Kali Linux is a security-oriented Linux distribution for penetration testing and digital forensics. Based on the Debian Testing branch, Kali Linux offers a balance between stability and offering the most up-to-date software.
This overview presents the 25 best Kali Linux tools chosen from over 600 tools available in the distribution.

Nmap
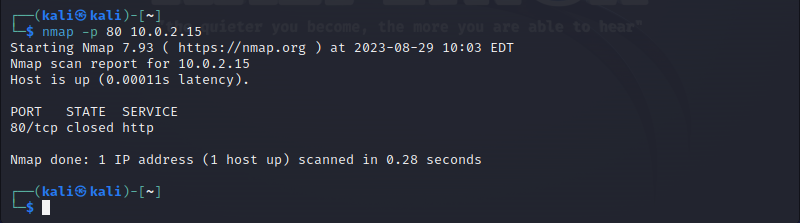
Nmap is a command-line network scanning utility for discovering and mapping networks, hosts, and services. It helps users perform network vulnerability assessments and improve network security.
Nmap works by sending data packets to a specified port and IP address. It waits for a response, analyses it, and provides a report.
Features
- Network hosts identification by protocol or port.
- Ping scan for host testing.
- Fast scan for quick port scanning.
- TCP/IP stack fingerprinting determines a network device's OS and hardware elements.
Pricing
Nmap is a free and open-source application.
Netcat
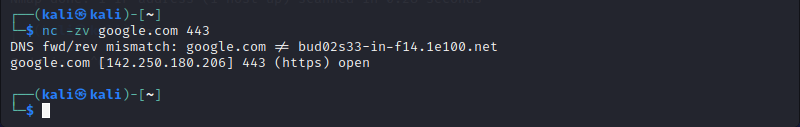
Netcat is a command-line utility that allows users to read and write data across network connections. It scans and listens to ports and transfers files using TCP and UDP protocols.
The tool facilitates debugging and investigation, but developers can include it as a backend for their programs and scripts. Netcat syntax includes various options for communicating and analyzing external websites and their ports.
Features
- TCP/UDP connections using any port.
- Port scanning with randomization.
- Full DNS forward and reverse checking.
- Usage of locally configured source port or network source address.
- Loose source-routing.
- TCP/UDP tunneling mode.
Pricing
Netcat is free of charge and open-source.
Fluxion
Fluxion is a tool for security auditing and researching user responses to social engineering attacks. It can conduct Wi-Fi access point attacks by providing a simple interface for setting up fake wireless networks.
Aside from the social engineering aspect, security professionals also use Fluxion to test the access point security of wireless networks by simulating Man in the Middle (MITM) attacks.
Features
- Handshake Snopper and Captive Portal for simulating an MITM attack.
- Evil Twin attacks.
- Credential harvesting.
- De-authentication attacks.
Pricing
Fluxion is a free and open-source tool.
Lynis
Lynis is a system hardening and compliance testing tool that performs comprehensive system health scans. Aside from IT security professionals, developers use Lynis to improve web application security, while sysadmins utilize it to discover new weaknesses.
Lynis uses an opportunistic and modular approach to scanning, meaning it can scan for available system tools and then perform a tailor-made system test. This approach allows Lynis to require no dependencies to run.
Features
- Over 300 built-in tests.
- Plugin and custom test support.
- Dynamic operating system detection.
- Detailed logging.
- Hardening index.
Pricing
Lynis is a free-of-charge and open-source application. There are also two SaaS offers for Lynis:
- The Premium includes all the modules and a monthly subscription.
- The Self-Hosted option allows users to customize the offer to meet their needs.
Nessus
Nessus is a comprehensive vulnerability assessment tool for identifying vulnerabilities, misconfigurations, and potential threats in systems and applications. It offers an extensive database of regularly updated vulnerability checks for up-to-date security assessment.

Features
- Fast asset discovery.
- Configuration auditing.
- Discovery of sensitive data.
- Malware detection.
Pricing
Nessus is a commercial product that offers three versions:
- Nessus Essentials is a free version that enables users to scan their environment with up to 16 IP addresses per scanner.
- Nessus Professional is a paid annual subscription option that offers all the essential modules.
- Nessus Expert annual subscription includes the Nessus Professional features and additional features such as external attack surface scanning, prebuilt scanning policies, and cloud infrastructure scanning.
Tiger
Tiger is a command-line tool written in shell language that performs security auditing and host-side intrusion detection. It can also provide a framework for combining other tools, like intrusion detection systems, integrity checkers, and logcheckers.
