An IP address identifies a device or network on the internet. Larger organizations often segment their internal networks for administrative, security, or performance reasons.
Instead of managing multiple separate IP address blocks, they create smaller internal networks, called subnets, within their existing IP address range.
In this article, find out how subnetting works, how to implement it, and what advantages it brings to your organization.
What Is a Subnet (Subnetwork)?
Subnets (subnetworks) are subdivisions of a larger IP network. Since each subnet has a unique identifier within the broader network address space, organizations use them to divide existing IP address blocks into smaller internal networks and separate devices into distinct logical groups. Devices within the same subnet can communicate directly, while communication across subnets requires a router.
A subnet is identified by the IP address and a subnet mask or Classless Inter-Domain Routing (CIDR) prefix. Devices use this information to determine which part of an address represents the network and which part identifies the individual device.
The example below shows how the IP address 192.168.2.16 is interpreted when used with a /24 CIDR prefix:
| IP Address | 192.168.2.16/24 |
|---|---|
| Network Portion | 192.168.2 (first 24 bits) |
| Host ID | 16 (last 8 bits) |
| CIDR (subnet mask) | /24 (255.255.255.0) |
| Subnet Range | 192.168.2.0 - 192.168.2.255 |
The CIDR prefix /24 tells the device that the first 24 bits of the IP address represent the network portion, and the remaining 8 bits represent the portion of the IP address that uniquely identifies that device/host within a subnet. By adjusting the prefix length, you control how many bits to allocate to the network versus the host. This determines how many hosts each subnet can support.
Subnet vs. Subnet Mask vs. CIDR Prefix
The difference between a subnet, subnet mask, and CIDR prefix can confuse those who are new to networking. The following table explains the roles more closely:
| Term | Definition | Usage | Example |
|---|---|---|---|
| Subnet | A logical subdivision of a larger IP network. | Grouping devices into smaller isolated segments within a wider internal network. | Separate subnets for different departments in a company. For example, a subnet for devices in the finance or HR department. |
| Subnet Mask | A 32-bit binary number (for example 255.255.255.0) used alongside an IP address to determine which part of the IP address identifies the network and which part identifies the device within a subnet. | Devices perform a bitwise AND operation on their IP and subnet mask to calculate their network address. This helps them determine if the destination is on the same subnet or if it should be routed through a gateway/router. | IP Address: 192.168.1.5Subnet Mask: 255.255.255.0The sending device calculates its network address 192.168.1.0 from the IP address and subnet mask. |
| CIDR Prefix | A shorthand way to write subnet masks using a slash notation, such as /24. | Specifies how many leading bits are used for the network portion and how many for the host/device ID. (e.g. /24 = 24 bits).Allows for classless and more flexible IP address allocation and subnetting in IPv4 and IPv6. | The sending device interprets 192.168.1.5/24 as: IP 192.168.1.5 with the subnet mask 255.255.255.0.The sending device calculates its network address as 192.168.1.0. |
What Is Subnetting?
Subnetting is the process of dividing a larger IP network into subnets. It is a network design strategy for managing IP address space more efficiently by creating multiple internal networks from a single IP address block using CIDR (Classless Inter-Domain Routing) and subnet masks.
These internal segments remain invisible to external networks. The entire subnetted structure appears as a unified network from the outside. This means subnetting can be applied within the same physical infrastructure without affecting global internet routing.
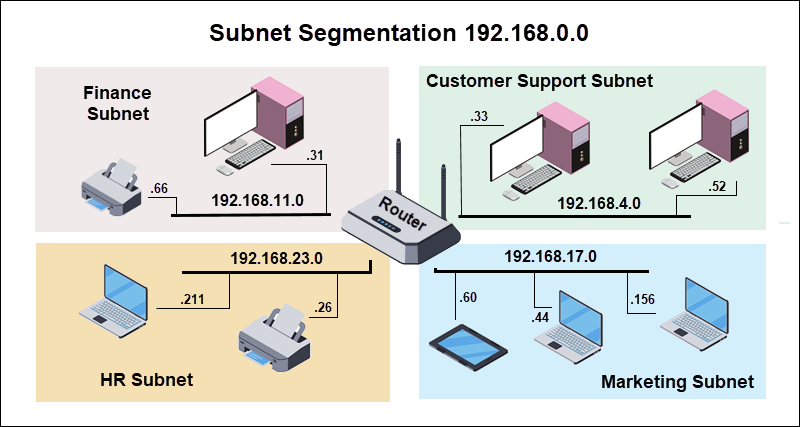
Subnetting can control and isolate data flows between departments, geographic locations, or services. Communication relies on routers or Layer 3 switches to direct traffic between subnets.
