SSH (Secure Shell) and SSL (Secure Sockets Layer) are cryptographic technologies that ensure secure communication over the internet. However, SSH and SSL have different purposes and distinct characteristics.
In this text, you will learn the features of SSH vs. SSL and how each protocol works.
SSH vs. SSL Main Differences
SSH and SSL are different protocols that serve different user groups.
SSH authenticates and encrypts data transmitted between clients and servers, enabling secure remote access over an unsecured network. The protocol requires client authentication to enable remote login and create a secure connection for issuing SSH commands.
On the other hand, SSL encrypts data transmitted between a website and visitors to protect sensitive information like credit card details. The protocol is popular in web browsers, servers, e-commerce, and online banking. SSL primarily encrypts data in transit between a web browser and a web server. SSL is also known as Transport Layer Security (TLS).
What is SSH?
The way Secure Shell (SSH) works is by allowing clients and servers to communicate via a secure channel, ensuring safe information transfer between machines.
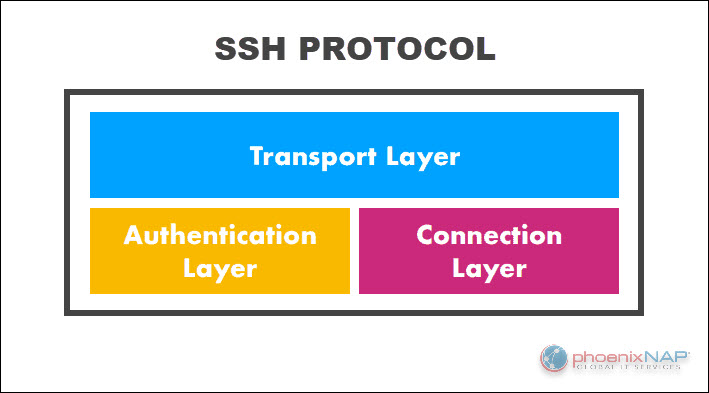
The SSH protocol has three layers:
- Transport layer. Encrypts data to ensure protection from tampering and handles the negotiation of cryptographic algorithms and parameters used for encryption, key exchange, and authentication. It caches and compresses data to improve connection efficiency.
- Authentication layer. Verifies the client's identity using password authentication, public key authentication, and host-based authentication.
- Connection layer. Manages communication channels after the authentication process completes. This layer creates separate channels for different data types, encrypts each channel, and handles channel-specific options, such as terminal settings and flow control.
The SSH purpose is to replace terminal emulation or login programs, such as Telnet, rlogin, and rsh, as well as file transfer programs, such as FTP and rcp. The significant SSH feature is it supports several encryption technologies:
- Symmetric encryption. Symmetric encryption algorithms encrypt data using the same key to encrypt and decrypt data, which provides fast and efficient encryption.
- Asymmetric encryption. Asymmetric encryption algorithms use a public key to encrypt data and a private key to decrypt data.
- Message authentication codes (MACs). MACs use a cryptographic hash function and a secret key. The recipient uses the same hash function and key to verify the MAC and ensure that the data has not been tampered with.
- Public key encryption. Public key encryption algorithms use SSH keys: a public key for encryption and a private key for decryption.
How does SSH Work?
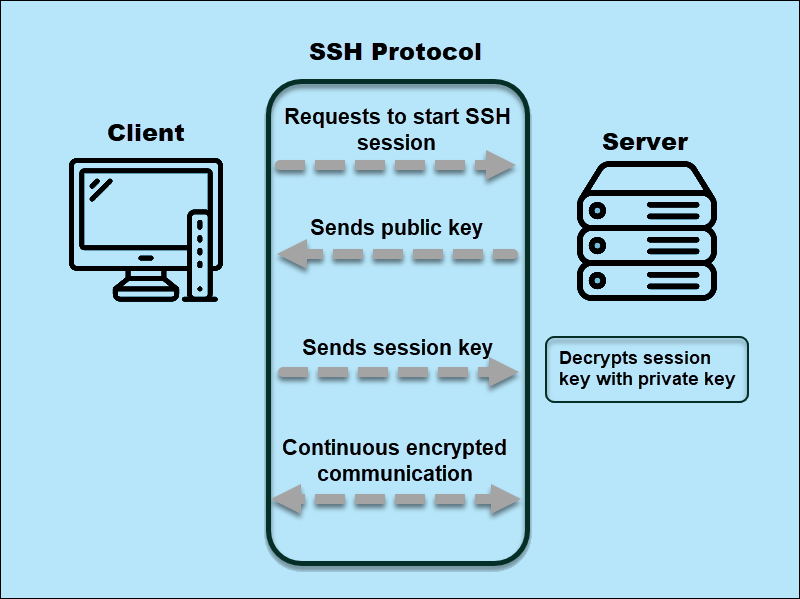
When a client initiates a connection to a server and sends a request to start an SSH session, the server responds with the public key. The client uses the public key to verify the server's identity and generates a session key.
