A Windows Server domain is a logical grouping of networked computers with shared security policies and the same user account database. A domain controller (DC) centralizes and authenticates all access requests to network resources within the same domain.
A DC is crucial to network security as it stores all the data for validating access to network assets. DC servers are effective gatekeepers for domain-bound resources, plus they give access to Microsoft's Active Directory Domain Services (AD DS).
This article takes you through everything you need to know about domain controllers. Learn how domain controllers work and how DC servers help maintain a high cybersecurity posture.

What Is a Domain Controller?
A domain controller is a server that verifies user identities and authorizes access to IT resources within a network domain. DC servers authenticate users, store account info, and enforce domain-based security policies.
Domain controllers are most commonly used in Windows Active Directory domains. However, there are ways to establish a DC in non-Windows systems, usually via Identity and Access Management (IAM) software. The most common example is using Samba to create a Linux-based domain controller.
The primary function of a domain controller is to grant access to domain-based resources (systems, applications, file storage systems, etc.), but DCs have a few more capabilities. Here's a closer look at a DC's main functions:
- Authentication. The DC verifies the identity of users and computers attempting to access domain-based resources.
- Authorization. Once authenticated, the DC determines the level of access the user or computer has within the domain.
- Account management. DCs handle the creation, modification, and deletion of user and computer accounts within the AD domain.
- Policy enforcement. DCs enable admins to enforce domain-relevant security protocols and rules. Common examples are requirements for strong passwords, banned websites, and account lockout policies.
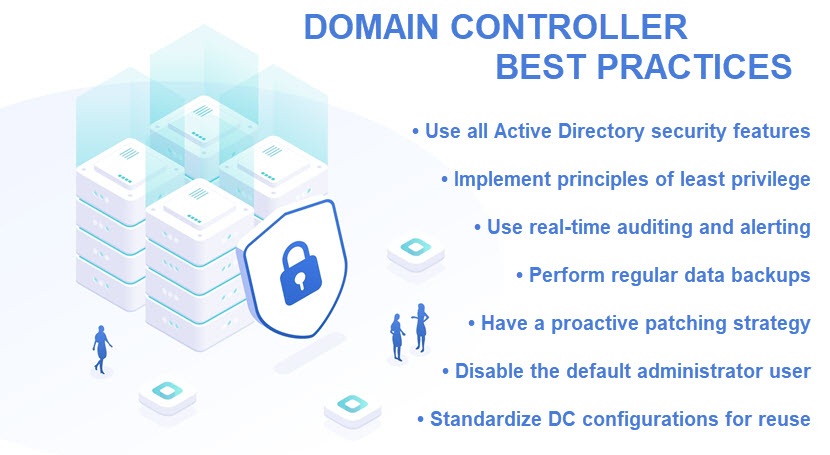
All network access requests must go through the domain controller, so protecting the DC server is vital. Here are the go-to security measures and precautions for keeping DCs safe:
- Firewall usage.
- Data encryption (at rest, in transit, and in use).
- Restricted use of risky protocols (e.g., remote desktop or BGP).
- Proactive patch management.
- Zero-trust security measures.
- Continuous monitoring and logging.
- Intrusion detection systems (IDSes).
- Regular data backups.
- Setup of multiple synchronized domain controllers for redundancy and high availability.
Plan to add a DC to your network? Remember to outline main configurations and go-to staff members in your network security policy.
What Is the Difference Between Active Directory and Domain Controller?
Active Directory and domain controllers are related concepts within the Microsoft Windows ecosystem. However, they refer to different components with distinct roles. AD is the overarching service, while a DC is a server that runs AD services.
Active Directory is Microsoft's directory service that provides a centralized location for managing and organizing network resources. AD serves as a database that stores all relevant information about network objects, including:
- User accounts (usernames, passwords, full names, emails, departments, etc.).
- Computer accounts (names and IP addresses).
- Security groups used to grant access permissions.
- Distribution groups for email distribution lists.
- Organizational Units (OUs) that allow an admin to organize and manage objects in a hierarchical structure.
- Group Policy Objects (GPOs) used to manage the settings and configurations of domain-based users and computers.
- DNS info (domain names, DNS-related records, trustworthy domain lists, etc.).
- Service Connection Points (SCPs) that define the location of services within the directory.
