Computers require strict, predefined rules to exchange data accurately and consistently. These rules are called network protocols. Hundreds of protocols support various types of machine-to-machine communication, from sending emails and streaming videos to routing packets across the internet.
Learn how network protocols work and why they are the foundation of modern networking.

What Is a Network Protocol?
A network protocol is a set of rules and standards that define how devices communicate over a network. Their function is to allow computers and other devices to identify each other, establish connections, and exchange information reliably and in the correct order.
Every device, such as a server, router, or smartphone, follows a specific set of protocols to:
- Format data into packets.
- Send them across the network.
- Interpret the packets it receives.
Without protocols, devices would not know how to organize, transmit, or understand the data moving between them.
Note: Companies need a set of measures and processes to secure their network infrastructure. Learn everything about network infrastructure security and protect your organization's hardware, software, and connected devices.
What Is a Protocol Suite?
Every network protocol is designed for a specific purpose. For example, HTTPS secures communication over the web, while DNS translates domain names into IP addresses. However, not every device needs every possible protocol.
Instead, devices rely on protocol suites, collections of related protocols that work together to support a specific set of communication functions.

For instance, a web server relies on the TCP/IP suite, which includes protocols for addressing (IP), transport (TCP/UDP), and application services (HTTP, DNS, or SMTP).
In contrast, a device that operates only within a local network, like a Bluetooth printer, needs a much smaller set of protocols for short-range wireless communication. These include L2CAP for packet segmentation, RFCOMM for serial data emulation, and SDP for discovering other devices and their services.
Note: Network latency is a common problem with wireless connections. Find out how IoT Edge Computing addresses this problem by processing data closer to where it's created.
What Is a Protocol Stack?
While a protocol suite defines which communication protocols a system uses, the protocol stack determines how those protocols are organized, layered, and executed within the system.
Operating systems such as Windows, Linux, Android, and iOS include their own TCP/IP stack for internet communication. This stack implements the protocols defined in the TCP/IP suite and enables core functions like sending emails, loading websites, and connecting to other devices.
Note: The TCP/IP model is used in real-world networking, while the OSI Model provides a more structured, conceptual way to understand the same principles.
Other technologies use different protocol stacks developed for their specific functions. For example, in mobile networks, LTE and 5G devices use stacks composed of layers such as RRC, PDCP, RLC, and MAC, which manage radio signaling, control, and data transmission.
How Do Network Protocols Work?
Network protocols work together in layers. Each layer handles a specific part of the communication process, from establishing connections and managing sessions to ensuring your data reaches the correct destination safely.
When one device sends data to another through a network, the following steps occur:
1. An application on the sending device generates data, for example, an API request, file transfer, or email.
2. The information is divided into small units of data called packets. Each packet contains the raw payload and protocol-specific information such as source and destination addresses, sequencing details, and error-checking codes.
3. Packets move down through the network stack on the sending device. Each layer adds a header (and sometimes a trailer) with information relevant to that layer. For example:
- TCP adds port numbers to manage sessions.
- IP adds source and destination addresses.
- Ethernet adds MAC headers for local delivery.
This process is called encapsulation. The packet is now structured and ready to travel through the network.
4. As encapsulated packets move through the network, intermediary devices such as routers, switches, and firewalls also perform partial processing. For instance, a router decapsulates packets only to the Internet layer to read IP headers and determine where to send them next.
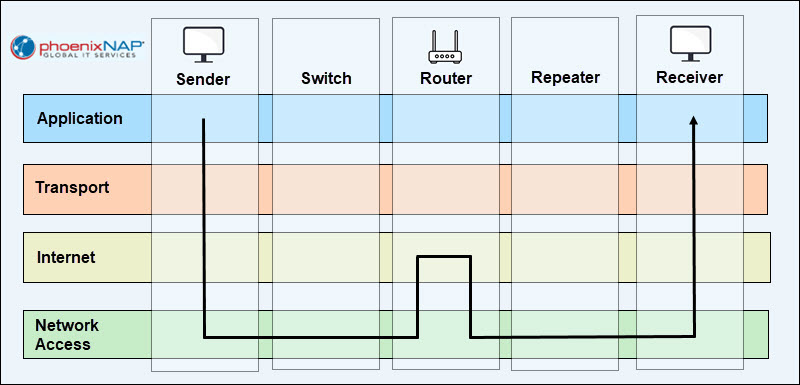
5. Once the packets reach the receiving device, they move upwards through the same network stack as on the sending device. Each layer removes its corresponding header and processes the information it contains. The process of stripping protocol information is called decapsulation.
