Crypto malware is a significant and rapidly growing threat to the security of digital assets in the cryptocurrency ecosystem. This type of malware exploits vulnerabilities in software, hardware, and user behavior to gain unauthorized access to cryptocurrency wallets, exchanges, and mining operations. It targets individuals and organizations aiming to steal digital assets, disrupt services, or illicitly mine cryptocurrencies using compromised computing resources.
This article explains what crypto malware is, how it infiltrates systems, the forms it takes, and what strategies you can employ to protect yourself from these threats.

What Is Crypto Malware?
Crypto malware is a category of malicious software engineered to exploit vulnerabilities in cryptocurrency systems and users. Unlike traditional malware that aims to steal data or disrupt operations, crypto malware focuses on unauthorized mining of cryptocurrencies (cryptojacking), theft of digital assets, or manipulation of cryptocurrency transactions. It leverages the unique aspects of blockchain technology, digital wallets, and cryptocurrency protocols to achieve its malicious objectives.
Crypto Malware Types
Here are the primary types of crypto malware:
- Cryptojacking malware. This software covertly hijacks a user's computing resources to mine cryptocurrencies without their consent. It often operates silently in the background, consuming CPU and GPU power. Attackers deploy cryptojacking malware through drive-by downloads, malicious browser extensions, or by exploiting server vulnerabilities.
- Wallet stealers. This malware is designed to locate and extract cryptocurrency wallet files and private keys from an infected system, enabling attackers to access and drain the victim's funds. Techniques include memory scraping, process hollowing, and targeting both software and hardware wallets.
- Clipboard hijackers. These are programs that monitor a user's clipboard activity to detect when a cryptocurrency wallet address is copied. They replace the intended address with one controlled by the attacker, redirecting funds during transactions. Clipboard hijackers support multiple cryptocurrencies and use pattern matching to identify wallet addresses.
- Keyloggers. This software records keystrokes to capture sensitive information such as passwords, seed phrases, and private keys associated with cryptocurrency wallets. Keyloggers may operate at the kernel level and implement anti-analysis techniques to avoid detection.
- Ransomware demanding cryptocurrency. This is malware that encrypts a victim's files and demands payment in cryptocurrency for the decryption key, leveraging the anonymity of digital currencies. Modern ransomware uses strong encryption algorithms, deletes backups to prevent recovery, and may employ double extortion tactics by threatening to release stolen data.
- Trojanized cryptocurrency apps. These are legitimate-looking applications that contain hidden malicious code, which can perform harmful actions once installed on a device. Attackers clone popular apps, inject malicious code, and abuse legitimate functionalities to access sensitive data.
- Botnets for mining. These are networks of compromised computers orchestrated to collectively mine cryptocurrencies, significantly boosting the attacker's mining capabilities. These botnets exploit command and control infrastructures, propagate through various methods, and employ stealth mechanisms to avoid detection.
Read our article on the most common types of cyber attacks you will likely encounter in the current cybercrime landscape.

Crypto Malware Examples
Below are several high-profile instances of crypto malware. Understanding these examples helps us recognize patterns and implement preventive measures.
Coinhive
Coinhive was a JavaScript-based cryptocurrency miner that could be embedded into websites. While initially created for legitimate purposes, cybercriminals used it without user consent to mine Monero by exploiting visitors' computing resources. Coinhive scripts were injected into compromised websites or delivered via malicious ads, leading to increased CPU usage and degraded performance.
CryptoLocker
CryptoLocker was one of the earliest and most notorious ransomware strains that demanded payment in Bitcoin. It used RSA public-key encryption to encrypt users' files, storing the private key on the attacker's server. Victims were given a deadline to pay the ransom, after which the private key would be destroyed, rendering the data irrecoverable.
WannaCry
WannaCry is a ransomware cryptoworm that targeted computers running the Microsoft Windows operating system. It propagated using EternalBlue, an exploit developed by the U.S. National Security Agency (NSA) for a vulnerability in the SMB protocol. WannaCry encrypted files and demanded Bitcoin payments for data recovery, causing widespread disruption in 2017.
