Secure Shell (SSH) provides secure remote access to servers and network devices. On most operating systems, direct root or administrator login is disabled by default to reduce the risk of attacks. Enabling root login simplifies administration but exposes the system to brute-force attacks.
This tutorial will show you how to enable or disable SSH root login and troubleshoot common issues.

How to Enable Root Login via SSH
When you enable root login via SSH, it allows direct administrative access to the server. While convenient, it bypasses the additional security layer provided by sudo.
The process is similar across most operating systems, with minor differences. For instance, on Windows, there is no root user. The equivalent is the Administrator account.
To use SSH on Windows, you need OpenSSH, a software package that provides both the SSH client (ssh) and server (sshd). This gives Windows the same SSH functionality as in any other OS and allows secure remote access.
The following steps show how to enable root login:
1. Open the sshd_config file with a text editor of choice. To do it with Nano, use:
sudo nano /etc/ssh/sshd_configNote: This path works for Linux distributions and other OSs. However, on Windows with OpenSSH installed, the file location is at C:\ProgramData\ssh\sshd_config.
2. Find the line that starts with #PermitRootLogin and change it to:
PermitRootLogin yes
3. Save the file and restart the SSH service. On Debian-based systems, enter:
sudo systemctl restart sshMost other Linux distributions use the following:
sudo systemctl restart sshdOn macOS systems, run these commands:
sudo launchctl stop com.openssh.sshd<br>sudo launchctl start com.openssh.sshdOn Windows with OpenSSH installed, run:
net stop sshd
net start sshd4. Test the connection by logging in as root (or Administrator on Windows)
Use the following syntax for Linux and macOS:
ssh root@[hostname_or_IP]Use the following syntax for Windows with OpenSSH installed:
ssh Administrator@[hostname_or_IP]Note: On Windows, SSH login as Administrator sometimes requires additional configuration.
This example shows how to log in as root on Ubuntu. Run:
ssh [email protected]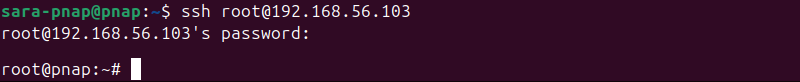
The system prompts for the root password and completes the login as the root user.
When you allow root login with a password, the server becomes a target for brute-force attacks. A safer option is to configure passwordless SSH login, which uses an SSH key pair (a private key stored on your computer and a public key added to the server).
To enforce root login only with SSH keys, set PermitRootLogin prohibit-password in the configuration.
Note: In recent versions, prohibit-password is an alias for the older without-password. Both work, but prohibit-password is the recommended form.
This process prevents attackers from guessing passwords, but still allows secure SSH access.
How to Disable Root Login via SSH
Disabling root login via SSH improves system security since it forces administrative users to connect with a regular account and use sudo for elevated tasks.
Take the following steps to disable root login:
1. Open the SSH configuration file:
sudo nano /etc/ssh/sshd_config2. Change the line that starts with PermitRootLogin to:
PermitRootLogin no
3. Save the file and use the same commands as described in the previous section to restart SSH.
4. Try to log in as root (or Administrator on Windows) to test the connection. For example, to accomplish it on Ubuntu, run:
ssh [email protected]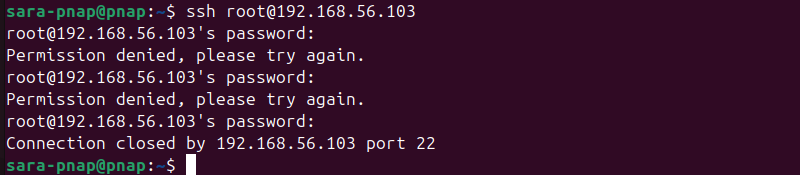
The system refuses to connect. For security reasons, SSH does not reveal the cause of the failure, so the error appears the same as when an incorrect password is used.
When to Have Root Login Enabled
While direct root login via SSH is a security risk, it is useful in certain situations. The following list explains some circumstances in which it is helpful to enable root login:
- Initial server setup. Root login simplifies installation and configuration tasks before a regular administrative user is created.
- Automated scripts or management tasks. Some legacy scripts or tools require direct root access to function properly.
- Emergency recovery. Root login provides a last-resort access method if normal user accounts are locked or misconfigured.
- Isolated or secure environments. On servers not exposed to the internet and physically secure, root login is a convenient option.
