Protecting personal and sensitive information is essential in the digital age. With cyber security attacks on the rise, businesses and individuals are constantly seeking more effective authentication methods.
Biometrics and passwords are two popular authentication methods used to verify a user’s identity and grant access to devices or accounts.
This article debates biometrics vs passwords, discusses the advantages and drawbacks of each method, and evaluates which security mechanism is safer.

What is Password Authentication?
Password authentication is a security mechanism used to verify the identity of a user before granting access to a system, application, or online service. It involves using a password - a secret combination of characters specified by the user - to prove their identity.
When a user attempts to access a password-protected resource, they are prompted to provide a password. The system compares the password to the stored password associated with that user account. If the entered password matches the stored credentials, authentication is successful, and the system grants access. However, if the passwords do not match, the authentication fails, and the user is denied access.
Password authentication relies on the assumption that the user is the only one who knows their password. It is a widely used authentication method due to its simplicity and easy implementation. However, for this authentication method to be effective, it is important to use strong passwords that are difficult to guess or crack.
Use phoenixNAP’s password generator tool to generate strong and complex passwords securely. A safe password should use at least 12 characters but the longer, the better.
What Is Biometric Authentication?
Biometric authentication is a security mechanism that uses an individual's unique biological characteristics or behavioral traits to verify their identity. It relies on the notion that these biometric features are distinctive and difficult to replicate, making them a reliable authentication method.
Biometric authentication systems capture and analyze an individual's various physical or behavioral attributes to determine their identity. Some commonly used biometric traits include:
- Fingerprint recognition. This process involves scanning and matching the unique patterns of the ridges and valleys on a person's fingertip.
- Face recognition. This method analyzes the unique facial features of an individual, such as the distance between the eyes, the shape of the nose, and the contours of the face.
- Voice recognition. Relies on the unique vocal characteristics of an individual, including pitch, tone, and speech patterns.
- Iris recognition. Uses the distinctive patterns in the colored portion of the eye, known as the iris, for identification purposes.
- Retina recognition. This technique examines the blood vessel patterns at the back of the eye, known as the retina, to authenticate a person's identity.
- Signature recognition. Involves analyzing the distinctive aspects of an individual's signature, such as the stroke order, pressure, and speed.
- Hand geometry. Measures and compares the size and shape of an individual's hand and fingers.
Biometric authentication offers several advantages over traditional authentication methods like passwords. Biometric traits are inherent to an individual and, in most cases, cannot be easily forgotten, lost, or stolen. They provide a higher level of security and convenience, as users don't need to remember or carry any additional tokens or passwords.
Biometric data contains sensitive personal information, and organizations implementing biometric authentication systems must ensure proper data security and compliance with privacy regulations to safeguard this data.
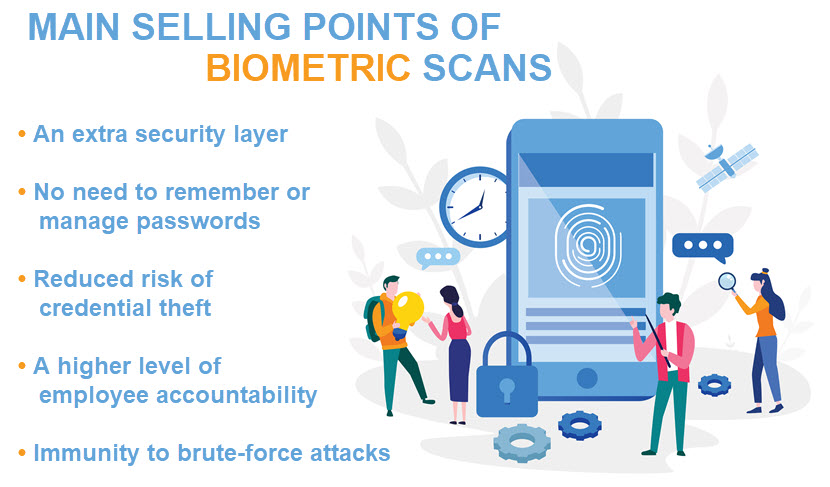
Why Are Biometrics Better than Passwords?
In general, passwords are easier to crack than biometrics. Biometrics are also better than passwords for the following reasons:
1. Enhanced Security
Biometric authentication adds an additional security layer. Furthermore, biometric traits are unique to individuals and are generally difficult to forge or replicate. Unlike passwords that can be guessed, stolen, or shared, biometrics are inherently tied to the person themselves, making it much harder for unauthorized individuals to impersonate someone else.
2. Difficult to Be Misused
Passwords can be shared or stolen, either intentionally or unintentionally. Biometric traits, on the other hand, are intrinsically linked to the account holder and are not easily transferable. It is much more challenging for someone to lend or share their biometric features with others, enhancing overall security.
3. Convenience
Biometric authentication eliminates the need to remember or manage passwords. Users don't have to worry about forgotten passwords or go through the hassle of creating and maintaining complex passwords for different accounts. Biometrics offer a more seamless and user-friendly authentication experience.
4. Resistant to Brute-Force Attacks
Biometric authentication is more resistant to traditional attack methods, such as brute-force attacks or dictionary attacks, where hackers attempt to guess or crack passwords. The uniqueness and complexity of biometric features prevent brute-force attacks, especially in multi-factor authentication setups.
5. Non-Repudiation
Biometrics provide a higher level of assurance in terms of non-repudiation. It is difficult for an individual to deny their involvement or presence when their unique biometric traits serve as evidence of authentication.
The Drawbacks of Biometrics
No authentication method is entirely foolproof. Biometric systems have their limitations, such as false positives or false negatives, and there have been cases of successful attacks on biometric systems.
Let’s consider the most significant drawbacks of biometrics:
- Data sensitivity. Biometric data is usually highly personal and sensitive information. Collecting, storing, and processing biometric data raises privacy concerns. There is a risk of unauthorized access or misuse of biometric information, potentially leading to identity theft or surveillance concerns. Organizations implementing biometric systems must adhere to strict privacy regulations and employ robust security measures to protect this data.
- Immutability. Compromised biometric data cannot be changed like a password since it’s tied to the user’s biological traits. Immutability poses a challenge in the event of a security breach or if an individual's biometric data is stolen. For the best protection against cyber-attacks, implement two-factor authentication (2FA) that combines biometrics with other authentication factors.
- Complex and costly implementation. Organizations wanting to implement biometric systems themselves may find it challenging to do so. Deploying biometric sensors or devices, integrating software, and maintaining the system requires substantial investments. Organizations should consider factors such as hardware costs, software development, system compatibility, and user enrollment processes.
- False positives and negatives. Biometric authentication may respond to a request with false positives or negatives. False acceptance occurs when the system incorrectly identifies an unauthorized person as authorized, granting them access. False rejection occurs when the system incorrectly denies access to an authorized person. Environmental conditions, variations in biometric traits over time, or weaknesses in the biometric technology used can lead to these errors.
- Social acceptance factors. Using biometric traits for user authentication may raise cultural or social concerns. Not all users want their personal biometric data stored in authentication systems. Some may even have religious, cultural, or personal objections to the use of biometric authentication. In such cases, organizations must respect the individuals’ preferences and beliefs.
- Even biometric traits change. Generally, biometric features are immutable. However, a new facial scar may confuse a facial recognition device into giving a false negative, and fingerprint scanners may not work if you have hand lotion.
Conclusion
Both biometrics and passwords offer specific advantages, with biometric authentication proving to be the safer option. However, this conversation should not focus on whether your organization should use one or the other. For the best protection, combine passwords and biometrics in multi-factor authentication systems.



