Linux configuration files shape the operating system's behavior and functionality. The files represent the core elements that strengthen the robust configurability of a Linux system.
This guide will explore the fundamental aspects of Linux config files and showcase their significance and crucial role in the Linux ecosystem.

What Is Config File in Linux?
A configuration (config) file is a local Linux file that controls how a program, utility, or process works. The config files are typically text files that contain the settings and instructions for various utilities, programs, and processes.
The config files are non-executable. They contain different parameters and settings for various parts of the OS. Those parts include processes, user groups, permissions, network access and protocols, OS directives on accessing internet name servers, etc.
Why Are Configuration Files Important?
Configuration files play a pivotal role in Linux systems. They enable system administrators to customize the OS, control the system and application settings, and ensure the setup persists across reboots.
Config files are essentially very simple, but they manage extremely complex interfaces. A single configuration file can control thousands of system features, making it essential for a properly functioning system.
The config files facilitate troubleshooting, version control, and backup, ensuring consistency across multiple systems. They also serve as documentation and house security policies, which makes them essential to Linux system management and flexibility.
Types of Config Files in Linux
Configuration files can be divided into two general categories:
- System-wide configuration files. These config files affect the entire system. They are usually located in the root (
/) partition and require superuser access for modification. - User-specific configuration files. These files tailor the environment to individual user preferences. They are usually located in the user's home directory and don't require superuser permissions for modification.
In addition to being divided into system-wide and user-specific files, Linux configuration files can also be grouped by type. These files play a critical role in managing authentication and system administration to configuring the behavior of user programs.
The sections below explain the different types of configuration files in a Linux system and list the most important configuration files for each type.
Network Access Files
The network access configuration files provide the rules and instructions for looking up hostnames and controlling network access. The files configure and manage access control policies for network services and hosts.
The access files are:
- /etc/hosts.config. Contains configuration options for hostname resolution using the /etc/hosts file.
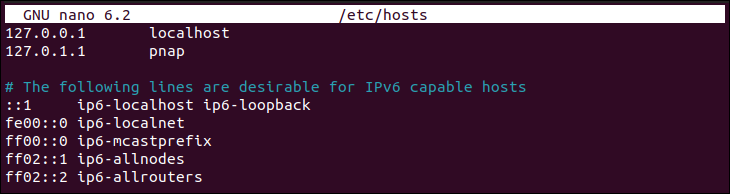
- /etc/hosts. A local database for mapping hostnames to IP addresses used when DNS is unavailable or for local network configurations.
- /etc/hosts.allow. Specifies rules for allowing network services based on criteria like IP addresses or hostnames.
- /etc/hosts.deny. Contains rules to deny network access to specific services or hosts based on criteria like IP addresses or hostnames.
The image below shows an example of the /etc/hosts file:
Note: Learn how to edit hosts file on Linux.
Booting
The boot configuration files affect the Linux system's boot process. These files provide system information, manage startup services, and define system runlevels.
The boot-related files include:
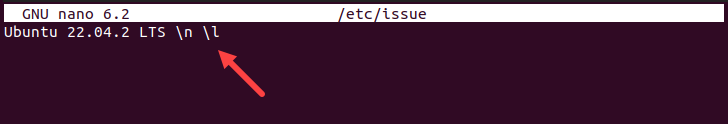
- /etc/issue. A text file that provides system information and a greeting message displayed before the login prompt.
- /etc/issue.net. Similar to /etc/issue but used for network connections and remote logins.
- /etc/rc.d/rc. A script that manages system runlevels and startup services.
- /etc/rc.d/rc.sysinit. A script responsible for system initialization tasks at boot time, including hardware initialization and mounting filesystems.
- /etc/rc.d/rcX.d/. A directory containing symbolic links to scripts that control services started or stopped at various runlevels (X represents the runlevel number).
The following image shows the contents of the /etc/issue file and the greeting message it contains:
Login/Logout
Login/logout config files are essential for managing user sessions in a Linux system. These files control login behavior and provide a welcoming message to users during login. The login/logout-related files include:
- /etc/issue. Provides system information and displays a greeting message before the login prompt.
- /etc/issue.net. Has the same purpose as /etc/issue, but is used for network connections and remote logins.
