When you enter a URL into a browser, DNS servers within the Domain Name System (DNS) translate the human-readable domain name into an IP address. This process, called DNS resolution, allows the browser to locate the correct host and request the web page.
Learn how DNS servers work, the different types of DNS servers, and find the right provider for your organization.
What Is a DNS Server?
DNS resolution is carried out by a distributed network of specialized DNS servers designed to complete specific tasks with low latency and high reliability. There are several types of DNS servers, each playing a distinct role in the resolution process.
Depending on its function within the broader DNS infrastructure, a DNS server may:
- Recursively query other DNS servers on behalf of the client to resolve a domain name into its corresponding IP address.
- Respond to iterative queries to guide resolvers to the next server in the DNS hierarchy.
- Store official DNS records to map domain names to IP addresses and define domain-related services.
- Cache DNS responses to speed up future DNS lookups.
- Forward client requests to upstream resolvers.
- Perform reverse DNS lookups using PTR records.
- Serve location-aware responses (GeoDNS) to route users to the nearest or most appropriate server.
- Filter or block queries based on preconfigured DNS security policies.
Not all DNS servers perform every task listed above. The behavior depends on their designated function within the hierarchy. Below is a brief overview of the core DNS server types and how they work together to resolve domains efficiently.
Types of DNS Servers
Each DNS server type has a specific role in resolving a domain name into an IP address. The following table lists DNS server types and their functions:
| DNS Server Type | Function | Example |
|---|---|---|
| Recursive DNS Server | Queries other servers in the DNS hierarchy on behalf of the client until it locates the IP address for a domain name. The results are temporarily cached to speed up future lookups. | A device sends a query for the phoenixnap.com domain to a recursive server like Google DNS (8.8.8.8) or Cloudflare (1.1.1.1). The server contacts root, TLD, and authoritative DNS servers to retrieve the IP address for the domain and returns it to the device. |
| Root DNS Server | Responds to recursive resolvers with a referral to the appropriate top-level domain (TLD) server based on the domain suffix (e.g., .com, .org). | A root server tells the recursive server that phoenixnap.com is part of the .com domain and refers it to the .com TLD server for more information. |
| TLD (Top-Level Domain) DNS Server | Handles queries for top-level domains and points the recursive DNS server to an authoritative server. | A .com TLD server contains information for all websites ending in .com. It tells the recursive server that the authoritative server for phoenixnap.com is ns1.example.com. |
| Authoritative DNS Server | Stores and serves official DNS records for a domain. When recursive servers query them, they return the IP address and other requested information. | The authoritative server for phoenixnap.com responds to the recursive server query with the actual IP address. |
| Caching DNS Server | Stores previous DNS query results to reduce latency and traffic loads. These servers do not perform recursion or serve authoritative records but only return cached responses when available. | A company configures its network to check a local caching server for the phoenixnap.com domain-to-IP mapping before forwarding the query to an external recursive resolver. |
| Forwarding DNS Server | Forwards queries to another DNS server (usually an upstream recursive resolver) instead of resolving them. Common in enterprise networks and home routers. | A home router receives a DNS query and forwards it to Cloudflare DNS (1.1.1.1) for resolution. |
Note: The Internet Assigned Numbers Authority (IANA), part of ICANN, manages the root zone and assigns responsibility for TLD nameservers.
How Do DNS Servers Work?
DNS systems are designed to respond quickly and conserve resources by minimizing the number of queries. If the example address is phoenixnap.com, the resolution process goes through the following steps:
1. The user enters the domain name into a browser.
Note: Modern browsers temporarily cache DNS records. If the record is found in the browser cache, the IP address is used and the HTTP request is sent directly to the destination server.
2. The operating system's DNS resolver also checks its local cache. If there is no cached entry, the query is forwarded to a configured recursive DNS resolver.
Note: In some cases, the local DNS cache may become corrupted. When this happens, the best solution is to flush the local DNS cache.
3. The DNS resolver checks its cache. If no entry is found, it queries a root nameserver to find the responsible TLD server.
4. The root server responds with a referral to the relevant TLD server. Since the domain in this example is phoenixnap.com, the TLD server is .com.
5. The resolver then queries the TLD server for phoenixnap.com.
6. The TLD server replies with the IP address of the authoritative nameserver for the domain.
7. The recursive server sends a final query to the authoritative nameserver.
8. The authoritative nameserver responds with the IP address for phoenixnap.com.
9. The recursive server caches the response and returns the IP address to the OS.
10. The OS passes the IP address to the browser, which uses it to send an HTTP(S) request to the destination web server.
11. The web server responds with the requested webpage.
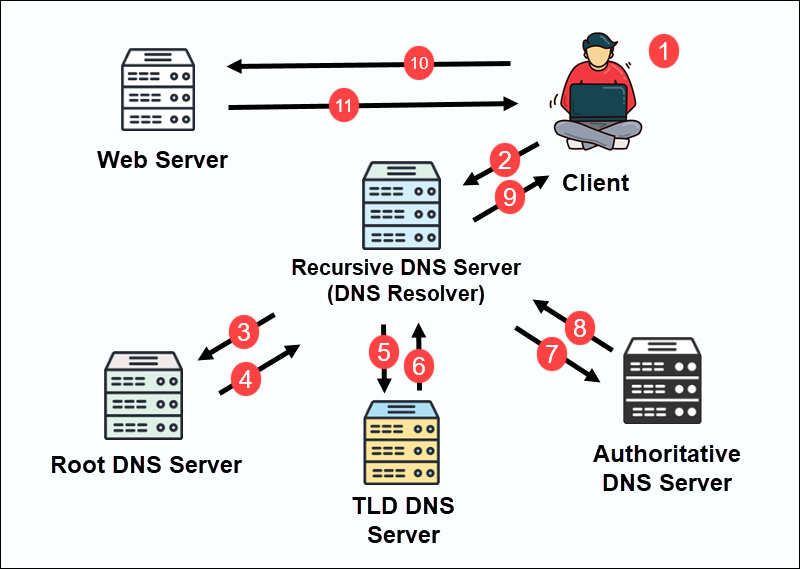
Note: This is a general overview of the DNS resolution process. Specific steps may vary depending on caching behavior, query type, and DNS record type.
