Keeping up with the latest cybersecurity trends is vital to preventing cyber attacks and data breaches. Organizations worldwide will collectively spend over $ 100 billion on cybersecurity this year, making it vital to understand the challenges your business faces to maintain a high ROI on security investments.
This article presents the most notable cybersecurity trends (although most are bound to have a significant impact beyond the current year). Jump in to learn about the latest trends in cybersecurity and see whether your IT defenses require some updating.

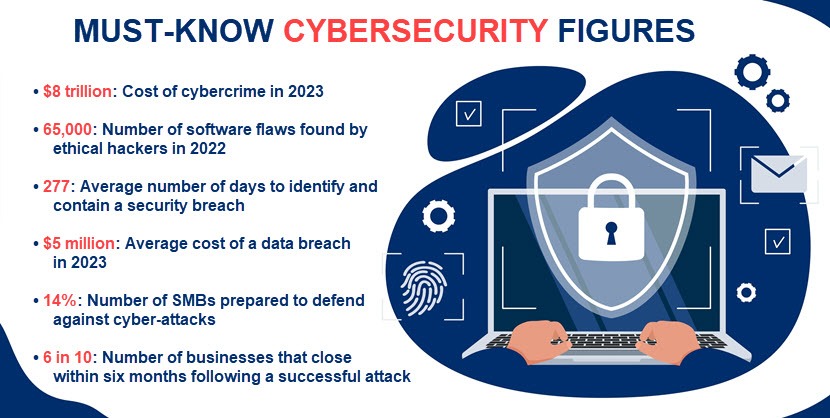
Cybercrime is now an $8 trillion "industry" expected to grow to $10.5 trillion by 2025. To put this figure into perspective, the current per-second global cost of cybercrime sits at an astonishing $255,000.
Top 12 Cybersecurity Trends in 2023
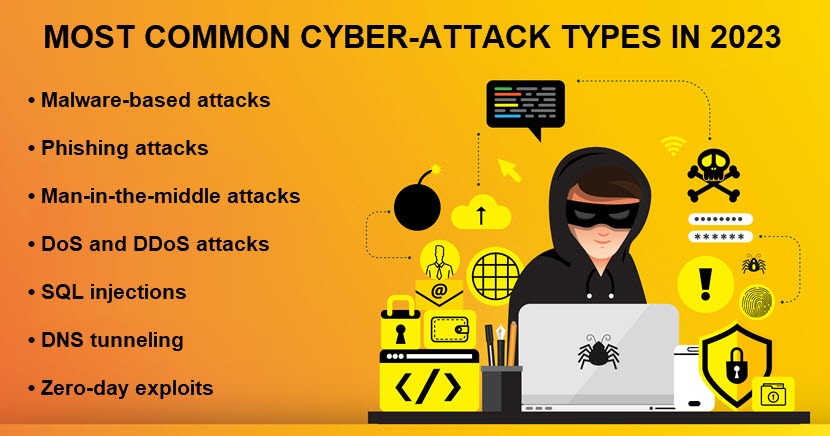
Like the previous few years, 2023 is proving to be highly busy for security teams. Below is a list of the most notable trends in cybersecurity you must account for when creating or revising a security strategy.
Human Error Remains the Leading Cause of Breaches
Approx. 74% of all data breaches in 2023 so far involved at least one human mistake. Here are a few common examples of costly employee errors:
- Failing to recognize a phishing email and clicking on a malicious link or attachment that installs malware on the system.
- Using weak passwords or reusing credentials across multiple accounts.
- Visiting an infected website that performs an unwanted drive-by download.
- Clicking on a malicious ad.
- Setting up wrong configurations of systems, databases, or cloud services.
- Losing a BYOD device that stores sensitive data.
The two most common reasons employees make mistakes are carelessness and failure to follow company policies. Here are a few go-to strategies for lowering the likelihood and impact of someone making a mistake at your company:
- Provide security awareness training to employees that explains cybersecurity best practices (e.g., password security, recognizing a phishing attack, safe browsing habits, etc.).
- Use an EPM platform to enforce strong password policies that require the workforce to use complex and unique passwords.
- Implement MFA for all systems and applications that store or access sensitive data.
- Regularly review and update privileges to ensure employees only have access to the data they need to perform their duties.
- Implement a zero-trust framework for all mission-critical data and systems.
- Boost email security to reduce the likelihood of successful phishing attacks.
- Regularly update teams on the latest cybersecurity trends and ensure everyone understands the importance of security protocols.
Use our guide to strong passwords to learn how to create impossible-to-crack passwords that are easy to remember (or use pNAP's free password generator to create bulletproof credentials instantly).