6. After all the headers have been removed, the data is reassembled in its original form and delivered to the target application.
Encapsulation and decapsulation happen continuously during every network connection.
Types of Network Protocols
In the following section, the most common networking protocols are grouped by their primary function. Each overview includes basic details, the ports they use, and examples of how they are applied in practical scenarios.
Communication Protocols
Communication protocols specify how devices, applications, and network services should format messages, manage addressing and routing, handle errors, and synchronize timing.
Together, these rules allow devices to communicate in a standardized way, regardless of their operating system or hardware.
| Protocol | Description | Standard Port(s) | Primary Role |
|---|---|---|---|
| HTTP | The Hypertext Transfer Protocol is the basis for web communication. It defines how servers and browsers request and deliver images, web pages, and data over the internet. | 80 | Carries data during regular web browsing, as well as when applications send and receive API requests and responses. |
| HTTPS | Hypertext Transfer Protocol Secure is an encrypted version of HTTP. It uses Transport Layer Security (TLS) to protect sensitive information like payment data or passwords during data transfers. | 443 | Used by secure websites, e-commerce platforms, and online banking systems to ensure that transmitted data cannot be tampered with and remains private. |
| DNS | The Domain Name System translates human-readable domain names, like phoenixnap.com, into IP addresses that computers use to locate each other. | 53 | Resolves domain names into IPs, allowing users to access websites without memorizing numeric IP addresses. |
| DHCP | The Dynamic Host Configuration Protocol automatically assigns IP addresses, gateways, and DNS settings to devices, systems, and applications that join a network. | 67 (client) 68 (server) | Whenever a new device connects to a network, DHCP instantly assigns an IP address so you can start using the connection straight away. |
| NTP | The Network Time Protocol synchronizes system clocks with precise atomic clocks or upstream time servers. | 123 | Keeps all devices and servers on a network aligned to the same time. |
Note: If your work involves routing or connecting across multiple networks, you probably know that the BGP communication protocol has several inherent vulnerabilities. Learn more about real-world BGP hijacking cases and how to mitigate them.
Data Transfer Protocols
Data transfer protocols are used to establish connections, split large files into smaller packets, verify delivery, and reassemble data at the destination.
Their primary function is to keep data moving reliably, efficiently, and in the correct order, even over complex or unstable connections.
| Protocol | Description | Standard Port(s) | Primary Role |
|---|---|---|---|
| FTP | The File Transfer Protocol is one of the oldest protocols for transferring files between computers on a network. It does not support encryption and can only transfer plain-text files. | 20 21 | Used to upload and download files to and from servers where security is not a concern. |
| SFTP | The Secure File Transfer Protocol is an upgraded, more secure version of FTP that runs over SSH. It encrypts all commands and data before exposing them to a public network. | 22 | Used to encrypt and exchange files and manage remote directories on servers through an SSH tunnel. |
| SMB | The Server Message Block is used in Windows systems to share files and directories across a network, as if they were local resources. | 139 445 | Enables users to share files and printers in a local area network (LAN). It is required for Windows file sharing and Active Directory services. |
| TCP | The Transmission Control Protocol resends lost packets, verifies that each piece of data is intact, and keeps them in the correct order. | / | Most internet-based applications use it to support web browsing, file transfers, and sending emails. |
| UDP | The User Datagram Protocol sends packets without establishing a session or guaranteeing delivery. | / | It's primarily used for applications that prioritize speed over reliability, such as video streaming, VoIP, and online gaming. |
Note: Data is most vulnerable when moving between two network points. Find out how data in transit encryption works and how it keeps your information safe.
