying the filters.
Best Practices for Windows Event Logs
To get the most out of Windows Event Logs, apply the following best practices:
- Use filters and custom views. To avoid scrolling through thousands of events, create reusable custom views that focus on specific event IDs, critical levels, or date ranges.
- Centralize log collection in networked environments. In distributed or enterprise environments, use a central log server to aggregate events from multiple machines. Centralized log management is more straightforward, and data is protected if a local machine is compromised.
- Monitor critical Event IDs. Set up automated alerts for critical event IDs like multiple failed login attempts (Event ID 4625) or NTFS corruption (Event ID 55). You can attach a task or script to these events and receive notifications in real time.
- Archive and clear logs. Event logs have size limits, and older entries are regularly overwritten once the limit is reached. Save and export important logs before clearing them to avoid losing important historical data. Store recent logs alongside other system backups so they are available during post-incident investigations.
- Restrict access to event logs. Event logs can contain sensitive user and device information. Only trusted administrators should have access to event logs.
- Set up audit policies. Not all policies are enabled by default. This means that some events do not get logged in Windows Event Logs. Ensure that the audit categories for the events you want to track are enabled and configured in Local Security Policy or Group Policy settings in Windows.
- Automate event tasks. Use PowerShell or similar tools to script repetitive tasks, like exporting and archiving logs, or filtering events. Besides saving time, automation can also improve data integrity.
- Event ID reference. Maintain a quick reference of event IDs or utilize an online resource to help staff identify events without needing to search repeatedly.
Benefits of Windows Event Logs
Advantages of using the Windows Event Log include:
- Centralized view. Event Viewer provides a single location to review important events originating from the operating system, applications, and security components.
- Troubleshooting and forensics. Log entries pinpoint the exact time and conditions of each event. They help identify the chain of events that led to an application crash, data breach attempts, or network interruption. Admins can use this information to fix urgent issues or analyze logs to detect long-term patterns.
- Security and compliance. Logs track user logins, failed authentication attempts, and privilege changes. The Windows Event Log supports compliance with HIPAA, PCI DSS, and ISO 27001 standards.
- Proactive maintenance. Severity level labels provide early warnings about low disk space, hardware problems, or resource usage spikes, giving you enough time to act before they escalate.
- Custom alerts. Users can set up automated scripts to trigger real-time alerts or actions when a specific event occurs.
- Support and vendor assistance. Event IDs and log files follow a consistent structure. Microsoft or software vendor support teams can understand your ticket instantly and resolve issues faster.
Conclusion
This tutorial showed you how Windows Event Logs work and how to use Event Viewer to review, filter, and customize log views or exports.
Next, explore these Syslog Servers to expand your system's monitoring and logging capabilities.