In the early days of cybercrime, hackers primarily ran smash-and-grab attacks that did as much damage as possible in one strike. Today, malicious actors prefer a stealthier approach.
After gaining initial access to a target system, a modern hacker typically tries to stealthily move through the network in search of anything of value (databases, devices, other hosts, etc.). This lateral movement enables an intruder to make the attack as devastating as possible.
This article provides an introduction to lateral movement and the various techniques attackers employ to penetrate compromised systems further. Jump in to learn how lateral movement works and see the most effective ways to prevent intruders from moving freely within your networks.
What Is Lateral Movement?
Lateral movement is the act of moving horizontally through a network after establishing an initial entry point into the system. Threat actors use lateral movement to progressively navigate a compromised network, searching for data and assets worth stealing or damaging.
Lateral movement is a significant cybersecurity concern because it enables intruders to expand their attack reach. All lateral movement usually follows the same pattern:
- Attackers gain initial access to the network (e.g., by compromising an endpoint with malware or cracking someone's credentials).
- Attackers move from the compromised system to other parts of the network operating at the same privilege level.
- Intruders stealthily establish a foothold within the system.
- The intruder expands the foothold and compromises more hosts, applications, or devices.
There are various reasons attackers decide to move laterally through a network, such as:
- Privilege escalation. The threat actor might attempt to elevate their privileges on the initially compromised system.
- Attack expansion. The intruder might use the compromised system as a pivot point to attack other systems within the network.
- Persistence. Intruders may move laterally to establish backdoors and maintain persistent access to the network. That way, attackers get to continue their activity even if the victim discovers and closes the initial entry point.
- Data theft. Once inside the network, attackers often move laterally to find and compromise databases that store valuable data.
- Bypassing security measures. Lateral movement is the go-to tactic when an attacker wants to bypass security controls present at the current part of the network.
Lateral movement is a manual process conducted by a hacker. However, some malicious software (e.g., a worm or ransomware) has the capability to move laterally through a network without human guidance.
Learn about the basics of network security and see what it takes to keep a network safe from threats.
Lateral Movement Techniques
Attackers rely on various techniques to move through a compromised network. Here are the most common tactics:
- Credential theft. Attackers steal login credentials from one system and then use them to log in to other parts of the network.
- Exploiting vulnerabilities. Exploiting system flaws (e.g., misconfigured access controls or weak authentication) to move between network segments and resources.
- Pass-the-Ticket (PtT). PtT is a lateral movement technique in which an attacker steals Kerberos tokens to gain unauthorized access to network resources.
- Pass-the-Hash (PtH). PtH is a technique in which an attacker captures a password hash from one system and then passes it through for authentication to other network parts.
- Overpass-the-Hash (or Pass-the-Key). If the compromised network relies on public key infrastructure (PKI), an attacker might try to steal private keys and use them to authenticate to other systems.
- Brute force attacks. A brute force attack occurs when an attacker uses a bot to try various character combinations until it cracks a password.
- Hijacking user sessions. Hijacking an active user session or stealing session tokens is sometimes enough to access other systems.
- Exploiting trust relationships. Intruders often abuse trust relationships between systems to move laterally. Common tactics include taking advantage of shared services or compromising a domain controller.
- Living-off-the-land techniques. An attacker uses existing system tools and scripts (e.g., PowerShell or Windows Management Instrumentation (WMI)) to perform lateral movement.
Most lateral movement techniques are fileless, which is why traditional security controls ususally have difficulty detecting an intruder or a piece of code moving within a network.
Lateral Movement Stages
Lateral movement typically occurs in three stages once an attacker gains the initial foothold within the network. Let's take a closer look at each stage of a typical lateral movement attempt.

Network Reconnaissance
The first thing on the intruder's to-do list is network reconnaissance. The goal is to gather info about the target network, its assets, configurations, and potential vulnerabilities.
Here's a look at what hackers do during the reconnaissance stage:
- Analyze the network's defenses and identify security measures (e.g., firewalls, intrusion detection systems (IDSes), antivirus solutions, etc.).
- Use various techniques (e.g., scanning IP ranges, pinging hosts, using network mapping software, etc.) to map the network's layout.
- Understand host naming conventions and network hierarchies.
- Determine what operating systems run on discovered systems.