CryptoShuffler
CryptoShuffler is a clipboard hijacker that monitors the clipboard for cryptocurrency wallet addresses. When it detects one, it replaces it with the attacker's address, causing the user to unknowingly send funds to the criminal. CryptoShuffler targeted multiple cryptocurrencies and operated silently, distributed through Trojanized software and phishing campaigns.
Ryuk Ransomware
Ryuk is a ransomware strain that has targeted large organizations and government agencies. It is known for demanding substantial payments in Bitcoin, often exceeding hundreds of thousands of dollars. Ryuk typically gains initial access through other malware like TrickBot or Emotet, employing strong encryption algorithms and deleting backups to prevent data recovery without paying the ransom.
DarkSide Ransomware
DarkSide is known for sophisticated attacks on critical infrastructure, most notably the Colonial Pipeline in 2021. Operating as a ransomware-as-a-service (RaaS), they provide malware to affiliates who conduct the attacks. DarkSide encrypts data and exfiltrates sensitive information, threatening to publish it if the ransom is not paid.
BadRabbit
BadRabbit spread primarily in Russia and Ukraine in 2017, masquerading as an Adobe Flash installer on compromised websites. Once executed, it encrypted files and demanded a Bitcoin ransom. BadRabbit used techniques like Mimikatz for credential harvesting and propagated via SMB shares.
TeslaCrypt
TeslaCrypt targeted gamers by encrypting game-related files and demanding Bitcoin payments. It spread through exploit kits and phishing emails, using AES encryption and evolving over time with stronger methods. The developers eventually released the master decryption key, allowing victims to recover their data without paying.
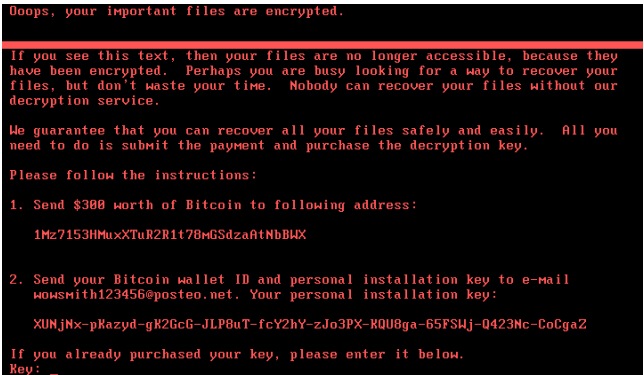
Read our article on the most famous ransomware examples of all time.
How Does Crypto Malware Work?
Below is an in-depth look at the stages of crypto malware infection.
Infection Vectors
The initial stage of a crypto malware attack involves infiltrating the target system. Attackers utilize various methods to deliver the malware payload to unsuspecting victims:
- Phishing emails. One of the most common methods involves phishing emails that contain malicious attachments or links that execute malware when opened. Attackers craft emails that appear legitimate, often impersonating trusted entities such as banks or service providers, to trick users into clicking on harmful content. These emails may use social engineering, urgent language, or threats to compel immediate action.
- Malicious downloads. Users may inadvertently install malware disguised as legitimate applications. This can occur when downloading software from untrustworthy sources, including pirated software, cracked versions of paid applications, or fake software updates. The malware is bundled with the desired software, and installation proceeds without the user's knowledge of the malicious payload.
- Drive-by downloads. Visiting a compromised website can trigger automatic malware downloads. Attackers exploit vulnerabilities in web browsers or plugins to initiate downloads without user consent. These downloads often occur in the background, leaving the user unaware of the infection.
- Exploit kits. Attackers deploy exploit kits—toolkits that automate the exploitation of known software vulnerabilities. These kits scan the victim's system for unpatched vulnerabilities in browsers, operating systems, or applications and deploy the appropriate exploits to deliver the malware.