How Does Subnetting Work?
After you set up a subnet, the sending device within a subnet uses its IP address and subnet mask to deliver a network packet to another device. The process looks like the following:
1. The device that wants to send data performs a bitwise AND operation using its own IP address and subnet mask to calculate its network address.
2. Then it executes a second bitwise AND operation using the same subnet mask and the destination IP address to calculate the destination's network address.
3. If the two network addresses match, the packet is sent directly. If the network addresses do not match, the packet travels to the sending device's default gateway/router.
4. The router receives the packet and consults its routing table. The routing table contains destination network addresses, their associated subnet masks or CIDR prefixes, and the next hop or outgoing interface.
5. The router applies subnet masks (or CIDR prefixes) from its routing table to determine the best match for the destination IP.
6. It forwards the packet through the corresponding interface toward the next router or the final destination.
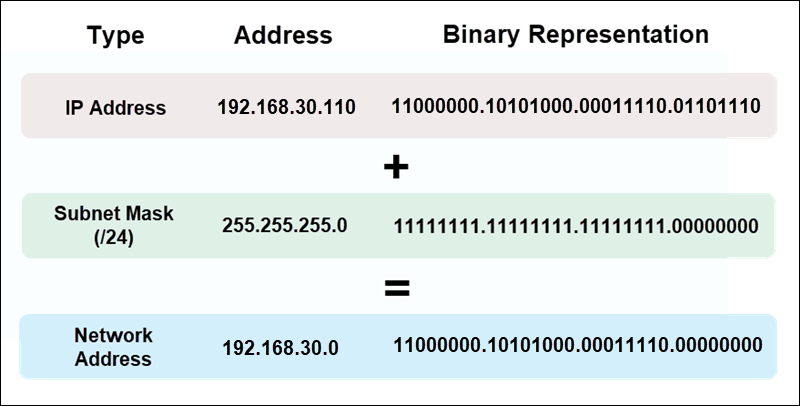
Calculating the network address depends on how the subnet mask divides it into the network and host portions. Historically, this was done using IP address classes with default subnet masks and bit boundaries. Modern networks use CIDR notations that allow for more flexible subnetting.
IP Address Classes
In early IP networking, the address space was divided into predefined IP ranges called classes, each with a default subnet mask. IP address classes are no longer widely used for modern network design, but they help explain default masks in some systems:
| Class | First Octet Range | Default Subnet Mask | Hosts Per Network | Use Case |
|---|---|---|---|---|
| A | 0–127 | 255.0.0.0 | 16,777,214 | Very large organizations (legacy). |
| B | 128–191 | 255.255.0.0 | 65,534 | Medium-sized networks. |
| C | 192–223 | 255.255.255.0 | 254 | Small business and home networks. |
| D | 224–239 | N/A | N/A | Reserved for multicast. |
| E | 240–255 | N/A | N/A | Reserved for experimental use. |
Modern networking uses CIDR instead of fixed classes because it lets administrators divide IP address blocks into subnets of different sizes.
CIDR
CIDR uses prefix notation, such as /24, to indicate how many bits of an IP address are used for the network portion. By adjusting the prefix, administrators can control the number of subnets and the number of hosts in each subnet.
The notation consists of an IP address followed by a slash and the number of bits used for the network ID. For example, 192.168.1.1/24 states that the first 24 bits represent the network address, and the remaining 8 bits represent host addresses. This structure matches the traditional Class C network scheme.
Changing the prefix to /22 allocates 22 bits to the network address and leaves 10 bits for host addresses. This means there are fewer networks, but that up to 1022 hosts can be attached per subnet (compared to 255 in a /24). The following table provides an overview of the most commonly used CIDR notations and corresponding subnet masks:
| CIDR | Subnet Mask (Decimal) | Usable Hosts | Use Case |
|---|---|---|---|
| /8 | 255.0.0.0 | 16,777,214 | Very large organizations (legacy Class A). |
| /16 | 255.255.0.0 | 65,534 | Large internal networks (Class B). |
| /24 | 255.255.255.0 | 254 | Standard LAN (Class C-style). |
| /25 | 255.255.255.128 | 126 | Split /24 in half. |
| /26 | 255.255.255.192 | 62 | VLANs or office segments. |
| /27 | 255.255.255.224 | 30 | Small networks or labs. |
| /28 | 255.255.255.240 | 14 | Small groups of devices. |
| /30 | 255.255.255.252 | 4 | Point-to-point links (routers). |
| /32 | 255.255.255.255 | 1 | Single host (loopback, firewall). |
Note: CIDR also supports IPv6. For example, the address 2001:db8::/32 indicates that the first 32 bits represent the network portion, while the remaining bits identify the host.
