While firewalls and anti-virus tools still play a major role in network security, these precautions often fail to identify more advanced cyber threats. One of the most effective ways to stop threats that fall through the cracks of traditional security tools is to deploy an intrusion prevention system (IPS).
Integrating an IPS into your network adds a crucial post-firewall layer of defense that actively identifies and prevents malicious activity. Real-time threat detection and mitigation significantly reduce the likelihood of data breaches and system compromise.
This article is an in-depth guide to intrusion prevention systems, covering everything you need to know about IPSs. Read on to learn how these systems work and assess whether deploying an IPS would be a worthwhile addition to your cybersecurity strategy.

What Is an Intrusion Prevention System (IPS)?
An intrusion prevention system is a security tool that continuously monitors traffic to detect and prevent potential network threats. IPSes examine data packets for signs of suspicious behavior or known attack patterns and actively block malicious activity before it can cause any harm. Another common name for an IPS is an intrusion detection and prevention system (IDPS).
An IPS can be an application installed on an endpoint, a piece of hardware connected to the network, or delivered as a cloud service. An IPS operates "inline" on the network (i.e., within the flow of network traffic), so packets pass directly through the IPS before reaching their intended destination.
Here are the key functions of an intrusion prevention system:
- Policy enforcement. An IPS enforces security policies outlined by the security team. These policies include rules on acceptable network traffic, allowed/restricted protocols, and thresholds for abnormal activity.
- Threat detection. IPSes identify both known and novel threats using signature-based, anomaly-based, and behavior-based detection methods.
- Automated responses. Once an IPS identifies a potential danger, the system takes real-time action to stop the threat. Common responses include dropping malicious packets, blocking IP addresses, or resetting network connections.
- Logging and reporting. An IPS keeps records of all detected threats to provide insights into network vulnerabilities and attack trends.
IPSes improve security postures, while also drastically lightening workloads for security teams. The staff can focus on more complex threats and high-level security strategies, while the IPS deals with more routine dangers to network safety.
IPSes build upon the capabilities of intrusion detection systems (IDSes). An IDS reliably detects threats but does not respond to malicious activity beyond sending an alert to the security team.
Types of Intrusion Prevention Systems
There are four types of intrusion prevention systems, each designed to protect different parts of a network infrastructure. Below is a close look at every type of intrusion prevention system you can use to keep your network safe from malicious actors.
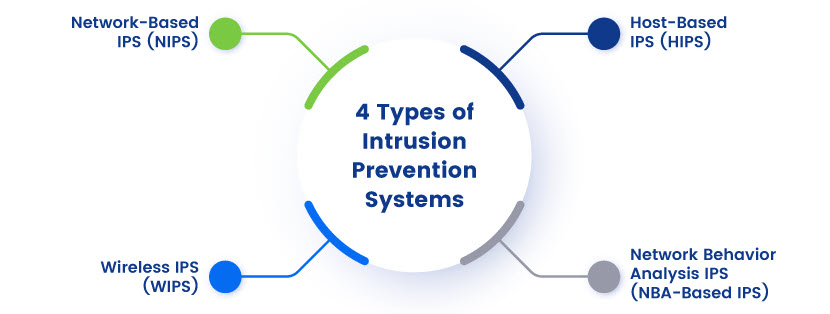
Network-Based IPS (NIPS)
A network-based IPS operates at network entry points where it monitors, detects, and blocks malicious activities in real-time. A NIPS focuses on protecting the entire network or assigned network segments.
Network-based IPSes continuously scan all incoming and outgoing packets across various network protocols, inspecting each packet for signs of:
- Known attack patterns.
- Unusual traffic behaviors.
- Poor IP and domain reputations.
- Deviations from protocol standards.
- Port-scanning attempts.
NIPSes can handle large traffic volumes, making them ideal for high-traffic networks with complex security requirements. Additionally, NIPS systems provide extensive logging and reporting, which helps security teams better analyze attack strategies and fine-tune security policies.