- Network vulnerabilities. Unsecured network configurations and unpatched systems accessible over the network provide entry points for attackers. Cybercriminals scan networks for open ports, outdated services, and default credentials to gain unauthorized access and deploy malware.
Learn how to check open ports in Linux.
Execution and Persistence
Once the malware has infiltrated the system, it must execute its payload and establish persistence to maintain a foothold:
- Process injection. The malware injects its code into legitimate processes running on the system. By embedding itself within trusted processes, such as system services or common applications, the malware hides its activities and makes detection more challenging. This technique allows the malware to bypass security measures designed to monitor unauthorized processes.
- Scheduled tasks and services. To ensure the malware runs each time the system boots, it creates scheduled tasks or services that execute the malicious code at startup. By registering itself as a legitimate service or task, the malware integrates into the system's normal operation cycle.
- Registry modification. The malware alters registry keys and settings to execute during system boot. For example, modifications to the Windows Registry can specify programs that run automatically at startup. This persistence mechanism allows the malware to survive reboots and remain active over extended periods.
- Bootkits and rootkits. Advanced malware may modify boot sectors or kernel modules, allowing it to load before the operating system. Bootkits infect the master boot record (MBR) or GUID partition table (GPT), ensuring the malware is the first code executed during the boot process. Rootkits manipulate the operating system at the kernel level, providing the malware with high privileges and making removal extremely difficult.
Privilege Escalation
To perform advanced operations and access protected resources, the malware attempts to escalate its privileges:
- Exploiting vulnerabilities. The malware leverages software flaws to escalate its privileges on the system. This includes exploiting zero-day vulnerabilities—previously unknown security flaws that have not yet been patched. By executing code with elevated privileges, the malware bypasses security restrictions and accesses sensitive system areas.
- Credential theft. The malware extracts passwords and authentication tokens from memory, configuration files, or credential stores using tools like Mimikatz. Stolen credentials allow the malware to impersonate legitimate users, access restricted areas, and move laterally within the network.
Resource Exploitation (Cryptojacking)
For cryptojacking malware, the primary objective is the unauthorized mining of cryptocurrencies using the victim's computing resources:
- Mining algorithms. The malware implements code for mining cryptocurrencies, often targeting coins like Monero due to its CPU-friendly mining algorithm and emphasis on privacy. The malware utilizes the system's CPU and GPU to perform complex calculations required for mining, consuming significant processing power.
- Process hiding. To avoid detection, the malware runs mining operations under legitimate system processes. By masking its activities within trusted processes, such as svchost.exe on Windows systems, the malware reduces the likelihood of being spotted by security software or system administrators.
- Resource throttling. The malware may limit its resource usage to avoid arousing suspicion. By adjusting mining intensity based on system activity, for example, reducing mining operations when the user is active, the malware remains undetected for longer periods while still profiting from the victim's resources.
Data Harvesting
Malware designed to steal cryptocurrency focuses on collecting sensitive data necessary to access and transfer digital assets:
- File enumeration. The malware scans the system for wallet files, configuration files, and other data related to cryptocurrency storage. It searches common directories and file paths associated with popular wallet applications.
- Memory scraping. By accessing memory regions of wallet applications, the malware attempts to extract private keys and passphrases directly from the system's RAM. This technique bypasses disk encryption and can capture data that is not written to disk.
- Browser data extraction. Many users store wallet access credentials, such as passwords and seed phrases, in web browsers. The malware retrieves saved passwords, cookies, and form data from browsers to gain access to online wallets and exchange accounts.
- Database access. Some wallet applications store encrypted keys in local databases. The malware targets these databases, attempting to extract and decrypt the stored keys. If successful, the attacker gains full control over the victim's cryptocurrency assets.
Transaction Manipulation
Malware can manipulate cryptocurrency transactions to redirect funds to attacker-controlled wallets. Clipboard hijacking is a common technique used in this stage:
- Clipboard monitoring. The malware continuously monitors the clipboard content on the victim's computer. When the user copies data to the clipboard, the malware checks if it matches the format of a cryptocurrency wallet address, which is typically a long string of alphanumeric characters unique to each account. This constant surveillance allows the malware to detect when a user is preparing to conduct a cryptocurrency transaction.