The AD centralizes authentication, authorization, and management of all domain-based objects. On the other hand, a domain controller is a server that runs the Active Directory services. The primary function of a DC is to manage security authentication requests and enforce security policies dictated by AD-based instructions.
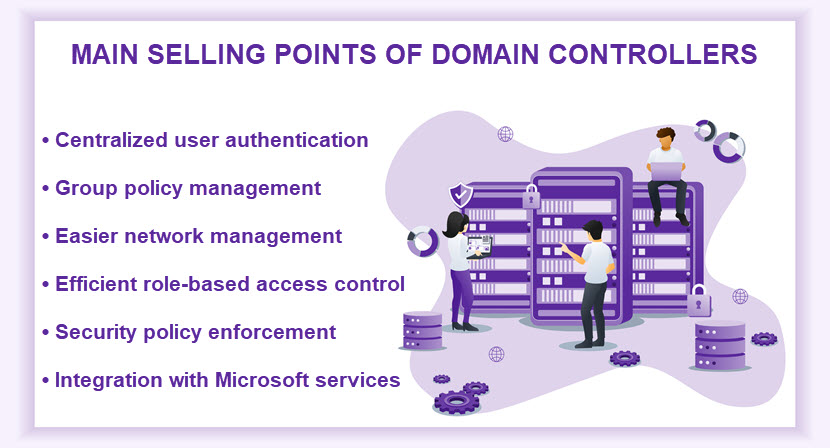
Types of Domain Controller
In the context of Microsoft AD, there are two types of domain controllers: read-only and read-write. These domain controllers serve different purposes within the network architecture.
A read-only domain controller (RODC) holds a read-only copy of the Active Directory database. The read-only nature makes this type of DC suitable for deployments in locations with more security risks.
As the name suggests, RODCs do not allow write operations directly to the AD database. Any changes or updates are replicated to a domain controller with write privileges. Here are a few scenarios in which a RODC is a sensible choice:
- Deployment in branch offices or remote locations where physical security is a concern.
- Scenarios in which you store sensitive info in the AD database and are concerned about having too many read-write DCs.
- Situations where an admin wants to grant read-only AD access to partners, external consultants, or auditors.
- Systems with limited bandwidth between the remote deployment location and the central data center.
On the other hand, a read-write domain controller (RWDC) is the standard type of domain controller in a Microsoft AD environment. Unlike an RODC, an RWDC has full read and write access to the AD DS. Therefore, these DCs can accept changes, updates, and modifications to the directory.
What Are the Main Components of a Domain Controller?
A domain controller consists of several components, each serving a specific function in managing and authenticating domain-based users and resources. Here are the main components of a domain controller:
- Active Directory database. This hierarchical database stores attributes and properties for each network object within the domain.
- Directory service. The directory service is a set of processes and services responsible for managing the AD database. The directory service includes components that handle authentication, authorization, and directory-related operations.
- Lightweight Directory Access Protocol (LDAP). The LDAP is a protocol for accessing and managing the info stored in the AD database. Clients use the LDAP to perform queries and updates to the directory service.
- The NetLogon service. This service handles authentication and domain controller location services.
- Domain Name System (DNS). The DC provides DNS services to translate domain names into IP addresses (and vice versa). Proper configuration and DNS best practices are crucial for replication and domain functionality.
- NT Directory Service (NTDS). The NTDS includes the Local Security Authority (LSA), which handles security policies. The NTDS also includes the replication engine, which ensures consistency in environments with multiple domain controllers.
- Security Accounts Manager (SAM). The SAM database stores security info for local user accounts and groups on the domain controller.
- Distributed File System Replication (DFSR). The DFSR is responsible for replicating SYSVOL, a shared folder that contains important system files, scripts, and Group Policy objects.
- Kerberos authentication service. Kerberos authentication provides a secure method for verifying the identity of users and computers accessing domain resources.
Seamless operation of the domain controller requires proper configuration for each component. Misconfigurations lead to authentication and replication problems, so ensure your staff has the technical know-how to set up and use the DC if you opt to deploy one.
How Domain Controllers Work
When a user attempts to log in to a computer or access a network resource, the domain controller starts the authentication process. The user provides a username and password, while the DC uses Kerberos to verify the user's identity.
