The Border Gateway Protocol (BGP) enables routers to determine the most efficient path for Internet traffic. Unfortunately, BGP was designed to make the Internet run smoothly, not securely.
This protocol is full of inherent vulnerabilities that often lead to BGP hijacking incidents (whether malicious or accidental). Cybercriminals use BGP hijacks to redirect traffic, tamper with in-transit files, and cause data breaches.
This article explains the dangers of BGP hijacking and shows how criminals exploit this protocol to spy on traffic and steal data. Jump in to see how BGP hijacks occur and learn about the most effective ways to protect your network from BGP-related incidents.

What Is BGP?
BGP is an exterior gateway protocol used to exchange routing information between autonomous systems (ASes). The main purpose of BGP is to provide directions to traffic going from one IP address to another.
An AS is a large network or group of networks under the control of a single administrative domain. Most ASes are either ISPs or large organizations with their own networks and multiple upstream connections to ISPs.
Each AS has a unique ASN (Autonomous System Number) that helps the BGP identify the entity. Here are a few examples:
- Verizon has an ASN of 701.
- AT&T has an ASN of 7018.
- Microsoft has an ASN of 8075.
- The University of Virginia has an ASN of 225.
Each AS contains multiple routers with specific IP prefixes (or routes) they advertise to neighboring ASes. Adjacent ASes connect with each other and share routes that they either:
- Originate (i.e., they are the source of).
- Learn from adjacent ASes.
Over time, AS routers build a routing table using the routes learned from adjacent ASes. The BGP uses this data to construct a map of network reachability. This "road" map enables the protocol to route traffic between IP addresses. Here's how this process works in practice:
- Someone in New York wants to access a website hosted in California.
- The request goes to the user's local ISP (i.e., the local AS).
- A DNS (Domain Name System) server provides the IP address.
- The BGP determines an optimal path for the request to reach the California-based website's IP address.
- BGP guides the traffic through AS routers and networks across the country and back.
BGP always favors the shortest route from one AS to another (i.e., the path with the fewest possible network hops).
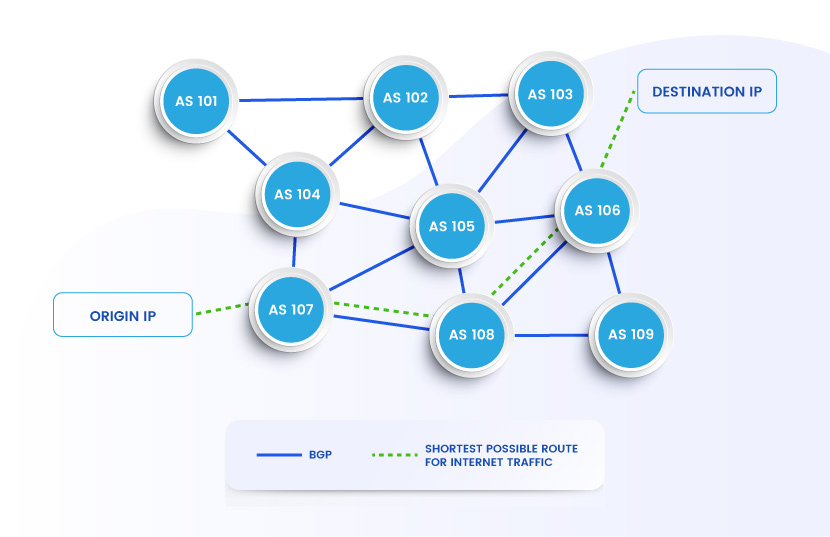
While effective, BGP is a trust-based protocol. Each AS inherently believes the info provided by its neighbor ASes. Any AS can advertise a better or more direct route (whether intentionally or accidentally), which is a major security loophole.
What Is BGP Hijacking?
BGP hijacking occurs when an AS announces IP address spaces belonging to another AS. This announcement attracts traffic meant for that IP address range.
Other common names for BGP hijacking are:
- Prefix hijacking.
- Route hijacking.
- IP hijacking.
BGP hijacking occurs when someone or something corrupts the routing tables maintained by AS routers. This corruption enables a backbone router to improperly advertise as having the most efficient route to a network.
Since BGP always favors the shortest path to the desired IP address, anyone looking to cause a BGP hijack must create a route announcement that either:
- Provides a more specific route with a smaller range of IP addresses than other ASes.
- Offers a shorter route to certain blocks of IP addresses.
