Businesses rely on system administrators to implement and maintain robust security measures that protect sensitive data on company servers.
Learn how to enhance the security of your systems by applying server security tips and best practices.
What Is Server Security?
Server security is a set of policies and practices designed to protect a server from all types of threats, such as DDoS attacks, brute force attacks, and careless or malicious users. These measures can include:
- Installing and maintaining firewalls.
- Enforcing strong passwords and user authentication protocols.
- Deploying antivirus software.
- Conducting regular backups to prevent data loss.
- Developing security procedures and employee training programs.
Why Is Server Security Important?
Servers play a crucial role in processing and storing business-sensitive data. Protecting servers from external threats is essential for maintaining:
- Integrity. Server security ensures the accuracy and completeness of the data stored on the server by preventing tampering and accidental modifications.
- Availability. System administrators must ensure that servers and services are consistently available to authorized users without interruptions.
- Confidentiality. The primary goal of any server security policy is to prevent unauthorized users from accessing or using sensitive data for malicious purposes.
- Reputation. Security breaches can lead to data loss or service disruption, damaging a company's reputation and causing financial losses.
- Compliance. Companies are often legally required to protect sensitive data stored on their servers. Failure to comply with these regulations can result in significant fines.
Common Server Security Issues
Some of the most common security issues stem from human error, ineffective policies, or a lack of security controls, such as:
- No encryption. Transmitting or storing sensitive data without encryption can lead to it being intercepted and read by unauthorized individuals.
- Weak passwords. Using simple or default passwords makes it easy for attackers to gain unauthorized access.
- Misconfigured firewall. Firewalls block unauthorized access and filter malicious traffic. If they are not correctly configured, they expose servers to a wide range of attacks.
- DDoS attacks. This type of attack tries to overwhelm a server with excessive traffic. The attacker aims to cause unavailability or disrupt company operations.
- Outdated software. Attackers regularly target software that has not been updated with the latest security patches to exploit its vulnerabilities.
- SQL Injection. Attackers try to exploit vulnerabilities in web applications' database queries.
- Poorly defined access controls. If user roles and permissions are not properly defined, it can lead to unauthorized access from both within and outside of the company.
- Lack of monitoring. Failing to monitor server activity closely allows potential security issues and breaches to fly under the radar.
- Malware. Viruses and other types of malware try to compromise data and system integrity.
- Ineffective backup. Lack of proper backup solutions can lead to data loss in case of an attack or hardware failure.

What Is Server (Security) Hardening?
Server hardening is a collection of steps and practices designed to reduce the server's attack surface and minimize vulnerabilities. The goal of server hardening is to create a secure environment for the server to operate in and to protect the data and services it hosts.
Effective server hardening establishes multiple security layers, including physical and software protections for the server.
How to Secure a Server: 22 Tips
The following list outlines best practices across the entire field of server security, focusing on areas where you can achieve the most significant improvements in your system's overall strength.
1. Use Secure Connections
When connecting to a remote server, it is essential to establish a secure channel for communication.
The SSH protocol is recommended for this purpose as it encrypts all data transmitted between the client and the server. Install the SSH daemon and an SSH client on your systems to securely manage servers.
Additionally, consider changing the default SSH port from 22 to a random, non-privileged port number between 1024 and 32,767. This change is one of the five best practices for secure SSH connections.
Note: You can use SSH to connect to a remote server from Windows, Linux, or macOS.
2. Set up SSH Keys Authentication
Instead of a password, you can authenticate to an SSH server using a pair of SSH keys. This method provides a more secure alternative to traditional logins, as these keys offer cryptographic strength that far exceeds typical password capabilities, such as those provided by RSA 2048-bit encryption.
The SSH key pair consists of a public and private key. The public key is installed on the server and can be shared publicly without compromising security. Anyone with the public key can encrypt data, but only the holder of the corresponding private key can decrypt this data.
