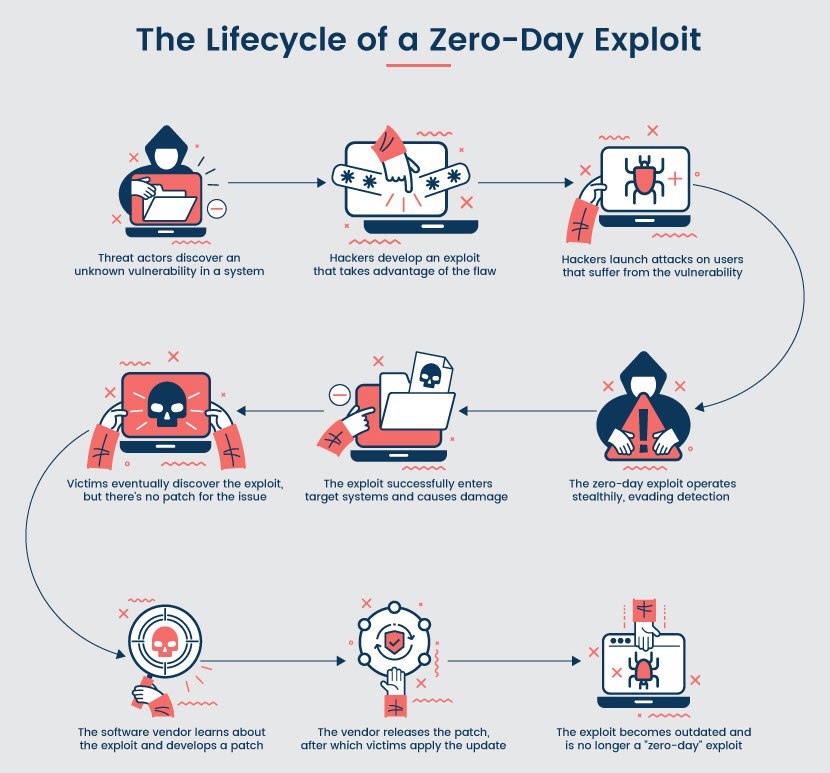
Zero-day vulnerabilities are undiscovered security flaws in IT systems. If threat actors discover such a vulnerability before anyone else, there's a chance they find an exploit to manipulate the system (e.g., gain unauthorized access, execute code, steal data, take remote control, etc.).
Meanwhile, victims have no way to stop the breach until a patch becomes available, which can take anywhere between a few days to several months.
This article is a complete guide to zero-day exploits and how companies deal with the danger of undiscovered security flaws in IT systems. We explain how zero-day exploits typically occur and present the most effective ways to prevent hackers from leveraging unknown vulnerabilities in your systems.

Our article on different types of cyber attacks provides an overview of threats you're most likely to encounter in the current cybercrime landscape.
What Is a Zero-Day Exploit?
A zero-day exploit is a method hackers use to take advantage of a software, hardware, or firmware flaw that is unknown to the team responsible for fixing the vulnerability. The term "zero-day" indicates that there's no time between the first attack and the moment the vendor learns about the vulnerability.
A zero-day exploit, vulnerability, and attack are not interchangeable terms. Here's what each of these terms represents:
- Zero-day vulnerabilities are security flaws discovered by somebody before the software vendor learns about the issue.
- A zero-day exploit is a specific technique or tactic of using a zero-day vulnerability to compromise an IT system.
- Zero-day attacks are cyberattacks that rely on a zero-day exploit to breach or damage the target system.
A zero-day exploit is typically a means to an end for a hacker. An exploit enables a threat actor to gain unauthorized access or manipulate a system, after which the criminal proceeds with the true objective (e.g., steal data, inject ransomware, set up an APT, etc.).
Almost 75% of zero-day exploits leverage memory corruption issues that enable threat actors to manipulate:
- Buffer overflows.
- Out-of-bounds read/writes.
The second most common cause (around 14%) are logic and design mistakes that allow sandbox escapes and remote privilege escalations.
In an ideal scenario, the person who discovers a zero-day vulnerability is an ethical hacker who notifies the vendor about the issue. Once the vendor is aware of the flaw, they fix the code and distribute a fix.
Users must update their systems immediately as the patch becomes available. Many fail to do so, however, so criminals typically continue to use the same exploit long after a vendor provides a patch.

What Is the Best Example of a Zero-Day Exploit?
Here are a few examples of devastating zero-day exploits from the last few years:
- In 2019, hackers exploited a vulnerability in WhatsApp's voice call feature to install spyware on user devices. As a result, attackers compromised thousands of devices, enabling them to spy on calls and messages.
- In 2020, threat actors discovered a vulnerability in Zoom that enabled them to remotely access the PC of any user running an older version of Windows.
- In March 2020, Microsoft notified its users of two zero-day exploits in the built-in Adobe Type Manager (ATM) library. Exploits targeted remote code execution (RCE) flaws and permitted attackers to run scripts and infect vulnerable devices.