NIPSes are well-suited for medium to large organizations with substantial network infrastructure and access to sensitive or regulated data. This type of IPS is also the go-to choice for enterprises that require high network availability and must minimize the chance of downtime caused by cyber attacks.
Host-Based IPS (HIPS)
A host-based IPS is a security solution installed directly on individual devices (e.g., servers, workstations, mobile endpoints). While NIPSes protect an entire network from threats, HIPSes focus on securing specific devices by analyzing local system activity and file integrity.
A HIPS continuously monitors system activity, application behavior, and file changes on the host device. When it detects suspicious behavior (e.g., unauthorized file modifications, unusual process execution, abnormal access attempts), the HIPS responds by:
- Blocking the activity.
- Stopping specific processes.
- Isolating the affected device from the rest of the network.
The primary purpose of HIPSes is to enhance endpoint security. Operating directly on the host enables a HIPS to provide visibility into device-specific activity, which makes these systems effective at protecting against insider threats, malware infections, and attacks that target specific system vulnerabilities.
HIPS is ideal for organizations with high-value endpoints that require an additional layer of security. HIPSes are also beneficial for organizations that provide employees with remote access as this type of IPS helps secure devices outside the network perimeter.
Wireless IPS (WIPS)
A wireless intrusion prevention system protects wireless networks from cyber threats. WIPSes continuously monitor the wireless environment to identify and prevent security threats unique to Wi-Fi networks, such as:
- Attempts to eavesdrop on or disrupt the network.
- Unauthorized access points set up to mimic legitimate networks (so-called rogue hotspots).
- Wi-Fi-specific exploits.
- Fake networks set up by attackers to steal data (so-called evil twin attacks).
- Unauthorized device logins.
- Jamming attempts that try to disrupt Wi-Fi signals and cause service outages.
A WIPS scans radio frequencies and analyzes wireless traffic patterns to detect unauthorized access points, suspicious clients, and potential vulnerabilities. Once a WIPS detects a threat, it disconnects malicious devices or adjusts access settings.
WIPSes are ideal for companies that require protection against Wi-Fi vulnerabilities. Any organization that relies heavily on wireless connectivity would benefit from implementing a WIPS.
Network Behavior Analysis IPS (NBA-Based IPS)
An NBA-based IPS focuses on detecting and responding to unusual network behavior rather than relying on known attack signatures. NBA-based IPSes are particularly effective at catching new or emerging attack strategies.
NBA-based IPSes establish a baseline of normal network activity based on metrics like traffic volume, flow patterns, and application usage. When the system detects deviations from this baseline (e.g., unusual traffic spikes, changes in communication patterns, abnormal data transfers), it restricts the anomalous traffic flow or isolates affected parts of the network. Most NBA-based IPSes rely on machine learning (ML) to continuously improve anomaly detection accuracy and reduce the rate of false positives.
By analyzing behavior rather than looking for specific attack signatures, NBA-based IPSes identify previously unknown threats. These attacks do not follow a predictable course of action, making it impossible to identify them any other way than by detecting deviations in network activity.
NBA-based IPSes are well-suited for networks in sectors where security against emerging and complex threats is essential. Enterprises with high-risk environments or regularly dealing with sensitive data benefit the most from the unique detection capabilities of an NBA-based IPS.
Remember that achieving well-rounded network security often requires a mix of different types of IPSes. It's not uncommon for companies serious about security to invest in all four types of IPS to ensure no threat falls through the cracks.
What Is an Example of an Intrusion Prevention System?
Here are a few examples of widely used intrusion prevention systems that companies use to boost network security:
- Snort. This tool is one of the most widely used open-source IDPSes on the market. Snort is maintained by Cisco and is known for its robust rule-based detection capabilities and high levels of customization.
- Suricata. This open-source network threat detection engine is maintained by the Open Information Security Foundation (OISF). Suricata's main selling points are its standout signature and anomaly-based detection, deep packet inspection (DPI), and file extraction for malware analysis.
