System Logging Protocol (syslog) has been a popular message logging method since the 1980s. The protocol's popularity stems from its simplicity and ease of transporting event log messages.
In this guide, you will learn about syslog and its related components, benefits, challenges, and best practices.

What Is syslog?
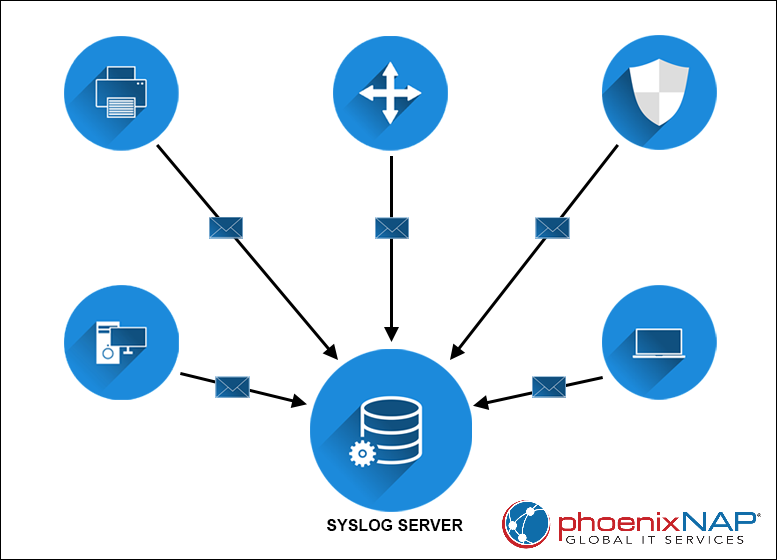
syslog is a UNIX protocol that facilitates information transfer, such as event data logs, from network devices to a central storage location, i.e., a syslog server. Although Windows does not provide native support for syslog, there are third-party tools for collecting event logs for Windows and transferring them to a syslog service.
The protocol uses a particular message format for its logs, which can then be analyzed by various types of software to perform audits, troubleshoot issues, monitor, and perform other key tasks.
The logging protocol is a crucial part of network monitoring since it helps users track the overall health of network devices.
There are three main components of the syslog system:
- The sender. The client app or system component that generates log messages.
- The receiver. The central server for storing log messages.
- The protocol. The format and structure of the transmitted log messages.
What Is a syslog Server?
A syslog server receives syslog messages and SNMP traps from syslog-enabled devices. After receiving the log data, the server processes, aggregates, and stores it for further analysis. Due to its centralized storage, users can easily search, filter, and view syslog messages.
Administrators use the syslog server to monitor network health, troubleshoot issues, and comply with audit requirements. The server consists of two components:
- Listener. The syslog listener gathers the event data and allows the server to start receiving messages.
- Database. Since the collector generates large data volumes, a large database is needed for fast read/write operations.
Most syslog servers have an intelligent alert feature that notifies the user about issues with log messages, and that way they prevent network downtime or failure. They also feature automatic message responses and can run scripts or forward messages.
Additionally, modern syslog servers often integrate with SIEM solutions, providing additional analytics and security insights.
How Does syslog Work?
Network devices use the syslog protocol to send event messages to a central logging server. These messages include timestamps, device IDs, IP addresses, event severity, and other event-specific information.
Most devices like routers and switches support syslog for recording events.
syslog uses a layered architecture that simplifies monitoring and management. The architecture consists of three layers:
- Transport layer. This layer sends messages over a network. It usually employs UDP on port 514 because of its speed and simplicity, even though UDP does not confirm delivery. Some devices use TCP (e.g., TCP 1468) for reliable message delivery. The transport layer ensures log messages travel from the source to the collection point.
- Application layer. Applications and system components generate and format log messages according to the syslog standard. This layer determines the content, severity, and metadata of each message. It also routes messages based on criteria such as facility and severity, preparing them for analysis and storage.