- Identify IP addresses, open ports, and services running on mapped devices.
- Look for shared folders, network shares, and resources accessible within the network.
- Use various techniques (e.g., querying the domain controller or exploiting poorly configured directory services) to identify usernames on the network.
- Use vulnerability scanning tools to identify flaws in network services, OSes, and apps.
- Gather info about network users and their roles from public sources, social media, email footers, or via social engineering.
The info gathered during this stage is essential for planning and executing the subsequent stages of lateral movement.
Privilege Escalation
Privilege escalation occurs when an intruder attempts to increase their level of access or permissions within a compromised system. Escalated privileges mean the attacker has more options for horizontal movement within the network.
The most common method of escalating privileges is to gain access to an account with admin rights. Attackers usually achieve this via credential harvesting. Go-to tactics for stealing usernames and passwords include:
- Phishing emails or websites that trick users into revealing login credentials.
- Keyloggers are used to record keystrokes on compromised systems.
- Brute force attacks that use a bot to guess usernames and passwords.
- Password spray attacks that use a few commonly used passwords against many usernames.
If simple credential harvesting is not an option, hackers typically turn to one of the following tactics:
- Exploiting misconfigurations to execute code with higher privileges.
- Extracting stored credentials from memory, databases, or config files.
- Using packet-sniffing tools to capture login credentials as they traverse the network in plain text or weakly encrypted forms.
Intruders also often look for apps with flaws that allow them to escalate privileges. In that case, attackers use one of the following tactics:
- Utilize SQL injections to exploit vulnerabilities and gain admin access to databases, potentially compromising the entire app.
- Exploit buffer overflow vulnerabilities to execute arbitrary code with elevated privileges.
More skilled hackers know how to remain completely undetected during this stage. Threat actors avoid actions that trigger an alert, such as making too many failed login attempts or causing unusual traffic patterns.
Moving Laterally Through Network
Once an attacker has analyzed the network and elevated enough privileges, it's time to move laterally and expand the foothold. This stage has one of two goals:
- Reach a specific part of the network that hosts the target system or database.
- Expand across the network and infect as many resources as possible.
Intruders use various techniques to move laterally, as explained earlier in the text. Once in a new segment of a network, attackers do one or more of the following:
- Set up persistence mechanisms (such as backdoors or scheduled tasks) to ensure they can return to the network even if the initial entry point disappears.
- Copy, exfiltrate, or manipulate files.
- Look for further opportunities for lateral movement.
Intruders go to great lengths to evade detection during lateral movement. Here are the usual evasion tactics:
- Deleting or modifying log files (security logs, event logs, system logs, etc.) to remove evidence of malicious actions.
- Altering timestamps on files, system events, or log entries.
- Removing any tools or malware used during the attack.
- Blending activities in with regular network traffic.
- Encrypting communication channels.
- Concealing backdoors and other persistence mechanisms.
On average, organizations take 212 days to identify a cyber intrusion, which shows just how skilled modern hackers are at concealing their presence within a network.

Which Attacks Use Lateral Movement?
Various cyberattacks rely on lateral movement to achieve objectives within the target network. Here are some notable attack types that often involve lateral movement:
- Distributed Denial of Service (DDoS). DDoS attackers often use lateral movement to reach more systems and create a more powerful botnet.
- Ransomware. After delivering ransomware to a system, most attackers try to move laterally to spread malware to as many systems and databases as possible.
- Advanced Persistent Threats (APTs). APT groups use lateral movement to expand their reach within the network. The two most common goals of APT attacks are espionage and data exfiltration.
- Worms. A worm is a self-replicating type of malware that automatically spreads between systems. Worms move laterally by exploiting vulnerabilities or using stolen credentials.
- Data breaches. Data breaches typically begin at a compromised endpoint and end with the attacker reaching the database server.
- Insider threats. Many insider threat scenarios involve an employee attempting to move laterally through the network. In most cases, malicious insiders try to reach resources or data they wouldn't normally have permission to access.
Our guide to different types of cyberattacks takes you through the most common tactics criminals use to infiltrate and damage target systems.