The modular nature of the tool allows users to decide which aspect of a UNIX system they want to check. For example, Tiger can check filesystem permissions, dormant users, and system file configuration. It can also scan for available patches not installed on the system.
Features
- Easily expandable modular design.
- Wide range of available checks.
- Highlights vulnerabilities in password policies, system logs, and network settings.
Pricing
Tiger is a free and open-source tool.
John the Ripper
John the Ripper (also known as John) is a password-hacking tool with a simple command-line interface. Cyber-security professionals use it for password security auditing and password recovery.
Features
John the Ripper supports many different hash and cipher types, such as:
- User passwords for Linux, BSD, macOS, and Windows users.
- User passwords for web apps and database servers.
- Network traffic captures.
- Encrypted private keys.
- Filesystems, documents, and archives.
Pricing
While the application is free, there are paid John the Ripper Pro versions tailored for many operating systems. The licensing and prices depend on the OS and the type of package.
Hydra
Hydra is a password-cracking tool that supports parallelized connects and attacks on multiple protocols. It combines various types of brute-force attacks for guessing the username/password pair.
Penetration testing experts often use Hydra with wordlist generators such as cupp and crunch.
Features
- Support for multiple protocols such as FTP, SSH, POP3, and IMAP.
- Support for website forms.
- Modular architecture.
- Dictionary-based and brute-force attacks.
- Parallel attacks.
- Support for custom scripts.
Pricing
Hydra is a free-to-use open-source tool.
Social-Engineer Toolkit (SET)
Social-Engineer Toolkit (SET) is a penetration testing kit for social engineering research written in Python. It allows security professionals to create a believable social engineering attack using custom attack vectors.
SET helps security professionals evaluate how susceptible organizations and individuals are to phishing, credential harvesting, and manipulation.
Features
- Support for various attack vectors (e.g., spear phishing, credential harvesting, etc.).
- Infectious media generation.
- Phishing website creation.
- Email-based attacks.
- Malicious USB device creation.
Pricing
Social-Engineer Toolkit is open source and free of charge.
WPScan
WPScan is a tool for detecting vulnerabilities, misconfigurations, and security issues in WordPress websites. It checks a manually updated database of WordPress vulnerabilities and reports on the state of a website.
WPScan can be integrated into a WordPress installation or used as a CLI tool. The CLI tool has a simple interface featuring the wpscan command:
Features
- Scanning outdated plugins, themes, and core files.
- Security checks for weak passwords, exposed sensitive information, and potential entry points.
- Version checks for the WordPress installation and plugins.
- Brute-force attacks for login credentials testing.
Pricing
The CLI version of WPScan is free of charge but limited to 25 API requests per day. The Enterprise edition is a paid option with custom solutions for enterprises.
Metasploit Framework
Metasploit Framework is a penetration testing system and a platform for creating security tools and exploits. It allows the user to perform all the necessary steps to create and deploy an exploit inside a single environment.
Metasploit facilitates writing, testing, and executing the exploit code. It supports actions such as exploit module configuration, pairing the module with the payload, and launching the exploit towards the target system.
Features
- Extensive database of exploits, payloads, and auxiliary modules.
- Supports various exploits, from remote code execution (RCE) to privilege escalation.
- Numerous security assessment options.
- Simple creation of custom exploits and payloads.
- Post-exploitation modules for reconnaissance, data extraction, and lateral movement in the exploited system.
Pricing
Metasploit Framework is open source and free to download but provides only the essential features. The company also offers a paid option called Metasploit Pro with additional advanced features.
Burp Suite
Burp Suite is a platform for discovering vulnerabilities and security testing of web applications. The suite automates repetitive tasks in every test and allows users to dive deeper with manual and semi-automated testing tools.
Burp Suite aims to provide an all-in-one solution for testing web application security. It provides the basic functionality through acting as a proxy server, scanner, and intruder, but can also work as a repeater, a decoder, a sequencer, and a comparer. The paid versions offer additional roles, such as an extender and a spider.
Features
- Smart automation.
- Support for HTTP/2-based testing.
- Out-of-band application security testing (OAST) that minimizes false positives.
- Scanning single-page applications (SPAs) and APIs.
- Prerecording of complex authentication sequences.
Pricing
Burp Suite Community Edition is free of charge but has a severely limited feature set. The Professional and Enterprise editions can be purchased after a trial period.
Aircrack-ng
Aircrack-ng is a Wi-Fi security tool for wireless network security assessment that helps the user discover, capture, and analyze Wi-Fi network traffic. It contains a detector, a packet sniffer, a password cracker, and a wireless LAN analysis tool.