Public vs. Private DNS Server
Anyone with an internet connection can use public DNS servers to translate domain names into IP addresses. These services are usually provided by internet providers or third-party companies like Google or Cloudflare. Besides DNS resolution, public DNS services often provide additional features such as traffic filtering, parental control, and phishing and malware protection.
Due to the nature of their operations, enterprise networks, data centers, and hybrid cloud environments combine public with private DNS servers. This is often necessary when internal DNS data must remain confidential and cannot be cached or exposed through public infrastructure. Private DNS servers allow organizations to implement robust network security policies.
Even though private DNS servers provide more security and flexibility regarding network design and customization, they also require dedicated staff, such as system or network administrators, and introduce additional costs related to setup and ongoing maintenance.
Note: Find out how to fix the DNS_PROBE_FINISHED_NXDOMAIN error in this step-by-step guide. This common issue occurs when the DNS system cannot resolve a provided URL into an IP address.
Choosing a DNS Server
While speed is essential, it is not the only consideration when selecting a DNS server, especially in a business environment.
When choosing a DNS service, consider the following:
- Use Case. You can use a public recursive DNS server like Cloudflare or Google to configure internet access for home devices or small office networks. However, if you own and manage a domain, you also need an authoritative DNS service to host and serve your domain's official DNS records.
- Need for private DNS. Most individuals and even small businesses can rely entirely on public DNS services. Organizations that handle sensitive DNS data, internal services, or private infrastructure should implement private DNS servers. This allows them to protect data from external exposure and gain more control over DNS policies.
- Performance and Reliability. Ideally, a DNS provider should deliver high uptime, low latency, and a global, distributed infrastructure. If you do not need private DNS servers, large public resolvers are highly optimized for speed and availability.
- Security Features. Both home users and companies should look for DNS services that offer Domain Name System Security Extensions (DNSSEC) to verify the authenticity of DNS responses, protocols for encrypting DNS traffic via HTTPS and TLS, and malware and phishing protection. Customizable logging policies are also essential if working in a privacy-oriented industry.
- Automation and Control. If you own and manage a domain, select a DNS service that allows you to customize DNS records, adjust TTL settings, and integrate with APIs to automate DNS management through deployment workflows or scripts.
DNS Providers
A DNS provider is an organization that offers DNS resolution services, such as public recursive resolvers, authoritative DNS hosting, or both.
The table below lists common DNS providers and compares them based on key features and capabilities:
| DNS Provider | Type | Privacy Policy | DNSSEC Support | Encrypted DNS (DoH / DoT) | Security Features | Content Filtering | API / Automation | Free/Paid |
|---|---|---|---|---|---|---|---|---|
| Cloudflare (1.1.1.1 / Cloudflare DNS) | Public resolver / Authoritative DNS | No logging (logs anonymized after 24h) | Yes | DoH and DoT | DDoS protection, bot management | No | Full API | Free Resolver and Paid Hosting |
| Google Public DNS (8.8.8.8) | Public resolver | Logs temporarily (for analysis) | Partial | DoH and DoT | Basic query validation only | No | None | Free |
| Quad9 (9.9.9.9) | Public resolver | No personal data stored | Yes | DoH and DoT | Malware + phishing blocking | Yes | None | Free |
| OpenDNS (Cisco) | Public resolver / Enterprise solutions | Customizable logging policies (enterprise solution) | Limited | No public DoT | Malware blocking, parental control | Yes | Full API (enterprise) | Free (basic) and Paid (enterprise) |
| NextDNS | Public resolver (customizable) | Fully private, user-controlled | Yes | DoH and DoT | Real-time threat protection | Yes | Full API | Free (basic) and Paid Plans |
| AWS Route 53 | Authoritative DNS hosting | AWS shared responsibility model | Yes | Not Applicable | Health checks, failover routing | No | Full API | Paid |
| Google Cloud DNS | Authoritative DNS hosting | Google Cloud privacy terms | Yes | Not Applicable | Scalable routing | No | Full API | Paid |
| Azure DNS | Authoritative DNS hosting | Azure privacy model | Yes | Not Applicable | Native integration with Azure | No | Full API | Paid |
| DNS Made Easy | Authoritative DNS hosting | Standard industry practices | Yes | Not Applicable | Traffic management, failover | No | Full API | Paid |
Conclusion
DNS is a foundational technology that keeps the internet running. By implementing a well-balanced DNS strategy, one that combines public and private servers, you can enhance performance, improve reliability, and ensure your online presence reaches its audience quickly.
DNS errors are common due to the number of different DNS providers, server types, and configurations. Even experienced network admins need a refresher and practical tips on troubleshooting DNS issues.