Both strategies require the hacker to either control an AS router or compromise one of the approx. 80,000 currently operational ASes. This process is easier said than done, which is why most malicious BGP hijacks are the work of highly skilled and well-funded hacker groups.
BGP hijacking enables attackers to reroute Internet traffic to the wrong destination or route. Rerouting traffic enables a threat actor to intercept, spy on, or tamper with transmitted data.
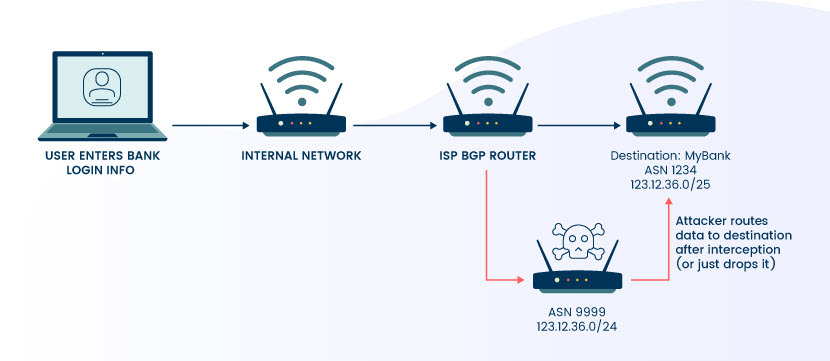
The easiest way to understand BGP hijacking is to compare it to someone secretly changing all the signs on a stretch of freeway and rerouting traffic onto incorrect exits.
How Can BGP Be Hijacked?
While the term BGP hijack implies malicious intent, BGP hijacking often results from accidental errors. These incidents are usually the result of human error or a misconfiguration in BGP routers.
Common causes of accidental BGP hijacking include:
- Incorrect prefix announcements.
- Unintentional propagation of incorrect routing info.
- Improper use of ASNs.
- Inadvertent advertising of IP prefixes that belong to another AS (so-called route leaks).
Intentional BGP hijacks are less common but more dangerous since there is a clear malicious goal behind the attack. Here are the most common ways threat actors cause hijacks:
- IP prefix spoofing. Threat actors announce IP prefixes that do not belong to them, creating false BGP announcements that divert traffic to or through their own network.
- ASN spoofing. Attackers announce routes with AS numbers they don't legitimately control. Threat actors impersonate another AS and direct traffic through their own network instead of the legitimate destination.
- AS hacking. Direct hacking of an AS enables a cybercriminal to compromise the internal infrastructure of an AS and gain control over one or more BGP routers. Hackers then manipulate announcements to redirect traffic.
- IP address spoofing. Attackers spoof the source IP address of BGP messages. Spoofing makes the message appear as if the announcement is coming from a trusted source, which hackers use to inject false routes into the BGP system.
- Session hijacking. Attackers intercept in-transit traffic and modify routing updates. That way, hackers gain access to BGP sessions and influence routes.
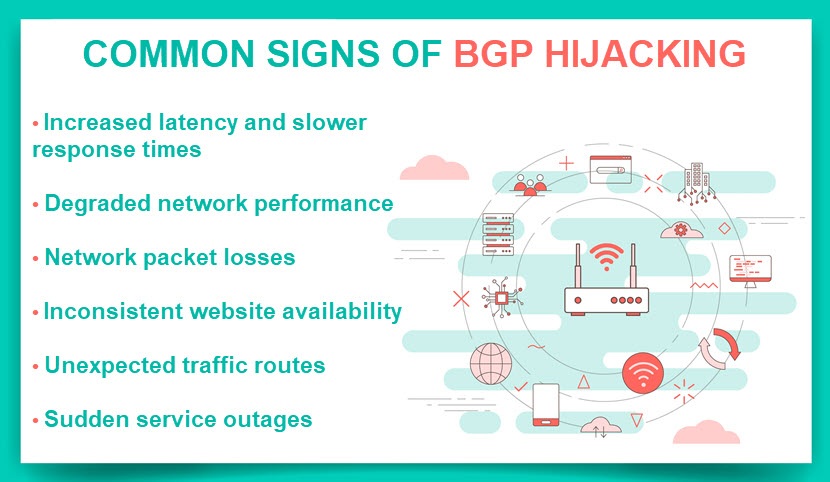
BGP hijacks are notoriously difficult to detect for non-AS admins. Common signs of a hijack (degraded performance, slow response times, etc.) could result from various other issues (e.g., network congestion or hardware failures).