Once authenticated, the DC determines the level of access the user has based on the following info in the AD DS:
- Group memberships.
- Relevant policies.
- Access control settings and restrictions.
In addition to authentication and authorization, the DC enforces policies set in the AD DS. The domain controller applies security policies to users and computers within the domain. The most common policies businesses enforce with a domain controller include:
- Password policies (e.g., complexity requirements, regular password changes, expiration times, etc.).
- Policies for user account creation, usage, and deletion.
- Configuration and security policies.
- Patching policies.
- Remote access policies.
- Device-related policies (e.g., the use of removable storage devices, peripheral device usage, BYOD policies, etc.).
Large networks often have multiple domain controllers. Two or more DCs enhance fault tolerance and ensure AD services remain available even if one domain controller goes down.
In a multi-DC environment, the primary read-write DC replicates changes made to the AD database to other DCs within the same domain. Replication ensures that all DCs have consistent and up-to-date data.
Who Needs a Domain Controller?
Whether an organization requires a domain controller depends on the size and complexity of the network. Companies interested in centralized authentication, efficient user and resource management, and consistent security policies are good candidates for a DC.
Here are the typical adopters of domain controllers:
- Organizations with a medium-to-large number of users, computers, and network resources that operate under the same set of rules.
- Companies that require a centralized authentication system that allows users to log in with a single set of credentials.
- Enterprises with diverse IT assets that want to use a DC to organize and control access to network resources.
- Organizations that want to enforce uniform security settings, configurations, and policies across a broad network.
- Businesses with multiple branch offices that want to optimize network traffic, lower latency, and provide localized authentication services.
- Organizations that use or want to start using Microsoft network services and technologies (e.g., Exchange Server or SharePoint).
- Companies in strict industries that want a DC to enforce security measures and maintain audit trails.
- Teams looking to deploy a hybrid cloud and use a domain controller to integrate on-prem AD with cloud services.
Interested in hybrid clouds? Check out pNAP hybrid cloud solutions and see how we help our clients cost-effectively combine public cloud, private cloud, and on-prem IT resources.
What Are the Advantages of Domain Controllers?
A domain controller provides a range of security and management benefits. Deploying a DC makes networks safer, more transparent, and easier to manage.
Here are the main benefits of using a domain controller:
- Reliable identity verification. A domain controller reliably authenticates and authorizes every user and computer before granting access to domain-based resources.
- Centralized authentication. A DC enables users to log into any computer within the domain with a single set of credentials. This centralization simplifies the login process for the end user and enhances overall security.
- Centralized management. A domain controller saves cost and time by enabling an admin to set login and security parameters from a centralized server. Network admins get to update network rules and manage accounts from a single location.
- Policy enforcement and management. A DC enables admins to define and enforce security settings, configurations, and policies across the domain.
- High scalability. Larger organizations typically use multiple DCs to distribute the authentication load and provide fault tolerance. This scalability is essential for large networks that regularly acquire new users and devices.
- Logging and auditing. Domain controllers generate logs that capture events and activities within the domain. Logging and auditing are crucial for monitoring a network and troubleshooting issues.
Perform a network security audit and find out whether your network could do with a boost in security controls.
What Are the Disadvantages of Domain Controllers?
While highly beneficial to network security, domain controllers have a few notable drawbacks. Admins must carefully configure and manage a DC. Mistakes during setup or day-to-day maintenance can lead to unauthorized access, data breaches, or disruptions to network services.
Here are the most common shortcomings of using a domain controller:
- Setup complexity. Setting up and configuring a DC is time-consuming and requires careful planning.
- Administration overhead. Maintaining a domain controller is complex, which poses a challenge for organizations with smaller teams or less experienced network admins.
- Extra IT costs. Deploying and maintaining a domain controller often involves costs associated with hardware, software licenses, and ongoing maintenance.
- Security risks. A poorly configured or maintained domain controller often leads to misconfigurations and vulnerabilities. A flaw or exploit in a DC can leave the entire network vulnerable to a cyber-attack.
- Replication challenges. Inconsistent replication between multiple domain controllers can cause data discrepancies and operational issues.
- Limited support for non-Windows environments. Domain controllers are primarily designed for Windows environments. Organizations with non-Windows systems may encounter compatibility and support limitations.