- Zeek. Zeek, formerly known as Bro, is a robust network analysis framework with both IDS and IPS capabilities. Zeek focuses on network behavior analysis and has an event-based scripting language for custom analysis and detection.
- Fail2Ban. This host-based intrusion prevention system protects from brute-force attacks by banning IP addresses with signs of malicious behavior. This lightweight IPS provides a customizable configuration for various services and protocols.
- OSSEC (Open Source Security Event Correlator). OSSEC is an open-source host-based intrusion detection and prevention tool that focuses on log analysis, integrity checking, and rootkit detection.
- McAfee Network Security Platform (NSP). McAfee NSP offers in-depth network traffic analysis and protects against known and unknown threats. The tool emphasizes low latency, which makes it suitable for high-speed network environments.
- Cisco Firepower. This intrusion prevention and threat detection solution is a part of the Cisco Secure Firewall lineup. Firepower provides robust threat intelligence, deep visibility, and real-time protection.
- IBM Security Network Intrusion Prevention System (XGS). IBM's XGS is a versatile IPS solution that combines signature-based detection with advanced analytics to provide enterprise-grade network security.
Looking for tools that can improve your network security? Check out our article on the market's top network security tools and see which ones are worth adding to your tool stack.
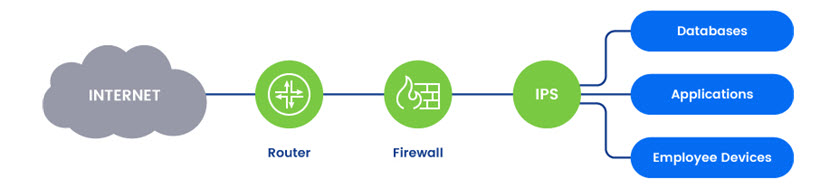
How Does an IPS Work?
An intrusion prevention system monitors, analyzes, and filters network traffic in real-time to identify and block potential threats. Most IPSes inspect the traffic that has already passed through a firewall, a strategy that lowers the load on the IPS and avoids network slowdowns.
IPSes use several detection methods to identify potential threats. Here are the most common ones:
- Signature-based detection. This method compares packets against a database of unique characteristics or behaviors associated with a specific threat. If a packet matches a known signature, the IPS flags it as malicious and blocks it from further access to the network.
- Anomaly-based detection. This method establishes a baseline of normal network behavior and identifies any deviation from that baseline that could indicate an attack. While valuable, anomaly-based detection is prone to false positives. Even benign activity, such as an authorized user accessing a sensitive folder for the first time, can trigger an anomaly-based IPS.
- Behavior-based detection. This method observes patterns in network behavior that are commonly associated with malicious activity. Common examples include repeated failed login attempts or users attempting to access their accounts from unusual locations.
- Policy-based detection. This method is based solely on security policies set by admins. Whenever the IPS detects an action that violates a rule outlined in a policy, the system blocks the activity.
Once an IPS identifies a suspicious or malicious activity, the tool responds immediately to prevent the threat from reaching its target. These responses most commonly involve dropping malicious packets, blocking IP addresses, or resetting connections.
Threat detection and remediation happen automatically, but the IPS still logs detected threats and alerts admins of what's transpired. Detailed logging provides a record of the threat's nature, origin, and time of detection. This information helps with post-incident analysis.
What Are the Advantages of Having an Intrusion Prevention System?
Implementing an intrusion prevention system offers several key advantages that enhance overall network security. Here are the main benefits of having an IPS:
- Lower risk of successful network attacks. IPSes continuously monitor network traffic for malicious activity and block threats immediately upon detection. That way, the IPS ensures that harmful traffic does not reach critical systems.
- Visibility into network activity. IPS tools provide detailed insights into traffic patterns, applications, and devices across the network. This level of visibility helps in network management, performance monitoring, and compliance reporting.
- Reduced incident response times. Automated mitigation reduces the response time for handling security incidents. Attackers and malicious programs have minimal dwell time to do damage to the network.