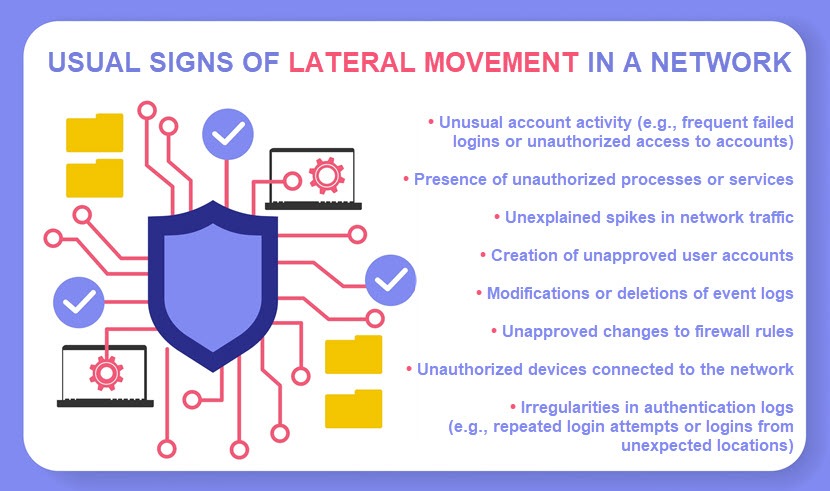
How to Detect Lateral Movement?
Here are some effective practices that enable you to detect an intruder's attempt to move laterally within your network:
- Continuously monitor east-west (lateral) traffic for unusual or unexpected patterns.
- Keep an eye out for port scanning.
- Monitor the network for changes from normal behavior (e.g., suspicious access requests or strange admin account activity).
- Analyze user behavior for anomalies, such as unusual login times or access requests from illogical locations.
- Monitor for signs of privilege escalation, such as the creation of new admin accounts or unexpected changes in user roles.
- Pay attention to high volumes of data transfers between internal systems, a tell-tale sign of someone covering up lateral movement.
- Track whether profiles and accounts access unfamiliar resources or systems.
- Monitor failed login attempts and connections to uncommon ports or protocols.
- Collect and analyze log files from various network devices, servers, and apps.
- Supervise Active Directory (AD) activities for signs of lateral movement, such as unusual account creation or group membership changes.
- Detect suspicious activities on endpoints, such as unauthorized process execution or file modifications.
In 2022, the average breakout time (how long an intruder takes to begin moving laterally from a compromised host) was 1 hour and 38 minutes. If it takes longer to detect an intruder, you run the risk of the malicious actor moving deeper into your network.
How to Prevent Lateral Movement?
Preventing lateral movement requires a mix of technical precautions, user awareness, and network monitoring. Here are the most effective ways to prevent lateral movement:
- Use network segmentation to divide your system into isolated zones with separate access controls. Only allow necessary communications between segments.
- Implement the principle of least privilege (PoLP) to ensure users and systems have only the minimum level of access required to perform their tasks.
- Remove unnecessary services, protocols, and apps from the network to reduce the attack surface.
- Keep all software up to date with the latest security patches.
- Use zero-trust security to ensure the network thoroughly checks every access request.
- Implement multi-factor authentication (MFA) and strong password policies.
- Boost endpoint security with anti-malware software, endpoint detection and response (EDR) capabilities, and app whitelisting.
- Set up intrusion detection and prevention systems (IDS and IPS) to detect and block suspicious network activity.
- Set a baseline for user and system behavior with a UEBA (User Entity and Behavior Analytics) tool. Then, set alerts for any deviations from normal behavior.
- Set up alerts for unauthorized access attempts and suspicious changes to access permissions.
- Use an automated tool to track privilege changes and send alerts whenever there's an unauthorized or unexpected modification.
- Organize security awareness training to ensure your employees know how to recognize social engineering tactics.
- Use web filtering to prevent employees from accessing malicious websites.
- Boost email security with a filtering tool that blocks malicious attachments and URLs.
- Conduct regular vulnerability assessments to identify flaws before attackers have a chance to exploit them.
Our article on network security tools presents 34 different solutions you can use to prevent malicious activity on your network.
Stopping Lateral Movement Must Be at the Top of Your Security To-Do List
A lack of anti-lateral movement precautions means a single infected endpoint is enough for an intruder to compromise everything of value on the network. Use what you learned in this article to ensure attackers cannot easily find valuable data or compromise additional systems even if they slip past your defenses.