You can mitigate most potential DC-related disadvantages through proper planning and staff training. Ensure your network admins plan for the pitfalls discussed above to get the most out of your DC.
How to Set up a Domain Controller
Setting up a domain controller on a server running Microsoft Windows Server 2022 is a two-step process. First, you must install the Active Directory Domain Services role. Then, you promote the server to a domain controller.
Before you start, there are a few prerequisites. You must install Microsoft Windows Server 2022 on a dedicated machine. Then, assign a static IP address to the server and choose a unique name for the server that complies with DNS naming conventions.
Step 1: Install Active Directory Domain Services Role
Log into the Active Directory Server and open the Server Manager. Follow these steps to install the AD DS role:
1. Click Manage in the upper right corner of the screen and select Add Roles and Features.
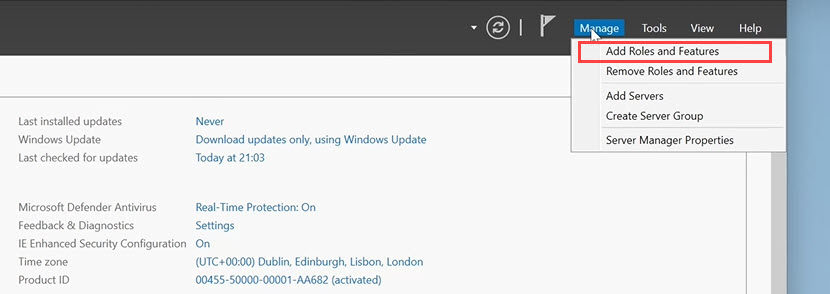
A Before You Begin screen pops up next. This text is purely informational, so read through it and click Next.
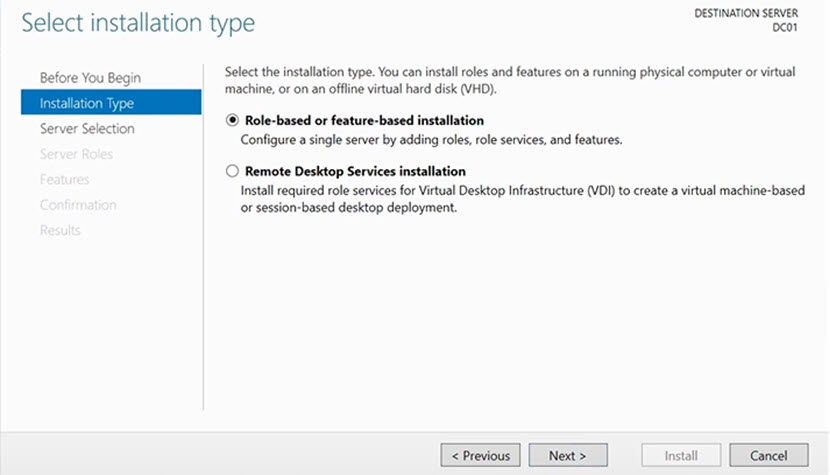
2. Choose the installation type. If you plan to deploy a DC on a virtual machine, choose Remote Desktop Services installation. Otherwise, go with Role-based or feature-based installation.
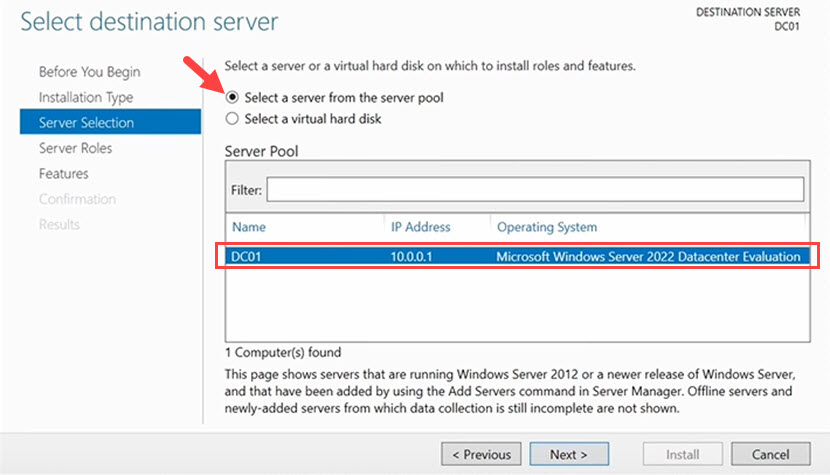
3. Select the destination server on which you want to install the AD DS role. Choose the server with the static IP address you created before starting the installation process.