ASes also often struggle with identifying a BGP hijack. Most threat actors camouflage their activity behind other ASes or announce unused blocks of IP prefixes.
What Happens When BGP Is Hijacked?
In the best-case scenario, BGP hijacking makes traffic take an unnecessarily long route, which increases latency. However, threat actors behind a BGP hijack typically have a more malicious goal than slowing down traffic. Here are the most common ones:
- Traffic redirection. Attackers use a BGP hijack to direct traffic to other destinations (e.g., a phishing or malware-infected website).
- Data interception. A hijack enables threat actors to spy on in-transit data while info passes through a malicious network. Attackers often also capture in-transit data, causing data leakage or breaches.
- Data manipulation. Hijackers can tamper with transmitted data. Threat actors may modify or inject malicious content into the traffic, leading to data corruption or the spread of malware.
- Service unavailability. BGP hijacking often causes the unavailability of services for impacted IP addresses.
- Resource abuse. Sometimes, attackers use illegitimately announced IP prefixes to abuse network resources belonging to target organizations.
- Distributed Denial of Service (DDoS). Some cybercriminals use BGP hijacking to run or amplify DDoS attacks. The hijacker redirects traffic through their infrastructure and overloads the target network or service with a massive volume of bogus traffic.
All pNAP servers have free DDoS protection that keeps you online 24/7 with automated traffic filtering and stand-by DDoS mitigation infrastructure.
BGP Hijacking Examples
While rare compared to more prevalent cyber attacks (e.g., ransomware, SQL injections, man-in-the-middle attacks, etc.), BGP hijacking is a common incident. Below are a few examples of impactful BGP hijacks from recent years.
Google, Apple, Facebook, Microsoft, Riot Games, and TwitchTV
In December 2017, threat actors made unauthorized announcements of around 80 IP prefixes used by six major companies (Google, Apple, Facebook, Microsoft, Riot Games, and TwitchTV). Threat actors caused traffic redirection that took data through the attacker's network, leading to:
- Service disruptions.
- Delays.
- Concerns about data security.
Hijackers operated from an AS in Russia called DV-LINK-AS (AS39523). While no official numbers ever surfaced, hackers likely compromised massive amounts of personal data (e.g., email addresses, passwords, usernames, etc.).
Crypto Mining Hijack
In March 2018, several ISPs (including Amazon and Google) were affected by BGP hijacks used to divert traffic to rogue servers.
The primary motive behind this BGP hijacking was to exploit the computing resources of redirected traffic for cryptocurrency mining. The attackers harnessed the computational power of the redirected devices to mine Bitcoin and Ethereum.
Learn more about crypto malware and cryptojacking.
MyEtherWallet (MEW)
In April 2018, threat actors used BGP hijacking to redirect traffic intended for MyEtherWallet.com, an Ethereum cryptocurrency wallet service, to a malicious server. Attackers stole approximately 1300 IP addresses belonging to AWS.
Redirecting traffic to a fraudulent server enabled criminals to capture:
- Login credentials.
- Private keys.
This incident resulted in the theft of $152,000 worth of cryptocurrency from users who attempted to access their accounts during the hijacking.
The MainOne Incident
In November 2018, a Russian ISP named MainOne unintentionally announced more than 200 IP prefixes from other ASes, including a few belonging to Google.
As a result of the route leak, Google's traffic was routed through MainOne's network. Several services, including Google Search and YouTube, experienced severe performance issues during the incident. There were also several reports of data security concerns.
European Telecommunication Networks
In June 2019, a Swiss data center accidentally leaked over 70,000 routes to China Telecom from its internal routing table. China Telecom re-announced these routes, declaring itself the shortest way to reach the Swiss data center and several other nearby European ISPs.
This incident lasted for over two hours. Users of affected networks suffered slow connections while local ASes had to deal with DoS-related issues.
Rostelecom
In April 2020, a BGP hijack involving over 8,800 prefixes affected companies such as Akamai, Amazon, and Alibaba. A Russian ISP called Rostelecom was implicated in the BGP hijack.
Major financial institutions and government organizations had to deal with traffic misdirection, service disruptions, and potential cybersecurity risks.
Celer Bridge
In August 2022, threat actors attacked the cryptocurrency service Celer Bridge using a BGP hijack that employed:
- Fake entries in AltDB (a free alternative to the IRR databases).
- Forged BGP announcements.