The private key must be kept secure and not shared with anyone. When establishing a connection, the server verifies that the user has the private key before granting access.
3. Secure File Transfer Protocol (FTPS)
Utilize File Transfer Protocol Secure (FTPS) to transfer files securely to and from a server. FTPS encrypts data files and authentication information using command and data channels.
However, it's important to note that FTPS only protects files during transfer. Once they reach the server, the data is no longer encrypted. To add an additional layer of security, consider encrypting files before sending them.
4. Implement SSL Certificates
Secure your web administration areas and forms with SSL/TLS certificates. These certificates encrypt information passed between two systems via the internet. SSL/TLS can be used in both server-client and server-server communication.
Websites with SSL certificates display HTTPS in their URLs, indicating enhanced security. SSL/TLS protocols also ensure that clients can verify the server’s certificates, which helps establish trust.
Administrators can configure servers to recognize certificates from a centralized authority to facilitate secure and authenticated communication across networks.
5. Set up Private Networks and VPNs
Open networks are accessible to the outside world and susceptible to attacks from malicious users. By implementing private networks and VPNs, you can restrict access to selected users and reduce the risk of external attacks.
Private networks use a private IP to establish isolated communication channels between servers within the same IP range. This allows multiple servers in the same network to exchange information and data without exposure to a public space.
A VPN allows you to connect to a remote server as if you were connecting locally through a private network. Additionally, a VPN can encompass multiple remote servers. Administrators must ensure that servers within the VPN network have the same security and configuration settings to enable effective communication.
6. Monitor Login Attempts
Protect your server against brute-force attacks by using intrusion prevention software to monitor login attempts.
Intrusion prevention software oversees all log files and detects suspicious login attempts. If the number of failed login attempts exceeds a predetermined threshold, the software blocks the IP address temporarily or permanently. This automated and preemptive action protects your server against unauthorized access.
Note: Learn about public and private IP addresses in our in-depth Public vs. Private IP Address comparison.
7. Manage User Access
Every server has a root user who has administrative access and can execute any command. Given this high level of access, root accounts can be dangerous in the wrong hands. Therefore, it is a best practice to disable root login for SSH altogether.
Instead, create limited user accounts that can perform necessary administrative tasks, such as executing sudo commands. This approach minimizes the risk associated with broader access rights and helps maintain control over server operations.
8. Implement Strong Firewall Policies
Use Linux firewall tools like GUFW, an intuitive graphical user interface for managing iptables, or iptables itself to configure rules that restrict access to your server and manage incoming and outgoing traffic. For Windows servers, consider using Windows Defender Firewall with Advanced Security.
A server runs multiple services that can be categorized as public, private, or internal:
- Public services. These services usually run on web servers, allowing anyone to access them over the Internet. To isolate this traffic, ensure that your firewall rules only allow traffic for public services on HTTP and HTTPS ports (80 and 443).
- Private services. Only a select group of users should have access to sensitive services such as managing a database control panel. Configure the firewall to restrict access to these services to specific IP addresses or VPN connections.
- Internal services. The firewall must block all external access to ports used by these services and only permit connections from local network addresses.
Regularly review and update firewall settings to address new security threats and changes in network or server configurations.
9. Establish Password Requirements
Set clear password requirements and rules that all server users must follow. Follow these essential guidelines:
- Do not allow empty or default passwords.
- Enforce a minimum password length and complexity.
- Maintain blocklists of unacceptable passwords and regularly update their indexes, such as usernames and passwords that have been compromised in known security breaches.
- Implement a lockout policy after several failed login attempts.
- Avoid using reversible encryption for storing passwords.
- Enforce session timeouts for inactivity.
- Enable two-factor authentication for added security.
- Set expiration dates depending on the level of security required. For example, a password might need to be changed every few weeks or months to mitigate risks associated with long-term exposure.