- Address replacement. If a wallet address is detected, the malware intercepts it and replaces it with an address controlled by the attacker. This substitution occurs silently, so when the user pastes the address into a transaction, they are unknowingly sending funds to the attacker instead of the intended recipient. The seamless nature of this replacement makes it difficult for users to notice the change unless they double-check the pasted address.
- Dynamic address generation. To prevent security systems from blacklisting known malicious addresses, the malware generates new attacker-controlled addresses on the fly. By constantly changing addresses, the attackers make it more difficult for anti-malware solutions and monitoring services to detect and block fraudulent transactions. This tactic also hinders efforts to trace and recover stolen funds.
Communication with Command-and-Control Servers
To receive instructions, updates, and exfiltrate data, the malware communicates with the attacker's command-and-control infrastructure:
- Beaconing. The malware periodically contacts command-and-control servers to check for new commands or payloads. Communication occurs over standard protocols like HTTP, HTTPS, or even custom protocols. Beaconing intervals may be randomized to avoid detection by network monitoring tools.
- Data exfiltration. Stolen data, such as credentials, private keys, and system information, is uploaded to the attacker's servers. This data can be used for further attacks, sold on dark web markets, or leveraged for extortion.
- Domain generation algorithms (DGAs). To maintain communication even if specific domains are blocked, the malware uses DGAs to generate a large number of domain names in a deterministic manner. The attacker knows which domains the malware will attempt to contact and can register some of them to receive communications.
- Encrypted communication. The malware encrypts its network traffic to prevent detection and analysis. By using encryption protocols or custom encryption methods, the malware conceals the content of its communications from intrusion detection systems.
Lateral Movement and Propagation
Some crypto malware is designed to spread within networks, increasing its impact by infecting additional systems:
- Credential reuse. Using stolen credentials, the malware attempts to access other systems within the network. By logging in as a legitimate user, the malware can move laterally without triggering security alerts.
- Exploiting network vulnerabilities. The malware scans the network for unpatched systems and exploits known vulnerabilities to infect additional machines. This propagation amplifies the attack's reach and potential damage.
- Leveraging legitimate tools. The malware may use built-in administrative tools like PsExec or Windows Management Instrumentation (WMI) for remote execution. By using legitimate tools, the malware avoids detection by security software that looks for malicious processes.
Cleanup and Anti-Detection Measures
To remain undetected and ensure longevity, crypto malware employs various anti-analysis and anti-detection techniques:
- Code obfuscation. The malware encrypts or obfuscates its code to hinder analysis by security researchers and automated tools. Obfuscation techniques include packing, code encryption, and using polymorphic code that changes with each infection.
- Anti-debugging techniques. The malware detects if it is running in a debugging environment or being analyzed by tools like debuggers or sandbox environments. If such tools are detected, the malware may alter its behavior, exit, or execute destructive actions to prevent analysis.
- Environment checks. To avoid detection in virtualized environments commonly used by analysts, the malware checks for signs of virtualization or emulation. If a virtual machine is detected, the malware may remain dormant or terminate to avoid revealing its presence.
- Log manipulation. The malware deletes or alters system logs and security logs to erase traces of its activities. By removing evidence of its operations, the malware complicates forensic investigations and prolongs the time it remains undetected.

Why Is Crypto Malware Popular?
Crypto malware has become increasingly popular among cybercriminals due to the following factors.
Anonymity of Transactions
Cryptocurrencies provide a level of anonymity that is particularly appealing to attackers, as they are difficult to trace. Linking wallet addresses to real-world identities is a challenge, especially with privacy-focused coins like Monero, which enhance transaction privacy through features such as obfuscated addresses and ring signatures. Additionally, attackers often use mixing services, or tumblers, to further obscure transaction trails, making it even harder for law enforcement to track illicit activities.