Features
- Cracking WEP, WPA/WPA2 and WPA2 keys.
- An injector and frame replay tool that supports de-authentication attacks.
- Packet sniffer.
- Wireless card server.
- Virtual tunnel interface creator.
- Automated WEP cracking WPA handshake logging.
Pricing
Aircrack-ng is a free-of-charge, open-source application.
Nikto
Nikto is a vulnerability scanner for assessing the security of web servers and applications. It scans web environments for potential vulnerabilities, misconfigurations, and security risks.
As a command-line tool, Nikto features the nikto command, which takes IP addresses and domain names as arguments. After analyzing the server behind the address, the tool returns a detailed report featuring basic information about the target and a list of potential vulnerabilities.
Features
- Identifies outdated software, misconfigured servers, and security issues.
- Scans and identifies over 6700 dangerous files and CGIs.
- Full SSL support.
- Full HTTP proxy support.
- Scans a port by using an Nmap file as input.
Pricing
Nikto is free of charge and open source.
Autopsy
Autopsy Forensic Browser is a comprehensive digital forensics tool for extracting and analyzing information from digital devices and data sources. Widely used by forensic professionals and law enforcement agencies, Autopsy provides a way to examine and recover evidence from various file systems.
Autopsy is installed via the CLI and accessed through a web interface.
Features
- Uncovering hidden or deleted information.
- Powerful keyword search capabilities.
- Timeline analysis provides insights into user activity.
- Integrated hash databases for file integrity verification.
- Hash filtering for flagging known bad files.
- Support for various data types.
Pricing
Autopsy is open-source and free to use.
King Phisher
King Phisher is a tool for simulating and executing phishing campaigns designed to test and promote security awareness. It helps organizations evaluate how susceptible they are to phishing attacks.
King Phisher can be used for anything from simple awareness training to a complex campaign that illustrates the dangers of credential harvesting. Its flexible architecture gives the user control over emails and the content on the server.

Features
- Support for simultaneous phishing campaigns.
- Landing page credential harvesting.
- Web page cloning.
- Integrated Sender Policy Framework (SPF) checks.
- Emails with embedded images.
- Two-Factor authentication.
Pricing
King Phisher is free of charge and open-source.
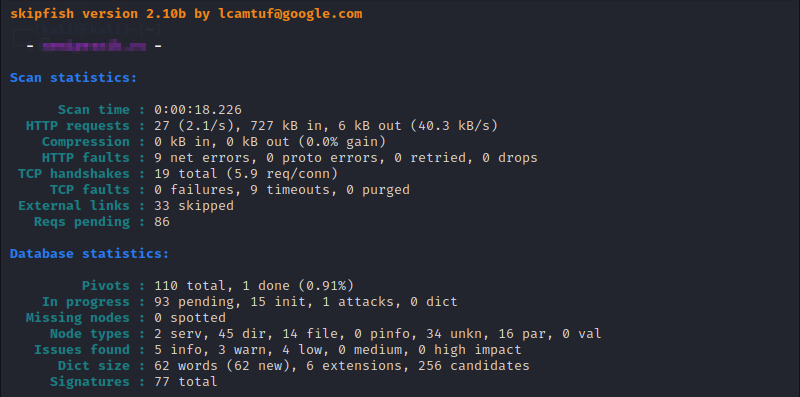
Skipfish
Skipfish is a tool for web application security assessment. It helps conduct security reconnaissance by carrying out a recursive crawl and dictionary-based probes and creating an interactive map of the target website.
The user initiates a Skipfish scan by providing a target website through its command-line interface.
Features
- Modular design and customizable options.
- Range requests, content compression, and keep-alive connections.
- Forced response size limiting.
- Enumeration tracking.
- Identifying potential vulnerabilities, such as SQL injection and cross-site scripting (XSS).
Pricing
Skipfish is an open-source application, and it is free to use.
BeEF
Browser Exploitation Framework (BeEF) is a platform for testing security and assessing the vulnerability of web browsers. It identifies exploitable browser weaknesses and helps users to design adequate web application defenses.
BeEF works by hooking a web browser and using it as a beachhead (i.e., an attack point) for executing directed command modules and other related attacks. This action enables the security expert to take limited control over the end user browser tab and conduct a test attack.

Features
- Targeting vulnerabilities such as cross-site scripting (XSS) and HTML injection.
- Targeting browser-specific weaknesses with custom browser-based attacks.
- The extension API and restful API.
- Keystroke logging.
- Browser proxying.
- Metasploit integration.