- Content/collection layer. The collection layer consists of syslog receivers or servers that listen for incoming messages. These receivers operate on ports such as UDP or TCP 514, and then store the logs in files, databases, or other storage systems. They also filter and route messages based on predefined criteria, generate alerts, and offer a centralized interface for administrators to analyze log data.
Essentially, syslog avoids complex device polling and relies on a continuous event data stream. Thus, it supports real-time monitoring, simplifies troubleshooting, and maintains system simplicity.
syslog vs. SNMP
syslog and SNMP serve different purposes in network management. SNMP (Simple Network Management Protocol) enables remote monitoring and control of SNMP-enabled devices, while syslog logs messages of varying severities across network devices that support syslog messages.
Unlike SNMP, syslog does not allow direct device remote control. SNMP provides in-depth network management and monitoring, while syslog is a simple logging tool for tracking and troubleshooting network events.
The following table outlines the key differences between SNMP and syslog:
| Feature | SNMP | syslog |
|---|---|---|
| Primary use | Remote monitoring and control of network devices. | Logging and alerting mechanism. |
| Message type | SNMP traps (real-time) and Get requests. | Log messages with severity levels. |
| Polling support | Yes. | No. |
| Security | SNMPv3 includes authentication and encryption. | No built-in security features. |
| Standardization | SNMP traps follow formal definitions in the MIB. | Messages follow a standard format but are not formally defined in an MIB. |
| Customization | Allows vendor-specific traps. | Messages follow a standardized format. |
| Delivery timing | Real-time delivery. | Messages can be queued, so they may not be delivered instantly. |
syslog Format and Messages
The syslog message format follows RFC 5424. It ensures faster communication between network devices and logging servers. Most network devices and applications use this standard format to exchange log messages.
A syslog message has three main components:
- Header. Contains details such as version, timestamp, hostname, application, process ID, message ID, and priority.
- Structured data. Holds data blocks formatted in a specific "key=value" order.
- Message. Encoded in UTF-8, it carries the actual event details. This part has no fixed format and provides flexibility to the log content.
The protocol calculates a priority (PRI) value by combining two elements:
- Facility. Identifies the message source (e.g., a value of 1 indicates a kernel-level message).
- Severity. Indicates the message urgency. The severity value ranges from 0 to 7. The following table details the severity levels:
| Severity value | Description |
|---|---|
| 0 | Emergency: System is unavailable for use. |
| 1 | Alert: Immediate action required for system stability. |
| 2 | Critical: Severe issues, such as primary ISP connection loss. |
| 3 | Error: System errors that need attention within a given time frame. |
| 4 | Warning: Potential issues if appropriate actions are not taken. |
| 5 | Notice: Stable system with a significant condition that persists. |
| 6 | Informational: General reporting and measurement messages. |
| 7 | Debugging: Application-specific debugging messages. |
The final message priority derives from combining Facility and Severity values.
syslog Benefits
There are numerous benefits of using syslog for your business. Some of them include:
- Improved security and data privacy. Centralized logging enhances security by providing a single point for log storage, and reduces the risk of manipulation or unauthorized changes.
- Easier monitoring and management. Consolidated log data simplifies tracking, speeds up anomaly detection, and offers real-time system visibility.
- Compatibility. Syslog works with nearly any device, regardless of the platform or operating system it uses.
- Scalability. A centralized approach efficiently manages large volumes of log data to ensure stability even under heavy workloads.
- Improved network performance. A standardized syslog collector simplifies log management, reduces review time, and aids in preventive troubleshooting.
- Enhanced security. Forwarding critical authentication events to a syslog server prevents attackers from erasing breach information from the original system.
- Advanced application monitoring. Detailed syslog entries provide granular insights into application behavior, such as errors during database writes or unauthorized file access.
syslog Challenges
Although syslog is a vital logging and monitoring tool, it also comes with several challenges. The protocol's design and widespread use can introduce issues with data volume, message reliability, security, and consistency that require careful planning and additional tools to overcome.