Note: The /etc/issue and /etc/issue.net files are relevant to both booting and login/logout. They serve a dual purpose in displaying system information and greetings during login.
File System
File system configuration files manage and define how storage devices and file systems are mounted and accessed. These files help control and specify storage management options. Some key file system configuration files are:
- /etc/mtab. A file that lists currently mounted file systems, the information about the device, mount point, and file system type.
- /etc/fstab. A configuration file that defines and configures static file system mounts, including options for each mount point.
- /etc/mtools.conf. The configuration file for the
mtoolspackage, used for accessing and managing MS-DOS (FAT) file systems, which specifies settings for tools likemcopyandmdir.
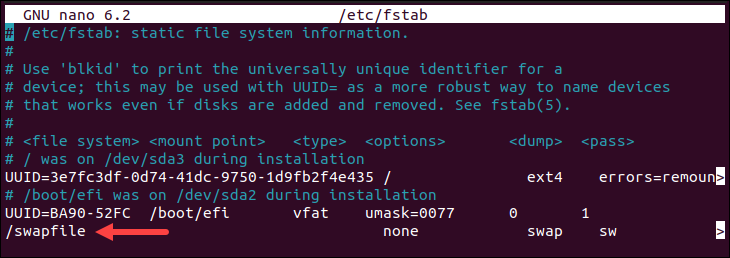
The following image shows the /etc/fstab file with a line that makes the swap partition persist across reboots:
System Administration
System administration configuration files in Linux store essential information about user accounts and user credentials, groups, file permissions, and manage system security policies. These files are crucial for ensuring the system's integrity and security.
Below are some key system administration configuration files:
- /etc/group. Contains information about user groups, including group names and associated user accounts.
- /etc/nologin. Prevents specified users from logging in, often used for system maintenance messages.
- /etc/passwd. Stores user account information, including usernames, user IDs, home directories, and shell executables.
- /etc/rpmrc. Configuration file for the RPM package manager that specifies global RPM settings.
- /etc/securetty. Lists terminals (TTYs) from which root (superuser) is allowed to log in directly.
- /etc/usertty. Specifies which terminals user accounts are allowed to use.
- /etc/shadow. Stores password hashes and security-related information for user accounts, enhancing password security.
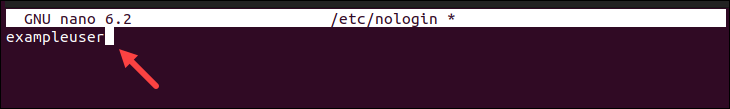
The following image shows the contents of the /etc/nologin file, with the specified exampleuser user being restricted from logging in:
System Commands
System command configuration files in Linux contain information about system-level utilities and commands used for system administration and operation. These files serve for configuring and managing system commands and utilities, thus ensuring the proper functioning of the system's core components and services.
Below are some key system command configuration files:
- /etc/lilo.conf. Configuration file for the LILO (LInux LOader) bootloader that specifies how the system should boot and manage multiple operating systems.
- /etc/logrotate.conf. Configuration file for the log rotation utility,
logrotate, that manages log files and controls log rotation policies. - /etc/identd.conf. Configuration file for the Ident daemon, which identifies the owner of TCP connections and is used for network services like IRC.
- /etc/ld.so.conf. Lists the directories in which the system should search for shared libraries dynamically linked to executable files.
- /etc/inittab. Configuration file for the
initprocess that specifies system runlevels, actions, and processes to execute during system initialization. - /etc/termcap. Defines terminal capabilities and characteristics for various terminal types, enabling applications to interact with terminal devices correctly.
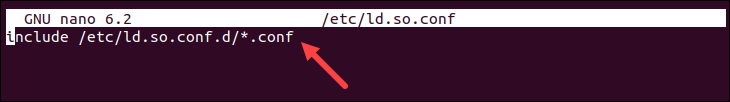
The following image is an example of the /etc/ld.so.conf file and the list of directories the system should search for dynamic links to executable files:
Daemons
Daemons are vital background processes that respond to network, hardware, or system requests to perform certain tasks. Configuration files for daemons help define their behavior and settings.