Direct Financial Incentives
Crypto malware provides attackers with immediate monetary benefits through various methods. One approach is the direct theft of funds from wallets, which provides immediate financial gain. Another common tactic is unauthorized mining, or cryptojacking, where attackers exploit victims' resources to mine cryptocurrency, allowing them to profit without the need for upfront costs or infrastructure investment.
Low Entry Barrier
The accessibility of malware tools significantly lowers the barrier for engaging in criminal activities. Ready-made malware kits, available on underground markets, come with support and allow even less technical individuals to launch attacks. Additionally, malicious actors can exploit open-source code by modifying existing projects for nefarious purposes, further facilitating the creation and distribution of malware.
Difficulty of Recovery
Victims face significant challenges in recovering from attacks involving cryptocurrencies. Due to the irreversible nature of blockchain transactions, once funds are confirmed, recovery is highly unlikely. Additionally, attackers often operate across borders, creating complex jurisdictional issues that hinder legal actions. The lack of regulation in the cryptocurrency space further exacerbates the problem, as it provides a haven for illicit activities beyond the reach of traditional financial oversight.
Growing Cryptocurrency Adoption
The expanding cryptocurrency ecosystem presents an increasing number of targets for attackers. As the user base expands, more individuals and businesses are adopting cryptocurrencies, often with limited security awareness. High-value targets, such as exchanges and platforms that hold substantial assets, attract sophisticated attacks. Additionally, the rapidly evolving and complex ecosystem of new technologies introduces exploitable vulnerabilities, making it easier for attackers to find weaknesses in systems under constant development and deployment.
Technological Advancements
Advancements in malware development have significantly enhanced the effectiveness of attacks. Strong encryption algorithms make unauthorized decryption nearly impossible, while sophisticated evasive techniques allow malware to bypass traditional security measures. Additionally, automated attack tools powered by artificial intelligence and machine learning enable more targeted and efficient attacks, further increasing the success rate of malicious activities.
Financial Instability and Speculation
Market dynamics add to the appeal of cryptocurrency-related attacks. The rapid appreciation in value of stolen cryptocurrencies can amplify attackers' gains over time. Additionally, the speculative nature of the market allows attackers to exploit hype, luring victims into investment scams or fraudulent schemes that promise high returns.

How Can Crypto Malware Affect You?
Crypto malware has severe and multifaceted impacts.
- Financial loss. The most immediate threat posed by crypto malware is financial loss. Hackers who gain unauthorized access to your cryptocurrency wallet can transfer funds to their accounts. Detecting, containing, and recovering from an attack also incurs significant costs.
- System performance and hardware damage. Crypto malware often consumes significant computing resources, reducing system performance. In severe cases, the strain on hardware causes physical damage. Overheating and sustained high usage shorten the lifespan of components like CPUs and GPUs.
- Data breach and privacy risks. Crypto malware often opportunistically steals sensitive information, such as personal data, financial details, and login credentials. This information can be used for identity theft, fraud, or other malicious purposes.
- Security posture erosion. Attackers often leave backdoors in compromised systems, allowing them to maintain access. Crypto malware can also spread to other devices on a network, further compromising security. Compromised defenses leave systems vulnerable to additional attacks.

How Do I Know If I Have Crypto Malware?
Detecting crypto malware involves observing behavioral signs and employing technical tools. Early detection is crucial for minimizing damage.
Here are the signs of infection:
- High CPU or GPU usage. Use system monitors (e.g., Task Manager on Windows, Activity Monitor on macOS) to observe resource utilization. Unexplained spikes when the system is idle may indicate cryptojacking.
- Reduced system performance. Persistent sluggishness, crashes, or unresponsiveness despite minimal applications running.
- Overheating devices. Monitor device temperatures with tools like HWMonitor or Core Temp. Overheating is often a sign of excessive resource usage.
- Unexpected network activity. Inspect network traffic with tools like Wireshark or Netstat. Unusual outbound connections or high data usage may signal data exfiltration.
