Passwords are the first line of defense against unauthorized access, shielding the data that drives business operations and protects user privacy. They are essential for any database system to enforce strong, unique, and regularly rotated credentials to thwart breaches and maintain trust.
In PostgreSQL, setting and routinely updating the superuser's password is the key step that secures the entire cluster from intruders.
In this tutorial, you will learn to view, set, and change the default password in PostgreSQL.
Prerequisites
- PostgreSQL installed (see how to install it on Windows or Ubuntu).
- An account with administrator privileges.
Does PostgreSQL Have Default Password?
PostgreSQL does not ship with a default password for security reasons. During installation, it creates a special database superuser account named postgres, but the account starts without a password. On many systems, local access to this account is controlled by operating system authentication (e.g., peer authentication on Linux), which means only the system user postgres can connect without a password.
This approach prevents the risk of attackers exploiting a well-known default password, ensuring that the database is only accessible after you define your own secure credentials. If you plan to allow remote connections or switch to password-based authentication, manually set a password for the postgres role, as explained in the next section.
How to Set PostgreSQL Password?
You can set or change a PostgreSQL password in several ways, depending on whether you are logged in locally or remotely, and which authentication method is in use. The most common method is to use the psql command-line tool.
Follow the steps below to set the PostgreSQL password:
1. Log in to PostgreSQL as the postgres superuser:
On Linux:
sudo -u postgres psqlOn Windows (if psql is in PATH):
psql -U postgresNote: If psql is not in PATH on Windows, you must navigate to bin or use the full path to the executable file.
2. Set a new password. In the psql prompt, use the following syntax:
ALTER USER postgres PASSWORD 'your_secure_password' VALID UNTIL '2025-12-31';- Replace
your_secure_passwordwith the password you want to set for the user. You can use our free password generator to instantly generate a secure, random password. - Replace
2025-12-31with the expiration date for your password. Use this parameter if you want to ensure the credentials are valid only until a certain point, after which a new password has to be set. However,VALID UNTILapplies only to password-based authentication methods (e.g., md5, scram-sha-256) and is ignored for peer or trust authentication.
Note: ALTER ROLE is interchangeable with ALTER USER, and is becoming more and more used in current docs.
3. Exit psql with:
\q4. Optionally, to require a password for all connections, edit the pg_hba.conf file to use md5 or scram-sha-256 authentication instead of trust or peer, then restart PostgreSQL.
This ensures your PostgreSQL instance is protected with a strong, unique password, especially before enabling remote access.
Note: PostgreSQL 14+ defaults to scram-sha-256 if password_encryption is set accordingly.
How to Reset PostgreSQL Password?
Resetting the PostgreSQL password works much like setting it, but the steps depend on whether you can still log in as a PostgreSQL superuser.
If you know your password:
1. Log in to psql with:
sudo -u postgres psql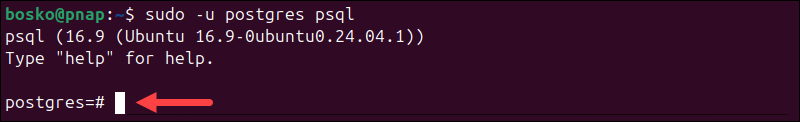
2. Change the password with the following command:
ALTER USER postgres PASSWORD 'new_secure_password';Replace your_secure_password with a new password you want to set for the user.
3. Quit psql:
\qIf you forgot your password:
You will need local OS access to the server where PostgreSQL is running. Follow the steps below:
1. Switch to the postgres system user.
On Linux:
sudo -u postgres psqlOn Windows:
Run psql from a terminal with admin rights, and specify the database name if needed:
psql -U postgres -d postgresIf password authentication blocks you, you must temporarily change the authentication method.