The following are the key daemon configuration files:
- /etc/syslogd.conf. Configuration file for the syslog daemon (
syslogd), which manages system and application logs, specifying how to handle log messages and where to store them. - /etc/httpd.conf. Configuration file for the Apache HTTP server (httpd), used to define server settings, virtual hosts, and behavior for serving web content.
Networking
Networking configuration files in Linux set up and manage network-related settings, services, and protocols, ensuring efficient and reliable network operations. These files play a crucial role in defining network behavior and connectivity.
The following list contains the key networking configuration files:
- /etc/gated.conf. Configuration file for the
gatedrouting protocol daemon. - /etc/gated.version. Contains the
gateddaemon version number. - /etc/gateway. An optional configuration file used by the
routeddaemon for routing information. - /etc/networks. Lists names and addresses of networks accessible from your network. Used by the route command for network routing.
- /etc/protocols. Lists currently available network protocols used for network communication.
- /etc/resolv.conf. Specifies which name server should be queried when resolving IP addresses.
- /etc/rpc. Contains instructions/rules for Remote Procedure Call (RPC) used in NFS calls, remote file system mounting, and more.
- /etc/exports. Configuration for exporting file systems via NFS, including permissions.
- /etc/services. Translates network service names to port numbers and protocols used by various network-related programs.
- /etc/inetd.conf. Configuration file for
inetd, which controls daemons or services for various network services. - /etc/sendmail.cf. Configuration file for the
sendmailmail transfer agent. - /etc/sysconfig/network. Indicates whether networking is enabled. The file is read during system initialization.
- /etc/sysconfig/network-scripts/if*. Red Hat network configuration scripts for managing network interfaces.
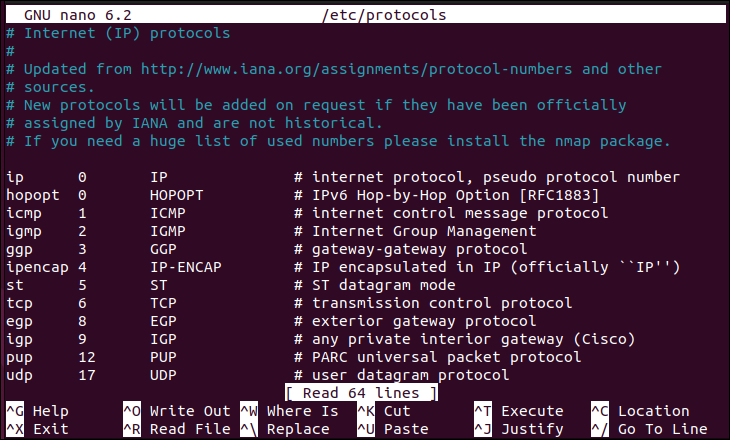
The following is an example of the /etc/protocols file with all the currently available protocols on the system:
User Programs
The configuration files for user programs allow you to customize and configure applications according to your preferences. The files are usually hidden and stored in the user's home directory. These hidden files and directories are prefixed with a . (dot), for example, .config or .appname. To view them, you can use the ls command.
User and system programs read their configuration files each time you run them. The default configuration is read from the config files stored in the /etc/ directory. Later, users can customize the programs using the rc and . (dot) files.
The section below explains how you can edit a configuration file in Linux.
How to Edit a Linux Config File?
Each Linux distribution has its configuration files, naming conventions, and specific storage locations. Some config files are referenced by filename, with or without the file extension, while others are specified by their directory location.
Despite differences among distributions, the general purpose of config files and the way they are manipulated to affect the system are the same. Configuration files are typically plain text files and can be edited with a text editor.
The format and syntax of the files depend on the application they are associated with, and some apps also provide GUI tools for modifying their settings. Common formats include INI-style, XML, JSON, or custom formats.
Important: Before changing any value in any of these files, ensure you make a backup and know everything about the configuration to avoid irreparable damage to the system.
Restart the program for which you made the config file changes if the system administrator or the kernel does not control it. Changing kernel configuration files immediately affects the system.
For example, adding a user in the passwd file immediately enables that user. However, only the superuser can modify kernel files, while other users have read-only access.
Conclusion
This article has explained the importance of Linux config files, how they work, and how they affect the system and user programs. Editing Linux config files allows users to tweak the system and programs to their preferences, providing many customization options.
Next, read about the most important Linux commands all users should know.