- Altered clipboard data. Verify that the pasted cryptocurrency address matches the one copied. Discrepancies may indicate a clipboard hijacker.
- Presence of unknown processes. Check running processes for unfamiliar entries consuming significant resources.
- Security software alerts. Pay attention to warnings from antivirus or anti-malware programs about detected threats or disabled features.
- Anomalous account activity. Monitor cryptocurrency accounts for unauthorized logins or transactions.
- System instability. Review system logs for recurring errors or crashes that may indicate malware interference.
How to Prevent Crypto Malware?
The following security practices significantly reduce the risk of crypto malware infections.
Implement Robust Security Software
Using reliable security software is the first line of defense against cyber threats. Installing reputable antivirus and anti-malware solutions that provide real-time protection helps safeguard systems from a wide range of attacks. Additionally, regularly updating the software's virus definitions is essential to ensure protection against the latest emerging threats.
Keep Systems and Software Updated
Regular updates are crucial for closing vulnerabilities that malware can exploit. Applying security patches by enabling automatic updates for operating systems and critical applications helps fix known vulnerabilities. Additionally, keeping browser plugins and extensions up to date, while disabling unnecessary ones, reduces the overall attack surface and enhances security.
Use Strong Authentication Methods
Enhancing authentication measures helps reduce the risk of unauthorized access. Implementing multi-factor authentication (MFA) for sensitive accounts and systems adds an extra layer of security beyond just a password. Additionally, using strong passwords and securely storing them with a password manager further protects against unauthorized entry.
Secure Network Configurations
Proper network security is essential for preventing unauthorized access. Deploying both network and host-based firewalls helps control incoming and outgoing traffic according to security policies. Implementing network segmentation separates critical systems and sensitive data from general network access, limiting the potential for lateral movement by attackers. Additionally, using virtual private networks (VPNs) secures remote access, protecting data transmission over untrusted networks.
Learn how to establish secure remote access.
Secure Cryptocurrency Assets
Protecting cryptocurrency assets requires specialized measures. Using hardware wallets provides a more secure storage option, as they are less vulnerable to malware attacks. It's also important to verify wallet software by downloading applications from official sources and checking their integrity with verified checksums. Additionally, enabling security features such as passphrase protection and keeping firmware updated on hardware wallets further enhances the safety of your assets.

How to Remove Crypto Malware?
Here are the steps to recover a system infected with crypto malware:
1. Isolate the Infected Device
Immediate isolation prevents further damage.
- Disconnect from networks. Immediately remove the device from wired and wireless networks to prevent the spread of malware and data exfiltration.
- Disable Wi-Fi and Bluetooth. Ensure all forms of connectivity are turned off to achieve complete isolation.
2. Boot into Safe Mode
Safe mode limits the malware's ability to operate.
- Restart in safe mode. Boot the system with minimal drivers and services to prevent malware from loading.
- Access recovery environments. Use system recovery options for advanced troubleshooting if safe mode is inaccessible.
3. Update and Run Full System Scans
Up-to-date tools are more effective at detection.
- Update security software. Ensure antivirus and anti-malware tools have the latest definitions, possibly updating from a clean device if necessary.
- Perform comprehensive scans. Run full system scans to detect and quarantine or remove malware.
4. Use Specialized Removal Tools
Some malware requires dedicated tools.
- Employ dedicated removal utilities. Use tools provided by security vendors designed to target specific malware strains.
- Scan with rootkit detectors. Use specialized software to detect and remove rootkits and bootkits.
5. Manually Inspect and Remove Malware
Manual inspection can catch what automated tools miss.
- Check startup items. Disable malicious entries in startup folders and registry keys.
- Analyze running processes. Identify and terminate suspicious processes using tools like Process Explorer.
- Delete malicious files. Remove malware files manually, ensuring they are not critical system files.
6. Restore System Files
Repairing system files ensures stability.
- Use system file checker (SFC). Run sfc/scannow to repair corrupted system files.
- Perform system restore. Revert the system to a previous state before the infection occurred.