- In April 2020, criminals managed to exploit an SQL injection vulnerability and target Sophos' built-in PostgreSQL database server. Attackers exploited the flaw to inject code into the database, change security settings, and install malware.
- In late 2020, threat actors used a vulnerability in iMessage to install the Pegasus spyware through a zero-click attack (i.e., an attack that requires no action from the victim). Malware granted hackers remote access to iOS devices, enabling them to steal data and listen to calls.
- In April 2021, LinkedIn discovered that threat actors compromised over 700 million user accounts via a zero-day exploit. Hackers scraped data from a public archive containing sensitive information (names, email addresses, phone numbers, job titles, etc.). Criminals sold that info on the Dark Web to anyone interested in running spamming or phishing campaigns.
- In August 2021, Microsoft urged its users to quickly install a security update with a fix for a vulnerability in the Netlogon protocol. This zero-day exploit enabled hackers to gain domain admin privileges.
Interested in in-depth analyses of real-world cyberattacks? Check out our deep dives into the 2022 PayPal attack and CommonSpirit Health ransomware attack.
How Does a Zero-Day Exploit Work?
All zero-day exploits start with the discovery of an exploitable flaw. There are two common ways threat actors discover vulnerabilities:
- Interacting and experimenting with an application.
- Buying info on vulnerabilities on the Dark Web.
Once hackers discover a flaw, they determine how to exploit the vulnerability. In most cases, this step involves the creation of malware. Hackers often perform a few proof-of-concept exploits to check whether the zero-day exploit works as expected.
The individuals possessing the exploit then decide who to target. There are two general types of strategies, depending on what exploits hackers discovered:
- Targeted attacks. Hackers discover an exploit and want to use it against a specific organization or individual.
- Non-targeted attacks. Hackers find an exploit and plan to infect as many systems as possible. Criminals typically use bots and automated scanners to identify victims with the discovered flaw.
Next, hackers infect target devices. Unless the zero-day flaw enables them to gain access, hackers turn to standard methods of infection, such as:
- Infected email attachments.
- Malicious websites that perform drive-by downloads.
- Malvertising.
- Direct network attacks.
Once hackers are inside the system, the zero-day vulnerability enables them to perform malicious activity, such as:
- Remote Code Execution (RCE).
- Injection of malicious code.
- Privilege escalation.
- Bypassing of authentication mechanisms.
- Data exfiltration (login credentials, financial data, intellectual property, etc.).
- Interception or eavesdropping of network traffic.
- Manipulation of network infrastructure.
- Establishing persistent access and backdoors.
- Remote control takeover.
The attacker continues to exploit the vulnerability until targets detect and report malicious activity, after which the vendor must patch the flaw and distribute an update. This time frame varies greatly depending on the complexity of the issue, but on average takes around 97 days.
Who Are Zero-Day Exploit Attackers?
Attributing zero-day exploits is challenging since attackers use different techniques to hide their identities, such as:
- Routing attacks through multiple compromised systems.
- Using various encryption techniques.
- Utilizing anonymization services.
Over 40% of zero-day exploits from 2020, 2021, and 2022 remain unattributed and unclaimed. Here are some common categories of zero-day exploit attackers:
- Cybercriminal individuals and groups motivated by financial gain (either by breaching targets directly or selling exploits to other hackers).
- Nation-states and private intelligence agencies that develop zero-day exploits for espionage, surveillance, or offensive cyber operations.
- Hacktivism groups that hack computer systems to promote social or political causes.
- Cybersecurity researchers who test exploits without proper authorization or for personal gain.
Ready-made exploits regularly command prices of over $1 million on the Dark Web. Another figure worth knowing is that the cost of successful zero-day attacks now averages $8.94 million if you factor in the costs of remediation, IT staff resources, the hit on end-user productivity, and data theft.
Who Are the Targets of Zero-Day Exploit Attacks?
Zero-day exploits leverage vulnerabilities in a variety of systems, including:
- Operating systems.
- Web browsers.
- Office apps.
- Network protocols.
- Anti-virus and malware tools.
- Open-source and commercial tools.
- Hardware components.
- Hardware and firmware.
- Internet of Things (IoT) devices.
Anyone using these technologies can be a target of zero-day exploits, which means anyone connected to the Internet is a potential victim. Attackers either go after a specific target or look to infect as many victims as possible:
- Targeted zero-day attacks go after potentially valuable targets (SMBs, large organizations, government agencies, high-profile individuals, healthcare organizations, technology companies, etc.).
- Non-targeted attacks target anyone with a device that contains a vulnerability. These campaigns enable attackers to gather personal data (such as passwords, credit card info, or healthcare data) or turn devices into bots for DDoS attacks.
Worried about someone using botnets to slow down or crash your network? Our DDoS server protection counters this threat with auto traffic filtering tools and near-instant infrastructure mitigation.
How Common Are Zero Day Exploits?
Estimating the number of currently active zero-day exploits is impossible since, by nature, these techniques rely on unknown vulnerabilities. The consensus is that zero-day exploits are relatively rare compared to exploits of known vulnerabilities.