10. Use Passphrases for Server Passwords
Encourage the use of passphrases for server passwords to elevate security. Passphrases are typically longer and include spaces between words, making them easier to remember and harder to crack.
For example, a password passphrase may be: Ilove!EatingPizzaAt1676MainSt.
This passphrase exceeds typical password lengths and includes a mix of upper and lowercase letters, numbers, and special characters.
Note: Use the phoenixNAP password generator tool to generate strong and complex passwords.
11. Password Don'ts
To maintain a secure server, employees need to avoid the following:
- Writing passwords on paper or storing them in an unencrypted digital format.
- Using personal information like birthdays, hometowns, and pet names, which can be easily guessed or traced.
- Creating passwords that contain simple dictionary words, as these are particularly vulnerable to dictionary (brute force) attacks.
- Repeating sequences of characters in the same password.
- Using the same password for multiple accounts. Recycled passwords significantly increase risk. Create a different password for every account and manage them with a password manager like KeePass.
Note: Check out our article on strong password ideas to better understand how to create and use passwords that are hard to crack.
12. Update and Upgrade Software Regularly
Keep your server software up to date to protect against vulnerabilities found in older versions. Regularly update your server control panel, content management systems, and associated plugins.

Consider enabling automatic updates to ensure you don't miss important updates and patches and that they are applied promptly. To avoid potential disruptions, test new updates in a controlled environment before deploying them to production.
13. Remove or Turn off All Unnecessary Services
Reduce your server's attack vector by enabling only the network ports the server OS and installed components require.
For a Linux operating system, opt for a minimal installation that includes only essential packages, such as core system utilities and security tools. Since most Linux distributions are configured to listen for incoming connections on the internet, it is vital to configure a firewall that allows only specific ports and denies all other unnecessary communications.
Before installing new software on your system, check for dependencies to ensure you are not adding anything unnecessary. Additionally, inspect which dependencies are auto-started on the system and determine if they are warranted.
14. Back up Your Server
Store encrypted backups of your critical data offsite or use a cloud data backup and restore solution.
Whether you have automated backup jobs or do them manually, performing regular backups must become a routine precautionary measure.
In addition, you should perform comprehensive backup tests to maintain data integrity. These tests, including sanity checks in which administrators or end users verify the accuracy of data recovery, add a layer of reliability to your backup systems.
15. Hide Server Information
Minimize the information your server discloses about its underlying infrastructure. For example, you can remove or customize HTTP headers that web servers send with each request. These headers often reveal specific versions and software types running on your server, which could aid attackers.
The less information attackers know about your system, the less likely they are to exploit specific weaknesses.
16. Use Intrusion Detection Systems (IDS)
An Intrusion Detection System (IDS) detects unusual activities that could indicate a security breach or an ongoing attack. Implement an IDS to continuously monitor and analyze network traffic for signs of unauthorized activities and potential threats on your server.
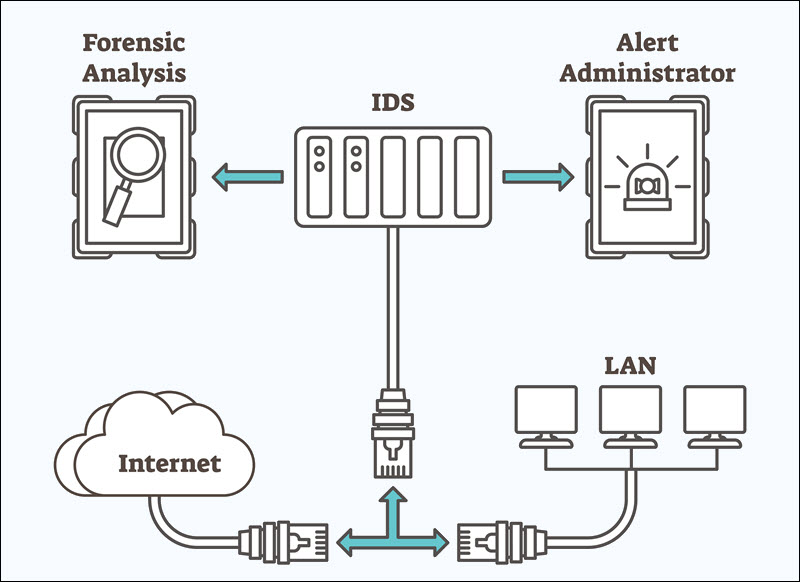
Configure the IDS to perform regular, automated scans of day-to-day operations. Additionally, integrate IDS alerts with your security management system to reduce response times when threats are detected.