Even in these cases, it is safer to use SSH keys instead of passwords.
Troubleshooting SSH Root Login Problems
SSH root login fails for various reasons, such as misconfigurations, authentication issues, or service problems. Troubleshoot these issues to ensure secure and reliable server access.
The following sections present common problems and solutions.
Permission Denied Errors
Permission Denied errors occur when SSH is unable to authenticate the user. Common causes include an incorrect password, a missing or misconfigured SSH key, or a combination of both.
To fix key-based login issues, take the following steps:
1. Use cat to ensure the user’s ~/.ssh/authorized_keys file contains the correct public key corresponding to your private key:
cat ~/.ssh/authorized_keys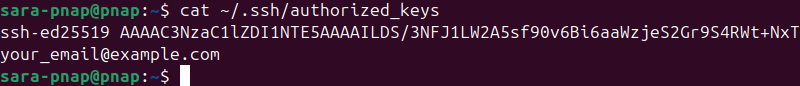
The output shows the public key is present.
2. Set correct file permissions with chmod:
chmod 600 ~/.ssh/authorized_keysThe command has no output. However, it ensures only the file owner can read and write it, which is necessary for key-based authentication to work.
3. Attempt to log in again using the private key or password.
SSH Not Running
If the SSH service is stopped, root login fails. Restart the service according to your operating system to resolve this issue.
On Debian-based systems, such as Ubuntu, Debian, or Linux Mint, run:
sudo systemctl restart sshOther Linux distributions and macOS use the following command:
sudo systemctl restart sshdNote: For more information, refer to our guide on how to start, stop, and restart services in Linux.
If you use Windows with OpenSSH installed, run:
net stop sshd
net start sshdFirewall Blocking SSH Connections
A firewall that blocks port 22 sometimes prevents SSH login. Ensure the firewall allows incoming connections on the SSH port.
Take the following steps:
1. Check the firewall status with the ufw command:
sudo ufw status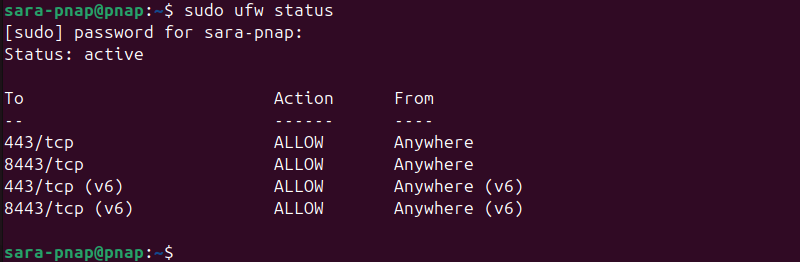
In this case, the firewall is active. However, port 22 is missing. This means SSH connections from other machines are blocked.
2. Enable incoming SSH connections to this port with:
sudo ufw allow 22/tcp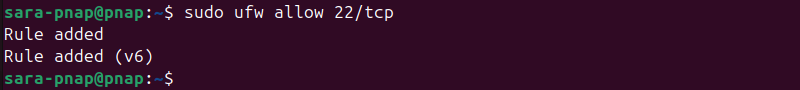
3. Check ufw status again:
sudo ufw status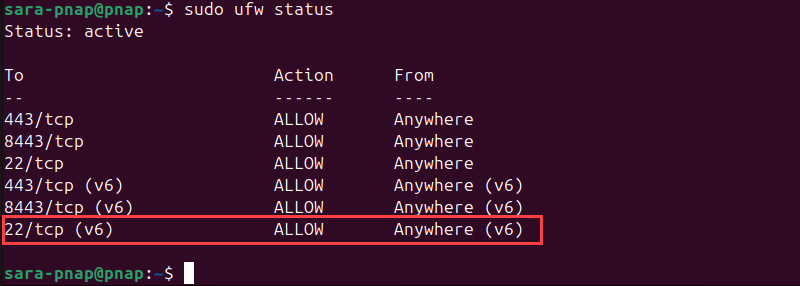
Incorrect PermitRootLogin Setting in sshd_config
If the PermitRootLogin line in sshd_config is incorrect, root login does not work.
Verify the configuration file contains the correct value (yes to enable, no to disable) and restart the SSH service after making changes.
Conclusion
This tutorial explained how to enable and disable SSH root login. It also highlighted situations in which root access is necessary and covered common issues along with practical solutions.
Next, learn about common SSH commands in Linux.