The Diffie-Hellman algorithm allows two or more parties to create a shared encryption key while communicating over an insecure network. Although the parties exchange plaintext data during the key generation process, the algorithm ensures that eavesdroppers cannot determine the chosen encryption key.
This article is a complete guide to the Diffie-Hellman key exchange. Jump in to learn how this algorithm works and see why a 50-year-old cryptographic strategy is still the go-to method for establishing a secure connection over an insecure channel.

What Is Diffie-Hellman Key Exchange?
The Diffie-Hellman key exchange is a protocol that allows devices to establish a shared secret over an insecure medium. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages.
Instead of generating and distributing a key to all participants, the Diffie-Hellman protocol enables each party to create the same custom key individually. At its most basic, this is a three-step process:
- Two or more parties exchange plaintext info over the network.
- The exchanged info enables participants to compute the same secret number independently.
- Each party inputs the secret number into a key derivation function (KDF) and generates a unique encryption key.
The algorithm never transmits the secret number over the network, which makes the Diffie-Hellman key exchange highly effective at preventing eavesdropping. While intruders can spy on plaintext data during the key creation process, there is not enough info to determine the key participants' plan to use during communication.
Once participants have a unique symmetric key, parties scramble all future messages. Only recipients with the appropriate decryption key can understand the content of the transmitted data.
Each time devices connect again, the Diffie-Hellman algorithm generates a new shared secret (i.e., a new symmetric key). This property aligns the algorithm with perfect forward secrecy (PFS), ensuring that past and future communications remain secure even if a malicious actor determines the key of the current session.
While relatively simple, encryption is the most effective strategy for protecting valuable files. The standard is to encrypt data at rest and in transit, but more organizations are also starting to implement encryption in use (scrambling data during active processing).
Diffie-Hellman Key Exchange vs. RSA
The Diffie-Hellman key exchange and Rivest-Shamir-Adleman (RSA) are two cryptographic algorithms that serve different purposes.
The Diffie-Hellman enables two parties who don't know each other to generate a shared key without anyone having to send the key to the other party. On the other hand, the RSA enables you to:
- Generate a public/private key pair.
- Publish the public key so anyone can encrypt messages before sending them to you.
- Be the only one capable of decrypting messages since you are the only one with the private key.
Here's a table that outlines the main differences between the Diffie-Hellman and RSA:
| Point of comparison | Diffie-Hellman algorithm | Rivest-Shamir-Adleman (RSA) |
|---|---|---|
| Main purpose | Enables secure communication over open networks without needing a pre-established secret key. | Enables secure messaging via asymmetric encryption. |
| Key methodology | Allows two parties to independently generate a shared symmetric key without directly transmitting it over the network. | Asymmetric encryption with a pair of keys: public for encryption, private for decryption. |
| Algorithmic foundation | Relies on the computational infeasibility of solving discrete logarithm problems. | Leverages the difficulty of integer factorization of numbers. |
| Perfect forward secrecy | Yes, since participants generate new shared secrets for each session. | No, since the key pair is static. |
| Authentication | Does not authenticate communication participants. | Authenticates parties involved in communication. |
| Prevalent use cases | Establishing secure connections on insecure networks. | Digital signatures, online transactions, and secure communication that require identity verification. |
Diffie-Hellman History
Before the Diffie-Hellman algorithm, all cryptographic systems using symmetric keys had to exchange the plaintext key before they could encrypt traffic. If an eavesdropper intercepted the key, the intruder could easily decrypt whatever data was moving through the network.
Whitfield Diffie, a researcher at Stanford, and Martin Hellman, a professor at Stanford, began collaborating to address this problem during the early 1970s. In 1976, the two introduced the concept of public-key cryptography in a paper titled "New Directions in Cryptography."
In this paper, Diffie and Hellman presented the idea of a key exchange protocol that allowed two or more network parties to establish a shared secret without directly exchanging the secret key. The main idea was to use a pair of mathematically related keys:
- A public key for encryption, which parties can openly share over the network.
- A private key for decryption, known only to the recipient.
The proposed algorithm relied on the mathematical difficulty of solving discrete logarithm problems. The algorithm made it computationally infeasible for an eavesdropper to determine the secret key (i.e., the private key) even if they knew the public parameters (i.e., the public key).