- Ability to detect novel attacks. Thanks to behavior-based and anomaly-based detection methods, IPSes are excellent at catching novel attacks that haven't yet been cataloged in threat databases.
- Improved compliance. Many industry regulations, like GDPR, HIPAA, and PCI DSS, mandate robust network security measures. Implementing an IPS helps meet these compliance requirements by adding an extra layer of security and providing detailed logs for audit purposes.
- Better network stability. By blocking malicious traffic, an IPS prevents harmful activities from causing issues like bandwidth overconsumption and resource overload.
- Cost savings. Reducing the number of successful breaches and mitigating incidents before they do harm helps avoid the high expenses of post-incident recovery and data losses.
- Enhanced user security. IPSes improve end-user experience by protecting against threats that cause performance issues or breaches of private user data.
Our article on the different types of network security explains what else you can use besides an IPS to keep intruders out of your network.
What Attacks Are Detected by IPS
An intrusion prevention system can identify and block a wide range of cyber attacks. Here are the main types of threats that an IPS is capable of detecting:
- Malware attacks. IPS systems detect malware (viruses, worms, trojans, ransomware, spyware, etc.) by matching known signatures or identifying unusual behavior patterns indicative of malicious software.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. An IPS prevents DoS and DDoS attacks (e.g., SYN flood, UDP flood, HTTP GET/POST flood) by identifying abnormal traffic spikes and blocking requests that attempt to overwhelm network resources.
- Exploits of known vulnerabilities. IPS systems detect malicious payloads that exploit specific vulnerabilities in software, applications, or protocols. Common examples of these attacks include SQL injections, cross-site scripting (XSS), and buffer overflow attacks.
- Man-in-the-Middle (MitM) attacks. An intrusion prevention system stops MitM attacks by detecting inconsistencies in network traffic patterns and blocking attempts to intercept or alter in-transit data.
- Unauthorized access attempts. An IPS prevents privilege escalation and lateral movement attempts by monitoring user activities and account privilege use.
- Phishing. IPSes stop phishing attacks by detecting and blocking malicious links and attachments before they reach their targets.
- Protocol anomaly attacks. An IPS detects protocol anomaly attacks (e.g., TCP/IP stack attacks or malformed packet injections) by inspecting protocol-specific traffic and blocking packets that do not adhere to the expected structure or behavior.
- Zero-day attacks. IPSes use behavioral analysis and anomaly-based detection to identify zero-day exploits that target unpatched vulnerabilities.
- Data exfiltration attempts. Intrusion prevention systems stop data exfiltration by identifying suspicious data flows and unusual outbound traffic patterns.
- Advanced persistent threats (APTs). IPSes track unusual activity over time, which helps identify stealthy APT attacks that attempt to establish a long-term presence in the network.
Want to protect your network from cyber threats? Before you start thinking about an IPS, you should first define your attack surface and understand what attack vectors malicious actors are most likely to use to breach your network.
Intrusion Prevention System Prevention Measures
When an intrusion prevention system detects a threat, it can take several immediate, automated actions to prevent harm. Here are the most common IPS prevention measures:
- Drop malicious packets. If an IPS detects packets containing malicious code or exploit attempts, the system drops these packets before they reach their intended destination.
- Block the IP address. When an intrusion prevention system detects malicious activity from a particular IP address, the IPS can block all traffic from that address. The block can be either temporary or permanent.
- Reset the connection. The IPS can reset a connection by sending a TCP reset packet to terminate the communication between the attacker and the network.
- Apply rate limiting or throttling. An IPS may apply rate limiting or throttling to reduce the flow of traffic during suspected DDoS attacks.
- Quarantine or isolate affected devices. If an IPS detects a compromised device, it can isolate that device from the rest of the network.
- Block specific applications or services. If a threat targets specific services or applications, the IPS can temporarily block access to that service to prevent exploitation.
- Prevent data theft. An IPS can block outbound traffic that appears to be part of a data exfiltration attempt.