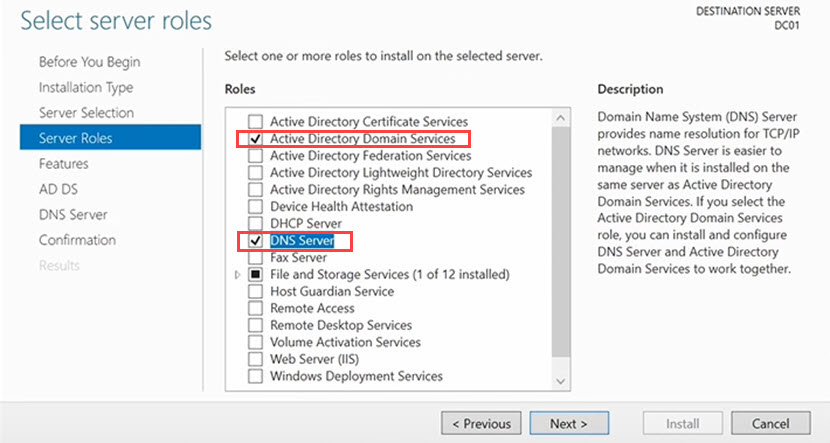
4. Select the roles you want to install on the server based on your needs. The two must-have roles are Active Directory Domain Services and DNS Server.
Hit Next to reach the Features screen.
5. Tick the Group Policy Management field and click Next.
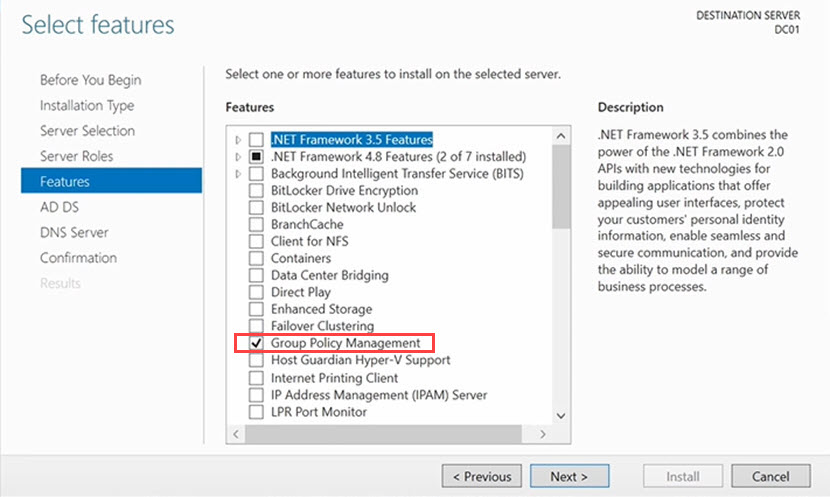
6. The next two screens (AD DS and DNS Server) present some useful info, so go through them and click Next once you finish reviewing them.
7. Select the Restart the destination server automatically if required button and click Install on the final screen. The installation process takes a few minutes.