Security and Encryption Protocols
Security protocols protect sensitive information and ensure it cannot be intercepted, altered, or hijacked during the transfer over public networks.
They apply the following security measures:
- Encryption. Converts data into unreadable code until the receiving system decrypts it.
- Authentication. Verifies that both parties involved in the communication are legitimate.
- Integrity checks. Detects any tampering or corruption of data during or after the transfer.
Note: Explore 13 network security tools designed to help you identify, mitigate, and prevent cyber threats.
| Protocol | Description | Standard Port(s) | Primary Role |
|---|---|---|---|
| SSH | Secure Shell enables users to log in and execute commands on a remote system. It encrypts the data and authentication credentials during transit. | 22 | Administrators can use SSH commands to manage multiple remote servers and terminals from a local device. |
| TSL/SSL | Transport Layer Security is a cryptographic protocol that authenticates, encrypts, and maintains data integrity during its transmission over the Internet. | 443 993 465 | Data sent through web traffic, virtual private networks (VPNs), and email communication is encrypted in transit to maintain its confidentiality. |
| DNSSEC | Domain Name System Security Extensions adds cryptographic signatures to standard DNS responses. These signatures verify the authenticity of DNS data. | 53 | It helps DNS systems maintain their integrity and protects against DNS spoofing. |
Note: Learn about different types of network security threats, how to identify them, mitigate their impact, and stop them from happening in the first place.
Email and Messaging Protocols
Email protocols define how messages are sent, downloaded to local devices, and synchronized between email servers and client applications.
Thanks to these protocols, you can access the same message on your phone, computer, or smartwatch without delay, duplication, or loss of data.
| Protocol | Description | Standard Port(s) | Primary Role |
|---|---|---|---|
| SMTP | The Simple Mail Transfer Protocol handles outgoing emails from clients to email servers and between email servers. | 25 465 587 | Defines how emails are relayed to ensure they reach their intended recipient. |
| IMAP | The Internet Message Access Protocol allows users to read and manage emails directly on the server. As a result, messages are synchronized across connected devices. | 143 993 | Enables users to access and modify emails from multiple devices in real time. |
| POP3 | Post Office Protocol v3 downloads emails from the server, stores them on a local device, and removes them from the server afterward. | 110 995 | Users can store and access emails on their devices without an active network connection. |
Note: Read our side-by-side comparison of IMAP, POP3, and SMTP to see how they work together to support email communication.
Network and Connectivity Protocols
You can use network and connectivity protocols to monitor and control routers, switches, servers, and other networked devices. They also help diagnose connectivity issues and report network errors.
| Protocol | Description | Standard Port(s) | Primary Role |
|---|---|---|---|
| IP | The Internet Protocol is the Internet's core addressing system. It defines how data packets are structured, labeled, and routed between networks. | / | Each device is assigned a unique IP address so that other devices can find and communicate with it online. |
| ICMP | The Internet Control Message Protocol enables devices to share diagnostic information and error messages about network connectivity. | / | Supports tools like ping and tracroute to help administrators test and troubleshoot network paths and check connectivity. |
| SNMP | The Simple Network Management Protocol is used to monitor switches, routers, and servers. Agents running on networked devices send performance data and configuration details to a central system that aggregates the data. | 161 (queries) 162 (traps) | Network admins use SNMP to track device health, monitor uptime, and receive updates when issues occur. |
| Ethernet | Also designated as IEEE 802.3, this standard defines how data is formatted and transmitted over physical cables in local networks. | / | Provides stable, high-speed communication in wired local area networks (LANs). |
| Wi-Fi | The IEEE 802.11 Wi-Fi standard enables devices to connect and communicate wirelessly, using radio frequencies instead of physical cables. | / | Used to enable wireless communication between devices in a local network (WLAN). |
Note: When working in a Linux environment, you can use a variety of network monitoring and bandwidth tools to maintain a stable network, identify slowdowns, and quickly fix malfunctions.
Conclusion
You now understand how network protocols work and how they enable devices, from smartphones and servers to self-driving cars, to exchange data securely and without interruption.
Next, explore Network Topology to see how physical and logical layouts interact with these protocols to form reliable and scalable networks.