SSH provides remote system access via an encrypted channel, enabling users to manage files and perform operating system maintenance from another machine. There are two ways to authenticate an SSH connection - password authentication and public key authentication.
This tutorial will teach you how to set up and enable passwordless SSH login.

Prerequisites
- Command-line access to the local system.
- SSH access to a remote server.
- User with sudo or root privileges.
Step 1: Verify SSH Server Is Running
Before using SSH to connect to a remote host, ensure the SSH daemon is active on the local machine. To check the SSH service status, enter the following command:
sudo systemctl status sshIf SSH runs as expected, the Active section shows the active (running) status.
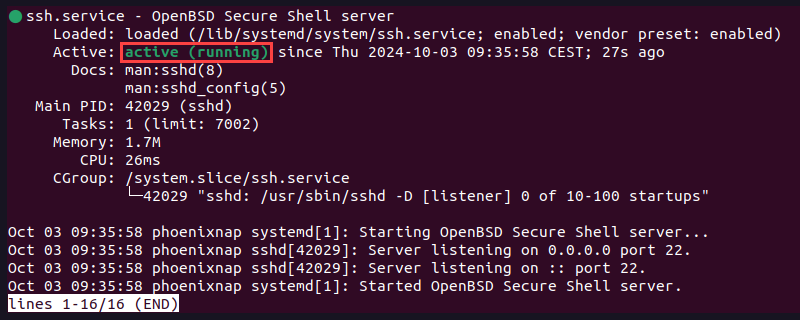
Press q to quit the status report.
Step 2: Generate SSH Key Pair
Start setting up passwordless authentication by generating an SSH key pair on the local machine.
1. Type the following command:
ssh-keygen -t [type] -b [number-of-bits]Note: The minimum number of bits in a key is 768. if the -b option is not specified, the system generates a 2048-bit key.
The example below shows how to generate a 4096-bit RSA key pair:
ssh-keygen -t rsa -b 40962. Type a custom key location or hit Enter to accept the default path.
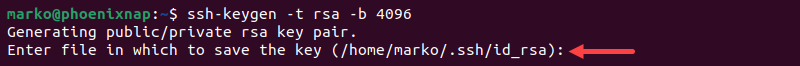
3. Set a passphrase or press Enter to skip this step. Passphrases make connections more secure, but they may disrupt automated processes.
The output shows the location of the private and public keys and displays a key fingerprint.
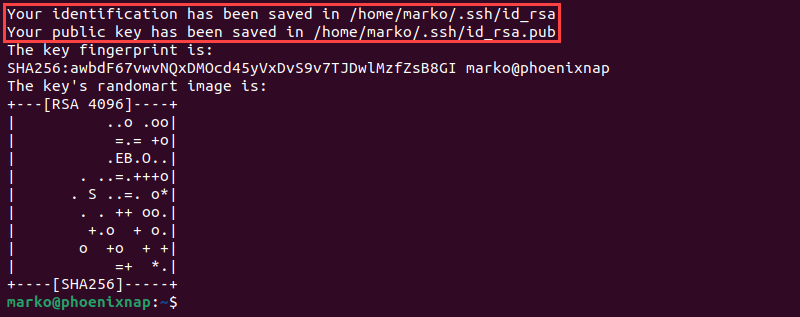
Step 3: Upload Public Key to Remote Server
Enable passwordless access by uploading a copy of the public key to a remote server. A public SSH key can be sent to a remote server using the ssh-copy-id or cat command.
The sections below provide steps for both options.
Option 1: Upload Public Key Using ssh-copy-id Command
The ssh-copy-id command is designed to transfer SSH credentials to remote hosts. Follow the steps below to learn to use it:
1. Connect to the remote server:
ssh-copy-id [remote_username]@[remote_server_ip_address]For example:
ssh-copy-id [email protected]2. Type yes and press Enter to confirm the connection.
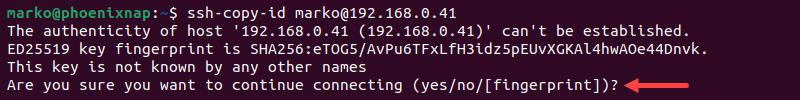
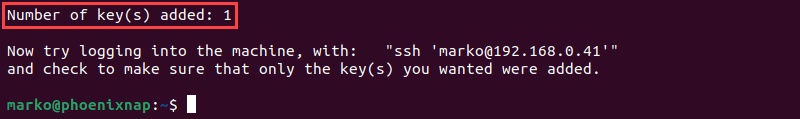
3. Enter the remote user's password.
The output confirms that one public key has been added to the remote host.
Option 2: Upload Public Key Using cat Command
If using ssh-copy-id is not an option, use the cat command to copy the public key to the server:
1. Start by connecting to the server and creating a .ssh directory:
ssh [remote_username]@[server_ip_address] mkdir -p .ssh 2. Enter the password for the remote user.
3. Upload the public key from the local machine to the remote server. The command also specifies that the key will be added to the .ssh/authorized_keys file:
cat .ssh/id_rsa.pub | ssh [remote_username]@[server_ip_address] 'cat >> .ssh/authorized_keys'Step 4: Log in to Server Without Password
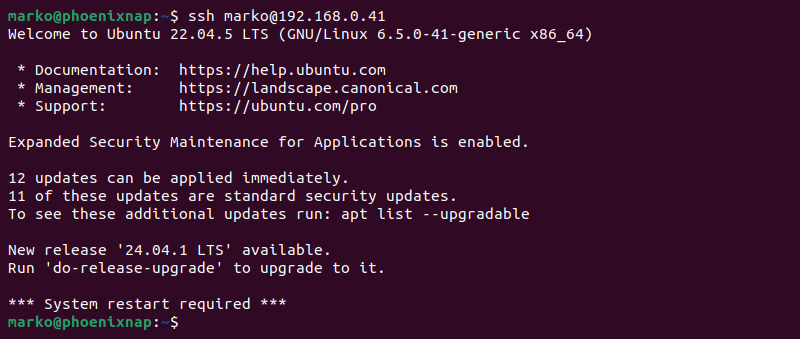
With the SSH key pair generated and the public key uploaded to the remote host, attempt to connect to the host without providing a password:
ssh [remote_username]@[server_ip_address]The system should log in directly to the remote server.
Note: After verifying that the passwordless authorization works as expected, disable SSH password authentication. This action will add another layer of protection and secure your server from brute-force attacks.
File permissions on the remote server may cause issues with passwordless SSH login. If you are still prompted for a password after going through all the steps, edit file permissions on the remote server by typing the following command:
ssh [remote_username]@[server_ip_address] "chmod 700 .ssh; chmod 640 .ssh/authorized_keys"When prompted, enter the password. There will be no output if the action is successful.
Conclusion
The instructions outlined in this article helped you to enable passwordless SSH login and seamlessly connect to a remote server. Use passwordless SSH to set up automatic maintenance tasks and increase the security of your connection.
For more SSH commands, check out these common Linux SSH commands with examples.