Some key challenges are:
- Data volume. High data volumes require robust infrastructure to prevent performance bottlenecks.
- Message delivery reliability. The common use of UDP means that messages may be lost, which risks missing critical events.
- Security concerns. Syslog lacks built-in encryption and authentication, which leaves log data vulnerable to interception and tampering.
- Inconsistent message formats. Despite RFC 5424 standards, the actual log content can vary widely, which can complicate correlation and log analysis.
- Integration and filtering complexity. Aggregating and filtering logs from diverse sources can be challenging, especially in large environments.
- Resource-intensive analysis. Parsing and storing massive amounts of unstructured data requires significant processing power and storage resources.
syslog Log Monitoring
Effective log monitoring is crucial for system health, security, and easier troubleshooting. Centralized syslog data provides a unified view of network events, which facilitates anomaly detection and identification of recurring issues. With comprehensive log monitoring, organizations can reduce downtime, meet compliance requirements, and improve network performance.
Use syslog log monitoring for:
- Issue detection. Quickly spot system errors or unusual activity before they escalate.
- Enhanced security. Identify and respond to security incidents by correlating logs from multiple sources.
- Operational efficiency. Streamline troubleshooting and reduce the time needed to isolate problems.
- Regulatory compliance. Maintain centralized logs to support audits and ensure adherence to data retention policies.
Some popular tools for syslog log monitoring are Graylog, Splunk, ELK stack, Kiwi syslog server, and others. The image below shows an example dashboard of the Graylog monitor:
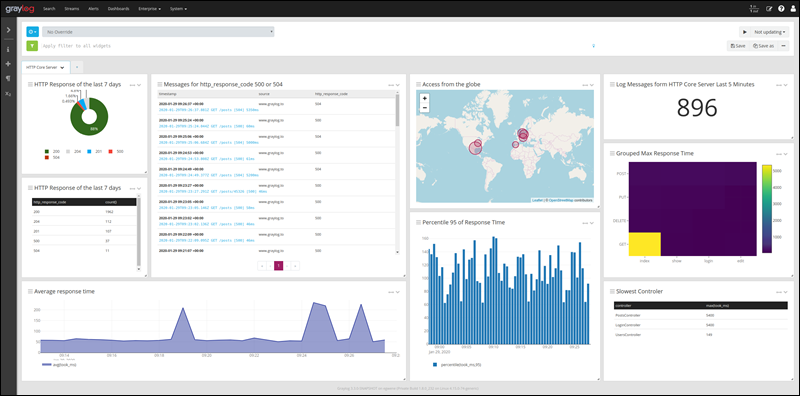
These tools enhance syslog's value by automating alerting, providing detailed analytics, and dashboards that simplify monitoring across complex network environments.
syslog: Best Practices
To ensure your syslog implementation remains efficient, adhere to the best practices, secure, and scalable. Follow standardized procedures and regularly review them to enhance reliability, protect sensitive data, and optimize performance.
Some key syslog best practices are:
- Centralize log collection. Use a dedicated syslog server to gather logs from all devices.
- Secure log transmission. Implement TLS or VPN to encrypt log data in transit.
- Standardize log formats. Maintain consistent log formats to simplify analysis and correlation.
- Implement filtering. Apply filters to reduce noise and focus on important events.
- Regular archiving. Archive logs systematically to support compliance and forensic analysis.
- Monitor performance. Continuously assess log processing performance to identify and resolve bottlenecks.
- Automate alerts. Set up automated alerts for prompt response to anomalies.
- Review policies regularly. Update logging policies to address new threats and changing environments.
Conclusion
This guide provided a comprehensive syslog explanation with a focus on its components, benefits, challenges, and best practices. Use the best practices outlined to optimize your logging strategy and improve network security.
Next, check out our list of best syslog servers or learn to view and read Linux log files.