Benefits of Subnetting
Using subnets in network addressing has the following benefits:
- Efficient IP address organization. Subnets allow you to structure internal networks around operational requirements. For example, a company with multiple locations can isolate each site into its own subnet or assign separate subnets for departments or divisions. With CIDR prefixes, network admins can closely match subnet sizes to the number of required hosts, maximizing IP address space usage.
- Isolation and security. Subnets help isolate devices and data flows into smaller logical groups. Traffic intended for one set of hosts stays within its subnet and does not broadcast to all hosts throughout the network. The containment creates an additional security layer and reduces the attack surface significantly. An attacker would need to access both the right network and the specific subnet of a target device.
- Lower network congestion. Networked devices compete for time on the network when sending packets. This competition can lead to congestion and slower packet delivery during peak traffic. By dividing a large network into smaller subnets, you reduce the number of devices competing for bandwidth on any one segment and across the broader network.
Subnetting Challenges and Limitations
While subnetting has many advantages, it also has several limitations:
- Increased latency due to routing. Devices on different subnets cannot communicate directly, even if they are in the same physical location. A router or switch must be configured to handle inter-subnet communication, which increases infrastructure costs and network latency.
- Requires extensive network planning. It is challenging to determine how many hosts to allocate per subnet while also accounting for future growth, potential IP conflicts, and changing business needs. This is particularly true in large or dynamic environments.
- Maintenance overhead. Managing many smaller subnets increases complexity and can make it more difficult to configure, monitor, and troubleshoot network settings. As the network grows, hiring additional staff to maintain routing, manage DHCP scopes, and configure firewall rules for each subnet may be necessary.
- Potentially wasted IP space. In the legacy class-based system, moving from a Class C to a Class B network would add over 65,000 usable IPs, even if you only need an additional 10. CIDR has mostly solved this issue by allowing more granular subnet sizing, but inefficient allocation is still a real problem, especially with poor planning.
How to Create a Subnet
To create a subnet, you need to:
1. Define network requirements by calculating how many subnets you need, the number of hosts per subnet, and whether you are working with IPv4 or IPv6 addresses.
2. Select an IP Address block based on those requirements. Choose a slightly larger block than the one calculated. For example:
192.168.10.0/24- Up to 254 hosts, sufficient for a small office or branch.192.168.0.0/22- Up to 1,022 hosts, enough for multiple departments in a medium-sized office.10.10.0.0/16- A larger internal network that can be deployed across multiple sites or departments.2001:db8:100::/48- A delegated IPv6 block for use in a lab or testing environment.
3. Based on the number of hosts needed, choose a CIDR prefix (or subnet mask):
/26- 62 usable IPs, can be used for small VLANs (e.g., printers, VoIP phones)./25- 126 usable IPs, which may be sufficient for a small team or department./24- 254 usable IPs, a standard LAN setup for an office branch./22- 1,022 usable IPs for a large open-office or guest Wi-Fi environment./64- Standard subnet size in most IPv6 deployments
4. Calculate the subnet ranges, which include the network address, broadcast address (if using IPv4), usable host range, and total number of addresses per block.
Note: Use a subnet calculator to avoid errors. They can assist with IPv4/IPv6 subnet calculations and CIDR-to-mask conversions.
5. Distribute the subnets to your organizational units. Keep a record of which subnet is used where, including DHCP ranges, gateway addresses, and reserved IPs.
6. Assign interface IPs from the appropriate subnets, update routing tables, and configure DHCP servers on routers, switches, and firewalls.
After configuring the network and related devices, test the setup in a real-world scenario to confirm that hosts can communicate, and that routing between subnets functions correctly.
Conclusion
The article explained how subnets work and how to use them to control traffic flows, reduce network congestion, and isolate sensitive systems.
During troubleshooting, network administrators often check subnet settings first. Tools like Nmap can help scan multiple hosts and subnets simultaneously.