2. Edit the pg_hba.conf file with a command-line text editor.
On Linux, it is commonly found at:
- In Debian, Ubuntu:
sudo nano /etc/postgresql/<version>/main/pg_hba.conf- RHEL-based:
/var/lib/pgsql/<version>/data/pg_hba.confFor example:
And on Windows it is usually:
C:\Program Files\PostgreSQL\<version>\data\pg_hba.confFind the lines controlling local connections, for example:
local all postgres peer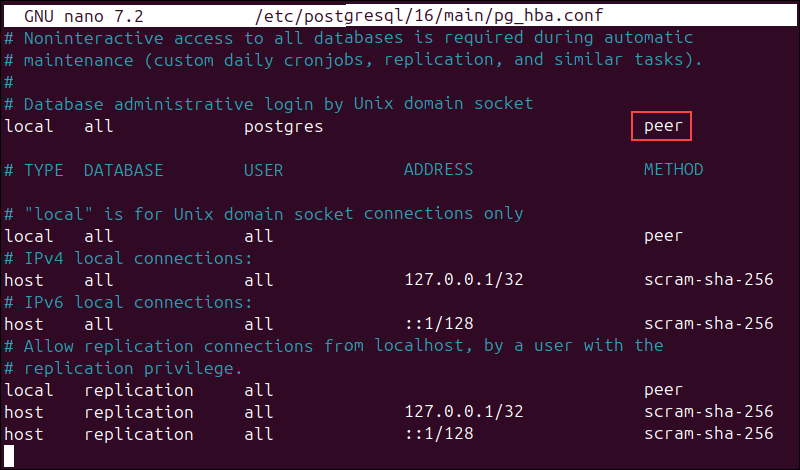
Change peer or md5 to trust so PostgreSQL does not ask for a password locally:
local all postgres trust3. Restart PostgreSQL for the changes to take effect:
On Linux:
sudo systemctl restart postgresqlOn Windows:
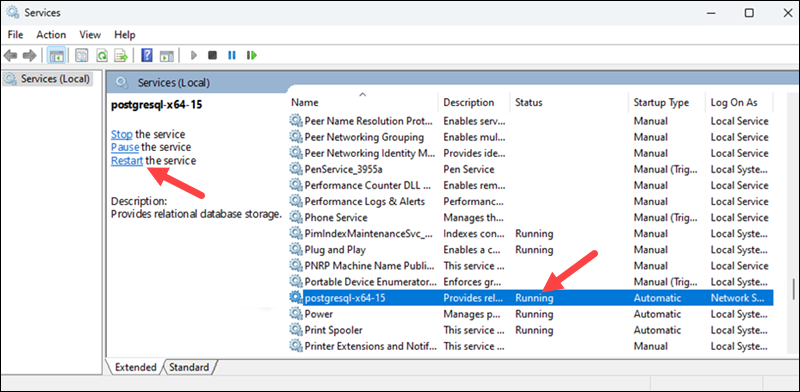
Restart the PostgreSQL service from the Services app. Press the Windows button and search for services. Open the app, find the PostgreSQL service in the list, and select the Restart option:
4. Log in and reset the password:
sudo -u postgres psqlALTER USER postgres PASSWORD 'new_secure_password';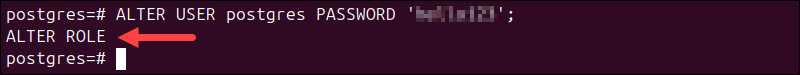
Important: Switching to trust is temporary and should be reverted immediately after you change the password to avoid allowing anyone with local or network access to log in as the superuser.
PostgreSQL Password Management Best Practices
Following password best practices in PostgreSQL helps maintain a strong security posture and reduces the risk of unauthorized access. These guidelines ensure that passwords are not only strong at creation but also properly protected, rotated, and supported by secure authentication methods.
The best practices in PostgreSQL password management are:
- Set a strong password immediately. Use at least 12-16 characters with a mix of uppercase, lowercase, numbers, and symbols.
- Use scram-sha-256 authentication. It offers stronger password hashing than the older md5 method.
- Rotate passwords regularly. Change passwords periodically and after any suspected compromise.
- Restrict remote access. Only trusted IPs should have remote access, configured via pg_hba.conf and firewall rules.
- Disable or rename unused superuser accounts. Doing so reduces potential attack surfaces.
- Store passwords securely. Use a password manager instead of saving passwords in plaintext files or scripts.
- Use least-privilege accounts. Create separate roles with only the permissions needed for each task.
- Audit login attempts. Check PostgreSQL logs for unusual or failed login activity.
- Enforce password expiration. Use the
VALID UNTILoption to require periodic changes. - Verify authentication changes. Test connections after updates to ensure security settings work as intended.
Conclusion
This article showed how to change or set the default PostgreSQL password to improve your database security significantly. Set a strong password for the PostgreSQL superuser to prevent unauthorized access and protect your database from potential breaches.
Next, learn about the PostgreSQL SELECT STATEMENT or see how to deploy PostgreSQL on Kubernetes.