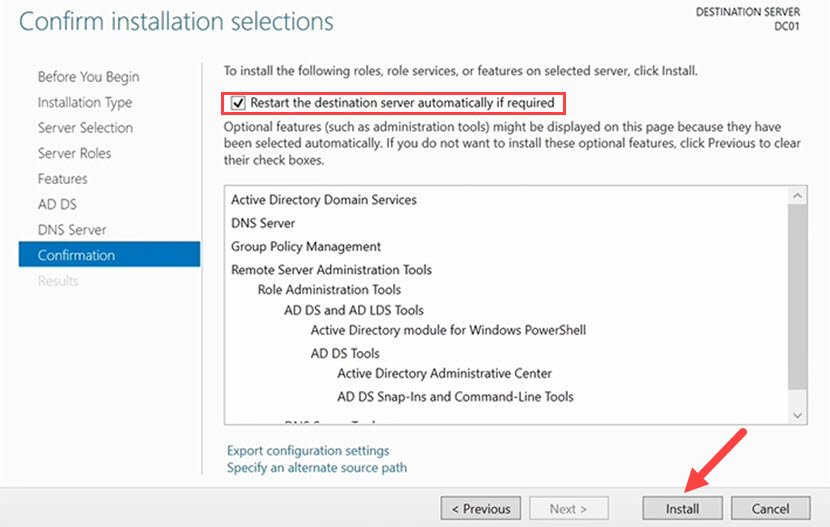
Step 2: Promote Server to a Domain Controller
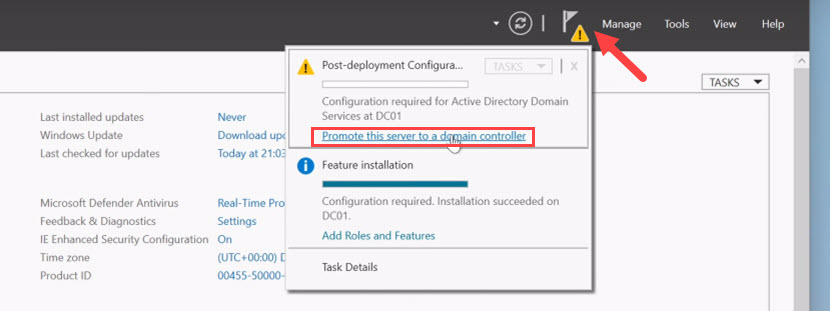
Once you install the AD DS role, a notification flag appears next to the Manage menu. Follow these steps to promote the server to a domain controller:
1. Open the notifications dropdown menu (which now has a small exclamation mark sign next to it) and select Promote this server to a domain controller to open the Deployment Configuration screen.
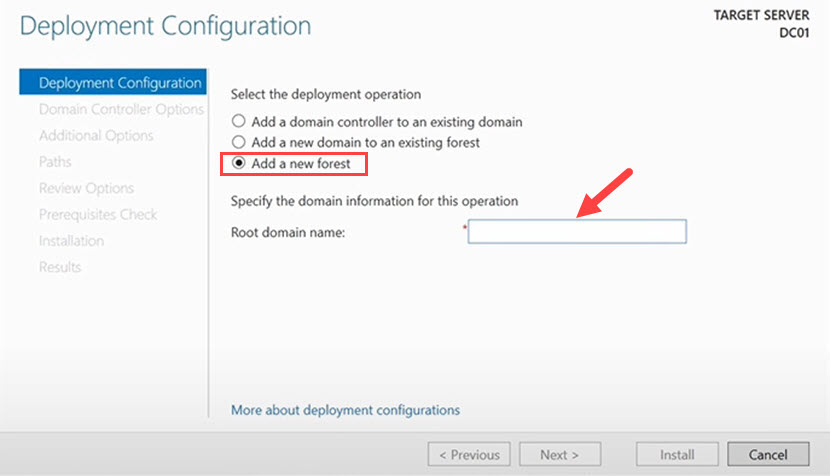
2. Click Add a new forest, type in your preferred Root domain name, and click Next.
3. Choose a forest functional level and a domain functional level. Remember that the domain functional level must be equal to or higher than the forest functional level.