Altering the contents of AltDB enabled the attacker to trick a transit provider into believing that a UK-based hosting center was allowed to transit address space belonging to AWS, which hosted the Celer Bridge infrastructure.
This BGP hijacking incident lasted around 3 hours and resulted in $235,000 in losses.
Interested in detailed analysis of major cyber-attacks? Check out our articles on the hacking of PayPal in 2022 and our in-depth breakdown of the CommonSpirit Health ransomware attack.
How To Prevent BGP Hijacking?
The short answer - you can't. Preventing BGP hijacks falls within the domain of ASes and ISPs since they configure and secure BGP routing. While non-AS networks and everyday users cannot prevent incidents, they can take certain steps to minimize the impact of BGP hijacks.
Implement BGP Monitoring
Any company can deploy a BGP monitoring tool that detects unusual announcements and suspicious routing changes. Many third-party companies and ISPs offer these services, plus there are a few open-source tools, such as:
- BGPstream (uses real-time, historical, and event-driven analysis of BGP data to detect and analyze hijacks and route leaks).
- BGPalerter (monitors BGP announcements and withdrawals for specific prefixes).
- OpenBMP (collects BGP routing info and monitors peer activity).
- BGPView (provides a graphical interface for monitoring BGP routing).
- ExaBGP (monitors announcements and withdrawals, plus has a Python API that allows users to build custom monitoring solutions).
Monitoring tools continuously collect BGP routing data and gather information about announcements, including:
- Advertised prefixes.
- Originating ASNs.
- Path attributes.
BGP monitoring tools send alerts to users when they detect anomalies in routing. Users then take appropriate action, such as adjusting routing policies, blocking specific routes, or notifying upstream providers.
Use RPKI for Route Validation
Resource Public Key Infrastructure (RPKI) is a cryptographic framework that verifies the authenticity of BGP routing announcements. Based on the PKI standard RFC6480, RPKI relies on digital signatures to create Route Origin Authorizations (ROAs).
A ROA is a digitally signed object that binds an IP address prefix with an AS. RPKI allows network operators to cryptographically sign BGP route announcements and create ROAs for their IP address prefixes.
ROAs prevent the propagation of unauthorized or invalid routes via Route Origin Validation (ROV). ROV is a mechanism that validates the authenticity of route announcements by checking if they match the ROAs.
Here's a general overview of how to implement RPKI, although specific steps differ depending on your router vendor and model:
- Check if your routers support RPKI. If yes, enable the RPKI validator and configure it properly.
- Register your IP address blocks with the appropriate Regional Internet Registry (RIR). Registration is required to generate ROAs for your IP address.
- Obtain the RPKI trust anchors from the RIR. Trust anchors verify the authenticity of ROAs and ensure the integrity of the RPKI system.
- Create ROAs for your IP address blocks and submit them to the RIR.
Rely on Multiple Service Providers
Having connections with multiple ISPs leads to improved network resilience and increased redundancy. This strategy has two drawbacks, though:
- You must hire at least two ISPs, which isn't ideal for organizations with a limited budget.
- Setting up and managing networks with multiple ISPs requires significant networking know-how.
If one ISP suffers a BGP hijack (or any other network-related problem), you shift traffic to another provider. Failover and load balancing mechanisms automatically redirect traffic to the unaffected ISP, ensuring continuous and safe Internet connectivity.
Use a VPN
Using Virtual Private Networks (VPNs) is another strategy non-AS networks and everyday users employ to protect against BGP hijacks. VPNs protect data integrity and confidentiality rather than addressing the core issue of BGP hijacking itself.
VPNs create secure, encrypted tunnels for internet traffic. A VPN safeguards data as it traverses potentially insecure networks, including those affected by a BGP hijack. Since all data moving through a VPN is encrypted, files are unreadable to eavesdroppers.
Additionally, most VPNs offer access control features that allow you to restrict who can connect to your network resources. This precaution prevents unauthorized access even if a BGP hijack reroutes traffic.
Encrypting valuable data is a vital precaution and a must-have in today's cybersecurity landscape. Learn about encryption at rest, in transit, and in use.
BGP Makes the Internet Work Quickly, Not Safely
Understanding the dangers of BGP hijacking is vital for maintaining your security posture. While you cannot directly prevent hijacks, you can prepare for incidents and ensure route hijacks do not impact your network, data, or end-users. Use what you learned in this article to boost your team's ability to mitigate the impact of BGP hijacking.