Novel Social Engineering Attacks
Social engineering attacks continue to rise yearly, and 2023 is no exception. Criminals are getting more creative, though, and there was a 135% increase in novel social engineering attacks at the start of 2023.
Here are the five currently most popular social engineering tactics criminals use to trick their victims:
- Doppelgangers: A doppelganger website is a malicious replica of another website. A criminal creates a duplicate page with a slightly different domain and "pushes" the fake website on search engines via paid ads. The goal is to get the victim to land on the fake website and try to log in, allowing the criminal to steal their credentials.
- Abuse of EDRs: Law enforcement uses Emergency Data Requests (EDRs) for time-sensitive emergencies (e.g., demanding the last known GPS coordinates for a missing person). Criminals are increasingly using fake or compromised law representatives' accounts to send EDRs and steal personal data from companies.
- Social media giveaways: Threat actors are increasingly creating fake influencer accounts on social media and posting fake giveaways. Victims click on malicious links to collect their winnings, which installs malware or enables hackers to steal data.
- Reputation ransomware: This scare tactic threatens a victim that criminals will leak news of a fictional data breach unless the victim pays a ransom. The threat is to damage the company's reputation if they refuse to meet the demands.
- Deepfakes: Developments in AI have made the technology more accessible, which has resulted in a spike in deepfake attacks. Criminals create convincing videos or audio recordings to trick victims into sharing data or paying money.
Another notable cybersecurity trend is that social engineering attacks are currently the most common type of attack on small businesses. The attacks are also becoming more targeted as criminals are taking more time to prepare before striking.
Learn more about social engineering attacks and the most effective ways of stopping criminals from tricking your employees. Also, explore the list of the most famous social engineering examples.
Ransomware Continues to Evolve
Ransomware accounts for 24% of all cyber-attacks in 2023 so far, and the global cost of this threat will likely exceed $30 billion by the end of the year. Here are the most noteworthy ransomware trends in 2023:
- Criminals are increasingly developing cloud-aware ransomware to exploit the ever-growing adoption of cloud computing.
- Many ransomware groups are adding advanced self-propagation capabilities to their variants.
- An increasing number of variants employ intermittent encryption, scrambling only parts of files to make them appear as corrupted data. Traditional anti-malware scans often struggle to detect these programs.
- Ransomware gangs are collaborating on advanced hack tools and new strategies for bypassing security measures.
- More criminals are relying on Ransomware-as-a-Service (subscription-based "service" that allows a threat actor to use a third-party tool to carry out attacks).
- We're seeing an increase in ransomware attacks targeting legacy two-factor and multi-factor authentication.
- Threat actors are continuously working on cross-platform variants capable of encrypting files on multiple operating systems.
Want to learn more about ransomware? Here's some further reading:
- How to Prevent Ransomware: 18 Best Practices
- Guide to Ransomware Detection
- How to Use Immutable Backups to Prevent Ransomware
- Ransomware Examples: 25 Most Famous Attacks
- How to Recover from a Ransomware Attack
- Malware vs Ransomware: How Do They Differ
Check out our ransomware protection services to see how pNAP helps companies protect against what's arguably the most significant threat in modern cybercrime.
Automotive Hacking
Modern vehicles use various software (cruise control, engine timing, door locks, airbags, driver assistance, etc.) that relies on Bluetooth and Wi-Fi. In 2023, we're seeing a steep spike (a growth of 225% since 2020) in hackers targeting smart vehicles.
Here are the most common goals of automotive hacking:
- Taking control over the accelerator, the brakes, and other driving operations.
- Unlocking or locking doors (typically with a fake car key fob).
- Accessing any device synchronized with the car, typically to either eavesdrop, steal sensitive data (bank info, driving records, data in-car apps, passwords, etc.), or spread malware.
- Adding the vehicle's IoT devices to a DDoS botnet.
- Hacking telematics systems used in fleets with the idea of spreading to more vehicles or infecting the company's mainframe.
Expect organizations to invest more resources into securing smart and self-driving vehicles this year. So far, encryption (at rest and in transit), advanced authentication, and real-time monitoring are the go-to prevention methods.
Note: Explore phoenixNAP's DDoS Server Protection and Mitigation services.
The Use of AI on Both Sides of the Law
The global artificial intelligence (AI) in cybersecurity market sat at $17.4B in 2022 and will reach $102.78B by 2032 (a CAGR of around 19.43%). Combined with machine learning (ML), AI has brought tremendous changes to cybersecurity. Here's how AI helps security teams:
- Analyze vast amounts of data (e.g., network traffic, logs, user behavior, etc.) to detect patterns and anomalies indicative of malicious activity.