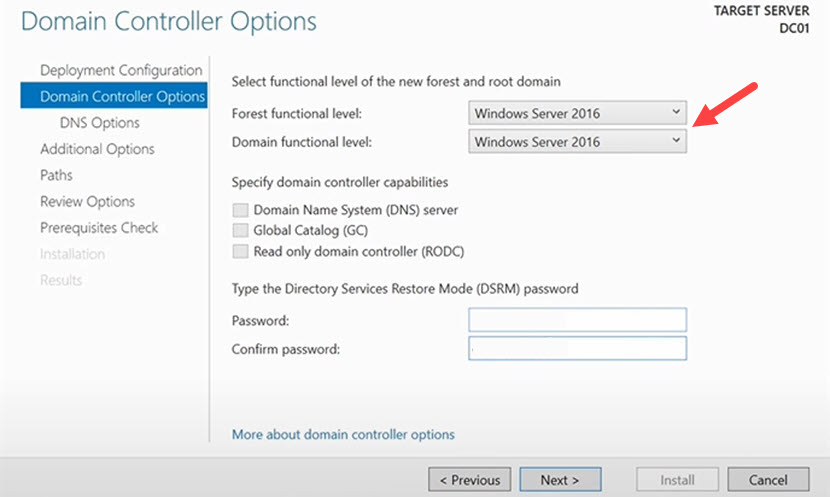
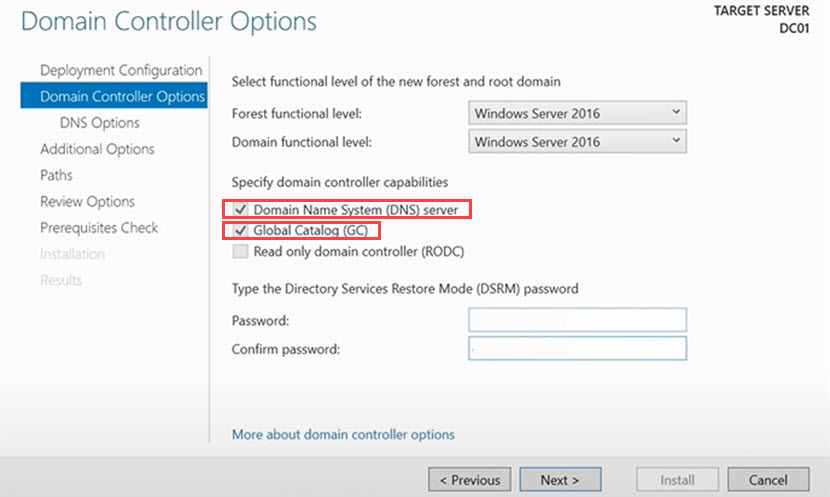
Under the Specify domain controller capabilities section, select the following options:
- Domain Name System (DNS) server.
- Global Catalog (GC).
Tick the Read only domain controller (RODC) if you want to deploy a read-only DC.
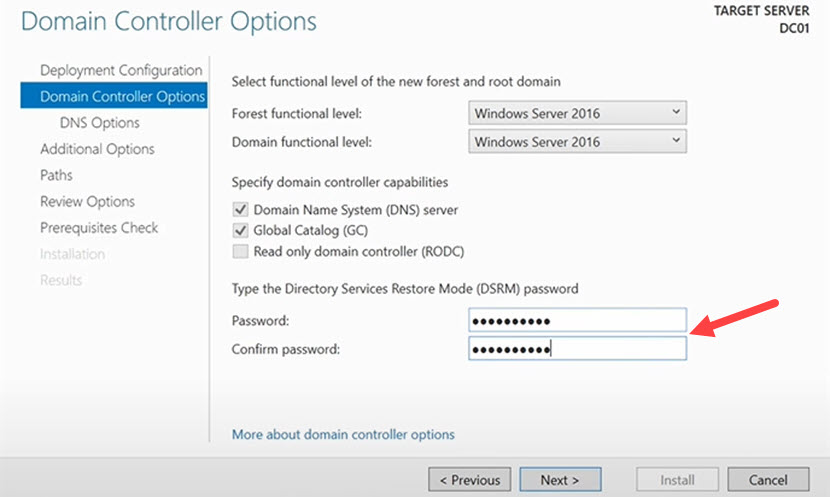
4. Enter a unique Directory Services Restore Mode (DSRM) password, which you can later use to restore AD data if something goes wrong. Click Next.
5. The DNS Options tab informs you that there is no way to create a delegation for this DNS server. Skip this menu by clicking Next.
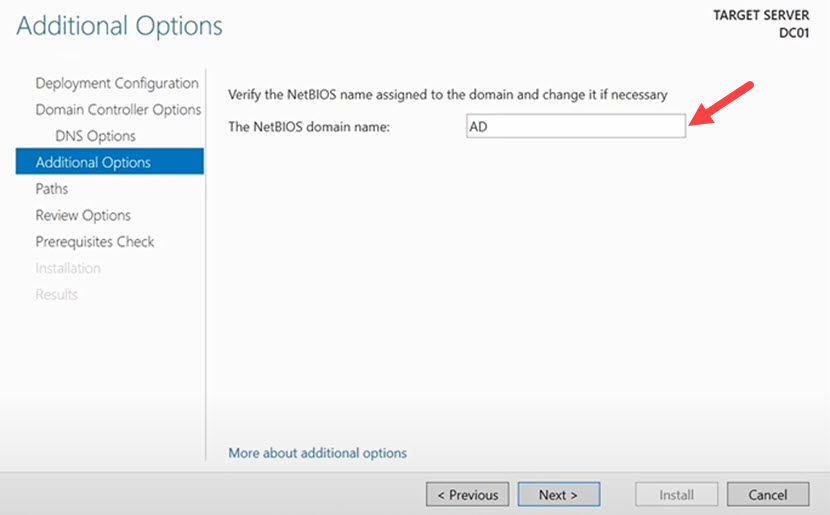
6. Enter a NetBIOS name for the domain on the next screen. We recommend matching the NetBIOS name with the root domain name. Once done, click Next.