17. File and Service Auditing
Audit files and services regularly to detect unauthorized changes or suspicious activity. File auditing creates a baseline snapshot of a system's optimal state and regularly compares it to its current state to identify unauthorized changes.
Service auditing assesses what services are running on the server, the protocols they use, and the ports they communicate through. These details are essential for understanding and effectively reducing vulnerabilities across the system's attack surfaces.
18. Create Multi-Server Environments
Instead of keeping all or several services on a single server, deploy individual isolated machines for different purposes. Separating database servers from web application servers, for example, is a standard practice that allows system administrators to minimize the attack surface for each server and configure server settings separately.
Using dedicated or bare metal servers that do not share resources with other machines provides maximum security. While this approach offers the highest level of security, it is also the costliest.
19. Create Virtual Isolated Environments
Smaller businesses often find complete isolation with dedicated server components an expensive prospect. Total isolation is usually unnecessary except in industries that need to comply with strict data protection laws and regulations, such as finance or healthcare.
As an alternative, consider setting up virtual isolated environments using virtual machines (VMs) or containers. These cost-effective and scalable environments contain breaches within a controlled space, preventing them from spreading across the network. Tools like Docker for containers and Proxmox or Hyper-V for VMs can help you create and manage these isolated environments.
Another option for virtualized environments in UNIX operating systems is creating chroot jails. Chroot isolates a process from the central operating system's root directory, allowing it to only access files within its directory tree. However, this is not complete isolation and should be implemented alongside other security measures, such as firewalls and access controls.
20. Run Comprehensive Security Audits
Conduct security audits to assess whether your security policies and practices are effective. It is a good idea to hire third-party security experts or consultants to conduct these audits and help you identify security vulnerabilities and gaps.
Security audits need to be comprehensive and cover both digital and physical security measures and practices. This includes access controls, network security, data encryption, and surveillance and intrusion detection systems.
21. Employee Training and Awareness
Predictable patterns in human behavior are the weakest link in security infrastructure. Employees should understand common threats, such as phishing and social engineering, and how their behavior might assist or prevent these attacks.
Train staff to recognize potential threats and adhere to strict security procedures. Provide access to online and in-person training courses and regularly update the material to reflect the latest developments in fraud prevention.

Analyze employee reactions to both simulated and actual attacks and adjust procedures to improve security measures and response strategies accordingly.
22. Leverage AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have captured the attention of both the public and IT professionals over the past year. Larger companies are already leveraging these technologies to improve server security by enabling more proactive and nuanced threat detection and response.
Unfortunately, malicious parties also use machine learning algorithms to overwhelm or bypass traditional server security tools and practices. Businesses can use AI and ML tools to analyze vast amounts of data and identify threat patterns and anomalies that elude traditional security measures.
These technologies can also automate responses to security incidents, such as isolating affected systems, blocking suspicious IP addresses, and temporarily restricting access to sensitive data.
Server Security Checklist
Download the Server Security Checklist in PDF format. This one-page reference sheet allows you to systematically address the various aspects of server security and protect your systems and data.

Conclusion
By reading and applying the tips and practices outlined in this article, you have significantly enhanced the security of your server infrastructure.
To stay up-to-date with best practices on cyber security, follow relevant Cyber Security Blogs and industry leaders through popular security podcasts.