Next, the client sends the key to the server in an encrypted form that only the server can decrypt. The server decrypts the code with the private key and uses it to encrypt all future communication with the client.
Both the client and server use the session key to encrypt all communication, providing confidentiality and integrity. Once the session is complete, both the client and server exchange a final message and close the connection.
Main Features of SSH
SSH provides a security layer for information transfer between machines. The main SSH features are:
- Remote access. SSH ensures encrypted, remote connections for users and processes.
- File transfers. SSH mostly uses SFTP, a secure file transfer protocol that provides a safe way to manipulate files over a network.
- X11 Forwarding. Allows users to run server-hosted X applications from the client machines.
- Port Forwarding. SSH helps secure other network protocols, such as TCP/IP, by mapping a client's port to the server's remote ports.
- Tunneling. This encapsulation technique provides secure data transfers. Tunneling is useful for accessing business-sensitive online materials from unsecured networks, as it acts as a VPN alternative.
- Network management. The SSH protocol is efficient in managing a network infrastructure and other system components.
- User and host authentication. SSH uses public-key cryptography to authenticate both the user and the host to provide an extra security layer.
- Script automation. SSH is able to execute automated scripts remotely, allowing for more efficient system administration and management.
What is SSL?
SSL secures, encrypts, and authenticates online communications. The SSL protocol creates a secure and encrypted connection between a web server and a web browser, protecting sensitive information such as passwords and credit card details from unauthorized access.
SSL certificates are essential components of the data encryption process. They provide authentication to protect the confidentiality and integrity of website communication with browsers. An SSL certificate is a data file containing a key pair and the website's authenticity details. The certificate's job is to initiate secure sessions with the user’s browser via the SSL protocol.
While SSL was replaced by an updated protocol called TLS (Transport Layer Security), the term SSL is still used to refer to this technology.
How Does SSL Work?
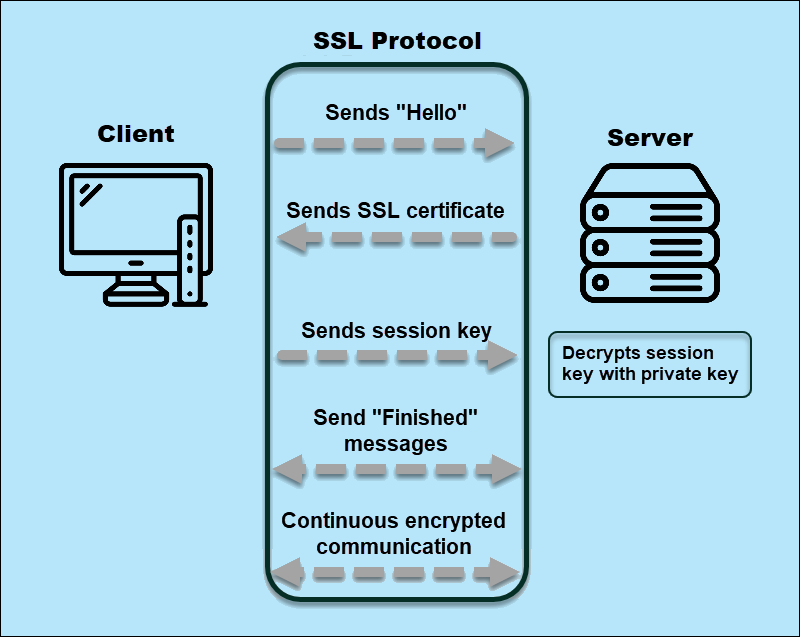
The SSL handshake is the process that establishes a secure connection between the client and server using the SSL protocol.
A client accesses a website using SSL by sending the initial "hello" message. The server responds with the SSL certificate, which includes the public key.
Next, the client verifies the authentication and confirms that it is communicating with the rightful domain owner. If the certificate is valid, the client sends an encrypted session key to the server. Only the server is able to decrypt the message with the private key.
From this point on, all data between the client and server is encrypted. However, before the handshake completes, both the client and the server send a Finished message encrypted with the secret session key.
Main features of SSL
SSL provides essential features for data encryption, authentication, and integrity. The main features of SSL include:
- Encryption. SSL encrypts data in transit to ensure that nobody gains access to it.
- Authentication. Digital certificates authenticate the server and client identities and ensure that the intended parties send and receive the data.
- Integrity. SSL ensures that data sent during transmission between the client and server has not been tampered with.
- Compatibility. Web browsers, servers, and other software support SSL. As a result, the protocol is easy to implement on a wide range of platforms.
- Visual indicators. SSL certificates provide a visual indicator of a website's security status, such as a lock icon or green address bar, which helps users verify the authenticity of a website.
Conclusion
After reading this article, you know the difference between SSH and SSL.
Next, read this guide to different types of SSL certificates.