7. Select folders where you want to store your database, log files, and SYSVOL. The default settings are typically fine, so review folder suggestions and click Next.
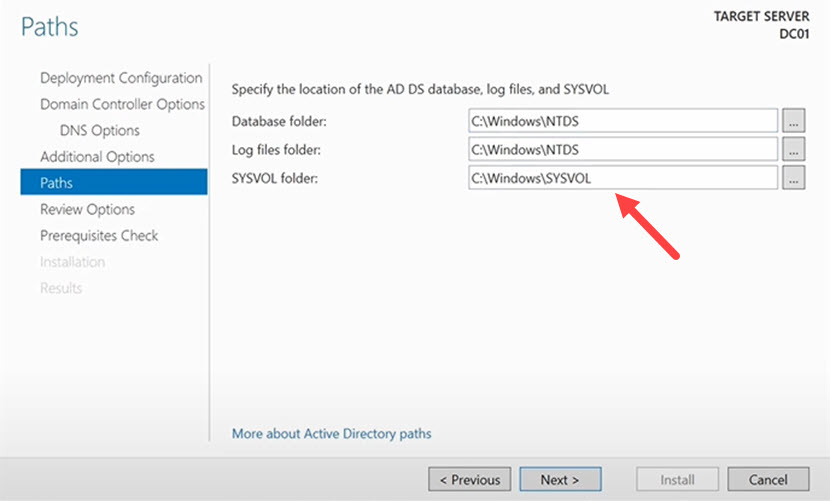
8. The Review Options tab presents an overview of the setup process. Review the presented info and click Next.
9. The Active Directory now performs a prerequisites check. Once the check ends, click Install. The setup wizard automatically reboots several times during the installation.
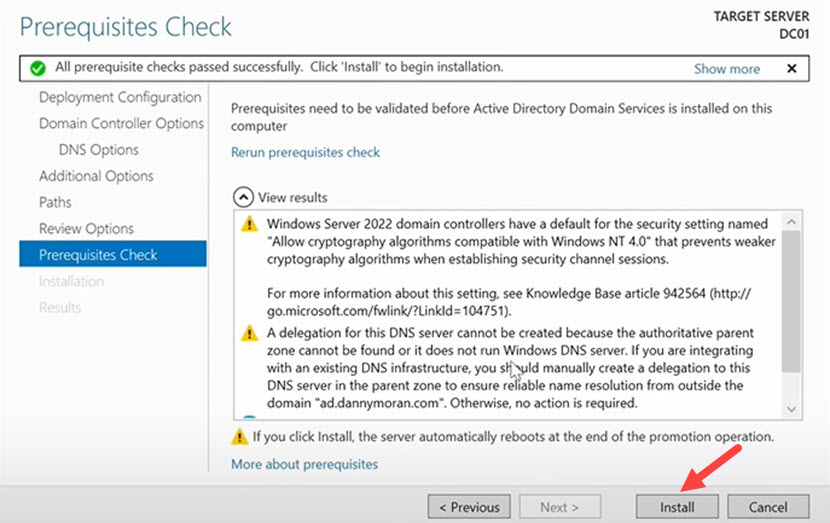
Once the installation ends, run the dcdiag /v command from the command line to verify the health of the domain controller.
DCs Make Networks Safer, More Consistent, and Easier to Manage
A domain controller is a valuable asset for any company with a large network that requires tighter security and more centralized control. Consider whether your business is a good candidate for DC deployment, and use what you learned here to get your adoption off to a good start.