In 2022, threat actors discovered and leveraged a total of 55 zero-day vulnerabilities (53 of which enabled hackers to elevate privileges or execute code remotely). That figure is lower than in the previous year (there were at least 66 different zero-day exploits in 2021), but the overall number of attacks is rising.
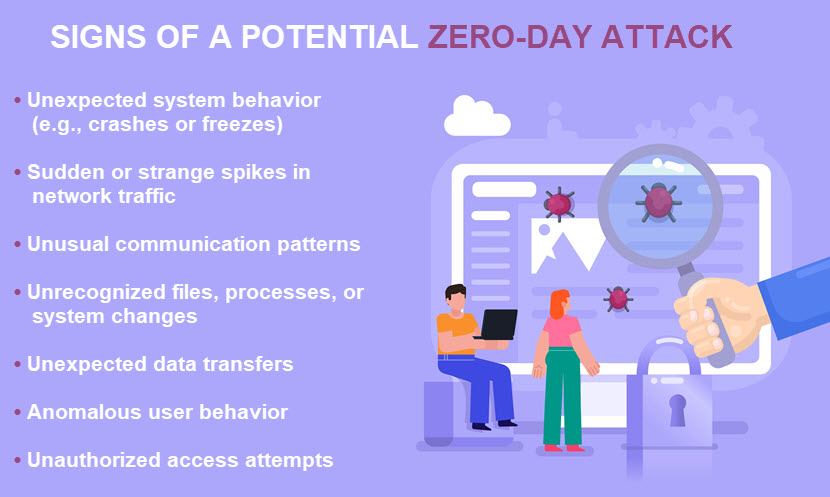
How to Detect Zero-Day Exploit Attacks?
A zero-day exploit is difficult to detect with standard anti-malware software and firewalls. Zero-day attacks do not have known signatures (patterns that enable tools to recognize threats, such as specific byte or instruction sequences), so the best way to identify an exploit is to rely on behavior analytics.
Here's how companies increase their chances of detecting zero-day exploits:
- Boost network monitoring with tools that analyze network traffic and behavior for anomalies and suspicious activity. Use an Intrusion Detection System (IDS) to identify unusual network patterns and unexpected data traffic.
- Use behavior-based analysis tools that monitor system processes, user behavior, and app activities. These tools establish a baseline of normal behavior and flag all activities that deviate from the norm.
- Improve endpoint security with tools that use behavior-based analysis, ML, and AI to detect and stop malicious activities on endpoints.
- Deploy an attack surface management (ASM) tool that continuously monitors your attack surface in search of unauthorized assets (e.g., shadow IT devices or rogue cloud instances).
Employee training also improves your ability to detect zero-day exploits. Raise your workforce's awareness of zero-day threats and educate them on social engineering techniques and safe computing practices.
Our article on security awareness training provides valuable tips on making your training sessions as engaging and impactful as possible.
What Are the Best Defenses Against Zero-Day Exploit Attacks?
Since every zero-day exploit targets an unknown vulnerability, companies cannot guard against specific exploits. There are, however, some general measures organizations take to reduce their risk levels, so here's what you should do:
- Ensure everyone at the organization applies all patches as soon as they become available. This strategy minimizes the window of opportunity for attackers to exploit recently discovered vulnerabilities.
- Set programs to auto-update (where possible).
- Deploy tools with behavior-based analytics to detect anomalies and unusual activities.
- Ensure employees never download and install software from untrusted sources.
- Set your anti-virus tool to flag out-of-date software.
- Educate employees about security best practices to minimize the likelihood of social engineering breaches.
- Implement a security scheme (e.g., Wi-Fi Protected Access 2) to boost protection against wireless-based attacks.
- Segment your network to limit an attacker's ability to move laterally and reach mission-critical parts of the network.
- Enforce zero-trust security to reduce the potential impact of successful zero-day exploits and prevent attackers from gaining excessive control or access.
- Tighten network access controls to prevent rogue machines from gaining remote access to mission-critical systems.
- Use an endpoint security tool that monitors for and responds automatically to anomalous code execution.
- Perform input validation and sanitization to prevent hackers from experimenting with input fields.
- Use IPsec (the IP security protocol) to apply in-transit encryption and authentication to network traffic.
- Consider outsourcing penetration testing services to ethical hackers to asses your system's vulnerabilities.
- Develop an incident response plan to quickly and effectively respond to zero-day exploits and attacks.
- Perform regular vulnerability assessments to discover exploitable flaws.
Remember to stay proactive with your defensive strategy. Identify weak points and blind spots before threat actors can exploit them, ensure admins have full transparency over network traffic, and never ignore patches to OSes and apps.
Take Zero Chances with Zero-Day Exploits
Despite their relative rarity compared to malware and viruses, zero-day exploits remain a considerable concern for organizations. A threat actor bypassing all defenses without alerting anyone is a recipe for disaster, which is why any security budget must have room for proactive patch management, vulnerability assessments, and behavior-based threat detection.