- Redirect traffic to a honeypot. Some security teams instruct their IPS to redirect traffic to a honeypot, a decoy asset that makes the attacker think they've successfully breached the system.
Regardless of the prevention measures the APS takes, the system always sends real-time alerts to the security team. The IPS notification provides details of the threat and the steps taken to mitigate the danger. Most IPSes send these reports through an integrated security information and event management (SIEM) tool.
What Are the Disadvantages of Intrusion Prevention Systems?
Despite being a must-have for most network security strategies, IPSes present certain challenges you must know about. Here are the most notable downsides of using an intrusion prevention system:
- False positives. An IPS will occasionally incorrectly flag legitimate traffic or activity as a threat. When that happens, the system disrupts normal business operations. Frequent false positives lead to frustrated users and needless delays. Security teams may also become desensitized to alerts.
- False negatives. No IPS is 100% accurate. False negatives occur when the IPS fails to detect certain threats, typically due to sophisticated evasion techniques. When that happens, it is up to the security team to quickly identify the situation and mitigate the threat.
- Complex configuration and management. IPS systems require regular configuration and fine-tuning to be effective. Companies need skilled staff members to prevent misconfigurations from causing security gaps or network disruptions.
- High initial and ongoing costs. Enterprise-grade IPSes are expensive to purchase, implement, and maintain. For smaller organizations, the cost of an advanced IPS may outweigh its security benefits.
- Network latency issues. IPSes can cause latency if they perform deep packet inspection or advanced threat analysis on large volumes of data. Latency can affect user experience and slow down critical applications.
- Resource-intensity. IPS solutions consume significant processing resources to monitor traffic, perform analysis, and apply prevention measures in real-time.
- Interference with other security tools. IPSes sometimes conflict with other network security tools, especially firewalls and intrusion detection systems. Coordination issues between these tools can lead to gaps in coverage or redundant alerts.
Want a clear picture of how secure your network is? Check out our article on network security audits to see the most effective ways you can assess the strength of your network's defenses.
Intrusion Prevention System FAQ
Below are answers to some of the most frequently asked questions about intrusion prevention systems and their role in network security.

Where to Put an Intrusion Prevention System?
Organizations place IPSes inline with network traffic, either at the network perimeter (between the internal network and the internet) or within specific internal network segments. This placement allows the IPS to monitor, detect, and block threats before they reach critical assets.
Can IPS Be Integrated into Existing Security Infrastructure?
Modern IPS solutions often integrate with and work alongside firewalls, SIEM systems, and other security tools. Integration with SIEM systems and SOC tools allows teams to incorporate IPS alerts into broader incident response workflows.
What's the Difference Between IDS and IPS?
An IDS detects malicious programs and users, but does not take action to remedy the danger. Instead, the IDS sends an alert to admins, who then must analyze the threat and take action to mitigate the risk. On the other hand, an IPS actively blocks detected threats to protect the network.
The table below offers a more detailed comparison of IDSes and IPSes:
| Point of Comparison | Intrusion Detection System (IDS) | Intrusion Prevention System (IPS) |
|---|---|---|
| Primary Function | Monitors network traffic for suspicious activity and alerts staff in case of danger. | Monitors and actively blocks or prevents suspicious traffic. |
| Response Type | Passive (sends alerts only, after which humans must act to remove the threat). | Active (responds to threats in accordance with preset security policies). |
| Typical Deployment Location | Out-of-band (does not affect traffic flow). | Inline (directly in the path of traffic flow). |
| Latency | None or minimal. | Can introduce latency due to active traffic inspection. |
| Impact of False Positives | False positives do not impact the network as the IDS does not block any traffic. | False positives disrupt services as the IPS blocks traffic in case of a detected threat. |
Use an IPS to Keep Intruders Out of Your Network
When it comes to network security, the last thing you want your staff to be is overly reactive. Deploying an IPS enables you to take a far more proactive approach to security, one that drastically lowers the chance of malicious actors and programs making their way into your network. Use an IPS alongside a firewall and a few strategically placed IDSes to ensure a top-tier network security posture.