The Domain Name System (DNS) is essential in network communication. Proper configuration and security are critical for ensuring business continuity and protecting against different cyberthreats. You can improve your infrastructure's reliability and performance by implementing the best practices listed in this guide.
This article outlines the best DNS practices and security measures to keep your infrastructure reliable and secure.

DNS Best Practices
A secure and maintained DNS infrastructure is essential for uninterrupted network operations. A properly configured DNS also helps secure an infrastructure against cyber attacks.
The following sections list the best DNS practices. Following these tips ensures the system is secure and has optimal performance.
1. Ensure DNS Redundancy and High Availability
DNS servers are the pillar of network reliability. To prevent downtime and ensure high availability, configure at least two DNS servers:
- Primary DNS server. Handles regular queries.
- Secondary DNS server. Acts as a backup server in case the primary one fails.
Implement continuous replication to ensure the DNS records are synchronized between the servers. In case of connection issues, the setup routes queries to the secondary DNS server to avoid interruptions.
2. Restrict Access to DNS Servers Information
DNS servers and data should not be available to all users. Restricted access helps protect servers from unauthorized changes and attacks. Ways to limit access include:
- Hide primary DNS servers. Ensure primary servers are not visible to external users or listed in the public nameserver databases.
- Limit access to authorized users. Grant access to system administrators and trusted IT personnel only. Implement access control lists (ACLs) to define who can query and access the DNS server.
- Use authoritative servers for public queries. If a DNS server requires external access, configure it as an authoritative-only server to handle zone-specific queries.
- Restrict recursive queries. Prevent external users from querying internal recursive DNS servers.
Controlling access and limiting visibility reduces the attack surface and strengthens DNS security.
3. Use Internal DNS Servers for Private Queries
For efficient and secure operations inside the network, internal DNS servers are used to resolve private domain names. External DNS servers are unfamiliar with internal resources and cannot resolve hostnames of internal devices. Attempting to use an external DNS server in these situations results in connectivity issues.
Devices within the organization should point to the internal DNS server to resolve private domains (e.g., file shares, internal documentation). This approach also safeguards private resources from exposure to external DNS servers.
4. Use Local or Closest DNS Servers
Large and distributed organizations can utilize local DNS servers to improve performance and reduce network latency. The load times increase when a query travels to a remote nameserver across WAN. When a user queries a local DNS server, the response times are minimal, and it improves user experience.
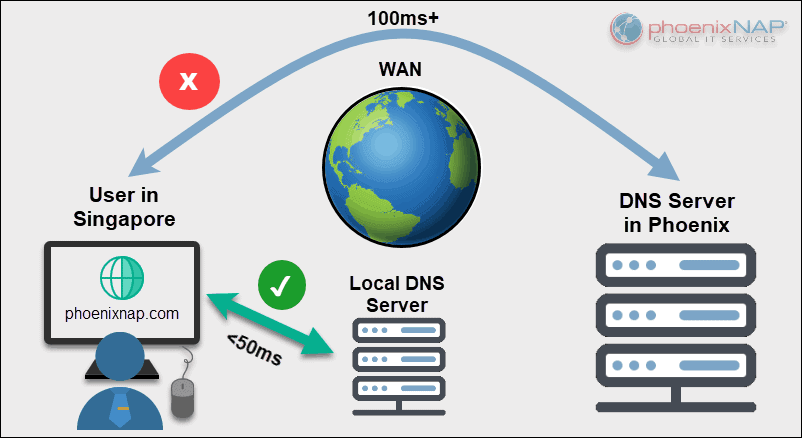
To further optimize performance:
- Set up local servers. Place the servers close to the end users to minimize latency.
- Point users to the closest server. Configure DNS settings to point users to the nearest DNS server to ensure the fastest response times.
- Reduce load on central servers. Central servers can offload most queries to local DNS servers and improve performance.
Utilizing the closest DNS server improves the speed and efficiency of DNS resolutions across the whole network.
Note: WANs can be an excellent communication strategy for the right kind of organization. If you are basing your strategy on the usage of WANs, we recommend you read our article on how carrier-neutral data centers can lower WAN costs.
5. Enable DNS Logging and Monitoring
Logging and monitoring are essential for tracking activity, identifying potential security threats, and troubleshooting DNS issues. Enable logging to monitor all requests and take action in case of unusual activity:
- Monitor queries. Logs help review DNS query records, which is essential when identifying patterns, troubleshooting, or detecting malicious activity.
- Enable debug logging. Debug logging affects performance, but it is essential when detecting configuration errors and cache poisoning attempts.
Actively logging and monitoring DNS activity improves infrastructure security and helps prevent Distributed Denial of Service (DDoS) or similar attacks.
Note: Learn how to check for a DDoS attack on a Linux server to improve detection and monitoring capabilities.
6. Lock DNS Cache
Cache locking prevents attackers from modifying cached DNS data before expiry. The process ensures DNS response data integrity and prevents malicious redirections. To secure the cache:
- Enable cache locking. Configure the DNS server to lock cached data for a specified duration. Typical duration is based on the TTL value.
- Set locking scale. Adjust the cache locking percentage, where 100 percent offers the highest security. The cached data is unalterable at this level until the TTL expires.