How Diffie-Hellman Key Exchange Works
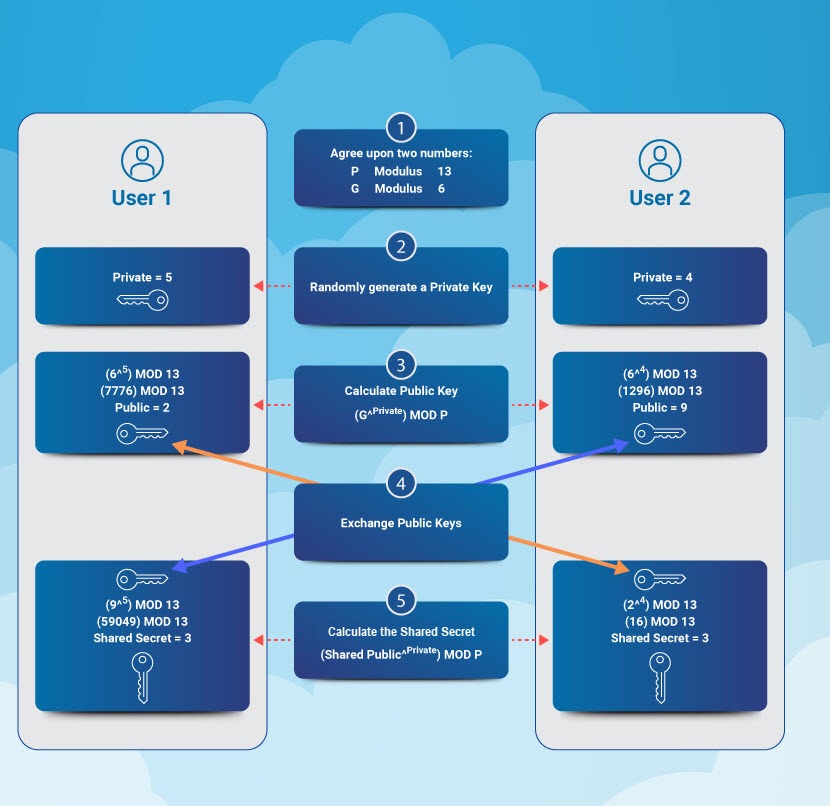
Let's say Dan and Bill want to exchange data over a potentially insecure network. The process starts with both parties publicly defining two numbers:
- The modulus (P), which must be a prime number.
- The base value (G).
In our example, the modulus (P) is 13, while the base (G) is 6. Once Dan and Bill agree on these numbers, both parties randomly generate a secret number (i.e., a private key) that they never share:
- Dan chooses a secret number (a) of 5.
- Bill selects a secret number (b) of 4.
Dan then performs the following calculation to get the number (i.e., the public key) he will send to Bill:
- A = Ga mod P
This calculation figures out the remainder after dividing the left side by the right. In our example, Dan calculates:
- A = 65 mod 13
- A = 7776 mod 13
- A = 2
Bill does the same calculation, but only for his secret number (b) of 4:
- B = 64 mod 13
- B = 1296 mod 13
- B = 9
Dan sends his public number (A) to Bill, while Bill sends his figure (B) to Dan. Dan calculates the shared secret (S) with the following formula:
- S = Ba mod P
- S = 95 mod 13
- S = 59049 mod 13
- S = 3
Bill performs the same calculation, but with Dan's public number (A) and his secret number (b):
- S = Ab mod P
- S = 24 mod 13
- S = 16 mod 13
- S = 3
Both parties end up with the same number (3), which Dan and Bill use as a basis for an encryption key. The secret number serves as input to a key derivation function, generating a unique symmetric key.
Remember that the Diffie-Hellman algorithm requires the use of exceptionally large prime numbers (P). We used a small modulus to simplify our example, but a real-life key exchange must use a prime number that's at least 2048 bits long (the binary equivalent of a decimal number with 512 digits).
Diffie-Hellman Algorithm Use Cases
The Diffie-Hellman algorithm has applications in various use cases that require secure key exchanges. The algorithm is valuable in any scenario that involves communication over a potentially unsafe channel. This key exchange is also vital where pre-shared secret keys are impossible or impractical.