- Detect unknown malware variants by analyzing their behavior instead of looking for known signatures.
- Automatically respond to a threat by quarantining suspicious files, isolating the compromised system, and triggering an alert for further action.
- Perform in-depth vulnerability assessments to uncover unknown weaknesses and zero-day exploits.
- Analyze email patterns, content, and metadata to block phishing attempts and other fraudulent activities.
Unfortunately, criminals also have access to AI-powered tools that enable them to design and execute more sophisticated attacks. Here are the main ways criminals are using AI in 2023:
- Developing more effective phishing campaigns.
- Launching automated attacks at scale.
- Probing and analyzing security measures.
- Testing evasion techniques.
- Identifying potential victims and gathering info about specific targets.
Expect massive advancements in how security teams and criminals use AI in the coming years. AI-powered security tools will become the industry standard, while criminals will find new, creative ways to leverage this cutting-edge tech.
The Explosion of Mobile Malware
Here are a few concerning mobile malware stats from last year:
- Almost 9% of organizations across the globe suffered a successful mobile malware attack in 2022.
- Over 18% of clicked malware-infected phishing emails in 2022 originated from mobile devices.
- Almost 58% of all company-owned mobile devices have at least one malicious URL in their browsing history.
- Over 18% of all company-owned mobile devices have at least one malware-infected app.
Cybersecurity trends in 2023 indicate no improvements in mobile malware. Kaspersky reports that its anti-virus tools blocked 4,948,522 mobile malware, adware, and riskware attacks in Q1 2023 alone (most of which were banking or ransomware Trojans).
The most common current strategy is to use so-called mobile droppers, Trojan malware that imitates an innocent app. Once installed, a dropper secretly installs malware, such as adware (malicious software that displays unwanted ads and pop-ups on the screen) or spyware (a type of malware that gathers data from the mobile device and relays it to a third party).
Last year also saw the highest rate of mobile phishing ever, with half of the mobile phone owners worldwide being targeted by a phishing attack every quarter (either through emails, vishing (voice phishing), smishing (SMS phishing), or quishing (QR code phishing)).
The most effective way to protect your staff's mobile devices is to boost endpoint security.
The Ever-Expanding IoT Attack Surface
So far in 2023, Internet of Things (IoT) devices were the most reported hardware targets for external attacks. There are a few reasons why attackers go after IoT devices so much:
- An average IoT device has weak security compared to a standard server. These devices have small computing capacity and low-power design, so most IoT machines can't support advanced authentication, encryption, or access controls.
- IoT devices often have outdated or unpatched firmware, making them a prime target for attackers seeking an unguarded gateway to other systems.
- IoT devices often collect and transmit sensitive data.
- Internet of Things devices are generally on 24/7, and many stay continuously connected to the cloud or a central system.
- Many employees create vulnerable IoT endpoints without the security team's support or knowledge (e.g., fitness trackers or digital assistants).
In 2022, there were approximately 14.3 billion active IoT endpoints worldwide. Researchers predict that the global number of connected IoT devices will increase by 16% by the end of 2023, resulting in approximately 16.7 billion prime targets for cyber-attacks.
Protecting such a vast attack surface is a challenge, so security teams in 2023 are increasingly turning towards advanced threat detection and asset management tools. Other go-to practices include proactive vulnerability assessments, disablement of unneeded devices, network segmentation, and auto-patching.
Zero-Trust Security Growing in Popularity (and Importance)
Current cybersecurity trends and risks are increasingly pushing organizations towards zero-trust security. Zero-trust systems follow the "never trust, always verify" mantra, so they constantly check, reassess, and reauthenticate users both inside and outside the network perimeter.
Two key factors are driving the speedy adoption of zero-trust security in 2023:
- The pressure to protect employees working off-site.
- The goal to reduce dependence on VPNs for secure access.
Another driving factor is that 80% of data breaches involve a poor or reused password. A zero-trust framework does not help prevent intruders from stealing credentials, but it does limit what a threat actor can do with a compromised password.
Gartner predicts that zero trust network access (ZTNA) will be the year's fastest-growing area in network security, with expected growth in adoption of 31%. Some bolder claims predict that ZTNAs will completely replace VPNs by 2025.
Cloud Computing Growing as a Go-To Target
Cloud security is the fastest-growing segment in the IT security market (growth of nearly 27% from 2022 to 2023). This market is expanding primarily due to an increasing number of risks facing cloud users. Here are the main concerns companies that use cloud resources have in 2023:
- Unpatched web services (an estimated 36% of organizations using the cloud have an unpatched web service in one of their cloud environments).