7. Update All Credentials
Prevent unauthorized access with new credentials.
- Change passwords. Immediately update passwords for all accounts accessed from the infected device, starting with financial and email accounts.
- Enable multi-factor authentication. Add MFA to enhance security for important accounts.
8. Reinstall the Operating System (If Necessary)
A clean installation may be required for severe infections.
- Perform a clean installation. If malware persists, wipe the system and reinstall the OS from trusted media.
- Format drives securely. Use secure erase methods to remove all traces of malware.
9. Update and Harden the System
Prevent future infections by enhancing security.
- Apply all updates. Install the latest patches for the OS and applications.
- Enhance security configurations. Implement best practices for system hardening, including disabling unnecessary services.
10. Consult Cybersecurity Professionals
Professional assistance ensures thorough remediation.
- Seek expert assistance. Contact cybersecurity experts if unsure about the removal process or if dealing with a sophisticated threat.
- Report the incident. Notify relevant authorities or regulatory bodies as required.
11. Document and Learn
Use the experience to improve defenses.
- Record the incident. Keep detailed records of the attack and response actions for future reference.
- Improve security measures. Address security gaps identified during the incident to prevent future infections.

Crypto Malware vs. Ransomware
While crypto malware and ransomware are related, they operate differently and have distinct objectives, methods, and impacts. The table below compares crypto malware and ransomware across several vital aspects.
| Aspect | Crypto malware | Ransomware |
| Objective | Unauthorized mining of cryptocurrencies or theft of digital assets. | Encrypts data to extort victims for payment in exchange for the decryption key. |
| Gain mechanism | Exploits victims' computing resources or steals funds directly. | Demands ransom payments to restore access to data. |
| Visibility | Operates stealthily to remain undetected and maximize resource exploitation over time. | Immediately announces its presence through ransom notes and encrypted files. |
| Detection | Subtle signs like degraded system performance or unusual resource usage. | Obvious due to inaccessible files and explicit ransom demands. |
| Performance issues | Causes sluggish systems and potential hardware damage. | Not typically affected. |
| Data loss | Not typically affected. | Critical files become inaccessible, halting operations. |
| Financial loss | Indirectly, through resource consumption and possible theft of assets. | Directly, through ransom payments and costs associated with downtime. |
| Infection vectors | Phishing, compromised websites, and malicious downloads. | Phishing, remote desktop protocol (RDP) attacks, and exploit kits. |
| Persistence | Uses stealth techniques to avoid detection. | Short-term impact focused on immediate ransom. |
| Propagation | Less focused on spreading across networks. | Actively spreads across networks to maximize impact. |
| Monetization | Accumulates value over time through mining or theft. | Seeks lump-sum payments quickly. |
| Anonymity needs | Less immediate urgency in laundering funds. | High priority to avoid tracing of ransom payments. |
| Removal | Restores system performance but may not recover stolen funds. | Does not decrypt files, data remains inaccessible without the decryption key. |
| Recovery | Difficult to reclaim stolen cryptocurrency due to transaction irreversibility. | Depends on availability of clean backups or paying the ransom (not recommended). |
| Defense strategy | System hardening and resource monitoring. | Regular backups and rapid incident response. |
| Detection tools | Performance monitoring and behavioral analysis. | Advanced threat detection and network monitoring. |
Not all ransomware behaves the same. Some strains encrypt files, others block access to systems, and some threaten to release or sell the data as a form of blackmail.
Read our article on the types of ransomware to understand their common features.

Protecting Your Digital Assets from Crypto Malware Attacks
Crypto malware is a significant and evolving threat that capitalizes on the widespread adoption of cryptocurrencies. From cryptojacking to wallet stealers, crypto malware exploits vulnerabilities in systems, networks, and user behavior.
Proactive measures are critical in preventing infections. These measures include robust security software, regular system updates, user education, and a comprehensive backup strategy. Early detection through vigilant monitoring of system performance and network activity can also mitigate the impact of crypto malware.