Here are a few everyday use cases for the Diffie-Hellman algorithm:
- Secure internet communication. Diffie-Hellman is a fundamental component in TLS and SSL protocols. The algorithm enables secure connections between web browsers and servers.
- Remote access protocols. Remote desktop protocols often use Diffie-Hellman to establish encrypted communication channels between remote users and servers.
- Wi-Fi security. The Diffie-Hellman key exchange enables secure connections between devices and access points in Wi-Fi networks.
- Virtual Private Networks (VPNs). VPNs commonly use Diffie-Hellman to establish secure communication channels over the Internet.
- Email protection. Several email security protocols (e.g., Pretty Good Privacy (PGP) or its open standard OpenPGP) use Diffie-Hellman to ensure safe key exchanges.
- Secure messaging. Many messaging applications, including Signal and WhatsApp, use Diffie-Hellman to protect the privacy of conversations.
- Secure file transfers. SSH (Secure Shell) and SFTP (Secure File Transfer Protocol) use Diffie-Hellman for secure key exchanges when establishing a secure channel for data transfers.
- Voice over Internet Protocol (VoIP). VoIP services use Diffie-Hellman to establish secure communication channels for voice and video calls.
Learn how SFTP works and how companies use this protocol to safely transfer files between local and remote systems.
Diffie-Hellman Algorithm Advantages
The main benefit of the Diffie-Hellman algorithm is that it enables two parties to establish a shared secret key without directly transmitting it over an untrusted channel. The algorithm lowers the risk of potential eavesdroppers and enables safe use of potentially dangerous networks.
Here are a few other benefits of the Diffie-Hellman key exchange:
- Perfect forward secrecy. The algorithm aligns with PFS, so past and future communications remain secure even if someone compromises a current session's key. PFS enhances overall security posture and limits the impact of successful breaches.
- Interoperability. Diffie-Hellman is widely supported and standardized. The algorithm offers high compatibility and interoperability across different systems and platforms, enabling the implementation of key exchange in various use cases.
- High effectiveness. Despite its simplicity, the Diffie-Hellman key exchange is highly effective. The algorithm makes it computationally infeasible for intruders to determine the shared secret even if they intercept all public parameters (the base value, modulus, and two public keys).
- Simple key management. The Diffie-Hellman algorithm simplifies key management by allowing participants to distribute public keys freely.
Learn about key management best practices and see how companies ensure encryption keys stay safe throughout their lifecycle.

Diffie Hellman Algorithm Disadvantages
While the Diffie-Hellman key exchange is highly effective, the algorithm has a few must-know disadvantages. The most notable shortcomings are its lack of authentication and susceptibility to man-in-the-middle attacks:
- The Diffie-Hellman algorithm establishes a shared secret without checking the identity of the involved entities. The process requires additional mechanisms, such as digital signatures or certificates, to address this limitation.
- Since the algorithm does not authenticate participants, it's relatively simple for someone to intercept and replace public parameters. These man-in-the-middle attacks allow a hacker to intercept and connect with legitimate entities, thereby obtaining the secret key for the current session.
Here are a few more noteworthy shortcomings of the Diffie-Hellman algorithm:
- Cryptanalysis. Advancements in computing power and cryptanalysis techniques could raise concerns about the algorithm's long-term security. Quantum computing, for example, has the potential to provide enough resources to crack algorithms that use 2048+ bits long prime numbers.
- Logjam attacks. The logjam attack targets the Diffie-Hellman key exchange with weak or commonly used prime numbers. This attack leverages precomputed tables to perform a fast computation of discrete logarithms.
- Key exchange overhead. The Diffie-Hellman key exchange involves complex mathematical operations. Calculations often result in computational overhead, making the algorithm unsuitable for resource-constrained environments.
If you decide to implement the Diffie-Hellman key exchange, ensure you mandate the use of random and appropriately high prime numbers in your network security policy.
The Diffie-Hellman Algorithm Is as Effective Today as It Was in 1976
Even though it's nearly 50 years old, the Diffie-Hellman algorithm is still the preferred method for secure communication over insecure channels. While this key exchange technique has some notable limitations, Diffie-Hellman plays a crucial role in enabling various applications that require communication over potentially compromised networks.