- Unsecured keys (approx. 49% of companies store access keys on a file system inside a virtual machine).
- Too many admin users (33% of businesses grant full admin privileges for more than 10% of IAM roles).
The cloud security market is also growing due to "evergreen" concerns associated with the cloud, such as:
- The increased risk of data breaches and leakages.
- Compliance violations.
- Insecure APIs.
- Misconfigurations.
- Limited visibility of how teams use cloud instances.
We're also seeing more businesses turning towards Secure Access Service Edge (SASE), a cloud architecture model that groups network and cloud-native security tech into a single cloud service.
Check out the following articles if you want to learn more about cloud security:
- Guide to Cloud Storage Security
- How to Create a Cloud Security Policy
- Data Security in Cloud Computing
- Cloud Security Tips to Reduce Security Risks
- Multi-Cloud Security Best Practices
You can also learn how we use advanced measures (segmentation controls, top-tier threat intelligence, endpoint protection, MDR, integrated backups, etc.) to ensure the safety of our Data Security Cloud.
The Risks of Remote Work
Remote work (particularly remote work at scale) continues to increase the attack surface for WFH-friendly organizations. Remote teams pose significant risks for several reasons:
- Remote work expands the attack surface outside conventional perimeter defenses (i.e., traditional intrusion detection systems (IDS) and firewalls).
- The security team cannot supervise activities on home networks.
- Working remotely often involves using an unsafe public Wi-Fi network.
- Since many workers use personal devices for work, there's an increased possibility of someone downloading malware-infected software or files.
- Remote work increases the chance of employees using unsanctioned tech and tools (so-called shadow IT).
- Remote workers often download sensitive info to their local devices, which typically lack proper security precautions.
- Working off-site increases reliance on emails, which makes employees more vulnerable to phishing.
Here's what companies do to reduce the chance of someone exploiting their remote employees:
- Utilize zero-trust security to continually reassess the validity of accounts and profiles.
- Ensure everyone uses virtual private networks when accessing enterprise systems.
- Define and enforce a strong password policy.
- Use cloud-based file sharing to keep data off worker devices.
- Ensure employees only use sanctioned apps for work.
- Ensure everyone keeps their software up to date with the latest patches (or use automated patching).
- Rely on user behavior analytics (UBA) to identify typical behavior patterns and flag suspicious activities.
Learn how to provide secure remote access for employees and maintain high levels of security when relying on an off-site workforce.
The Rise of Firewall-as-a-Service (FWaaS)
Firewall-as-a-Service (FWaaS) is a firewall solution delivered as a cloud-based service, running either as IaaS or PaaS. The FWaaS market grew from $2.32 billion in 2022 to $2.93 billion in 2023 (CAGR of 26.3%).
A cloud-based firewall works independently of the network it protects, so a FWaaS system filters internet traffic for users from any location. FWaaS also provides access to advanced firewall capabilities and outsources all admin tasks (setup, deployment, patching, etc.) to the cloud provider.
Expect FWaaS to grow in popularity in 2023 and the coming years. This firewall type is ideal for modern platforms due to its cloud-native characteristics and is an excellent option for remote or hybrid workforces.

DDoS Attacks are Becoming More Frequent and Sophisticated
Distributed Denial-of-Service (DDoS) is a type of cyber-attack in which an attacker uses a botnet to overwhelm a website or network with traffic. There's been a 300% increase in the number of DDoS incidents in the first three months of 2023 compared to the same period last year.
We're also seeing an increase in hyper-volumetric DDoS attacks, the largest one peaking at 71 million requests per second (Google's previous DDoS world record was 46 million requests per second).
Hyper-volumetric DDoS attacks leverage botnets primarily comprised of Virtual Private Servers (VPS) threat actors typically compromise by:
- Exploiting unpatched servers.
- Hacking into management consoles using leaked API credentials.
Using VPSes allows attackers to utilize significantly fewer devices for more powerful attacks than those conducted by a conventional IoT-based botnet.
Ransom DDoS attacks are also becoming more common in 2023. A criminal keeps flooding the target network or system until the victim meets the attacker's demand to pay money (typically demanded in cryptocurrencies).
Our article on DDoS prevention presents a variety of tried-and-tested methods for stopping would-be hackers from disrupting your operations.
Cybersecurity Trends: Ready to Update Your Security Strategies?
The current year is bringing a variety of new and evolving cybersecurity trends that you should consider when creating or updating IT defenses. Use this article to stay up to date with the latest risks and lower the likelihood of your organization falling victim to cybercrime.



