Network ports are standardized numbers that allow devices to use a single IP address to handle multiple network requests simultaneously. Since there are 65535 port numbers, keeping a record of which ports are in use can be challenging.
This article will teach you how to check for open listening ports on a Linux system using five popular networking tools.
Prerequisites
- A Linux distribution.
- Administrative access to the command line.
- sudo or root privileges.
What Is a Listening Port?
Applications and services use listening ports to listen for incoming network requests. Each listening port is tied to an IP address and a communication protocol such as TCP or UDP.
Depending on the network setup, listening ports can be open or closed.
- Open ports accept outside connections using the correct protocol.
- Closed ports do not accept all the connections. They communicate with a predetermined outside service or application while a firewall blocks other attempted connections.
One listening port can host only one service. For instance, if a web server on the system already uses port 80, any other installed web server must use a different, non-default port.
How to Check Open Ports in Linux?
Linux users can check open ports using multiple available networking tools. Each tool displays the same results, but the output format and the amount of information vary.
The following sections provide instructions for checking open ports using lsof, netstat, ss, Nmap, and netcat utilities.
Check Ports via lsof Command
The lsof command allows users to list the programs that utilize listening ports and daemons that maintain active network connections.
Use the lsof command to:
- Display a list of ports in use:
sudo lsof -nP -iTCP -sTCP:LISTENThe command outputs a list of connections that use the TCP protocol.
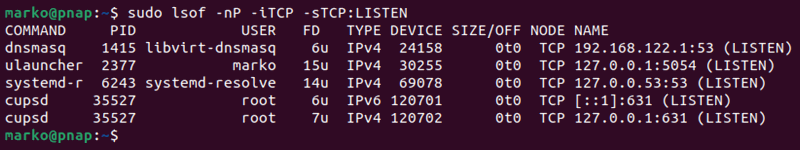
- Check a specific port number with this syntax:
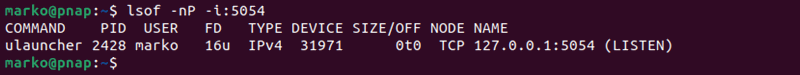
sudo lsof -nP -i:[port-number]For example, to check if port 5054 is in use, type:
sudo lsof -nP -i:5054If the port is free, the command shows no output. If an application is using the port, the output shows its details:
- Specify the protocol you wish to scan by adding it to the
-ioption.
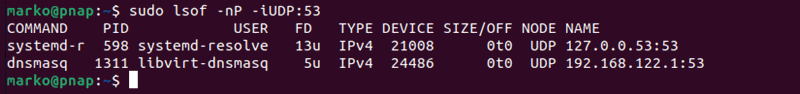
For example, to check if the UDP port 53 is open, type:
sudo lsof -nP -iUDP:53The output shows if an application already uses the port.
Check Ports via netstat Command
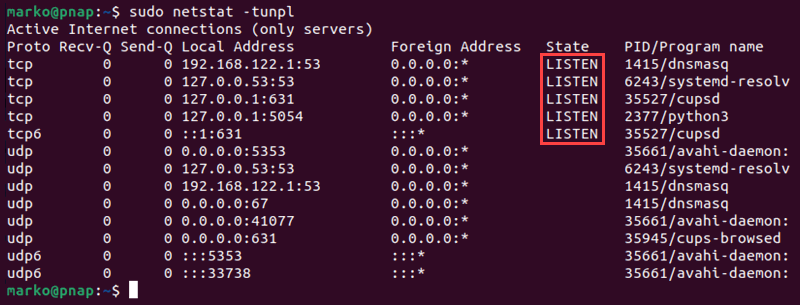
The netstat command provides an overview of network activity and statistics. Use the command below to display the listening ports on the system with netstat:
sudo netstat -tunplThe command uses five command arguments:
-t- Queries the command for TCP ports.-u- Queries for UDP ports.-n- Avoids DNS lookup and shows only IP addresses to speed up the process.-p- Displays the process ID and the name of the program using the port.-l- Outputs listening ports.
Identify the listening ports/sockets by checking the State column and looking for the label LISTENING.
Check Ports via ss Command
The ss command is a faster and easier-to-use version of the obsolete netstat command. It uses the same options as netstat, but provides more statistics in the output.