- Plugin detection.
Pricing
BeEF is a free and open-source tool.
Wireshark
Wireshark is a packet-analyzing tool for network troubleshooting and analysis. The tool can capture and analyze network traffic in real time, or it can analyze previously captured packets. The analysis offers insights into network behavior and facilitates diagnostics and identification of potential security threats.
The main Wireshark application is GUI-based. However, there is a command-line version called TShark.
Features
- Real-time data capture.
- Reading data from Ethernet, IEEE 802.11, PPP, and loopback networks.
- Display filters.
- Plugin support.
- VoIP call detection.
- Raw USB data capture.
Pricing
Wireshark is free-of-charge and open source.
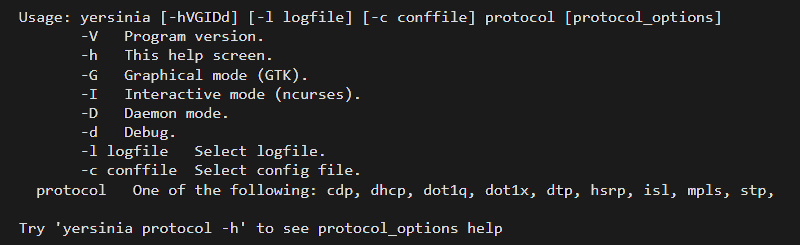
Yersinia
Yersinia is a network protocol exploitation tool that simulates and tests attacks against network protocols. It performs Layer 2 attacks by spoofing a solid framework for the deployed networks and systems testing and analysis.
Features
Yersinia supports attacking the following protocols:
- Cisco Discovery Protocol (CDP).
- Dynamic Host Configuration Protocol (DHCP).
- 802.1q and 802.1x.
- Dynamic Trunking Protocol (DTP).
- Hot Standby Router Protocol (HSRP).
- Inter-Switch Link Protocol (ISL).
- VLAN Trunking Protocol (VTP).
- Spanning Tree Protocol (STP).
Pricing
Yersinia is a free-of-charge and open-source tool.
Maltego
Maltego is an intelligence and data visualization tool for gathering and analyzing data from different sources and uncovering relationships and patterns. It provides a library of transforms for data discovery and a graph-formatted visualization of the data, which can be used for data mining and link analysis.
Features
- Simplified information gathering from dispersed data sources.
- Up to 1 million entities viewable on the map.
- Automatic linking and combining of map information.
- Pattern recognition that includes block, hierarchical, circular, and organic layouts.
Pricing
Maltego Community Edition is free of charge but requires registration. The paid options, Maltego Pro and Maltego Enterprise provide additional features. This includes using the tool on multiple devices, deploying it in virtual machines, accessing additional transforms on commercial Transform Hub, etc.
Apktool
Apktool is an application that allows users to reverse-engineer Android APK files. It disassembles resources and provides a way to make changes or analyze the disassembled application.
Features
- Extracts resources, assets, and code.
- Facilitates the examination of layouts, images, and XML files.
- Recompiles the code back to APK.
Pricing
Apktool is open-source and free to use.
sqlmap
sqlmap is a utility for detecting and exploiting SQL injection vulnerabilities in web apps and databases. The tool automates vulnerability detection and assists in database server takeovers.
Features
- Automatic and manual SQL injection testing.
- Support for a wide range of database management systems (DMS), such as MySQL, PostgreSQL, MariaDB, SQLite, Microsoft SQL Server, and many more.
- Support for six SQL injection techniques: error-based, UNION query-based, boolean-based blind, time-based blind, stacked queries, and out-of-band.
- Automatic password hash format recognition.
- Support for dumping database tables.
Pricing
sqlmap is open-source and free to use.
Dirb
Dirb is a tool for brute-forcing directories and files on web servers. Dirb launches a dictionary-based attack against a specified web server and analyses the response.
Features
- Uncovers resources that are hidden or unprotected.
- Supports multiple HTTP methods and scanning modes.
- Customizable scanning process.
- Preconfigured attack wordlists.
Pricing
Dirb is an open-source tool that is free to use.
Reaver
Reaver is a tool for exploiting Wi-Fi Protected Setup (WPS) weaknesses. It works by attempting to crack the WPS PIN and access a Wi-Fi network without authorization, highlighting the weaknesses in the setup.
Features
- Preconfigured attack wordlists.
- Custom wordlists.
Pricing
Dirb is a free-of-charge open-source application.
Conclusion
This article presented 25 popular cyber security tools frequently employed on Kali Linux. It offered an overview of each tool's features and versions.