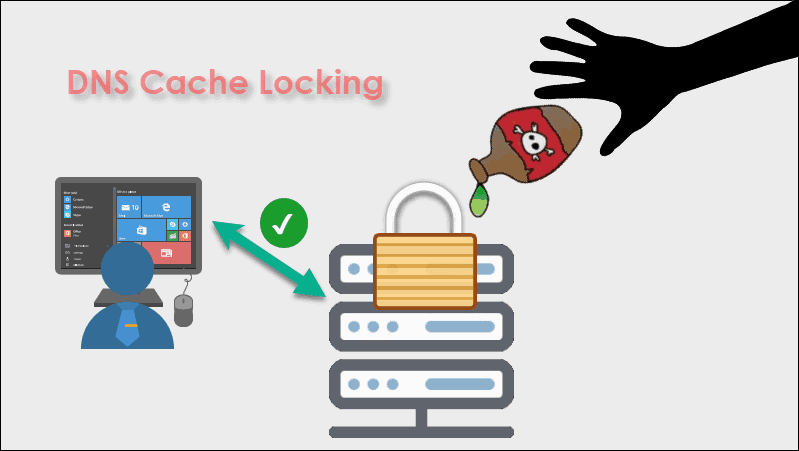
Implementing cache locking helps prevent cache poisoning and strengthens DNS security. It ensures users have accurate and unaltered DNS response records.
Note: Clearing DNS cache is also an important security precaution. Learn more about why and how to do it by reading our article How to Flush DNS Cache on Windows, macOS, & Linux.
7. Filter Requests
DNS filtering is an effective way to block access to suspicious websites. By blocking queries to known malicious domains, you can lower the risk of attacks and protect your network from various threats. To filter requests:
- Block malicious domains. Prevent users from accessing websites known for malware, phishing, and other cyber threats.
- Improve productivity. Block non-business websites to improve productivity. Social media or streaming platforms should be inaccessible based on company policies.
Modern DNS tools offer regularly updated pre-configured blocklists, which are simple to implement and maintain. Filtering requests is a good way to safeguard your network and reduce exposure to known threats.
8. Validate DNS Data Integrity with DNSSEC
Domain Name System Security Extensions (DNSSEC) is a protection layer for DNS queries that ensures data integrity and record authenticity. DNSSEC prevents spoofing and changing DNS records by using digital signatures to verify a response's authenticity. As a result, clients know they received verified information for the request they sent.
Validating the source of DNS responses blocks attackers from injecting false records or redirecting to malicious sites. It protects and secures the DNS infrastructure from common attacks.
9. Implement Rate Limiting
Rate limiting helps prevent a DNS server from being overwhelmed by excessive requests, such as those in Denial-of-Service (DoS) attacks. Limiting the number of queries a server can process from a single source helps prevent abuse and ensures network stability.
Set the query thresholds to block excessive requests. Rate limiting controls the request volume and ensures consistent performance during high-demand periods. Consider using a tool like the Apache mod_evasive module to detect and respond to abnormal request patterns.
Note: Learn how to improve DNS lookup time by setting up Raspberry Pi DNS Server.
10. Update DNS Software
Regular updates to DNS software are required to maintain network security and optimal system performance. New updates often include vulnerability patches, additional features, and performance optimization.
Reasons to keep DNS software up-to-date include:
- Addressing vulnerabilities. Updates address flaws that attackers may use to exploit the system.
- Performance improvements. Updates also include optimizations that help reduce latency and improve query handling.
- Compliance. Upgrading ensures the DNS infrastructure follows the latest protocols and security requirements.
A proactive approach to maintaining DNS software ensures the server operates securely and efficiently.
11. Separate Authoritative and Recursive DNS Servers
Separating authoritative and recursive DNS servers reduces the attack surface and improves overall security. Every server type has unique responsibilities:
- Authoritative servers. They store and give answers for specific domain zones. They respond only to queries for which they are authoritative.
- Recursive servers. These servers resolve external queries by searching different DNS servers.
Combining the two functions into one server creates unnecessary vulnerabilities and complicates management. By creating a clear division, the infrastructure is simpler, and the scope of a potential breach is limited.
12. Implement DDoS Protection
DNS servers are common targets for DDoS attacks. Implementing a robust DDoS protection service ensures the infrastructure stays secure even when under attack.
To make the most out of such services, invest in a cloud-based dedicated infrastructure with DDoS migration services to absorb or deflect malicious traffic.
Note: See how phoenixNAP provides enterprise-level DDoS protection and mitigation for more details.
13. Secure Zone Transfers
DNS zone transfers are DNS transactions that help maintain synchronization between primary and secondary servers. Implementing proper security ensures only authorized servers participate in the zone transfer process.
- Restrict data transfers. Restrict transfers to trusted servers to allow replication between specific locations.
- Use encryption. Encrypt the data in transit to prevent man-in-the-middle attacks and unauthorized access.
- Authenticate servers. Set up authentication for all servers to help verify identity and prevent tampering with DNS data.
14. Perform Periodic Testing
Testing the DNS infrastructure helps identify weaknesses. The process ensures the server can handle high traffic or mitigate potential attacks.
Simulate high traffic to perform stress tests and evaluate how the DNS server performs under heavy load. Identify potential gaps and exposure points and test the failover mechanism between primary and secondary servers.
15. Create Backups
Back up the DNS configuration to ensure a quick recovery in case of data corruption, loss, or a security breach. Create an effective backup strategy with these guidelines:
- Schedule regular backups. Back up DNS configuration regularly or set up automated backups to ensure the most recent data is copied.
- Secure backups. Use an encrypted storage solution to safeguard backup files from unauthorized access.
- Test the restore process. Test the backups in a controlled environment to verify their integrity and to simulate a disaster recovery process.
Managing backups helps reduce downtime, resolves critical issues, and keeps the network operational.
Conclusion
This guide listed the best practices for securing and optimizing DNS servers. The system can ensure high availability and efficient performance by following these tips.
For more network tools and tips, see how to flush the DNS cache in various systems.