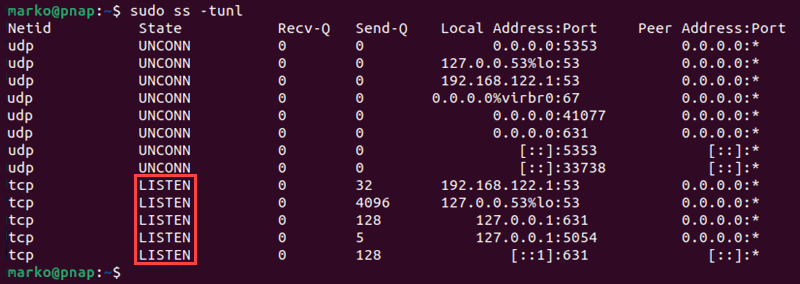
The following command scans TCP and UDP ports for listening sockets and displays them in a list:
sudo ss -tunlThe listening ports/sockets are marked as LISTEN in the State column.
Check Ports via nmap Command
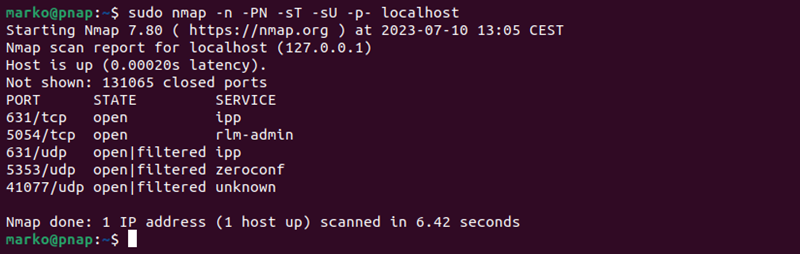
The Nmap utility allows users to scan for open ports on local and remote systems. Execute the command below to scan for all open TCP and UDP ports on the local system:
sudo nmap -n -PN -sT -sU -p- localhost The following are the nmap options used in the example.
-n- Skips DNS resolution.-PN- Skips the discovery phase.-sTand-sU- Tellnetstatto scan TCP and UDP ports, respectively.-p-- Scans all the ports.
The output lists open ports along with the services that use them.
Note: If you want to scan a port range, specify it with the -p option. For example, to scan only the UDP ports from 1 to 1023, type:
sudo nmap -p U:1-1023 localhost
Check Ports via nc Command
The nc command in Linux allows users to control the netcat utility. netcat can scan ports on local and remote systems and report whether they are open, closed, or filtered by a firewall.
Note: In CentOS, RHEL, and Debian the natcat command is ncat.
Scan all the ports on the local system by typing:
nc -z -v localhost 1-65535The -z flag enables the zero-I/O mode used for scanning, while the -v option tells netcat to produce verbose output.
When the command is executed, netcat attempts to connect to all ports and reports the success for each. Scanning many ports at once produces an extensive output.
To show only the ports where the connection succeeded, i.e., the open ports, use the 2>$1 expression to redirect the output. Then, pipe the expression to the grep command and search for the word succeeded.
nc -z -v localhost 1-65535 2>&1 | grep succeeded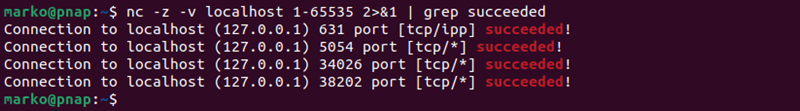
By default, netcat scans TCP ports. To check UDP ports, add the -u option:
nc -z -v -u localhost 1-65535 2>&1 | grep succeeded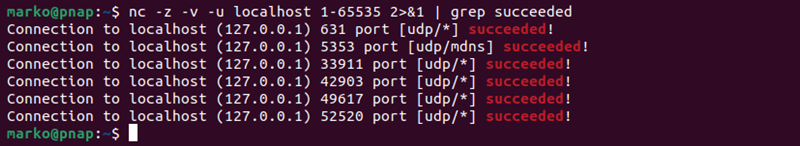
Conclusion
After reading this article, you should know how to use the five popular Linux utilities to check for open ports. Knowing which ports are open on your system may help you detect an intrusion or troubleshoot network-related issues.